Each month, the Intel team provides Red Canary customers with an analysis of trending, emerging, or otherwise important threats that we’ve encountered in confirmed threat detections, intelligence reporting, and elsewhere over the preceding month. We call this report our “Intelligence Insights” and share a public version of it with the broader infosec community.
Highlights
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Here’s how the numbers shook out for October 2022:
| Last month's rank | Threat name | Threat description |
|---|---|---|
| Last month's rank: ➡ 1 | Threat name: | Threat description : Banking trojan focused on stealing user data and banking credentials; delivered through phishing, existing Emotet infections, and malicious Windows Installer (MSI) packages |
| Last month's rank: ⬆ 2 | Threat name: | Threat description : Collection of Python classes to construct/manipulate network protocols |
| Last month's rank: ⬆ 3 | Threat name: | Threat description : Open source tool that dumps credentials using various techniques |
| Last month's rank: ⬆ 4 | Threat name: | Threat description : Open source tool used to identify attack paths and relationships in Active Directory |
| Last month's rank: ⬇ 5 | Threat name: | Threat description : Activity cluster using a worm spread by external drives that leverages Windows Installer to download a malicious DLL |
| Last month's rank: ⬆ 6* | Threat name: Zloader | Threat description : Banking trojan with many variants that originally focused on credential theft but in more recent years has delivered pre-ransomware payloads for a number of different ransomware families |
| Last month's rank: ⬆ 6* | Threat name: | Threat description : Malware family associated with ad fraud activity through the distribution of adware applications |
| Last month's rank: ⬆ 8* | Threat name: | Threat description : Malware family used as part of a botnet. Some variants are worms and frequently spread via infected USB drives |
| Last month's rank: ⬆ 8* | Threat name: Metasploit | Threat description : Penetration testing framework with a robust set of tools for exploiting vulnerabilities and executing code on a remote target machine |
| Last month's rank: ⬆ 8* | Threat name: | Threat description : Dropper/downloader that uses compromised WordPress sites to redirect users to adversary infrastructure posing as necessary browser updates to trick users into running malicious code |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Observations on trending threats
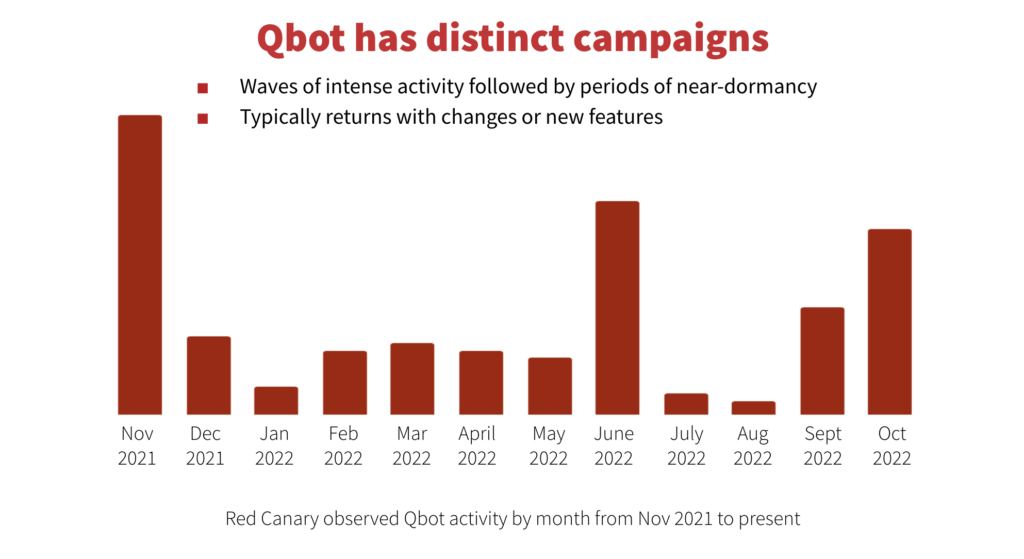
October’s top 10 includes threats that are no stranger to our trending threat list. Qbot claimed the number 1 spot for the second consecutive month. Several threats fell out of the top 10 from September 2022, including Gootloader, Web Companion, RedLine, and PureCrypter.
