Carbon Black Response can be an extremely powerful tool, but many security teams don’t have the internal resources to unlock its true potential. That was the case for Bryan*, the lead infrastructure engineer at a fast-growing technology company. He decided to roll out Cb Response to record all endpoint activity and detect suspicious behavior, but quickly realized his team of three couldn’t manage the massive volume of endpoint data.
“Carbon Black Response collects thousands of events every hour,” Bryan explained. “Analyzing that volume of data across 600+ endpoints would take a huge level of effort and time from our internal team, even with automation. We would have had to hire more people or sacrifice quality.”
Instead, Bryan decided to look for a strategic partner to operationalize Cb Response. “There is a level of impact you can make with automation, but you’ll never get to the scale of a vendor who is seeing all different things in different customers’ environments,” he commented.
Evaluation Criteria
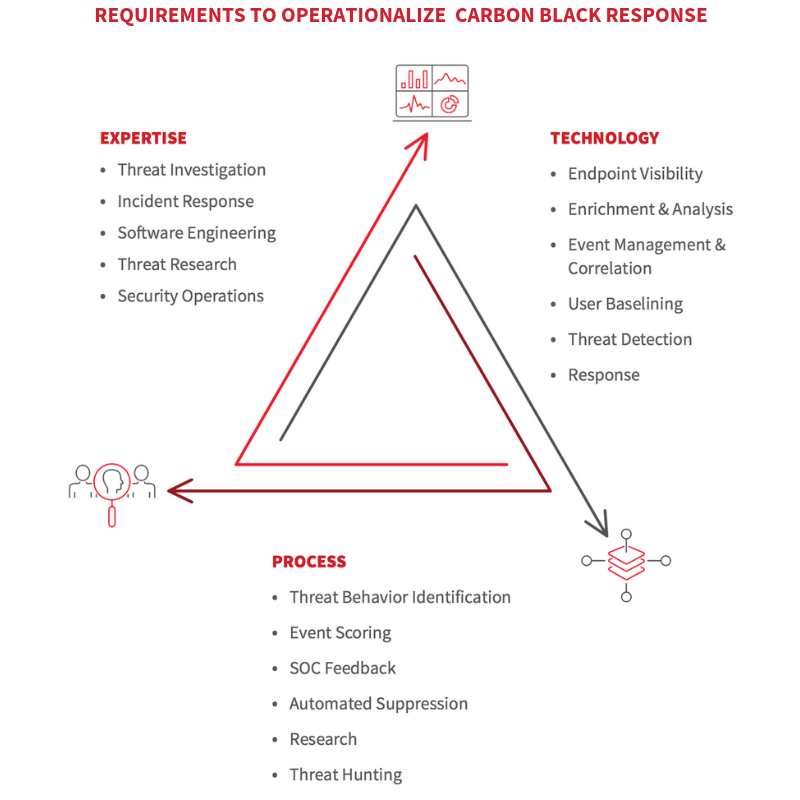
So how do you tell the difference between Cb Response partners when they all seem to promise the same thing? Managed detection and response (MDR) itself is still a fairly new category, with varied and complex nuances. One place to start is by looking at what’s required to operationalize Cb Response.
Download the complete evaluation guide: Finding the Right Strategic Partner to Operationalize Carbon Black Response
Once you’ve mapped out critical areas like threat detection, investigation, and response, you can begin crafting evaluation questions to uncover strengths and weaknesses.
Here are the top 10 questions to ask:
1: Have you moved beyond watchlists and threat intel to detect potential threats?
If the answer to this question is no: RUN. Watchlists are useful for IOC matching and basic behavior identification, but that represents a small percentage of the detection that can be built using Cb Response data. Watchlists are not sufficient to identify the behaviors associated with privilege escalation, defense evasion, credential access, and lateral movement.
2: Are you using Cb Response to triage and investigate alerts?
Cb Response drastically reduces the duration of endpoint investigations. However, a thorough investigation might require an analyst to move between 5 to 25 different processes and supporting information to understand the full picture. This takes time and is inefficient, especially across hundreds of customers.
