In the first six months of 2024, identities continued to be a major trend among the malicious and suspicious activity that Red Canary detected, with a trio of cloud-native techniques enabled by compromised identities making our 10 most prevalent MITRE ATT&CK® techniques. Additionally, the top 10 threats we tracked in the first half of the year were largely arriving on customer endpoints by way of web-based initial access. These are two of the key findings you can read about in-depth in our first inaugural Threat Detection Report midyear update.
What’s in the midyear update?
The midyear update is designed to be a lightweight overview of the threats and techniques we detected in the first half of the year—as well as an examination of the most impactful security trend impacting organizations. It is effectively a preview of what you can expect to see in the more in-depth Threat Detection Report we’ll be releasing in 2025.
Since you can go and read the report yourself (and it’s not terribly) long, we’ll just briefly highlight what the Threat Detection Report midyear update includes.
Key trend: Adversaries abusing identities
The report opens with an examination of the identity threat landscape. We chose to focus on the kinds of threats and techniques we’re seeing in identity-related detections, the ways that adversaries go about compromising identities, and what they often do after compromising an identity.
Beyond that, the report explores the many challenges that organizations face as they attempt to strengthen their identity infrastructure, including the challenges presented by MFA adoption, the complexities of permission sprawl, and the potential deluge of identity alerts they may face. Perhaps most importantly, we also offer guidance on how security teams can leverage things like conditional access policies, identity threat detection and response (ITDR) and more to mitigate the risks posed by adversaries targeting their identities.
Threats: ChromeLoader, Scarlet Goldfinch, and Atomic Stealer
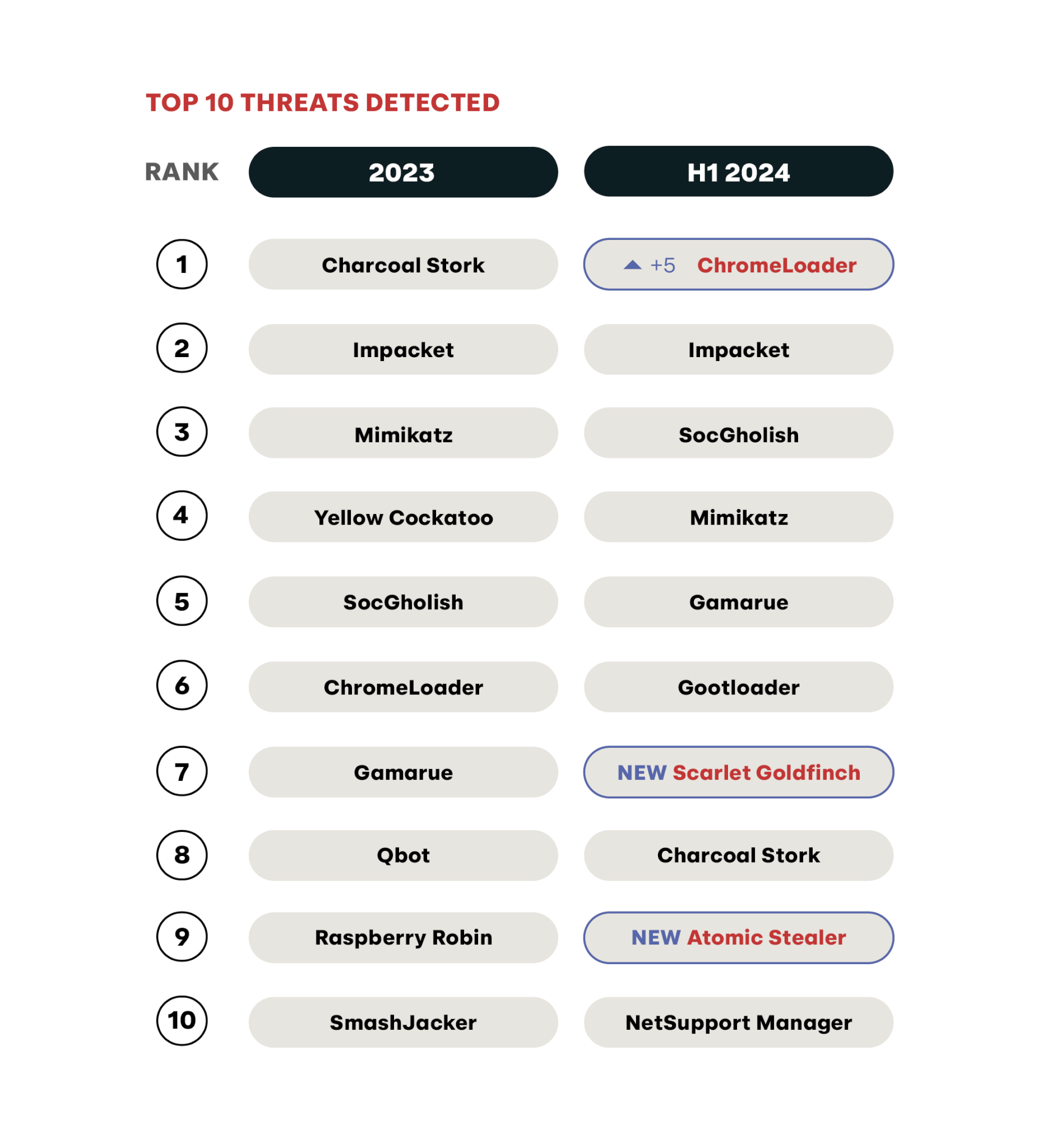
In all, the following table shows the 10 most prevalent threats we detected across our customers at Red Canary from January 1, 2024 up until June 30, 2024.
