Today’s threat landscape, characterized by the rapid growth of sophisticated threats, is creating a widening security gap. And unfortunately, traditional security operations center (SOC) strategies simply can’t keep up, leaving organizations scrambling to strengthen their defenses and scale their teams amid talent shortages and skills gaps. But the good news: adopting an intelligence-led mindset and applying foundational, tested, and understood principles of product management can help you bridge this gap.
In the webinar, “Building a modern Security Operations Center,” Red Canary Co-founder and Chief Security Officer Keith McCammon dives into the essential goals of the modern SOC, addresses common challenges facing them, and presents a framework that offers a more effective path forward.
Even if you’re not familiar with the principles of product management, you can learn the basics of how to benefit from this approach by watching the full recording here or exploring the key takeaways below.
Think of your SOC as a product
Every security team faces the same challenge: identifying the most prevalent, impactful threats to their business and prioritizing them effectively.
Security teams—much like product and engineering teams—constantly grapple with balancing the need to implement new security measures in addition to upgrading or fixing what currently exists. To manage these tradeoffs, security teams are tasked with analyzing current trends, prioritizing security risks based on potential impact, and managing stakeholder expectations around security posture.
Just like Keith highlights, the challenges and opportunities faced by security teams mirror those of product teams. Both are under pressure to innovate while also ensuring the stability and core functionally of their respective areas.
Threat intelligence as the “product manager”
Strategically identifying and prioritizing threats is crucial, but challenging. The solution? An intelligence-led approach, with threat intelligence forming the groundwork for informed decision-making.
Threat intelligence helps you understand the threat landscape and develop security strategies that are effective against the real-world threats that matter most to your business. This is similar to how a product manager helps their company understand its customers and develop products that meet their needs. Therefore, you can think of threat intelligence as a product manager, empowering your team to make informed decisions about where to allocate your security resources to make the biggest impact.
As Keith explains, this intelligence-driven approach is the cornerstone of modern security operations.
With an intelligence-driven approach, you can become more proactive in your security strategy. Here’s how it works:
- Start by identifying the most prevalent and impactful threats to your business. Knowing what to look for will help guide you as you seek greater visibility into your environment.
- Focus on implementing controls that offer the most protection for your resources. Again, threat intelligence guides you here—understanding threats helps you choose the most impactful controls.
- Learn from every incident. Itʼs impractical to see and control everything. When responding to incidents, keep an eye toward future optimization by documenting or automating learnings and best practices.
- Continuously iterate and adapt. The threat landscape is constantly evolving, and so too should your security strategy.
Keith expands on steps 3 and 4 in this snippet.
TL;DR: Prevent what you can, be cognizant that things will inevitably slip through the cracks, detect the rest, and most importantly, learn from it all.
Prioritize based on risk assessment
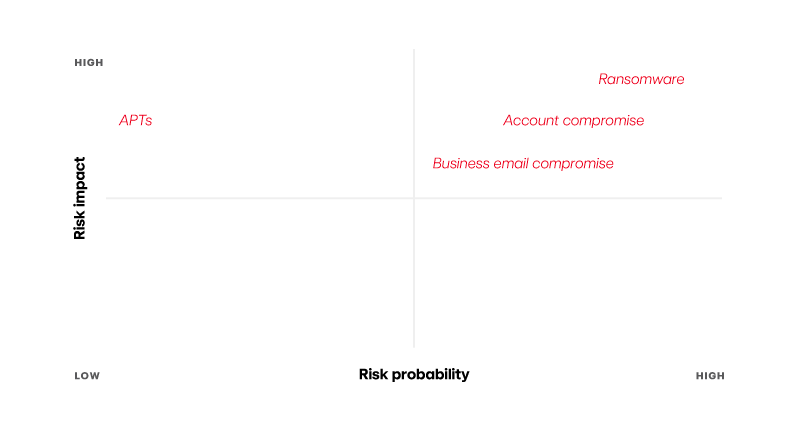
The above mentioned strategy starts with—you guessed it—high-quality threat intelligence. Many practitioners tend to fixate on flashy threats that, in reality, occur much less frequently compared to other, more prevalent ones. Take advanced persistent threats (APT), for example. While APTs pose real problems, they’re statistically uncommon.
