A batch of Atomic Red Team™ tests are literally (*counts on fingers*) just four clicks away for users of Microsoft’s enterprise endpoint security platform, Defender for Endpoint. Microsoft added the tests, which we custom-built to emulate prevalent adversary behaviors listed in the 2021 Threat Detection Report, to Defender for Endpoint’s simulations and tutorials portal late last month.
For those of you who don’t already know, Atomic Red Team is an open source library of tests that security teams can use to validate detection logic, generate telemetry, or otherwise emulate adversaries techniques (all of which are mapped to MITRE ATT&CK). While we’re on the topic of explaining things we probably don’t need to, Defender for Endpoint is Microsoft’s comprehensive endpoint security product. It does everything from protection to vulnerability management to IT administration to (importantly) testing—and many things in between.
The marriage of Atomic Red Team and Defender for Endpoint enables security folks to readily validate detective controls, helps newer community entrants develop an eye for what malicious behavior looks like, and offers an approachable entry point into Atomic Red Team—and into testing and validation more generally.
Testing made easy
Our partnership with Microsoft isn’t a new one. We’ve been ingesting telemetry from their various sensors and using it to help our customers detect and respond to threats for years. Defender for Endpoint is intuitive and relatively easy to use. Security and administrative features that once required the extensive and continuous turning of nerd-knobs are now just a slider click away.
Atomic Red Team is also easy to use. If you know how to copy, open a command shell, and paste, then you’re 80 percent of the way there. However, it’s a great big library that can be a little overwhelming. Defender for Endpoint users now have an accessible road map of where to begin with testing.
“How do I get started with Atomic Red Team?”
The first annual Threat Detection Report, which enumerated prevalent ATT&CK techniques, offered a really solid answer to this question: you should run tests associated with the ATT&CK techniques that adversaries are most likely to deploy in your environment. While that first report answered the question of where to get started, it wasn’t until the second annual report that we started to address the question of how to get started. We did this by adding testing sections for each prevalent technique. Readers could then implement the detection guidance in the report and run the tests to see if it worked or not.
Still, copying a dozen scripts from a dozen web pages and pasting them into a dozen command shells is pretty time consuming. Surely there’s an easier way…
Enter Defender for Endpoint
Atomic Red Team’s integration into the tutorials and simulations portal in Defender for Endpoint makes it properly simple for Defender for Endpoint users to run atomic tests. All you have to do is click over to the simulations page, download the simulations file, and execute the batch script.
Let’s talk benefits
The primary (and most obvious) benefit of this integration is that it makes testing and validation more readily available to the great swath of people running Defender for Endpoint. That said, there are two subtler knock-on benefits that are worth exploring.
Expanding the community
Atomic Red Team is incredibly well-known in the adversary emulation space, but there’s no shortage of Defender for Endpoint users who are new to Atomic Red Team and adversary emulation. The incorporation of Atomic Red Team into Defender could be a major boon for industry-wide testing and validation efforts, raising awareness about the library of tests and substantially lowering the barrier of entry for people who are interested in validating their security controls.
We’re hopeful this integration will lead new users to Atomic Red Team—and that those users will help us bolster our coverage by adding new and innovative tests to the library. We’re also excited that Defender for Endpoint users now have a pathway into Atomic Red Team, which boasts a wide breadth of test coverage and a generous, knowledgable community.
Learn what malicious looks like
Speaking purely for myself, I’ve learned a lot about detection and what malicious looks like by executing atomic tests and then examining the telemetry or alerting generated by various security tools. In fact, my admittedly limited experience with Defender for Endpoint has consisted entirely of running atomics on a virtual machine and then examining how it reacts.
More than anything related to operational detection validation, Atomic Red Team has been an educational tool for me. By reading the Markdown files in the Atomic Red Team GitHub repo, I’ve been able to better conceptualize what adversary behaviors look like—and by extension, how you might think about detecting them. By using Invoke-Atomic, I’ve learned a lot of basics about using PowerShell. By putzing around the repo, I’ve learned a lot about GitHub and software development.
To make this about someone other than me, Atomic Red Team is full of opportunities that can help security analysts escape the drudgery of the alert queue and learn about visibility, detection, and more, whether they’re running existing tests or developing new ones.
So what happens if I double click the batch script?
The Atomic Red Team section of the simulations and tutorials portal includes detailed documentation explaining what each of the tests in the batch script does. We’ll summarize that documentation here.
