Highlights from September
Debuting at number 1 on our top 10 most prevalent threat list is Tampered Chef, an Electron Node.JS-based threat designed to process steganographic content with arbitrary JavaScript code delivered alongside recipe or calendar-themed lures. We first saw this activity in June 2025, and initially tracked it as a potentially unwanted program (PUP) until our own research and that of other researchers uncovered the application’s suspicious and deceptive qualities. You can read more about Tampered Chef below.
Akira, an opportunistic ransomware group that steals sensitive data and operates a TOR leak site, made the list for the first time sharing spot 8 in a tie. This is the first time we’ve seen a ransomware group in our monthly top 10 list since November 2021.
Latrodectus, a downloader used by adversaries to execute arbitrary commands and deliver additional payloads, made the list this month in a tie for 8th. This is Latrodectus’s second time in the top 10 after its debut on the list in May 2025; it continues to be one of the payloads of choice for ongoing paste-and-run campaigns.
Our final newcomer to the top 10 this month is Rhadamanthys, a stealer written in C++ that is used to steal credentials, cryptocurrency wallets, and browser data, as well as download and execute additional payloads. Rhadamanthys isn’t a new threat—it first appeared in 2022 and Red Canary has been tracking it since that time—but this is the first time it’s made the list. Like Latrodectus, it’s on the list this month as a paste-and-run payload.
This month’s top 10 threats
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Here’s how the numbers shook out for September 2025:
| Month's rank | Threat name | Threat description |
|---|---|---|
| Month's rank: ⬆ 1 | Threat name: Tampered Chef | Threat description : Electron Node.JS-based threat designed to process steganographic content with arbitrary JavaScript code delivered alongside recipes for meals |
| Month's rank: ⬇ 2 | Threat name: | Threat description : Traffic distribution system, first observed in 2024, that uses compromised WordPress sites to deploy malicious code that may lead to malware families such as Rhysida and Interlock ransomware, D3F@ck Loader, Mocha Manakin, Mintsloader, and WARMCOOKIE |
| Month's rank: ⬇ 3 | Threat name: | Threat description : Red Canary's name for a cluster of activity, delivered via installers masquerading as legitimate free software, that progresses through several stages to a PyInstaller EXE with stealer capabilities |
| Month's rank: ⬆ 4 | Threat name: | Threat description : Legitimate remote access tool (RAT) that can be used as a trojan by adversaries to remotely control victim endpoints for unauthorized access |
| Month's rank: ⬇ 5 | Threat name: | Threat description : A loader designed to maintain persistence and deliver additional threats |
| Month's rank: ⬆ 6* | Threat name: | Threat description : Open-source tool that dumps credentials using various techniques |
| Month's rank: ⬇ 6* | Threat name: | Threat description : Activity cluster that uses a distribution scheme similar to SocGholish and uses JScript files to drop NetSupport Manager onto victim systems |
| Month's rank: ⬆8* | Threat name: | Threat description : Opportunistic ransomware group operating since March 2023 that steals sensitive data and operates a TOR leak site |
| Month's rank: ⬆8* | Threat name: | Threat description : Downloader used by adversaries to execute arbitrary commands and deliver additional payloads |
| Month's rank: ⬇10* | Threat name: | Threat description : Information stealer designed to target data within web browsers and locally stored files on macOS systems, with the goal of accessing sensitive information including credentials, payment card data, keychain details, and cryptocurrency wallets |
| Month's rank: ⬆10* | Threat name: | Threat description : Malware family used as part of a botnet. Some variants are worms and frequently spread via infected USB drives |
| Month's rank: ⬆ 10* | Threat name: Rhadamanthys | Threat description : Information stealer written in C++ that is used to steal credentials, cryptocurrency wallets, and browser data, as well as download and execute additional payloads |
| Month's rank: ⬆ 10* | Threat name: | Threat description : Dropper/Downloader that uses compromised WordPress sites to redirect users to adversary infrastructure posing as necessary browser updates to trick users into running malicious code |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Tampered Chef savors steganography
We first saw Tampered Chef in early June 2025, as a sudden high-volume wave of activity that we initially classified as a PUP before we took a closer look at its code. We weren’t the only ones doing so; within days of our first seeing it, other researchers published their findings on this threat. Tampered Chef has several suspicious and intentionally deceptive qualities that led us to reassess it as malware. Our updated classification makes it eligible for inclusion in our top 10 list, since we do not typically include adware.