The most mature providers streamline this process by building their own endpoint analysis and investigation platform. These platforms ingest all of the raw endpoint activity collected by Cb Response and correlate and enrich that data with other valuable pieces of information such as binary signing information, decoded base64 commands, detection criteria information, historical user/endpoint information, and customer environment information.
 3: What is my role in responding to and remediating threats?
3: What is my role in responding to and remediating threats?
Many components impact how quickly an individual threat is remediated, and the scope of features offered by providers varies drastically. Some simply forward alerts and the customer has to interpret what happened. Others will investigate alerts, confirm threats, and then quarantine a compromised endpoint. Some even provide automation capabilities for initial containment and remediation steps. A thorough evaluation of a Cb Response provider requires understanding when the baton passes from the provider to customer, what context is included, and what must happen next.
4: What is the composition of your security team?
Cb Response is different from many other traditional security products that normally can be outsourced to a general MSSP. Detecting and investigating endpoint threats requires a low-level understanding of endpoint operating systems, how threats manifest themselves across operating systems, and the ability to discern good activity from bad activity. MSSPs rarely staff for this skill set, and a network forensics background typically doesn’t translate well to investigations that start on the endpoint. Look for a partner that staffs its security team with experienced analysts, responders, security engineers, threat researchers, and forensic experts who have been using Cb Response as their primary tool for years.
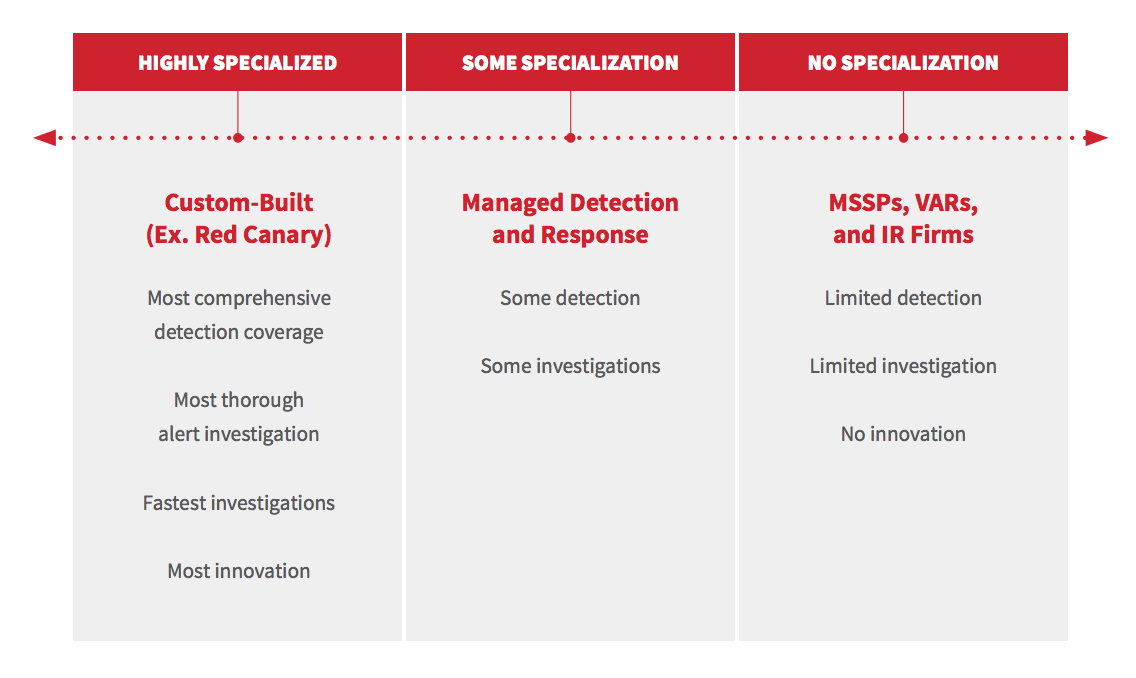
5: How specialized is your Cb Response offering?
There are multiple types of Cb Response providers: MSSPs, VARs, IR firms, and custom-built solutions. For all but custom-built solutions, the provider is trying to balance their Cb Response offering with the other line items they sell. Balancing multiple offerings will impact a provider’s innovation, reliability, and efficacy. The level of specialization impacts everything from detection coverage to investigation speed.
