What we detect
Ransomware and malware
Detect the tactics and tools used to deliver malicious executablesAdversary techniques
Identify the tradecraft adversaries leverage for initial access, reconnaissance, and lateral movementNetwork threats
Detect indicators of lateral movement or other malicious network activityKey benefits
Unmatched depth of detection
By processing massive amounts of streaming data, Red Canary can significantly increase the detection of confirmed threats
Speed and flexibility of remediation
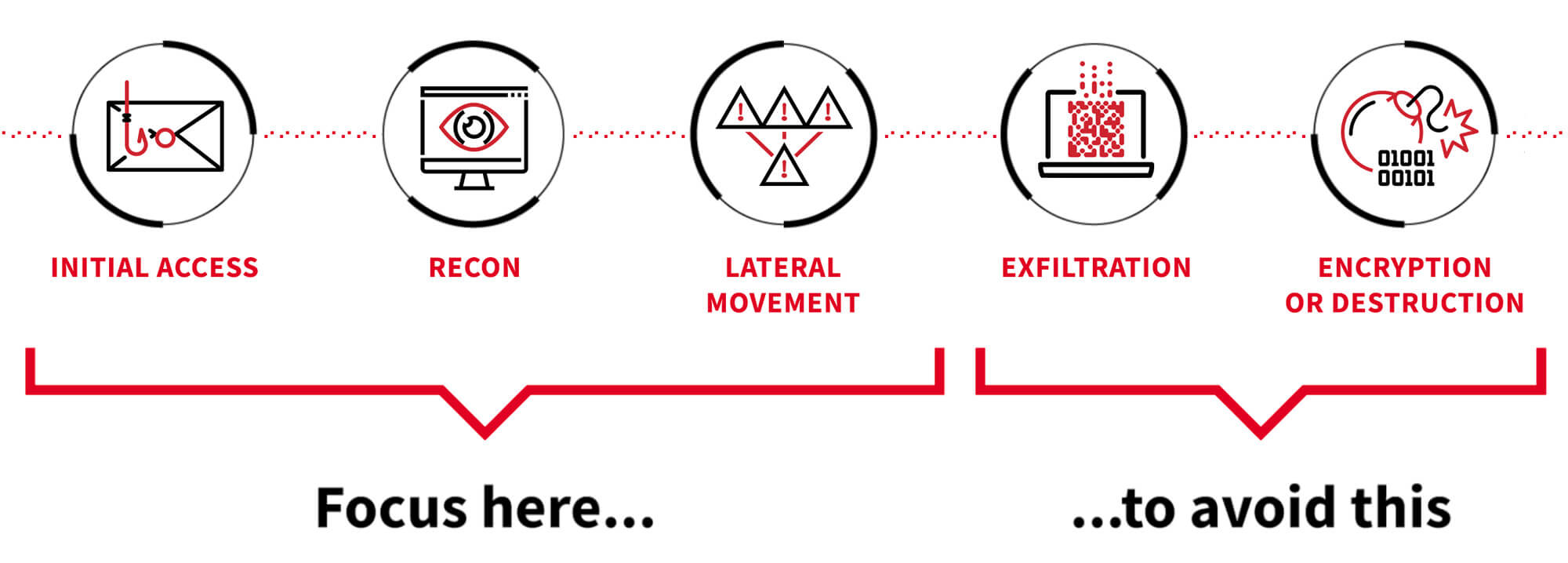
We stop threats before they negatively impact organizations by focusing on detecting and responding to early-stage adversary activity
Quality of partnership
Red Canary does the heavy lifting for your team while providing unlimited access to our experts
“I can say with high confidence we have not had further incursions since we brought on Red Canary. When you hear about breaches in the news it's usually because the attacker had an established presence and took some time to develop their attack techniques. With Red Canary we are able to knock them out before they establish any level of presence.”

Red Canary optimizes for detecting and responding rapidly to early-stage adversary activity
We find and stop threats, no matter where adversaries choose to attack
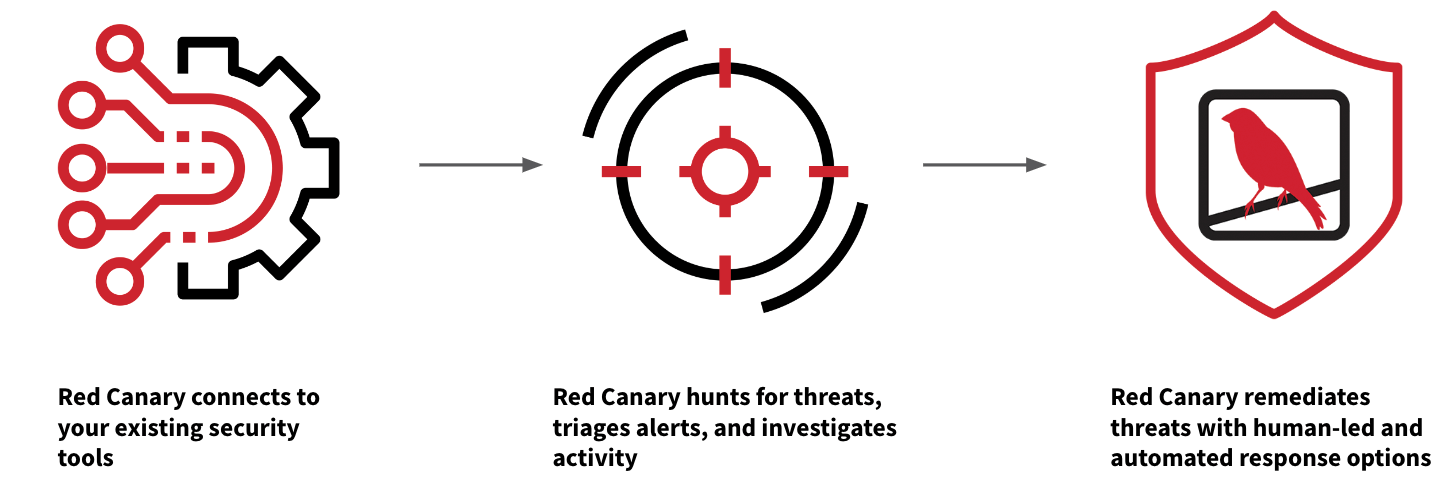
Red Canary Managed Detection and Response (MDR) combines trailblazing security technology and human expertise to detect endpoint and network threats earlier and stop them faster.
- Data is ingested from your current EDR, XDR, SIEM, and network security tools.
- Thousands of behavior-based detections and proprietary threat intelligence are applied to hunt for suspicious activity.
- Our team of experts investigates activity, eliminates noise, and correlates events from disparate sources.
- View investigations in a unified timeline, written in clear language with all the necessary context, making it easy to understand the root cause and scope of a threat.
- Take action with our combination of automated and human-led response capabilities.
learn about red canary mdr
Red Canary Managed Detection and Response (MDR)
Guides & Overviews
Red Canary Managed Detection & Response Overview
Readiness Exercises
Security Integrations
Guides & Overviews
Red Canary 2023 Threat Detection Report
Blog
Case Studies
Seeking an Ally to Accelerate Incident Response
Guides & Overviews
Top 5 endpoint and network security best practices