Each month, the Intel team provides Red Canary customers with an analysis of trending, emerging, or otherwise important threats that we’ve encountered in confirmed threat detections, intelligence reporting, and elsewhere over the preceding month. We call this report our “Intelligence Insights” and share a public version of it with the broader infosec community.
Highlights
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Here’s how the numbers shook out for August 2023:
| Last month's rank | Threat name | Threat description |
|---|---|---|
| Last month's rank: ⬆ 1 | Threat name: Charcoal Stork | Threat description: Suspected pay-per-install (PPI) provider that uses malvertising to deliver installers, often disguised as cracked games, fonts, or desktop wallpaper |
| Last month's rank: ➡ 2 | Threat name: | Threat description: Malware family used as part of a botnet. Some variants are worms and frequently spread via infected USB drives |
| Last month's rank: ⬆ 3* | Threat name: | Threat description: Activity cluster characterized by the delivery of an information stealer and .NET RAT via search engine redirects |
| Last month's rank: ➡ 3* | Threat name: | Threat description: Open source tool that dumps credentials using various techniques |
| Last month's rank: ⬆ 5* | Threat name: Atomic Stealer | Threat description: Information stealer designed to target data within web browsers and locally stored files on macOS systems, with the goal of accessing sensitive information including credentials, payment card data, keychain details, and cryptocurrency wallets |
| Last month's rank: ⬆ 5* | Threat name: NetSupport Manager | Threat description: Legitimate remote access tool (RAT) that can be used as a trojan by adversaries to remotely control victim endpoints for unauthorized access |
| Last month's rank: ⬆ 5* | Threat name: Scarlet Goldfinch | Threat description: Activity cluster that uses a distribution scheme similar to SocGholish and uses JScript files to drop NetSupport Manager onto victim systems |
| Last month's rank: ⬆ 8 | Threat name: | Threat description: Information stealer sold on underground forums and used by a variety of adversaries |
| Last month's rank: ⬇ 9* | Threat name: | Threat description: Malware that modifies victims’ browser settings and redirects user traffic to advertisement websites |
| Last month's rank: ⬆ 9* | Threat name: | Threat description: Penetration testing tool that integrates functionality from multiple offensive security projects and has the ability to extend its functionality with a native scripting language |
| Last month's rank: ⬆ 9* | Threat name: Danabot | Threat description: Modular trojan used by multiple adversaries and distributed via phishing campaigns, pirated software, and Fallout Exploit Kit |
| Last month's rank: ⬇ 9* | Threat name: | Threat description: Collection of Python classes to construct/manipulate network protocols |
| Last month's rank: ⬆ 9* | Threat name: | Threat description: Activity cluster using a worm spread by external drives that leverages Windows Installer to download malicious files |
| Last month's rank: ⬇ 9* | Threat name: | Threat description: Dropper/downloader that uses compromised WordPress sites to redirect users to adversary infrastructure posing as necessary browser updates to trick users into running malicious code |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Observations on trending threats
We have three newcomers to this month’s top 10, appearing alongside many regulars and returning threats. Two of the newcomers to the list are Red Canary clusters making their public debuts. Claiming the top spot for both the month and the year-to-date is Charcoal Stork, a suspected pay-per-install (PPI) content provider that we’ve been tracking internally since January 2022. We’ve seen Charcoal Stork deliver both ChromeLoader and SmashJacker. You can read a lot more about Charcoal Stork below.
Appearing in a three-way tie for spot 5, Scarlet Goldfinch is a new activity cluster we began tracking in June 2023. Scarlet Goldfinch is similar to SocGholish in its use of fake update lures that use JScript files to directly drop NetSupport Manager—a payload that, not coincidentally, also tied for spot 5. We named Scarlet Goldfinch to track activity similar to but not the same as FakeSG/Rogue Raticate. Read on to learn more.
Rounding out the three-way tie for spot 5 is Atomic Stealer, our third newcomer to our top 10, following a wave of activity at the beginning of August. Atomic Stealer is an information stealer designed to target macOS systems. It targets data within web browsers and files stored locally on macOS systems to discover sensitive data including credentials, payment card data, cookies, keychain details, and cryptocurrency wallet details.
Charcoal Stork delivers malware, not joy
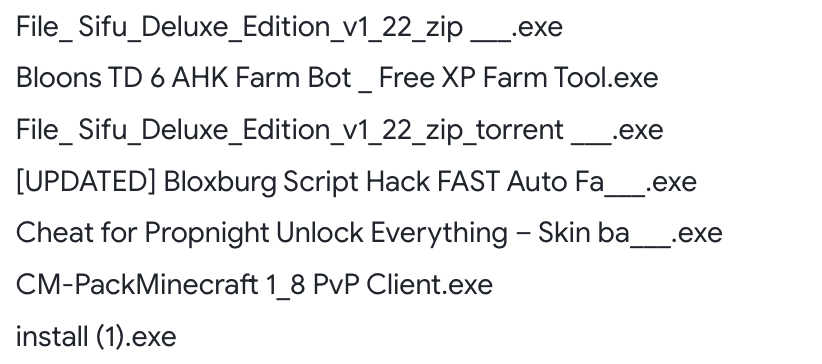
Charcoal Stork is a suspected pay-per-install (PPI) content provider that relies on malvertising and SEO optimization to lure victims. We distinguish its activity primarily through installer file names and hashes. Common default filenames for Charcoal Stork are Your File Is Ready To Download and install, though we see other filenames related to wallpapers, online gaming, software, and livestreaming. Below is an example of what Charcoal Stork filenames look like in VirusTotal details. Note that some filenames are variants of install.exe, but many relate to software and games.
