Since the dawn of modern information security in the mid-1990s, the industry has been fixated on how to prevent bad things from happening. Yet even a cursory review of headlines shows we’ve not made much meaningful progress toward this goal since then. The bad guys continue to “get in” and cause damage to victims. However, security professionals realize this does not represent a failing. Rather, we must recognize that full “prevention” is a logical fallacy in an environment with human adversaries and defenders. Prevention is necessarily limited to known threats, and understanding the critical role for procedures and technology that provide detection and response in a comprehensive information security program is integral to the success of those programs.
Many information security leaders, especially those new to the field, are astonished at the number of security threats that soar past antivirus, intrusion prevention systems, and similar technology. While there are numerous reasons for threat prevention not working, the core truth is that attackers have access to the same products as defenders—and engineering their way around those known hurdles becomes a fairly simple task. These threats can evolve far faster than our prevention products—no matter what sales and marketing in the industry would suggest.
Put simply: without a massive revolution in technology, there is no foreseeable way to prevent unknown threats with any meaningful rate of success.
Enhancing Preventive Products With Continuous Incident Response
This doesn’t mean the concept of prevention should be abandoned. We still need reliable prevention solutions to address the known threats, freeing precious and expensive human attention for the evolving threats. Perhaps a good analogy here can be borrowed from the medical world. Your home and office probably have a first aid kit that can deal with basic medical needs. You may have an AED (defibrillator) on hand that would help someone in certain types of cardiac crisis. These are important and necessary components of a comprehensive first aid plan. However, having those items doesn’t negate the importance of a working phone where you can also call emergency services when needed.
By this comparison, it is equally important to balance the expectations for and limitations of prevention technology in the information security space. As soon as we accept that these platforms are not end-all solutions, the need for a detection and response component to the overall information security program becomes crystal clear.
Read more from Red Canary’s CSO: How CISOs Can Navigate the Shift Toward Detection and Response
How Detection and Response Can Address Endpoint Security Gaps
Detection and response comprise the portion of information security programs that deal with threats that slip through the nets laid by typical prevention platforms. Where antivirus quarantines are designed to identify and neutralize known malware, detection looks for software with behaviors that are not quite in line with expected norms. Response is the critical human-run phase that investigates detected anomalies and ultimately makes a safe/unsafe decision and takes appropriate cleanup and corrective actions. A mature information security program will use the response phase to locally generate threat intelligence about the previously missed threat which can be fed back into both prevention and more decisive detection. This lifecycle is the footprint for “Continuous Incident Response.”
Phases of a Continuous Incident Response Program
1. Visibility
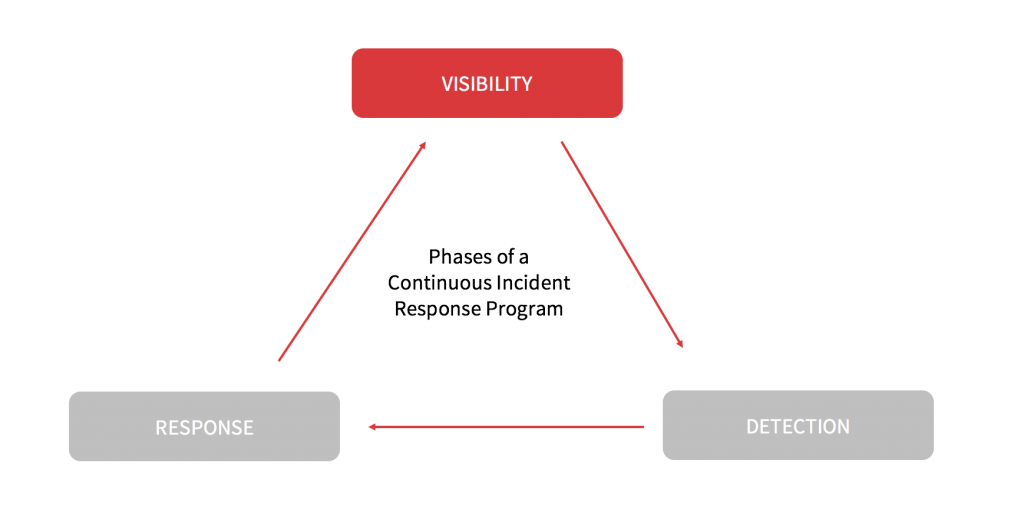
Read more about common visibility concerns and assessment criteria
2. Detection
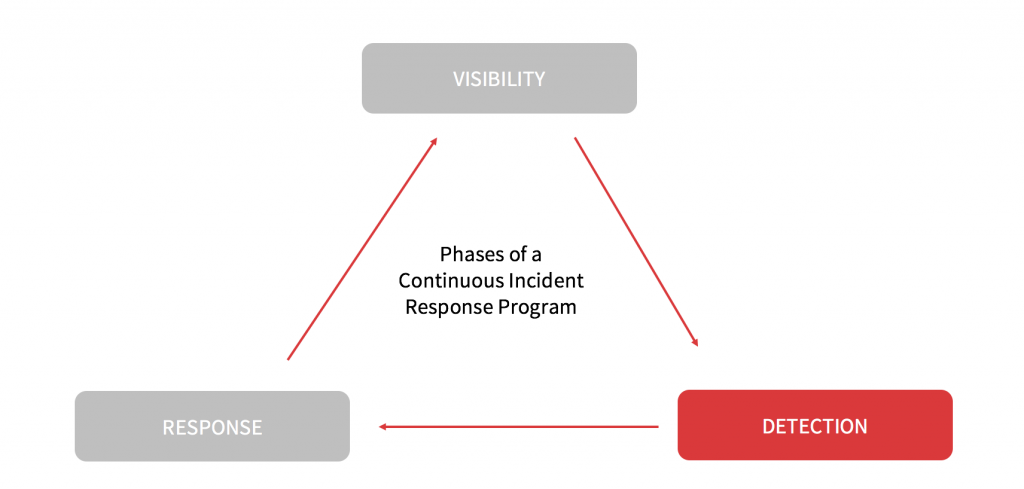
Because of this scale, the detection phase may be partially or fully automated. There are trade-offs to consider in evaluating this balance. Any degree of automation opens the potential for attackers to trivially evade detection, should the automation method become known. Therefore an ideal detection phase casts a wide net, and identifies far more potential threats than are eventually confirmed as suspicious.
