No one really plans to fail, do they? Could you imagine a scenario where all of your hardwork and effort to build a comprehensive incident response plan (IRP) and readiness strategy fails during a critical moment? If you have not thought about all the potential gaps or failures in your IRP, it may be time to conduct a premortem analysis.
Any criminal justice or murder mystery aficionado is familiar with the postmortem examination, during which the medical examiner attempts to determine a victim’s cause and manner of death. This practice has been adapted by other disciplines in which a detailed investigation is needed after an accident or event. For example, authorities will take painstaking measures to ensure that airplane crashes are properly investigated so that future occurrences are reduced.
In much the same way, detection and response professionals will often conduct a postmortem analysis of a security incident or training exercise as part of the post-incident activity. This is an excellent practice, but it does have one disadvantage: Visibility into gaps or failures are only identified in the scope of the incident or exercise itself. There is no doubt this is absolutely a valuable practice and an important part of post-incident activities, however, it can lead to a false sense of security as not all potential failures or gaps have been explored. A useful tool for identifying potential IRP gaps or failures before an incident occurs is the premortem analysis.
What is a premortem?
A premortem is an analysis tool in which a team—in this case made up of IR stakeholders—starts with the assumption that the plan has failed and then ascertains the likely causes of that failure. While it functions in a similar way to a postmortem analysis, the significant difference between the two is that the premortem analysis works backwards to identify gaps by preemptively considering scenarios that could occur. From here, organizations can analyze and identify the specific elements or conditions that caused the failure and adjust the plan or execution of incident response activities as needed.
The concept of the premortem analysis was developed by Dr. Gary Klein, a cognitive psychologist and author. Klein developed this approach based on research that indicated organizations often become overconfident in their planning and an inability to identify potential failure points. What was needed was a process where conceivable failures in the plan can be identified and addressed.
Premortem workup
The process for conducting a premortem analysis is straightforward and not at all time consuming. Organizations can conduct a session in 60-90 minutes, without the need for much in the way of preparation. An IRP premortem is composed of six steps:
Step 1
Familiarize your cyber incident response team (CIRT) and other stakeholders with the plan. Give the team some time to read over a draft copy of the IRP before moving on to Step 2.
Step 2
Bring the team together. This should involve individuals who have a key role or function during the entire lifecycle of an incident. This includes not only technical personnel but other members such as corporate counsel and marketing. It is best to hold this session in a location where the entire team can collaborate. In the event that remote team members are involved in response activities, a virtual meeting will suffice.
Each participant should be provided note-taking material such as notepads or sticky notes. Once the team is appropriately briefed on the intention, the facilitator starts the process by establishing a scenario in which the IRP has been a spectacular failure. As a result, an incident has led to a catastrophic impact on the organization.
Note: The facilitator does not need to be specific with outlining the failure. For example, a simple statement that indicates the plan has failed and the organization has experienced significant downtime and resulting impact. The overall intent is to get to specifics in Step 3.
Step 3
With the scenario set, each member will identify why the plan has failed. For example, a participant may identify that a key individual was not available since they often go hiking on the weekends and were not able to assist. Each participant writes down their reasons on the sticky notes. The facilitator should give approximately 5 minutes for this step with a 30-second warning before wrapping it up.
Step 4
Now each team member takes a turn and tells the group one of their reasons that the plan failed. The facilitator records these on a whiteboard or other medium where everyone can see. Each participant should provide a reason before the second round. Any duplicates can be consolidated. This usually takes two or three rounds to complete.
Step 5
With Step 4 completed, the team now has a detailed list of reasons why the plan would fail. Next, for each of these reasons, the team briefly discusses the merits of them all. Some are easily dismissed but others may have real merit. For those teams centrally located, the reasons can be placed onto a board for everyone to see. For remote collaboration platforms, a simple Google Doc with each failure point written out is helpful for all participants.
Step 6
Rank those reasons found in Step 5. If you have a dozen or less, you can evaluate each one. You want to focus on those top reasons for failure rather than trying to address 30 or so. Each member of the team then takes a turn coming up with solutions or actions that can be taken to address the reasons for plan failure.
From here, two courses of action can be taken:
- Clear failures in the plan can be remediated immediately. For example, not having backup people for key IR roles can be remedied rather quickly.
- It may be enough to simply observe and recognize—without taking action—that certain conditions may lead to failure. For example, understanding that rushing restoration of systems may be detrimental without a clear indication that all adversarial C2 has been removed.
Premortem execution
The premortem execution takes only about 60-90 minutes to complete. The following are some general rules to keep in mind:
- Most IRPs have gaps: This exercise is designed specifically to suss out those gaps and correct them where possible.