Qbot’s malicious monologue continues
October was Qbot’s most active month in 2022 at Red Canary. Other researchers have also observed an increase in Qbot activity during the past two months. As we discussed in October’s insight, Qbot historically cycles from very high levels of activity to quiet near-dormancy.
New Qbot campaigns typically kick off with different indicators than previous campaigns, especially the initial phish and early dropper/loader stages. This is likely in an attempt to make Qbot more challenging for defenders to rapidly detect. Earlier Qbot campaigns had relatively stable indicators within the campaign itself. More recently, during the May 2022-June 2022 campaign, we saw Qbot operators begin to make very frequent changes—sometimes daily—to indicators and behaviors. The current campaign has also had significant changes to indicators and delivery methods occur during the campaign itself.
Some key Qbot observables have remained consistent over the years, including:
- Randomly named directories and files created during the installation process. Note that the random names can be strings of alphanumeric characters, numbers, or words.
- Unusual
regsr32.exeandrundll32.exeactivity, including external network connections with no command-line arguments - Reconnaissance commands executed by unusual processes that Qbot has injected into such as
wermgr.exe, to give a recent example
Most recently we have seen Qbot operators continuing to leverage optical disc image ISOs in their delivery methodology, with ISO files dropping a variety of malicious executables. One observed malicious executable file type is JavaScript .js files, which gives us a detection opportunity.
Detection opportunity: JavaScript .js files executing from optical disc image ISOs
The following pseudo-detection analytic identifies .js files executing from drives other than the default C:\ drive. Malware such as Qbot can be introduced through ISOs that contain malicious .js files. It is rare for .js files to execute from a drive other than the default drive. Since this may occur legitimately if the endpoint’s main partition is not on C:\: additional review may be needed to determine if this is malicious behavior.
filetype == (.js)
&&
filepath_does_not_contain == (C:\)
Turning the spotlight on stealers
As seen on previous top 10 lists, we routinely observe stealers like RedLine and Vidar. “Stealer” is an umbrella term used for malware capable of collecting a range of sensitive data, including but not limited to browser information, bank account and credit card numbers, cryptocurrency wallets, system information, and credentials. Historically, stealers have been used in attacks on individuals and smaller organizations, usually with the end goal of collecting the aforementioned sensitive data.
Now the risks associated with stealers are no longer limited to losing information from a single user or system. Researchers increasingly see adversaries using credentials stolen with these tools as an initial access vector in attacks on enterprise organizations. For example, operators like Lapsus$ have used stealers as a means to gain credentials for initial enterprise access. It’s also worth noting that compromises on an individual’s personal accounts can have ramifications for enterprise security, in cases where individuals use the same password across multiple accounts.
Because several stealers have similar functionality, many of the same detection analytics can be used to identify common malicious behaviors. A common vector for stealer payload delivery will be an EXE or DLL file dropped to disk or injected into another process, regardless of whether delivery is via a loader like PureCrypter, a malicious document, or some other delivery methodology.
Once the stealer executes, it typically looks for other apps that exist on the victim system. This is usually achieved with a combination of measures:
- Querying Windows Registry keys like
HKLM\SOFTWARE\[Wow6432Node]\Microsoft\Windows\CurrentVersion\Uninstall - Enumerating files on disk searching for known structures like
servers.xmlfor FileZilla - Querying additional system information including
- Hardware details like CPU/RAM/HDD space
- Geolocation and network configuration
- Time zone, system language, and locale details
- Current username
Some stealers, especially stealer-as-a-service malware like Raccoon and RedLine, will also create a network connection to a command and control (C2) system to download configuration details.
Detection opportunity: Processes making outbound network connections to Telegram shortened domains t[.]me or tttttt[.]me
The following pseudo-detection analytic identifies unexpected processes making outbound network connections to the Telegram shortened domains t[.]me or tttttt[.]me. Telegram has been used for command and control (C2) by various stealers including RedLine, Vidar, and Raccoon. Since legitimate applications like Windows browsers, Zscaler, and others have been observed using t[.]me, additional investigation of the executing binary’s reputation is key.
process_does_not_equal == (windows_browsers, zsatunnel.exe, telegram.exe, tg.exe, *.exe)
&&
Netconn_includes == (t[.]me, tttttt[.]me)
Note: * is a placeholder for binaries associated with legitimate use of shortened Telegram domains in your specific environment