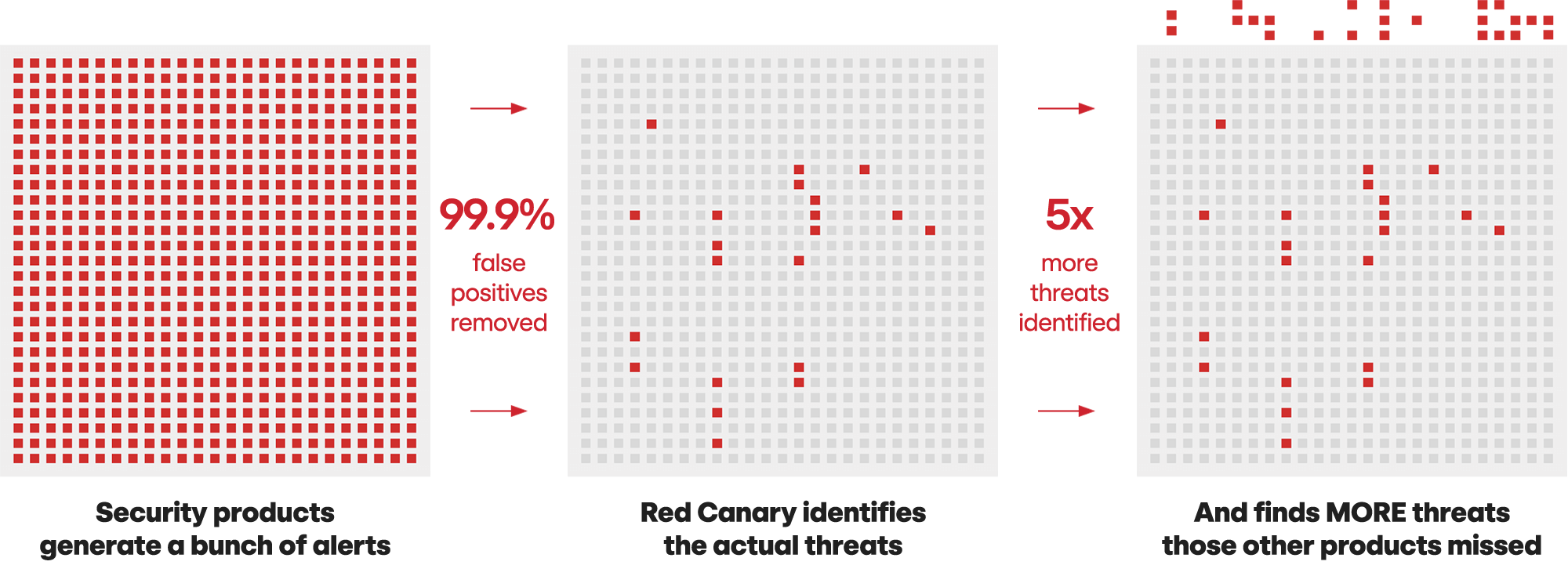
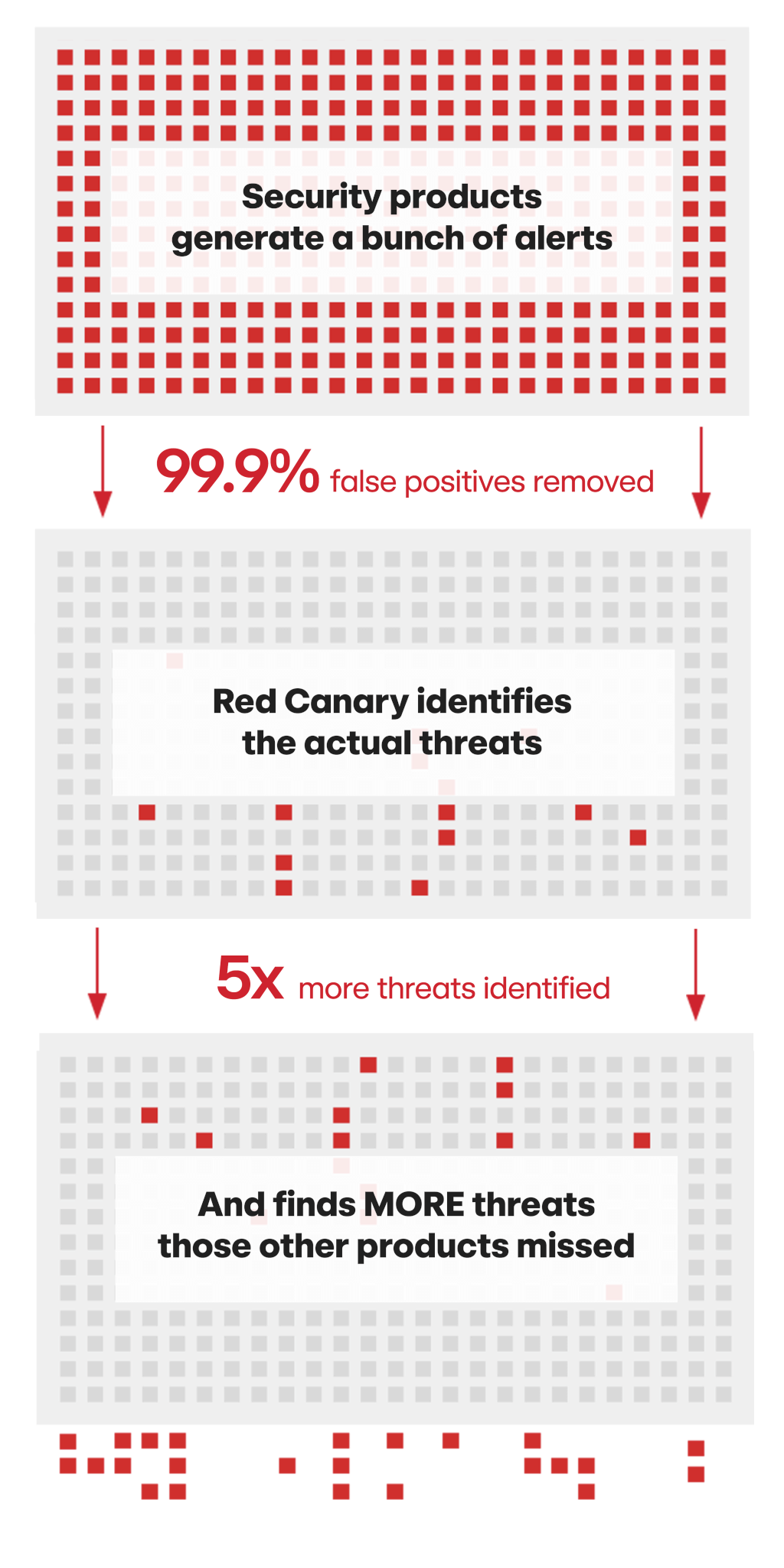
Unmatched detection
Customers validated a 99.6% threat accuracy rate across nearly 70,000 threat notifications from Red Canary last year. That means instead of wasting hours on false positives, your team stays focused on its priorities and only pivots to actual threats.
Actionable threat intelligence
Actionable threat profiles, intel-driven analytics, and situation-specific response and remediation recommendations enable you to continuously improve your security posture. Help your team make better decisions and prioritize resources according to the most relevant threats to your organization.
24×7 expert response
Ungated access to response experts helps you rest assured that no matter the day, hour, or threat, Red Canary’s got you covered 24×7. Guided, automated, or active human-led response options allow you to accelerate response time according to your organization’s preferences.
Learn more about our capabilities
Our values
We are relentless
Our adversary is very human and relentless in their crimes. We are equally relentless in finding and stopping those adversaries. Security teams we partner with have to be ready 24×7, and we are always there alongside them. Every time we ship code, respond to a support request, or coach our partners, we always push to go a little faster.
We always deliver quality
Our industry is littered with products that were well loved when they were small but lost their quality as they grew. We obsess over not being one of them. Our guiding principle is that we’ll try to grow as quickly as possible, while maintaining quality.
We are kind and authentic
Being kind is often a novelty in security and technology business, and we believe in changing that. We embrace our authenticity and show kindness to other Canaries, competitors, and the community.
We do what’s right for our customers
Our hypergrowth means we are making hundreds of decisions every day, and we believe we can quickly make the best decisions by thinking about what is best for our customers in both the near and long term.


“Red Canary – it’s the correct thing to do for security. It’s the surety of having professionals looking at our alerts around the clock, and we have a resource to go to immediately if we have questions around detection and response.”