The detection phase is also where threat intelligence is typically applied. Whether internally-developed or externally-sourced, threat intelligence helps to determine what events that have been collected qualify as “anomalous.” Threat intelligence may focus on specific data points such as IP addresses, domain names, or malicious executables. In any case, the threat intelligence must be weighed against data being collected to ensure a proper search can be accomplished.
Another detection method involves using localized baselines of normal activity to identify anomalous patterns. Internally-generated baselines may focus on behavioral heuristics such as typical patterns of activity on an endpoint, windows of active time per day for each user, or highest volume IP addresses or networks. The key to baselines is that the collection phase will determine what baselines are available, and ongoing use requires the same visibility into actions within the environment. These baselines will be invaluable for identifying attacker behaviors, as they will almost certainly stand out from the “normal” activities the baselines characterize.
3. Response
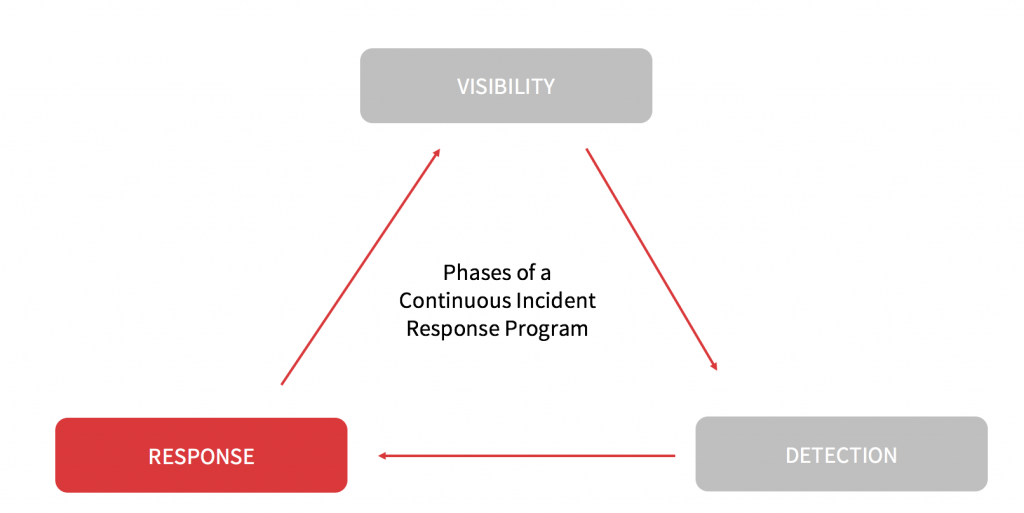
While there is no industry-standard blueprint for response actions, their need underscores the notion that pure prevention actions are insufficient to address emerging threats. A wily human attacker can change tactics quickly, requiring a similarly wily human responder to give chase and take appropriate action in turn.
During and after the response phase, mature IR teams will examine the data generated during the continuous IR process to determine if any indicators or related threat intelligence would be beneficial in identifying future malicious activity. This feedback loop is critical to shorten the time an attacker can operate with impunity in the victim’s environment. As always, operational intelligence should be reevaluated periodically to ensure it is still relevant to ongoing IR requirements.
Key Takeaways
Implementing a program involving detection and response, in addition to targeted prevention where feasible, will result in a comprehensive information security posture that is best suited to today’s threat landscape. By implementing balanced components of each phase and re-evaluating efficiency and currency on an ongoing basis, security managers can be assured they are not overly relying on the fallacy of prevention for their organization’s security needs.
Looking to augment your detection and response? Learn more about Red Canary Managed Detection and Response