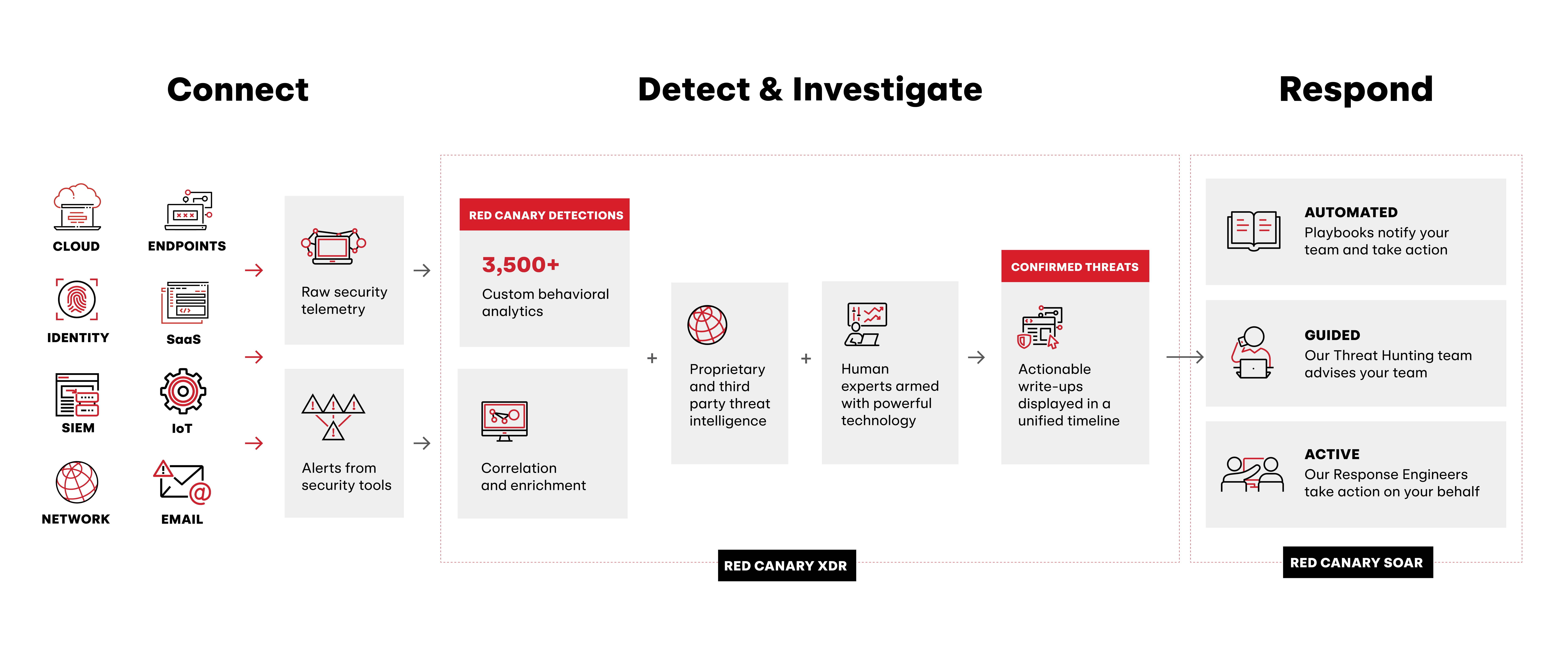
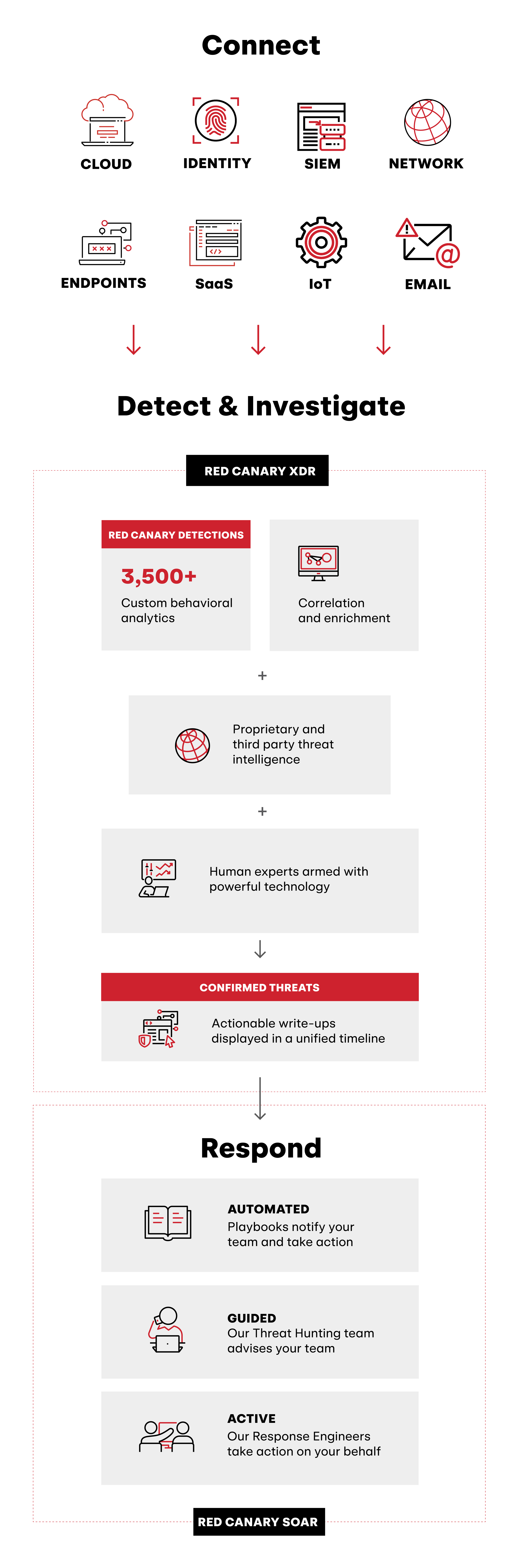
Managed Detection and Response
Red Canary detects threats that no one else does, and we do it 24×7 across your endpoints, network, cloud, identities, and SaaS apps.
get a demo Guide: 15 essential questions to ask when evaluating MDR solutions
We protect your endpoints, network, cloud workloads, identities, and SaaS applications
Some MSSP, MDR, and other security products think it’s totally normal to regurgitate alerts back to you. But you deserve better. We are your proverbial canary in the coal mine, alerting you to threats quickly.