6: How do your reports help me understand the impact of your work on my security program?
Reporting is essential to knowing how well your investments and actions are improving your security. Every provider will have different report sets that are automatically generated as a part of their solution. Will these reports help convey the value of the provider? Will they be instrumental to your security program’s maturation? And ultimately, are you able to make improvements to your program based on the insights gleaned from the provider’s reports?
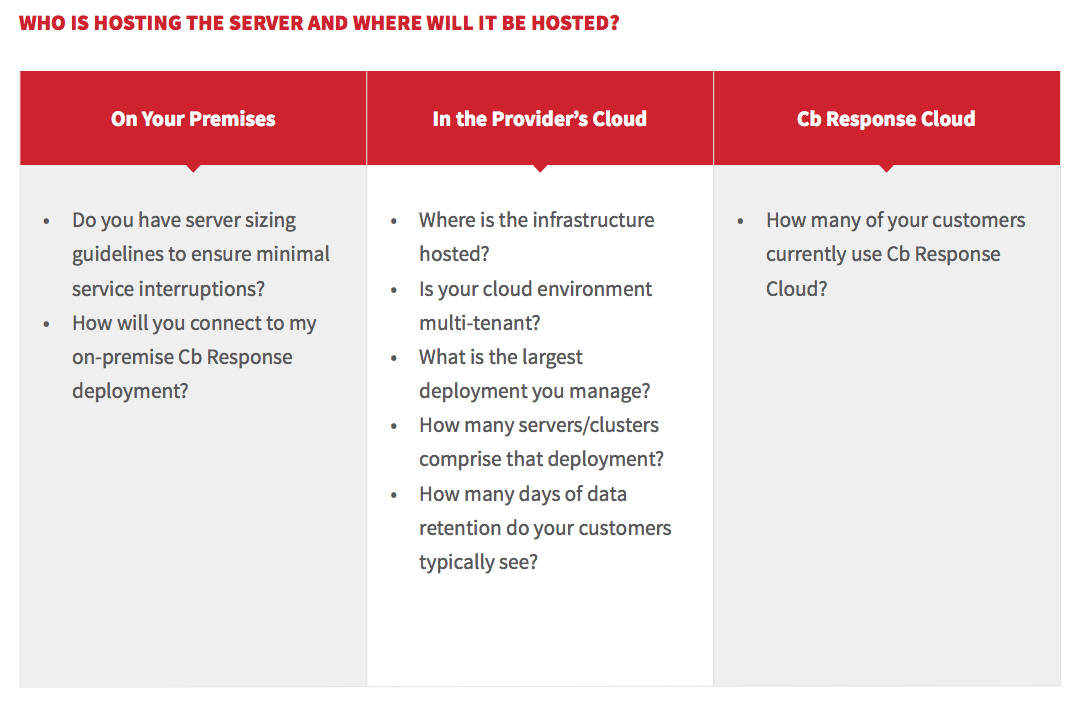
7: How much expertise does your team have running Cb Response infrastructure?
Running Cb Response infrastructure requires equal amounts of expertise and processes. A competent provider should be able to host and manage servers, monitor server and sensor health, test and update new software versions, and ensure access to Cb Response is restricted and auditable. It is worthwhile to ask the vendor how long they have been working with Cb Response and what sensor version they started working on.
Identifying a strategic partner that can master Cb Response’s data to deliver a true detection and response capability requires a thorough evaluation. We hope the questions compiled here will help organizations make an informed decisions that truly impacts security.
Bryan concluded, “My best advice for other security teams is to make sure you understand the value EDR provides. Once you see why it’s important, you can decide whether to bring in people and have analysts hunting through those events, or partner with a managed provider. For us, the choice to use a partner was obvious. It provides better benefits and is sustainable over the long term.”
Download a comprehensive evaluation guide for dozens more questions to ask and real-world case studies of successful Carbon Black Response deployments.
*Personal details including the engineer’s name have been anonymized.
 3: What is my role in responding to and remediating threats?
3: What is my role in responding to and remediating threats?