The day the network went silent: a (cautionary) tale
It was a seemingly ordinary Tuesday morning at Birdhouse Pharma, an innovative mid-sized pharmaceutical company preparing for the launch of its groundbreaking new treatment. The entire organization was abuzz as researchers exchanged final notes, operations teams prepped distribution logistics, and marketing partners mobilized for an aggressive campaign. The culmination of years of effort was just days away.
That’s when the first email arrived; sent to the company’s security team. A researcher was locked out of critical lab systems, and attempts to troubleshoot produced only error codes. Within minutes, more employees complained of inaccessible files. Soon after, the IT team uncovered encrypted data strewn across servers and the chilling ransom message: Pay 500 Bitcoin to unlock operations.
The chaos was palpable. Executives scrambled in emergency meetings with technical, legal, and PR teams. Partners started asking questions. Worst of all, Birdhouse Pharma’s vendors—including one responsible for manufacturing components for the treatment—reported nearly identical disruptions, leading to delays across their shared supply chain.
Adversaries had penetrated Birdhouse Pharma through a third-party contractor via a spear phishing attack. Despite basic safeguards, it quickly became evident how inadequate their incident response and readiness plans were. Their team lacked clarity on roles and response protocols, their systems couldn’t identify the scope of the attack fast enough, and their cyber insurance provider began raising questions about policy exclusions.
The eventual recovery was costly, taking months and burning through goodwill with partners and customers alike. Birdhouse Pharma learned a painful lesson: cyber resilience isn’t optional; it is critical.
Balancing AI with human intervention when responding to incidents
As this hypothetical scenario highlights, in today’s hyper-connected landscape, cyber attacks are no longer isolated disruptions; they can become business-wide disasters with the power to compromise operations, market cap, reputation, and trust. Whether the goal be extortion, exposing healthcare data, stealing intellectual property, or crippling entire supply chains, adversaries are exploiting vulnerabilities faster than organizations can adapt. So what does this all mean for you?
Effective incident response isn’t just a technical challenge, it’s a business imperative.
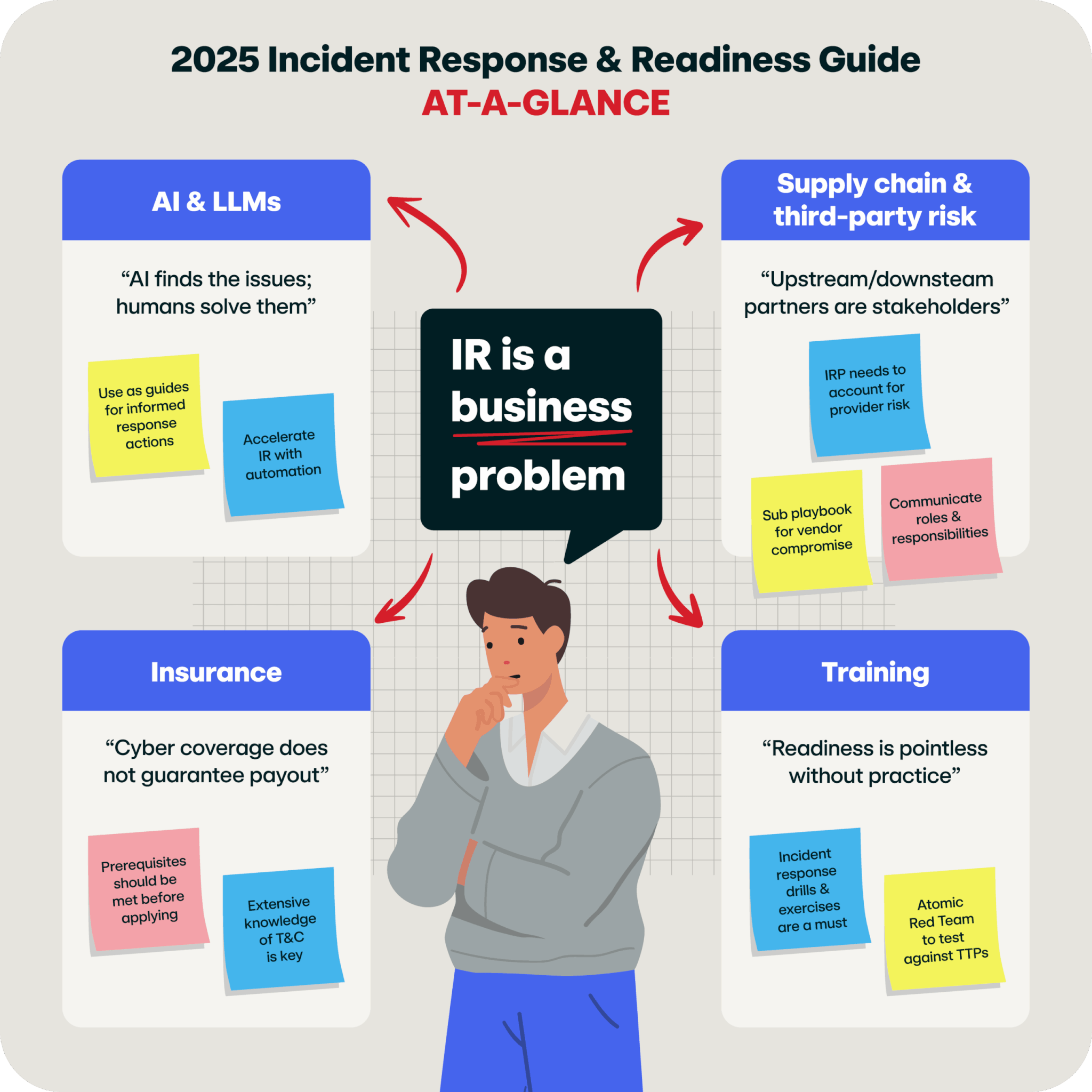
Welcome to 2025, an era in which artificial intelligence (AI) and large language models (LLMs) are revolutionizing cybersecurity. These tools are empowering defenders to respond to incidents with unprecedented speed and precision, analyzing sprawling datasets, detecting emerging threats, and streamlining communications during chaotic events. While AI is undoubtedly a transformative ally, over-reliance on automation and adversary exploitation of AI systems highlight the need for balanced human oversight.
Beyond just technology, organizations must consider preparedness by factoring in risks from increasingly complex supply chains, third-party vendor relationships, and cloud ecosystems. The growing influence of cyber insurance in incident recovery further complicates the landscape, emphasizing the importance of proactive planning, resilient frameworks, documentation and validation of preventive measures, and clear responsibility models.
That’s where our newly updated Incident Response and Readiness Guide comes in. It delves deeper into evolving threats, the importance of staying proactive, and offers up actionable strategies to enhance your organization’s readiness. From leveraging AI-driven tools to building robust partnerships and response processes, this guide provides the strategic insights every defender needs to know to fortify your network, protect critical assets, and instill confidence in stakeholders.