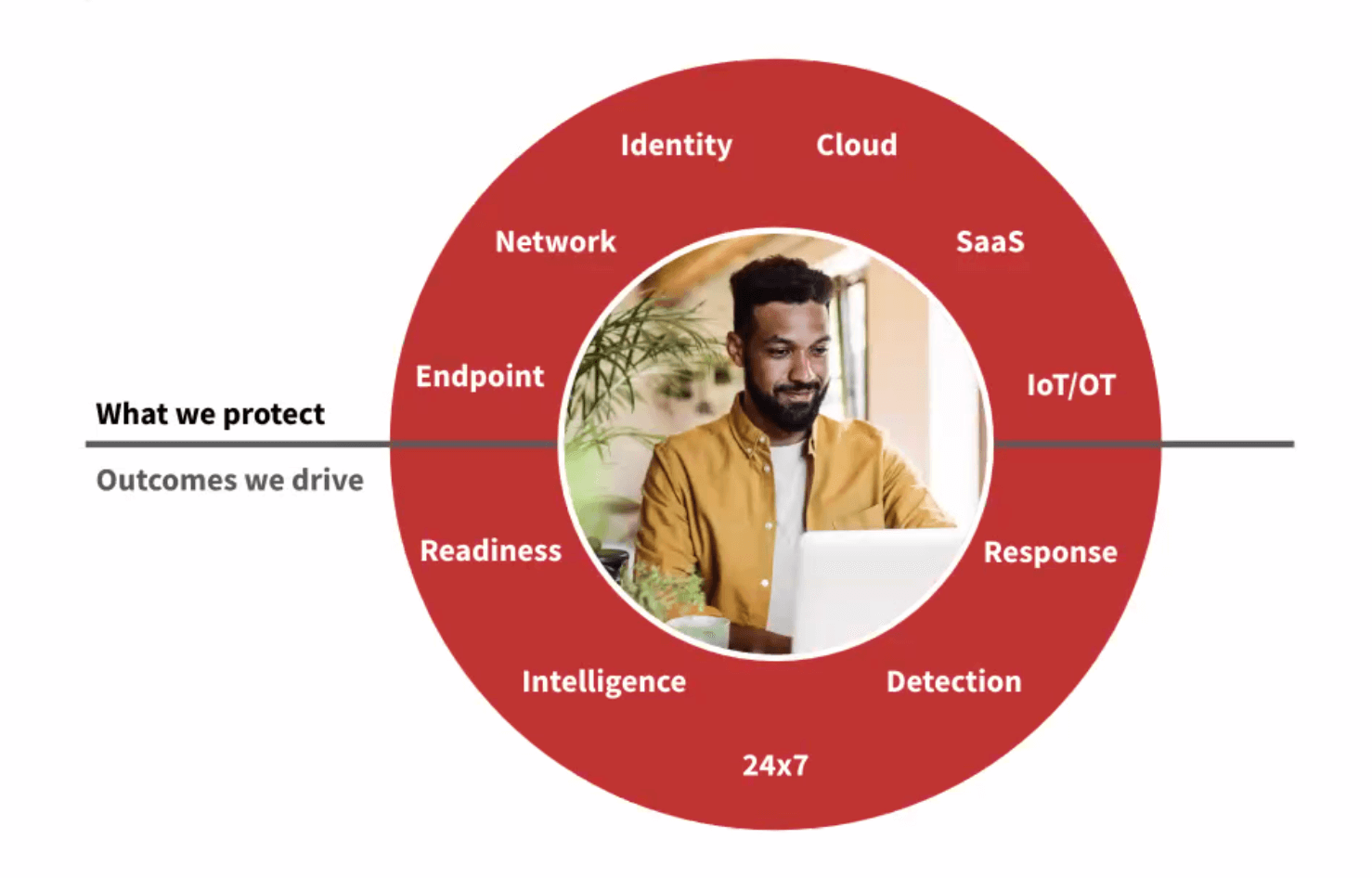
Supercharge the value of your existing security investments
Whether you have two security products or 20, we’ll help you understand what is important and ignore the noise. Not seeing a product in your security stack? Let us know – our integrations are growing quickly.
learn more about our integrationsWHAT SETS US APART
We think differently
Other MDR solutions rely solely on the alerts and logs coming from your security products. But that’s not us.
We process raw telemetry from the leading cybersecurity companies so we can apply thousands of our own analytics. Why? Because it allows our experts to spot attacks that others can’t.