While we recognize binary names are a weak characteristic for correlation—and we will have many gaps around this threat—we’ve found it helpful to track this cluster. Doing so has resulted in our realization that it is widespread across many environments.
A single Charcoal Stork installer may be reused hundreds of times to deliver the same payload to different victims, often with different filenames depending on what the victim searched for in a search engine. It includes a number of distinct installers delivering a variety of payloads, which is why we suspect that Charcoal Stork is a pay-per-install (PPI) content provider relying on malvertising and SEO optimization to lure victims. Most Charcoal Stork payloads consist of nothing more than a browser extension designed to redirect search engine queries through a specified domain. However, some Charcoal Stork payloads, like ChromeLoader, include all the components required for backdoor access and code execution.
Because Charcoal Stork can lead to ChromeLoader, many other research teams track Charcoal Stork with ChromeLoader under the ChromeLoader family name. However, we’ve observed payloads delivered by Charcoal Stork that do not quite match ChromeLoader, including SmashJacker in mid-2023 and a new payload in August 2023. Therefore, we think it is useful to track the initial delivery affiliate, Charcoal Stork, as distinct from the payloads it delivers.
Charcoal Stork’s timeline
In January 2022, we started seeing a wave of dubious installer binaries masquerading as anything from cracked games to wallpaper. One distinguishing characteristic of the installer was the use of the default filename Your File Is Ready To Download, presented as a disc image—ISO on Windows, DMG on macOS—and requiring multiple rounds of user interaction to run. The specific installer file remained unchanged regardless of the filename it used to misdirect victims. We often saw the same hashes in multiple environments and also found them on VirusTotal under a variety of unrelated names. The installer often dropped what we tracked as AdSearch at that time, and sometimes it dropped ChromeLoader. We decided to track the Your File Is Ready To Download installer internally under the name Charcoal Stork; it was clearly malicious, it was widespread, and it was something we wanted to keep tabs on if it appeared in our customers’ environments.
Charcoal Stork has used various file types over the time we have tracked them:
- Throughout most of 2022, Charcoal Stork used a default file name of
Your File Is Ready To Downloadpresented as a disc image—ISO on Windows, DMG on macOS. (You can read more about VirusTotal’s observation of this filename in their Malware Trends Report.) - In late 2022 into early 2023, Charcoal Stork briefly relied on Visual Basic files to initiate the installation process.
- In April 2023, the malvertising link led directly to an EXE installer. In June 2023, Microsoft Software Installer (MSI) files became dominant.
- In August 2023, Charcoal Stork switched to a default filename of
install.exefor its binaries and began to occasionally deliver a new payload different from ChromeLoader.
Intelligence gaps: We need your help!
We have many intelligence gaps around this cluster. It is possible that these different threats are separate components leveraged by the same commonly controlled adversary. The proliferation of specialized affiliates in today’s threat landscape also suggests that each tool in this activity chain may belong to distinct groups working together. If you are also tracking an aspect of Charcoal Stork, we would appreciate the opportunity to collaborate as we seek to better understand this threat. (Please send us an email!) Despite our many gaps, it’s worth noting that through the first seven months of 2023, Charcoal Stork has far and away been our most prevalent threat, over three times more than the next most common threat. This emphasizes the importance of continuing to track this cluster.
Scarlet Goldfinch: Novel behavior
Scarlet Goldfinch is a cluster of activity that Red Canary first observed in late June 2023. Initially, Scarlet Goldfinch appears very similar to SocGholish (aka FakeUpdates). Like SocGholish, Scarlet Goldfinch activity begins with JScript files distributed under the guise of web browser updates with names like Browser_update_16.0.5836.js or BrowserInstaller.js. Unlike SocGholish, which conducts additional discovery and execution using JScript, Scarlet Goldfinch uses these lures as a dropper, pulling down BAT and VBS files to download and install NetSupport Manager for remote control of victim systems. Scarlet Goldfinch closely matches activity reported by Trellix in August 2023.
Around the same time, we saw additional activity consistent with another SocGholish doppelganger named FakeSG or Rogue Raticate, as documented by Malwarebytes and additional researchers. Just like SocGholish and Scarlet Goldfinch, initial access is via JScript files masquerading as browser updates, starting a chain of activity that eventually delivers a payload, also typically NetSupport Manager. However, FakeSG/Rogue Raticate uses PowerShell and Mshta to download its payload, as opposed to the BAT/VBS activity leveraged by Scarlet Goldfinch. Red Canary currently tracks Scarlet Goldfinch as a distinct cluster separate from both SocGholish and FakeSG/Rogue Raticate due to the differences in TTPs. Despite the similarity in initial access lures and common choice of remote access payload, we are not currently aware of any direct connections between these three activity clusters.
Detection opportunity: Scripts executed from built-in Explorer ZIP functions
The following pseudo-detection analytic identifies scripts executed from the built-in explorer.exe ZIP folder function. Adversaries like Scarlet Goldfinch often compress malicious scripts via a ZIP file in an attempt to evade network-based security products. Investigating follow-on file modifications, registry modifications, and child processes related to this behavior can help determine if it is malicious or legitimate.
parent_process == (explorer.exe)
&&
process == (wscript.exe)
&&
command_line_includes ( users, temp) && (.zip, .js)
&&
has_netconn