We limited our focus to just a trio of threats (and threats commonly associated with them) for the midyear report.
- ChromeLoader: A Charcoal Stork-delivered browser hijacker that’s currently the most prevalent threat across Red Canary customers
- Scarlet Goldfinch: A Red Canary-identified activity cluster that’s new to the top 10 and leverages fake browser updates to deliver NetSupport Manager its victims.
- Atomic Stealer: Another newcomer, this macOS information stealer is so prevalent that it made the top 10 despite macOS machines representing a small fraction of the endpoints we monitor.
For each of these threats, we include analysis and guidance on what organizations can do to prevent it or mitigate its risk.
Techniques: Cloud Accounts, Email Forwarding Rules, and Email Hiding Rules
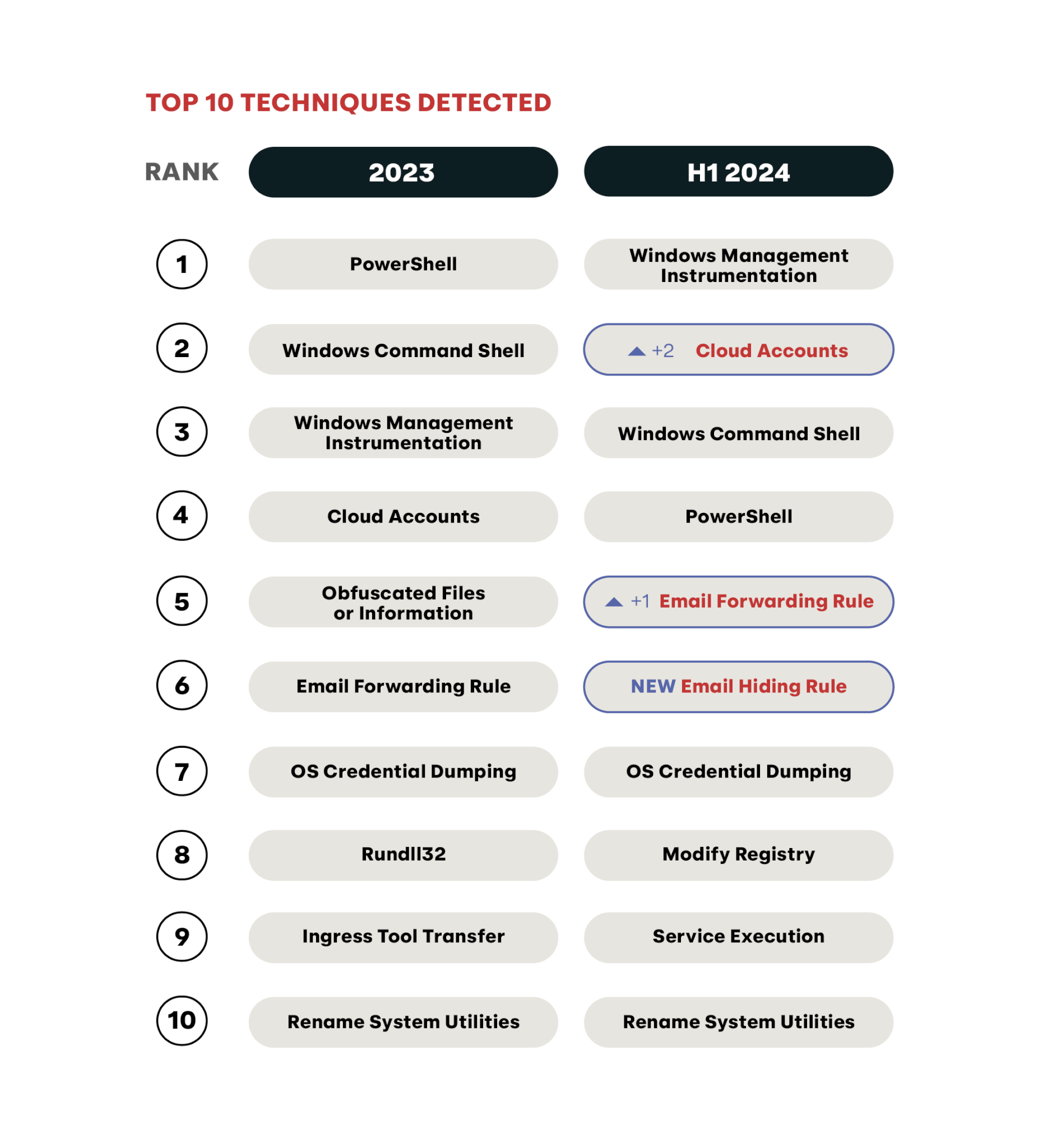
In all, the following table shows the 10 most prevalent ATT&CK techniques we detected across our customers at Red Canary from January 1, 2024 up until June 30, 2024.
As is the case with threats, we chose to focus on just a few techniques, in this case specifically those that are truly emergent in our detection dataset. Each of these is a cloud-native technique that’s playing an important role in driving the identity trend we also discuss in the report:
- Cloud Accounts: Adversaries leverage valid cloud accounts to access their victim’s cloud environments.
- Email Forwarding Rules: Adversaries create forwarding rules to to move email route email messages to external addresses or specified folders.
- Email Hiding Rules: Adversaries attempt to hide email messages by deleting them or moving them to places where victims are unlikely to look.
As was the case with threats and the identity section, we offer guidance on how security teams can monitor their cloud and email systems and what they can to reduce the risk associated with these prevalent ATT&CK techniques.