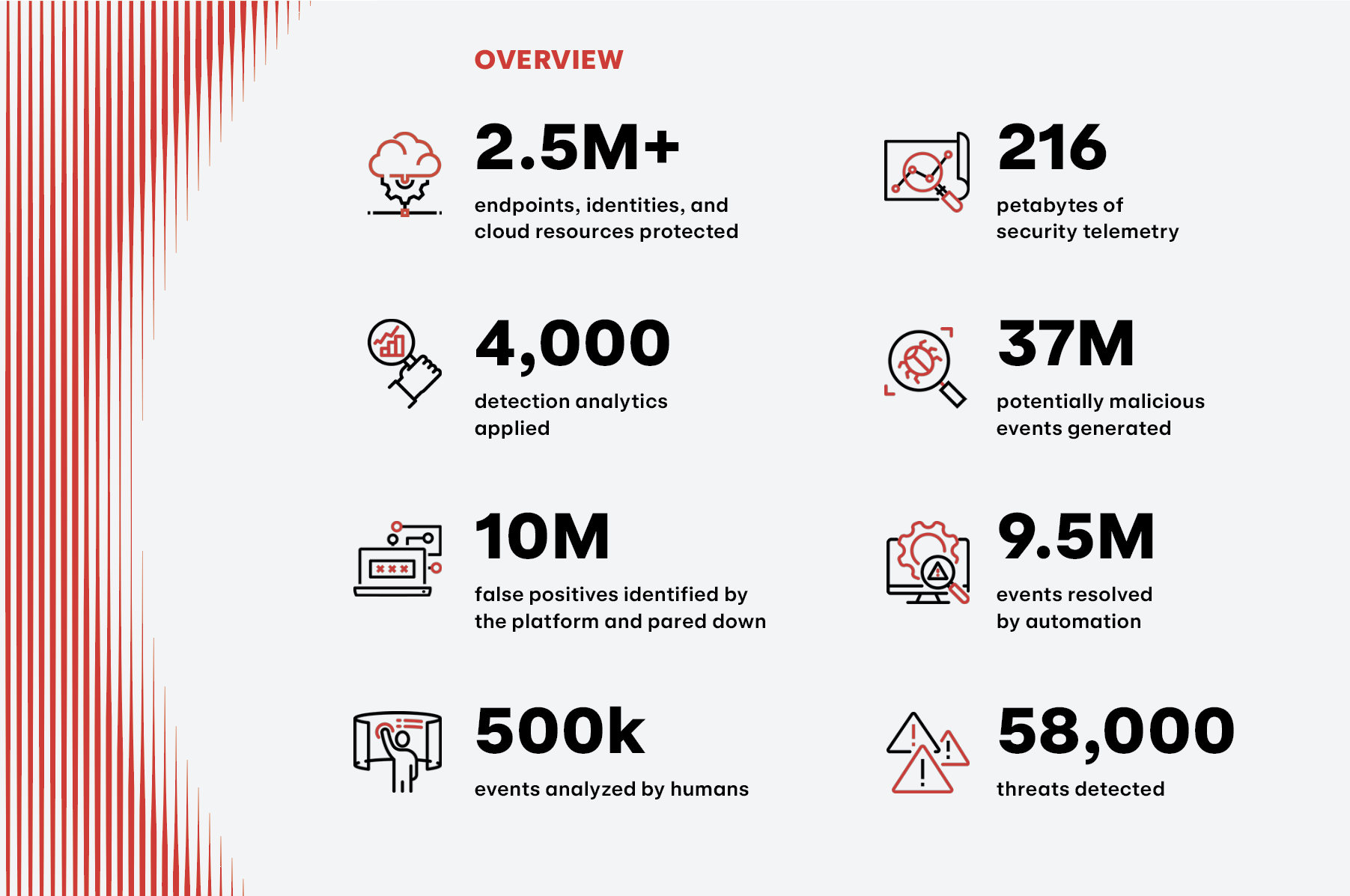
The 2024 Threat Detection Report is here, bringing you and your team actionable insights into the year’s most prevalent security trends, threats, and MITRE ATT&CK® techniques. Our sixth annual retrospective presents an in-depth analysis of nearly 60,000 threats detected across our more than 1,000 customers’ endpoints, networks, cloud infrastructure, identities, and SaaS applications over the past year. This report provides you with a comprehensive view of this threat landscape, along with practical guidance on detection, testing, prevention, and mitigation.
Key findings
As the technology that we rely on to conduct business continues to evolve, so do the threats that we face. Here are some of our key findings:
- Everyone is migrating to the cloud, including bad guys: Cloud Accounts was the fourth most prevalent ATT&CK technique we detected this year, increasing 15-fold in detection volume and affecting three times as many customers as last year.
- Despite a spate of new CVEs, humans remained the primary vulnerability that adversaries took advantage of in 2023. Adversaries used compromised identities to access cloud service APIs, execute payroll fraud with email forwarding rules, launch ransomware attacks, and more.
