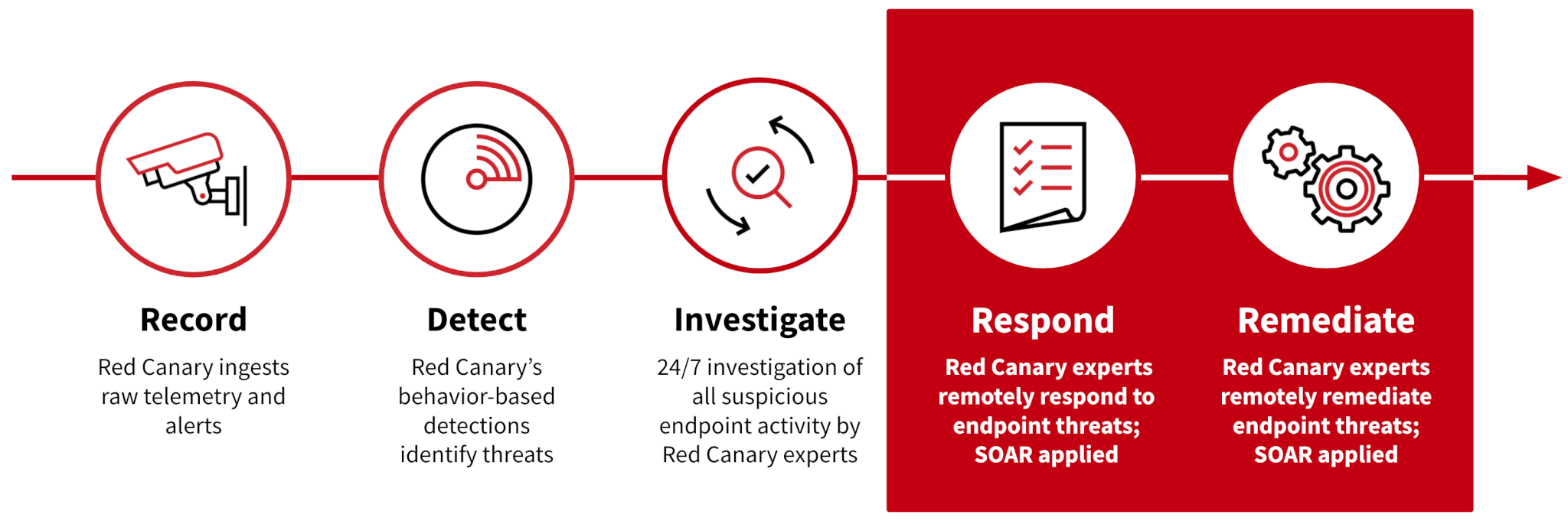
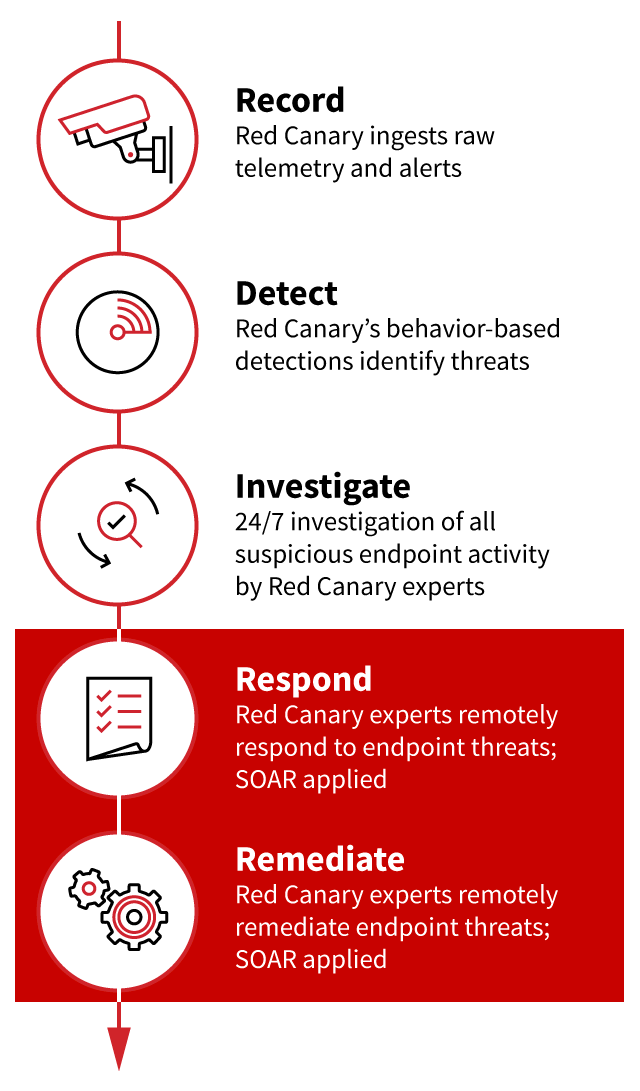
Effective cyber threat response requires specific skills and knowledge, both deployed as fast as possible. When teams are stretched thin, though, one or more of the necessary pieces isn’t in place.