203 ATT&CK TECHNIQUES COVEREDWe hunt differently
We optimize for coverage and cast the broadest detection net possible with more analytics and security telemetry than anyone else.
- 3,000+ analytics
- 20,000+ tests
- Petabytes of security telemetry
We treat you differently
We’re always here for you – you have unlimited access to our security teams whenever you need us, at no additional cost.
Our pricing is simple and predictable. Flat price per endpoint per year. No gotchas.
GET IN TOUCHWHY DOES ALL THIS MATTER?
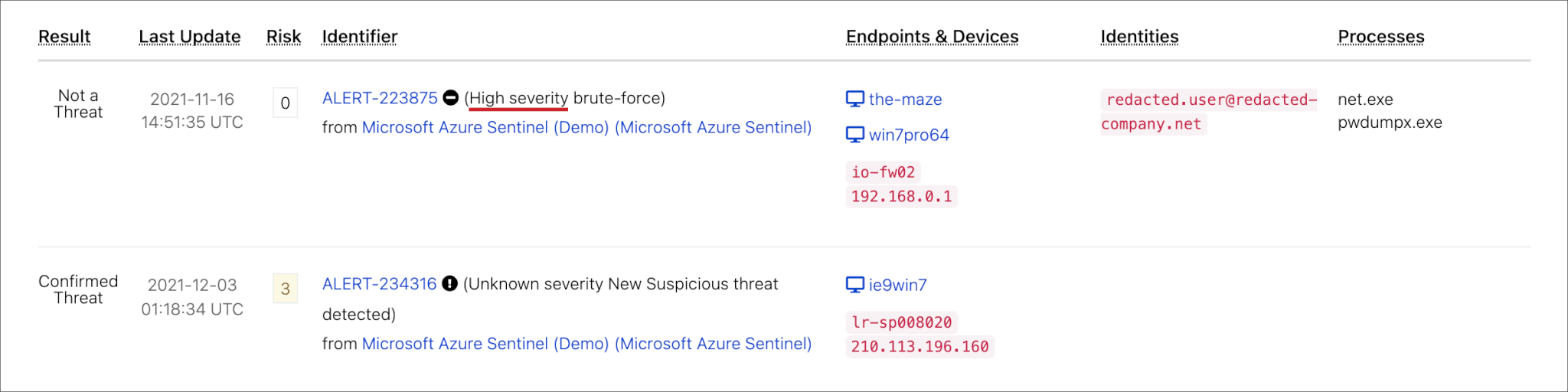
No more wondering. As soon as it happens, you’ll know.