The script in the simulations and tutorials portal is a compilation of tests from the 2021 Threat Detection Report, which simulate the following ATT&CK techniques:
LSASS memory dump
In this test, rundll32.exe will write a full lsass.exe process dump to %windir%\Temp\lsass.dmp using MiniDump.
Rename system utilities
This test executes an encoded PowerShell command while masquerading as notepad.exe, which is a copy of PowerShell placed in the %windir%\Temp\ directory.
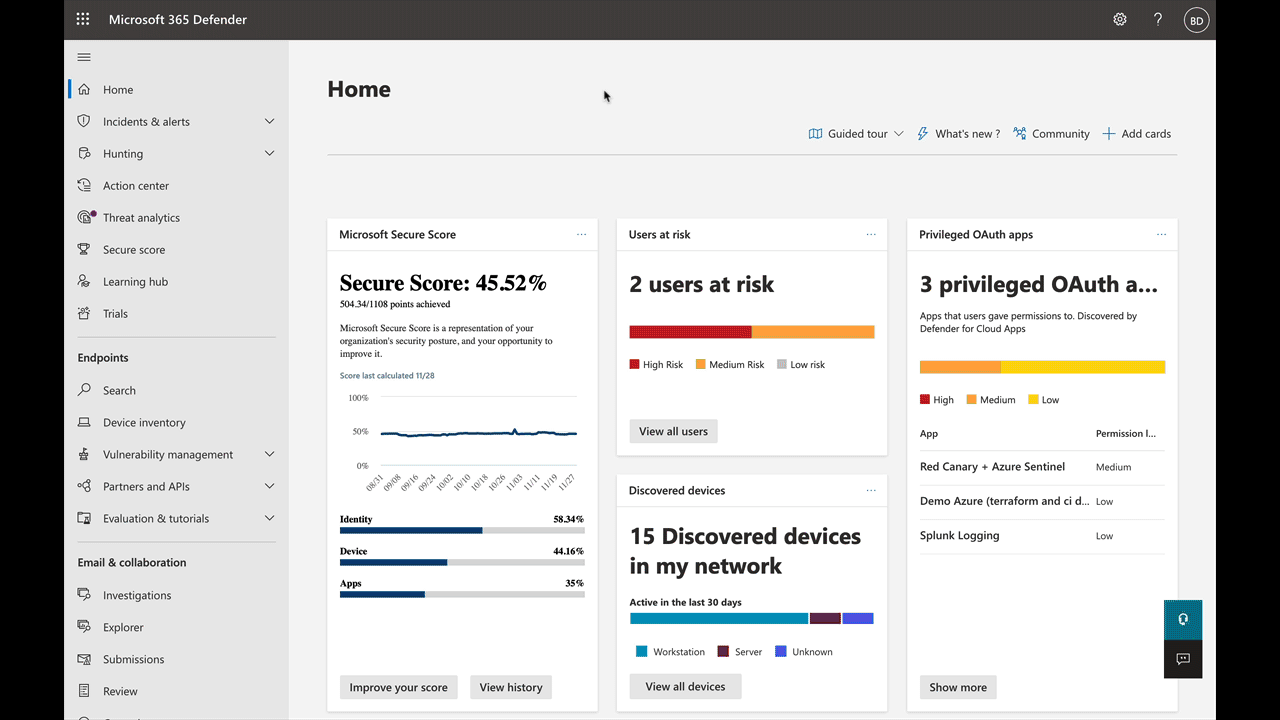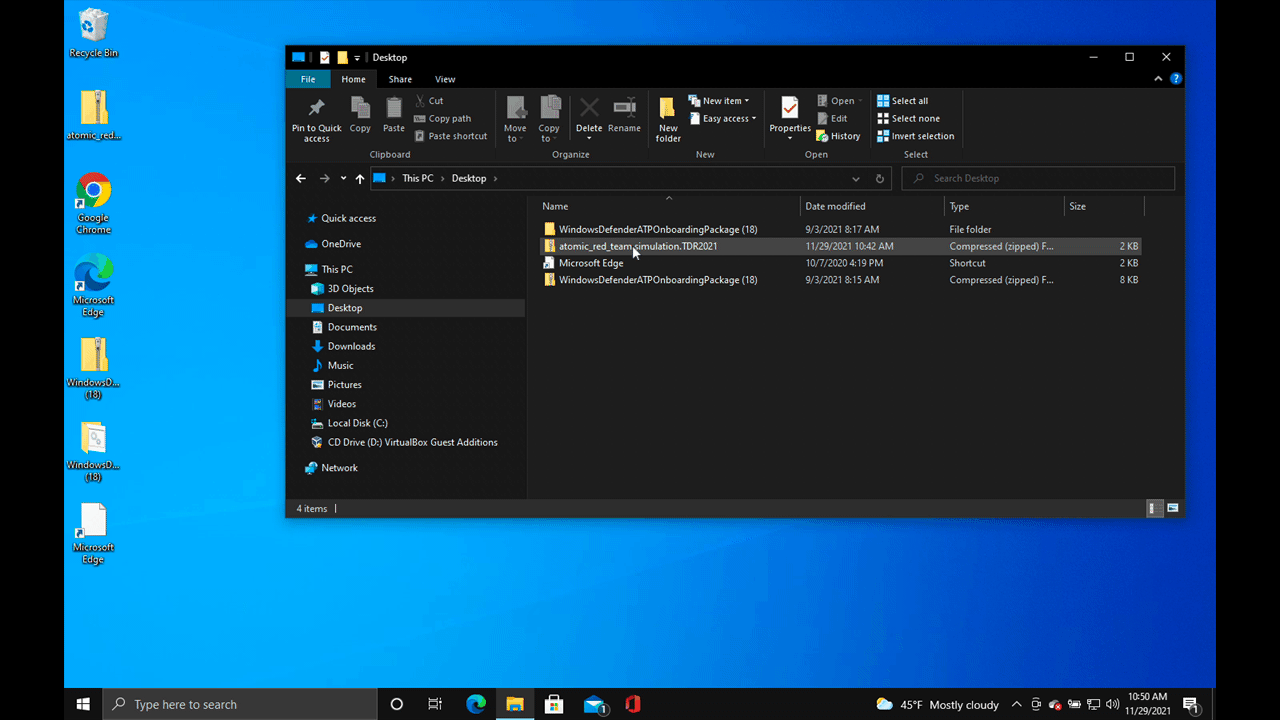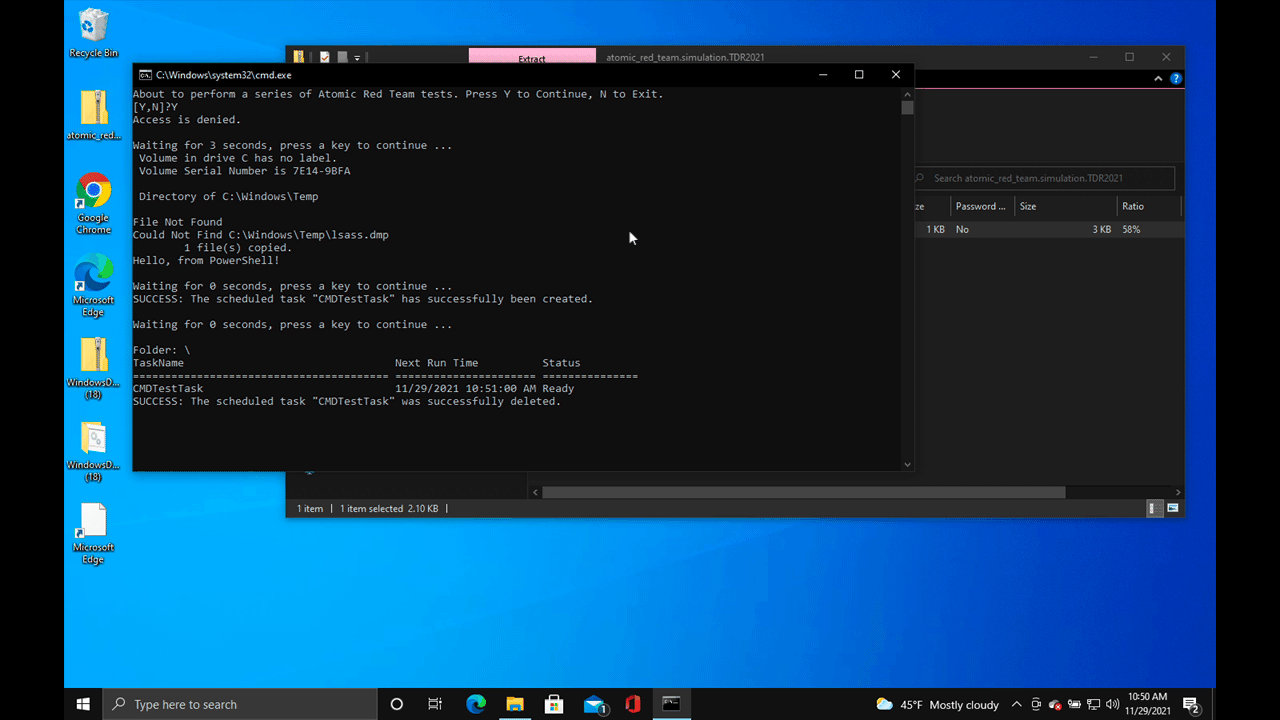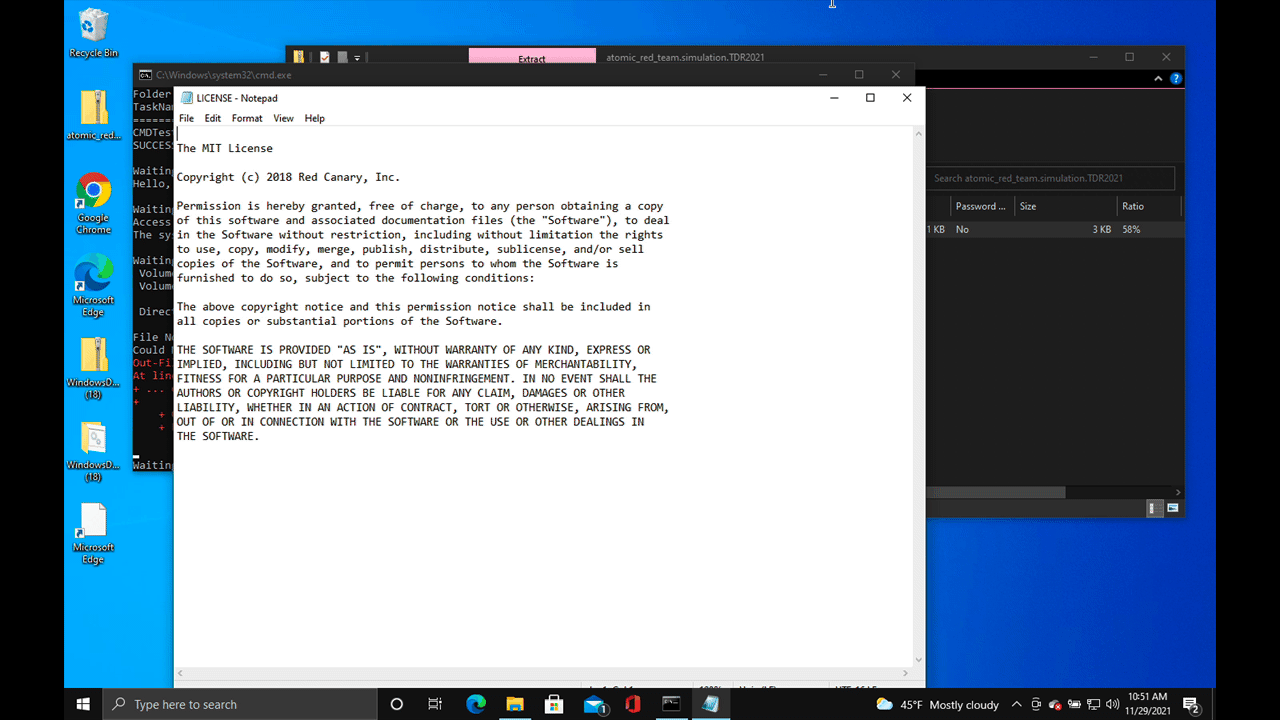
Scheduled task
Running this test will create a scheduled task named CMDTestTask that runs cmd.exe every three minutes. This scheduled task is then deleted.
Process injection
In this test, mavinject.exe will inject vbscript.dll into the running lsass.exe process using dynamic-link library injection.
PowerShell
Running this test should print Hello, from PowerShell! to the terminal via an obfuscated command.
Windows command shell
This test obfuscates cmd.exe, writes Hello, from CMD! to hello.txt, and then displays it.
Ingress tool transfer
This test will use PowerShell to download a file from the public internet to LICENSE.txt and display it with notepad.exe.
Rundll32
In this test, notepad.exe will spawn as a child process of rundll32.exe.
Windows service
The test consists of commands that will install a service named CMDTestService. That service executes cmd.exe, which, in turn, writes the current date to %windir%\Temp\current_date.txt. The service is then deleted.
DEMO
Dive in
We owe a huge thanks to Microsoft for recognizing how important it is for them to empower their users to run tests like these (and others) natively from Defender for Endpoint. Of course, none of this would be possible without the dedication of the Atomic Red Team maintainers and the community of security practitioners who develop and use atomic tests every day. If you have any questions about this integration or Atomic Red Team in general, join our Slack channel and say hi!