Small teams often don’t have the skills or knowledge necessary to respond with confidence.
Larger teams consumed with other priorities often aren’t ready to respond to threats immediately and with precision.
At Red Canary, we obsess over minimizing the time it takes for our customers to detect and respond to threats. That’s why we are excited to announce Active Remediation, a service in which our experts remediate cyber threats on your endpoints 24/7, using a combination of hands-on-keyboard expertise and automation.
How it works
- When Red Canary confirms a threat on your endpoints, we immediately run automated responses that are customized for your environment.
- Our detection engineers—the experts who confirmed the threat—escalate the detection to our Incident Handling Team, who begin hands-on cyber remediation of the endpoint threats.
- We log all response actions that we take on your endpoints so that when we’re done remediating, you can have full visibility into what we did and why we did it.
- We let you know when we’ve completed remediation, and our Incident Handling Team is available to walk you through the threat and remediation timeline in as much detail as you’d like.
Benefits
- Add expertise to your team
Let our experts go from guiding to doing. With Active Remediation, your Incident Handling Team gets to work the moment a detection is confirmed. Every second counts when responding to an incident, and Active Remediation ensures that our experts start containing and remediating on your endpoints as soon as possible. - Free up your staff
We take even more off your team’s plate with Active Remediation. Which means that you and your staff get even more time to focus on more forward-looking, strategic projects. This translates to more time and more budget that you can allocate from hiring to other efforts. - Rest assured that your endpoints are in the best hands
Sleep easier knowing that the experts in endpoint security have you covered 24/7 across the full endpoint threat lifecycle. We give you full transparency into all actions we take on your endpoints so that you can audit everything we do. And we work with you post-incident to help you make sure similar incidents don’t happen again in the future.
When is it available?
Active Remediation is currently available for organizations using Microsoft, CrowdStrike, Carbon Black, Palo Alto Networks, or SentinelOne as their EDR provider.
Do you have any references?
Learn how Schumacher Homes reduced its mean-time-to-respond dramatically with Active Remediation. You can also check out the Active Remediation infographic to see more.
Effective cyber threat response requires specific skills and knowledge, both deployed as fast as possible. When teams are stretched thin, though, one or more of the necessary pieces isn’t in place.
Small teams often don’t have the skills or knowledge necessary to respond with confidence.
Larger teams consumed with other priorities often aren’t ready to respond to threats immediately and with precision.
At Red Canary, we obsess over minimizing the time it takes for our customers to detect and respond to threats. That’s why we are excited to announce Active Remediation, a service in which our experts remediate cyber threats on your endpoints 24/7, using a combination of hands-on-keyboard expertise and automation.
How it works
- When Red Canary confirms a threat on your endpoints, we immediately run automated responses that are customized for your environment.
- Our detection engineers—the experts who confirmed the threat—escalate the detection to our Incident Handling Team, who begin hands-on cyber remediation of the endpoint threats.
- We log all response actions that we take on your endpoints so that when we’re done remediating, you can have full visibility into what we did and why we did it.
- We let you know when we’ve completed remediation, and our Incident Handling Team is available to walk you through the threat and remediation timeline in as much detail as you’d like.
Benefits
- Add expertise to your team
Let our experts go from guiding to doing. With Active Remediation, your Incident Handling Team gets to work the moment a detection is confirmed. Every second counts when responding to an incident, and Active Remediation ensures that our experts start containing and remediating on your endpoints as soon as possible. - Free up your staff
We take even more off your team’s plate with Active Remediation. Which means that you and your staff get even more time to focus on more forward-looking, strategic projects. This translates to more time and more budget that you can allocate from hiring to other efforts. - Rest assured that your endpoints are in the best hands
Sleep easier knowing that the experts in endpoint security have you covered 24/7 across the full endpoint threat lifecycle. We give you full transparency into all actions we take on your endpoints so that you can audit everything we do. And we work with you post-incident to help you make sure similar incidents don’t happen again in the future.
When is it available?
Active Remediation is currently available for organizations using Microsoft, CrowdStrike, Carbon Black, or SentinelOne as their EDR provider.
Do you have any references?
Learn how Schumacher Homes reduced its mean-time-to-respond dramatically with Active Remediation. You can also check out the Active Remediation infographic to see more.
ACTIVE REMEDIATION
Be the first to know about support for additional EDR providers.
Head back to the blog