- While both defenders and cybercriminals have discovered use cases for generative artificial intelligence (GenAI), we see defenders as having the edge.
- Container technology is omnipresent, and it’s as important as ever to secure your Linux systems to prevent adversaries from escaping to host systems.
- Mac threats are no myth–this year we saw more stealer activity on macOS environments than ever, along with instances of reflective code loading and AppleScript abuse.
- Our new industry analysis showcases how adversaries reliably leverage the same small set of 10-20 techniques against organizations, regardless of their sector or industry.
We also check back on the timeless threats and techniques that are prevalent year-after-year, explore emerging ones that are worth keeping an eye on, and introduce two new free tools that security teams can start using immediately.
Trends
Since its inception six years ago, The Threat Detection Report has been anchored by data-driven insights into the most prevalent adversary behaviors we witness on a daily basis. The Trends section allows us to zoom out from our top 10 lists to highlight developments in adversary tradecraft and other patterns that we anticipate making waves in the coming year.
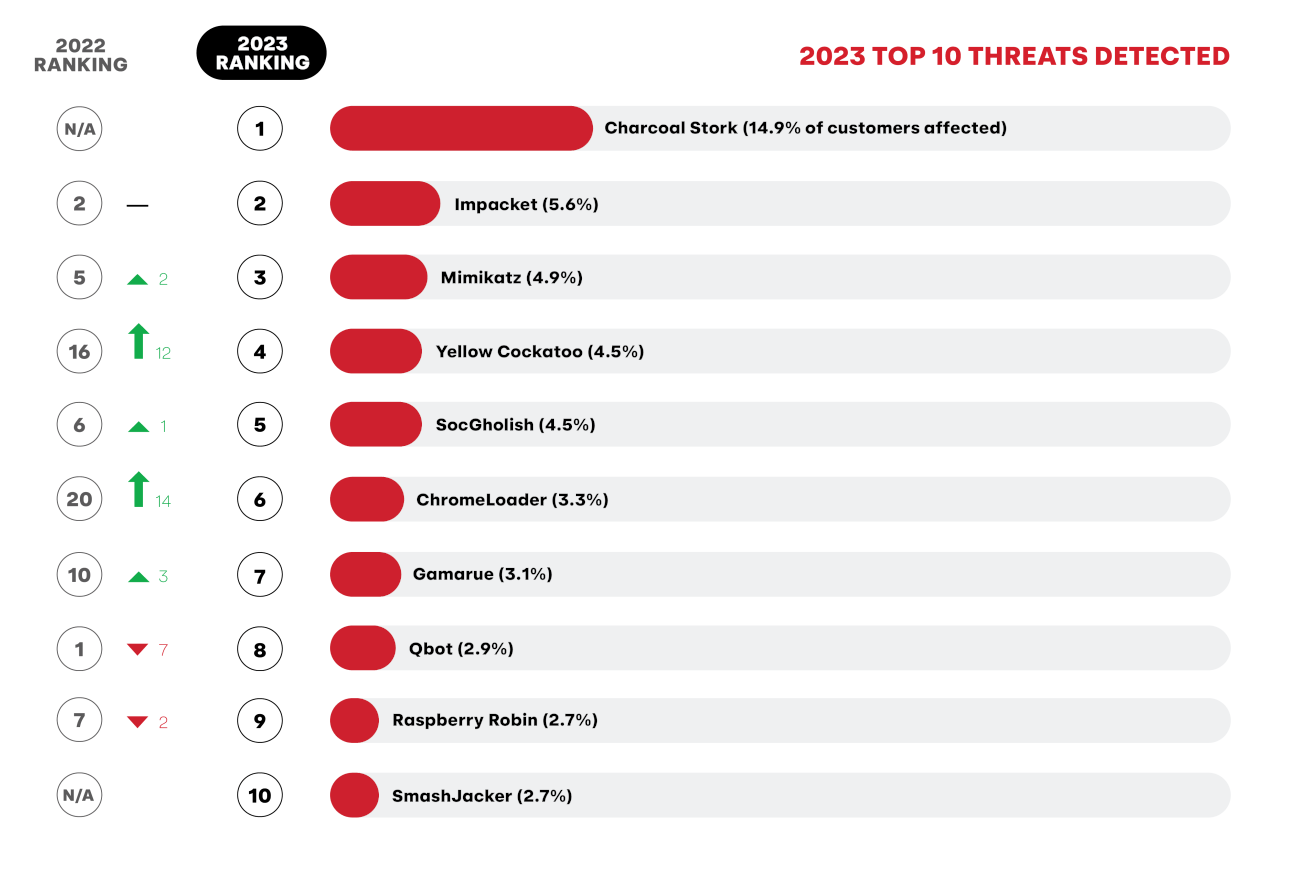
Threats
Often dismissed, malvertising threats can deliver payloads far more serious than adware, as exemplified by the Red Canary-named Charcoal Stork, our most prevalent threat of the year, and related malware ChromeLoader and SmashJacker.