First, we tell you which alerts deserve your immediate attention.
We only notify you of cyber threats that matter, so you can avoid the noise.
Then we detect the threats that everything else missed.
For example, we generally find 5 times more threats on your endpoints than your EDR products alert you to.
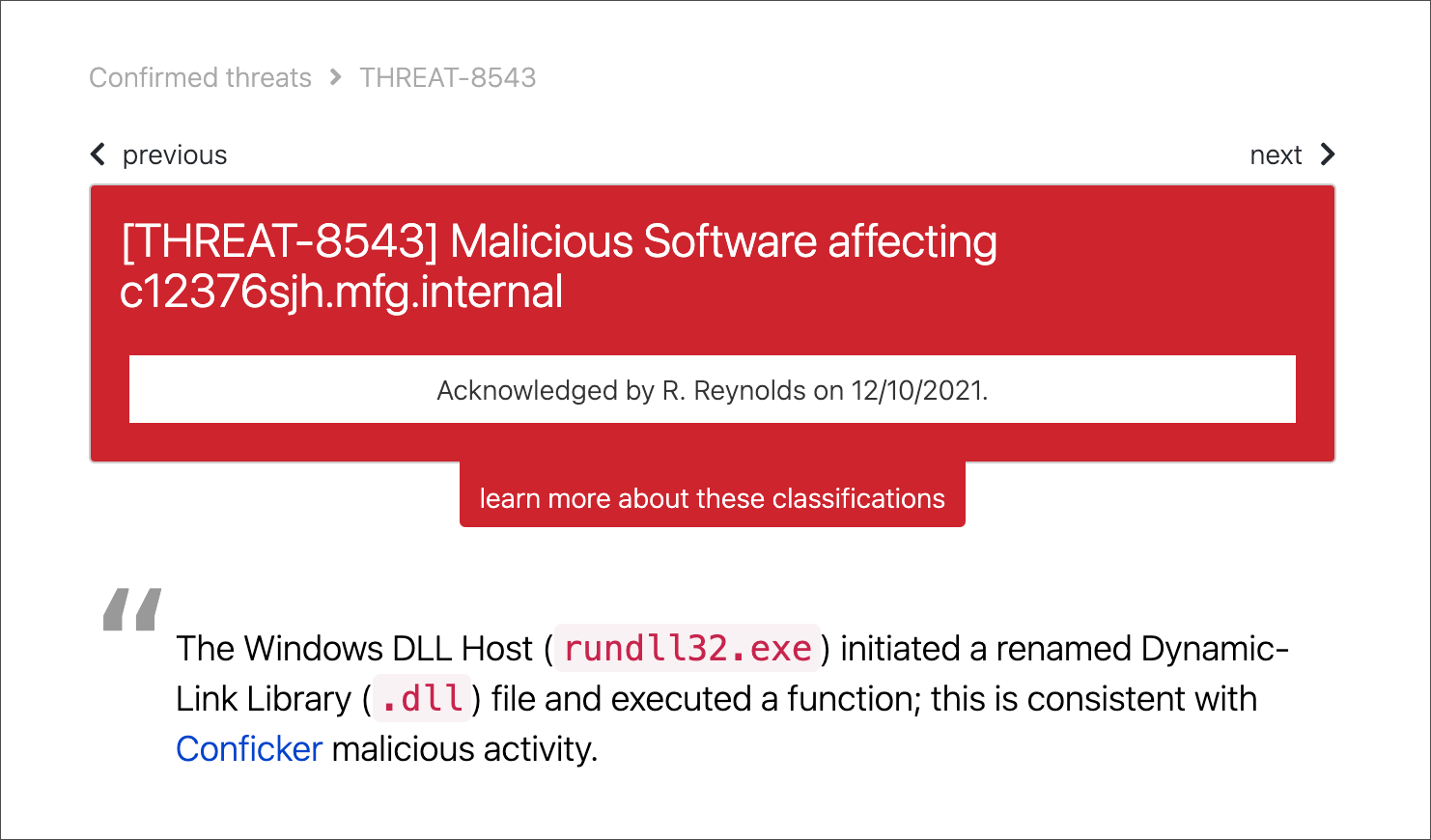
We help you respond, recover, and improve
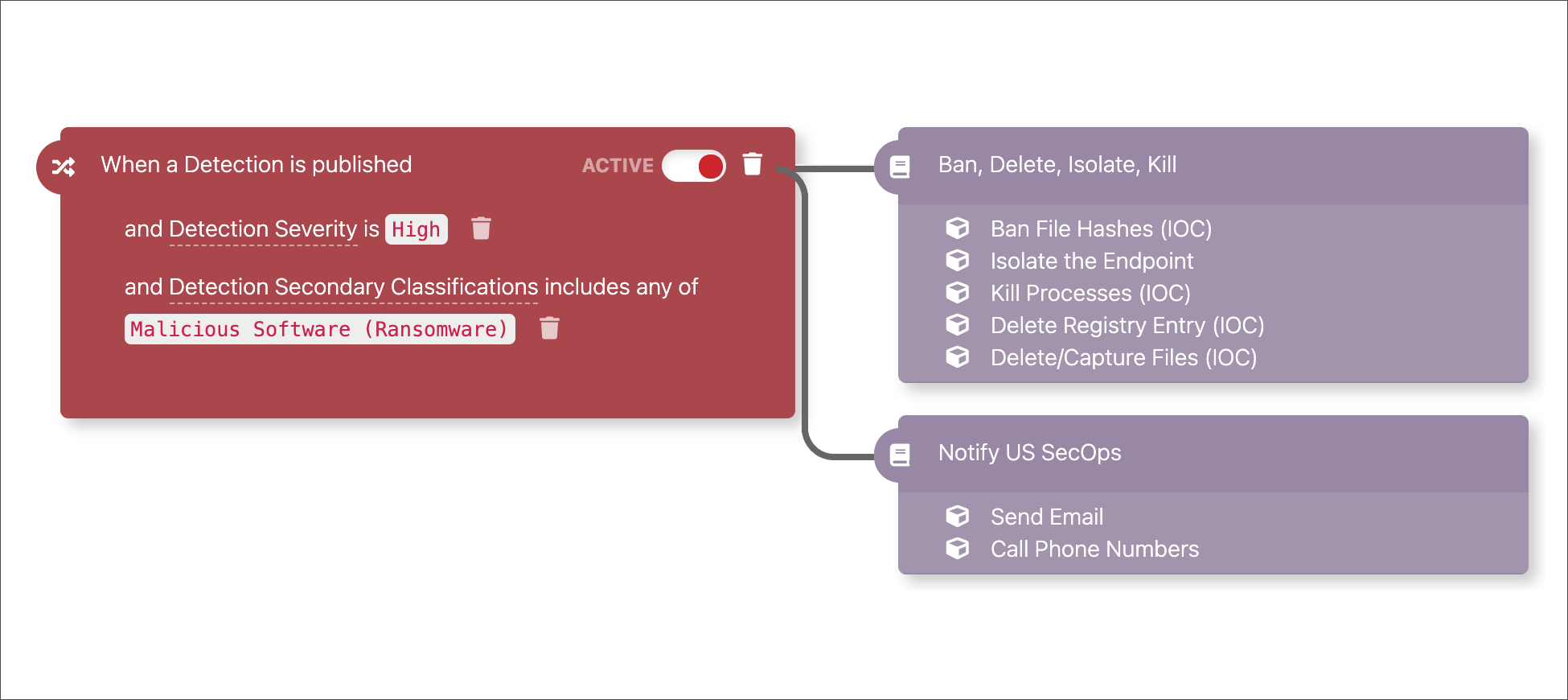
Automatically respond across your systems
Your response can be automated through playbooks that integrate with your chatops, incident management, and security tools.
Would you rather have Red Canary handle the remediation? No problem. We got you.
Track your performance
Measures like infection rate and mean time to response are essential to understand how well you’re preventing, detecting, and responding to threats.