- Keep plan failures realistic: When you start getting into fantasy, stop and come back to reality. It is fine to consider a failure such as not having access to the network colocation facility on a Sunday morning because the on-call overslept, but when you start talking about meteor strike or zombie apocalypse, you have gone too far.
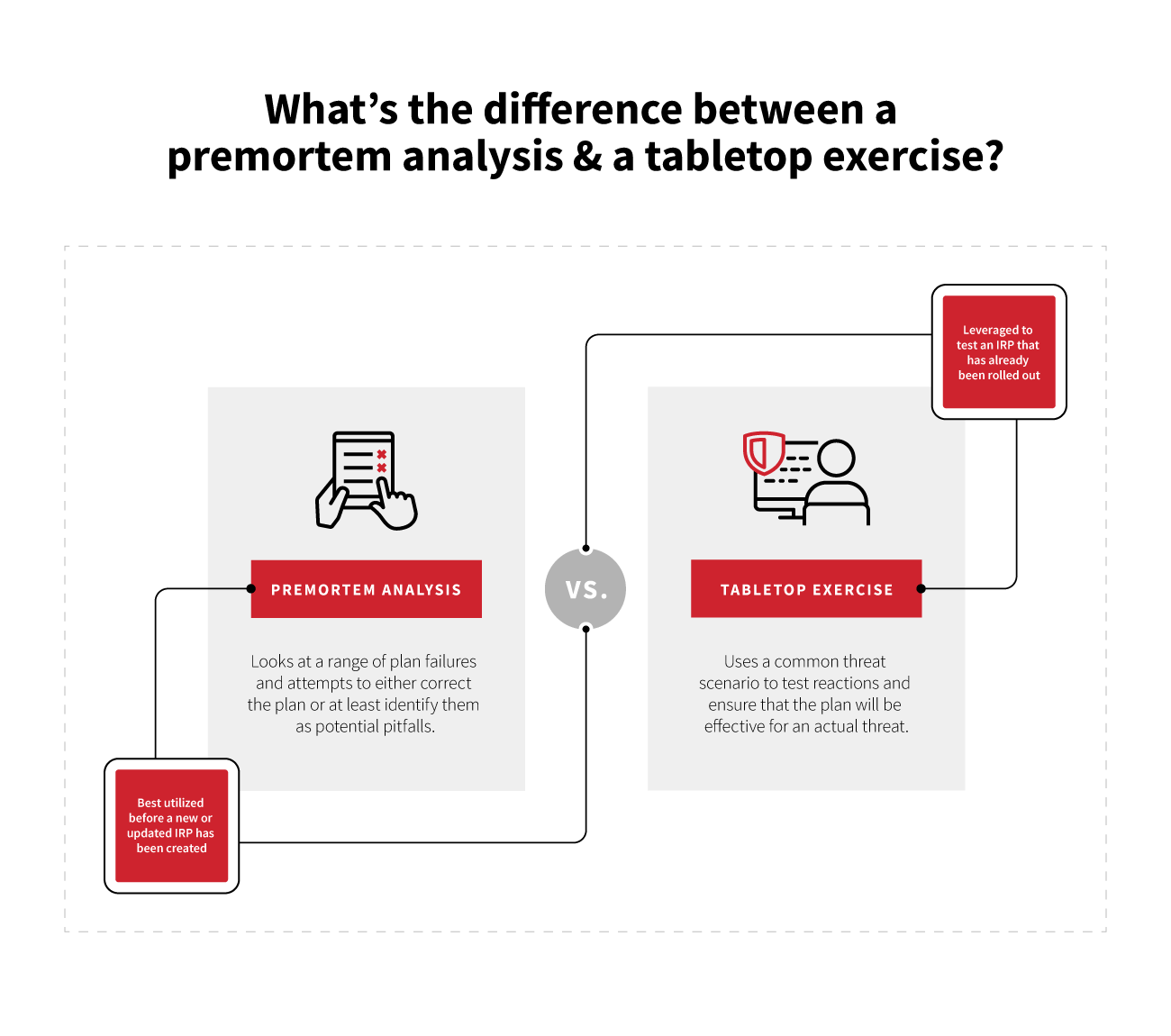
- A premortem analysis is != (not equal to) a tabletop exercise: The premortem looks at a range of plan failures and attempts to either correct the plan or at least identify them as potential pitfalls. A tabletop exercise uses a common threat scenario to test reactions and ensure that the plan will be effective for an actual threat. They both have their place in an overall readiness perspective, but the premortem is best used before a new or updated IRP has been created.
A premortem analysis is a quick way to gain insight into the potential gaps and failure points of your IRP. By evaluating additional perspectives from the team in a structured manner, the team gains an opportunity to improve upon the plan along with gaining a greater amount of confidence in the ability to respond to an incident.