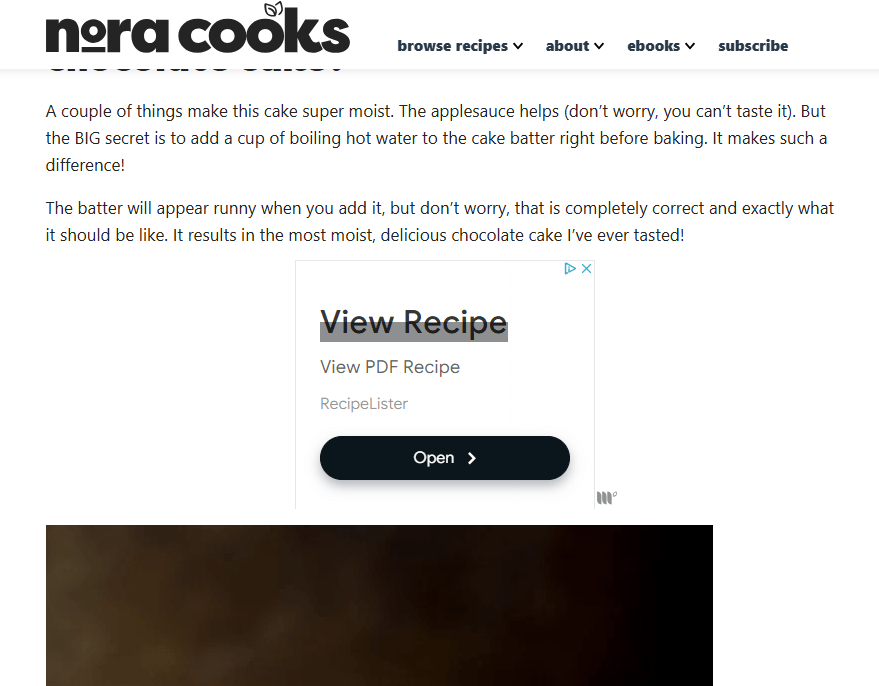
The recipe-themed version of the lure disguises itself as a calorie-counting recipe tool, presented to users via sidebar or banner ads, sometimes on websites with articles that promote the tool.
The Great Trojan Bakeoff : Tampered Chef vs. JustAskJacky vs. Browser Assistant
Tampered Chef is not the only high-volume trojan horse application that we (and others) have observed recently. Another example is JustAskJacky, a family of NodeJS applications that masquerade as a helpful AI or utility tool while conducting reconnaissance and executing arbitrary commands in memory in the background. Another threat we’ve seen mentioned at the same time is Baoloader, which we track as Browser Assistant here at Red Canary. We are currently tracking these three threats as separate and distinct clusters, due to differences in behavior.
Here’s a very brief breakdown of how we’re differentiating them:
| Tampered Chef | JustAskJacky | Browser Assistant | |
|---|---|---|---|
| : Also known as: | Tampered Chef: Calendaromatic, Recipe Lister | JustAskJacky: GoAskBobby, AskBettyHow, OpenMyManual, and many more | Browser Assistant: Baoloader |
| : Masquerades as: | Tampered Chef: Recipe applications or calendar helpers | JustAskJacky: Helpful AI or utility tool, sometimes PDF-themed NodeJS application | Browser Assistant: Helpful browser extensions and, more recently, PDF readers |
| : Language/file: | Tampered Chef: Node.JS Electron application | JustAskJacky: Family of NodeJS applications | Browser Assistant: JavaScript |
| : Behavior: | Tampered Chef: Uses steganography for command and control messages | JustAskJacky: Typically has GUID values in its filenames, for example | Browser Assistant: May use EXE or MSI files for installation, for example |