Organizations that choose Red Canary quickly improve their performance—you’ll have the data to see for yourself.
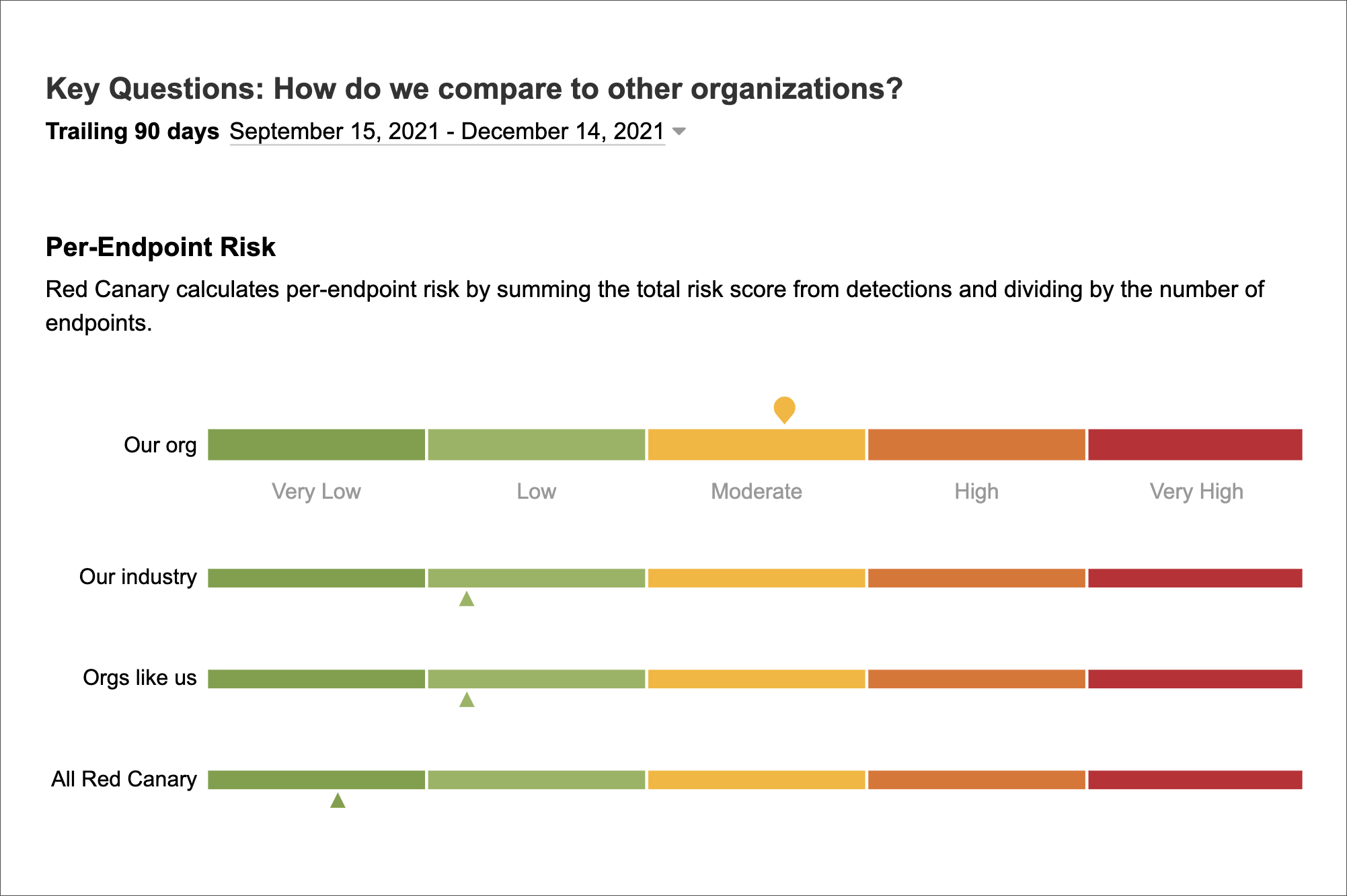
Compare yourself to other organizations
We help you understand how you compare to other organizations of similar size, industry, or globally so you can evaluate your investments and make the right moves.
Why security teams partner with Red Canary
Your organization is unique, and so is our ability to solve your challenges. Explore the use cases below to see how other teams are using Red Canary MDR to improve security outcomes.