The key to a successful intelligence-led strategy lies in prioritizing actionable details. Don’t get distracted by sensational headlines. Instead, focus on understanding the adversary’s modus operandi by asking questions such as:
- Who are they targeting?
- What methods are they using?
- How will these threats manifest?
By asking these essential questions, you can effectively distill the noise and prioritize the most probable, impactful risks. This ensures your time and resources are directed at threats that truly matter.
Sometimes saying “no” is just as important as saying “yes”
Put simply, you can’t do everything. So strategy really is all about picking your battles.
In this clip, Keith explains how using an intelligence-led approach empowers you to weed out low-impact tasks and ruthlessly prioritize the most critical ones.
Focus on what’s unique to your business
In addition to increasingly complex environments, security teams are also feeling the strain of limited resources, funds, and talent. So how do you sharpen your focus to ensure you’re spending your precious time and energy on what truly matters?
The answer lies in a hybrid SOC approach. This means strategically dividing security tasks between your internal team and trusted third-party vendors like managed detection and response (MDR) providers.
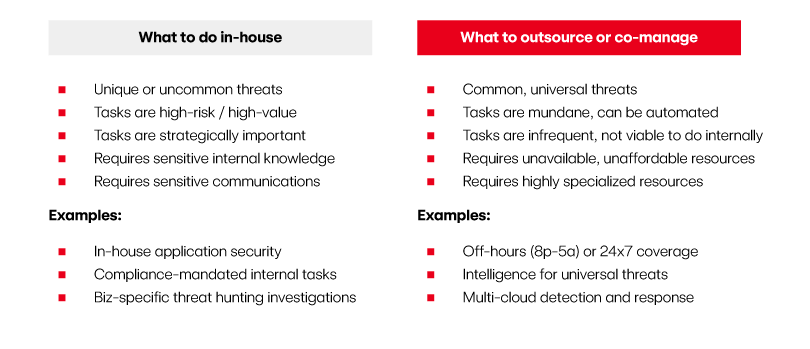
But how do you decide what to keep in-house and what to outsource? Here’s a simple approach: focus on what’s unique to your business. These include tasks that require specialized industry knowledge or sensitive internal communication. Compliance-driven tasks often fall under your in-house purview as well. Everything else—that is, anything that isn’t unique to your business, like common, universal security threats—is likely a viable candidate to outsource or co-manage.
Think of it like this:
Fine tune your hybrid SOC strategy
Ready to get started but unsure of where to begin? We’ve got you. Enter the Cybersecurity Maturity Model, a simple tool developed by Keith himself to help guide preliminary discussions on what to do in-house and what to outsource.
This framework, inspired by Sounil Yu’s Cyber Defense Matrix, helps you assess the maturity, control coverage, and other crucial aspects of your security program. By mapping your security posture, you can quickly visualize gaps in your security program and identify which tasks are:
- Strong candidates for transfer: Our view is that your tech stack (e.g., operating systems, cloud platforms, identity management solutions, etc.) actually defines about 80 percent of your threat model. Third-party vendors can leverage economies of scale and expertise to handle these efficiently. In turn, you benefit from “herd immunity” through their services.
- Best suited for in-house management: The remaining 20 percent of your threat model encompasses industry-specific tasks and those requiring specialized knowledge, like in-house applications. Here’s where you want to focus your team’s time and effort.
We encourage you to go through this exercise with your team to gain clarity on your security posture, see how you might optimize resource allocation, and ultimately, discover a hybrid SOC model that works best for your organization.
Adopt an intelligence-led SOC with Red Canary
By adopting a product manager mindset and leveraging a hybrid SOC model—one that combines the deep and broad capabilities of service providers like Red Canary with the business-specific strengths of your internal staff—you can do more with less, all while narrowing your focus on what’s unique to your business.
At Red Canary, we understand security is a shared journey, regardless of industry or size. We also share your goal of not getting breached. That’s why we act like an extension of your team, taking ownership over domains and security tasks that aren’t unique to your business, so you can stay focused on what is.