Notably absent from this year’s top 10 is the command and control (C2) framework Cobalt Strike, a mainstay that was disrupted by a coalition of vendors and law enforcement in a effort to take down certain ransomware operations.
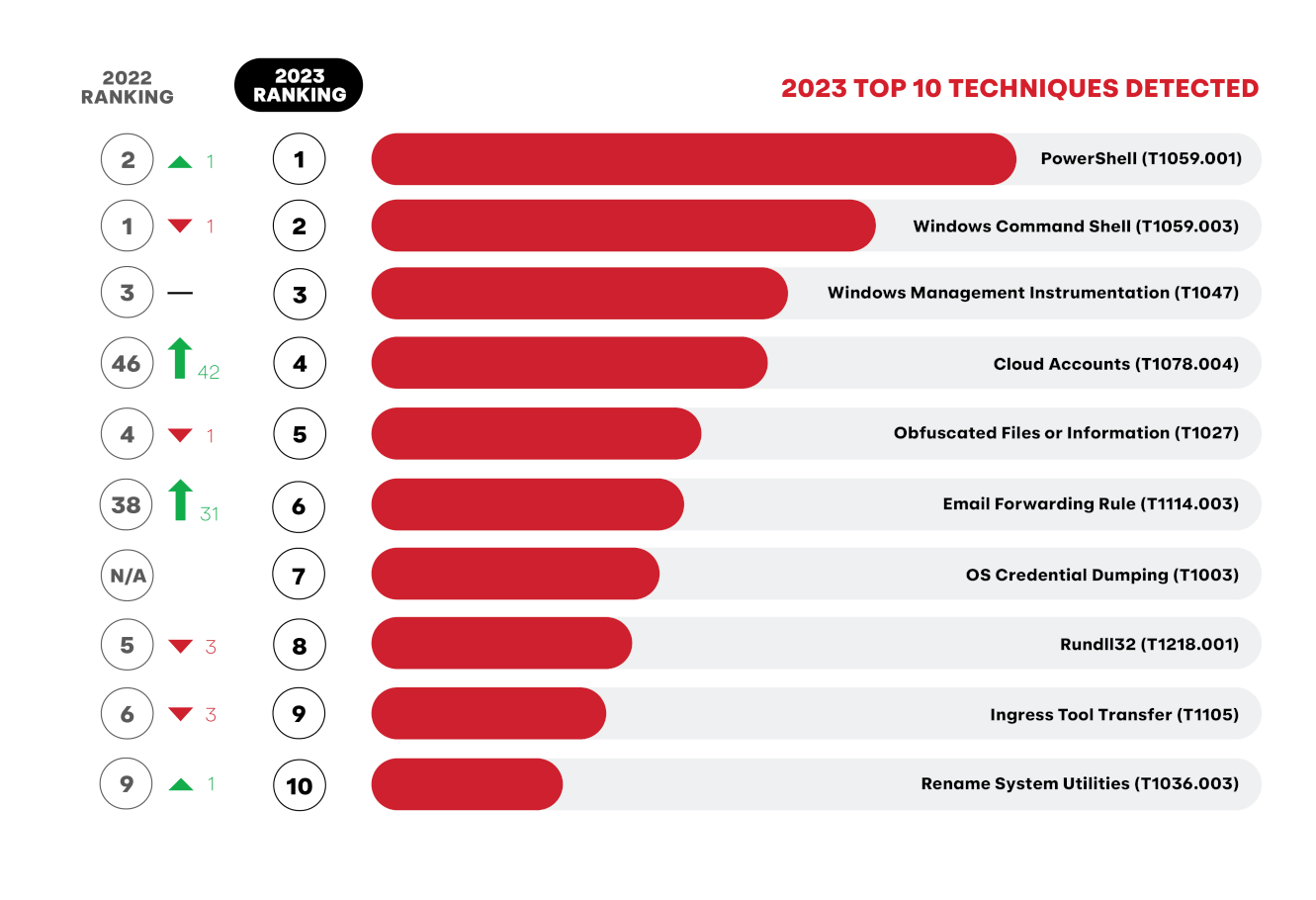
Techniques
Forecasted for years, cloud-based attacks are no longer outliers in our data. Cloud Accounts and Email Forwarding Rule make their top 10 debuts alongside the usual suspects like PowerShell and Windows Command Shell.
We’ve also featured five additional ATT&CK techniques to give you insight into emerging tradecraft and our research on macOS, Linux, containers, Windows installer packages, and more.
Get started
The Threat Detection Report is both a timely read and an evergreen resource that you can refer to throughout the year. The web version of the report includes even more technical details into visibility, collection, detection and testing.
If you’re intimidated by the page count, don’t fret–the Executive Summary provides high-level takeaways for security leaders and any one else who’s short on time. To kick things off, we encourage you to flip through the report, share it with your team, and start a discussion about which threats and techniques should be prioritized in your organization’s threat model.