We often first hear from an organization when they’ve self-diagnosed themselves with a common information security condition: endpoint blindness. You have hundreds—maybe thousands—of laptops, workstations, and servers in your environment and you’ve realized “I have no idea what is actually happening on them until it is too late.”
Visibility into endpoint activity helps, but is just the first step. Oftentimes, the consequence of knowing everything about your endpoints the day after knowing nothing about them is that you are immediately overwhelmed with ALL THE DATA. Your head will be spinning and you’ll still understand very little about your endpoints. To truly address your endpoint blindness you need the ability to sift through the data, identify activity that could be associated with a threat, and the power to stop the threat before harm is inflicted.
And that is exactly how Red Canary supports customers: comprehensively monitoring everything happening on an organization’s endpoints and then accurately detecting suspicious/malicious activity. We like to say we are the “easy button” solution for endpoint blindness.
So that all makes sense but what does it really look like from an implementation and day-to-day standpoint? How does it really work?
It’s actually pretty simple (for you at least).
1. You tell Red Canary you want endpoint visibility and detection.
Within 15 minutes, we provision your Red Canary portal and send you a link to activate your account.
2. You deploy a lightweight sensor to your endpoints, servers, and workstations.
From your Red Canary portal, you then download your very own Carbon Black sensor for Windows, OS X, and Linux and deploy away to your endpoints using SCCM, GPO, your McAfee EPO, or whatever methods your organization uses.
3. We continually analyze every piece of information observed on your endpoints.
Data begins flowing from those endpoints to Red Canary within minutes (SSL keyed uniquely to your organization over port 443). We continually analyze your endpoint events using hundreds of “detectors” that leverage many detection technologies including process behavioral analysis, user behavior analytics, organizational behavior, binary analysis, and threat intelligence.
When we say analysis begins in minutes we mean it. Read how we detected a threat within 30 minutes of deploying in a new environment.
4. Our Security Operation Center triages potential threats
When we detect a potential threat, an analyst from our Security Operations Center reviews the event to determine if it is truly a threat to your organization. Our technology automatically correlates associated events and enriches every potential threat with about a dozen unique pieces of information to aid in this decision. If our analysts cannot immediately determine the nature of a potential threat they will hunt through the full record of activity we retain for the endpoint.
5. If the event is a false positive…
Nothing more happens. We don’t wake you up at 2am because someone in the overseas engineering department installed a new version of his or her IDE. We don’t pull you out of an important meeting because two AV vendors you’ve never heard of marked the Windows kernel as malware. (True story)
(In case you’re interested, our detection technology nominates these “false positives” to the analysis team quite often – by design. As mentioned before, we cast hundreds of wide detection nets to minimize the chances of missing a critical event. Some of our “detectors” have a very high false positive rate. We know this and are ok with it. We don’t want to miss the 1 time out of 100 PowerShell is used maliciously. This is why our human analysts remain a critical and hyper-focused element in the overall detection process. We over nominate to our analysts and rely on their intuition and experience as the ultimate decision-making role.)
6. For a real threat…
We ring alarm bells everywhere. You’re notified via whatever channels best suit your business processes: email, SMS, SIEM integration, PagerDuty phone call, or whatever WHOOMPF integration you put together with your Red Canary technical account manager.
When you get a Red Canary detection notification, remember that it’s been validated by human analysts. When we tell you something bad happens, there’s a 99.98% chance it is real (based on our past false positive rates).
7. Respond!
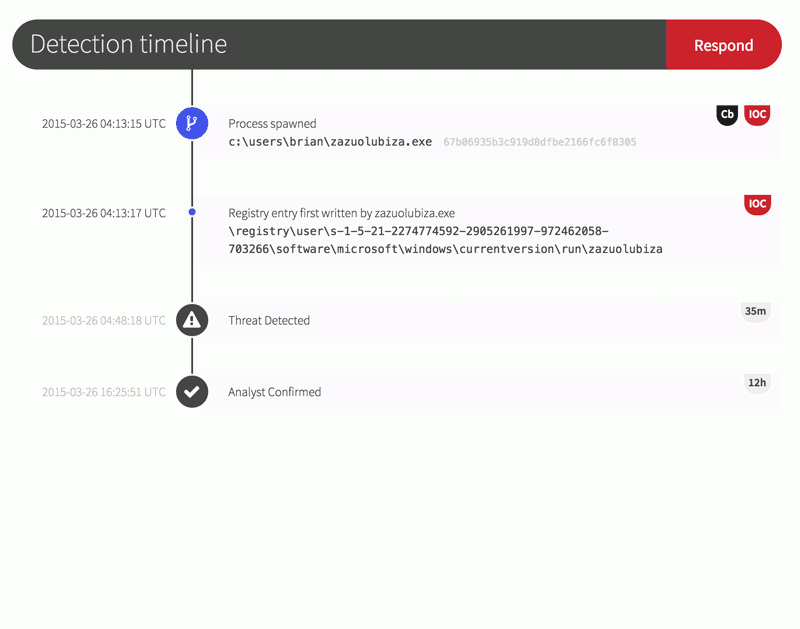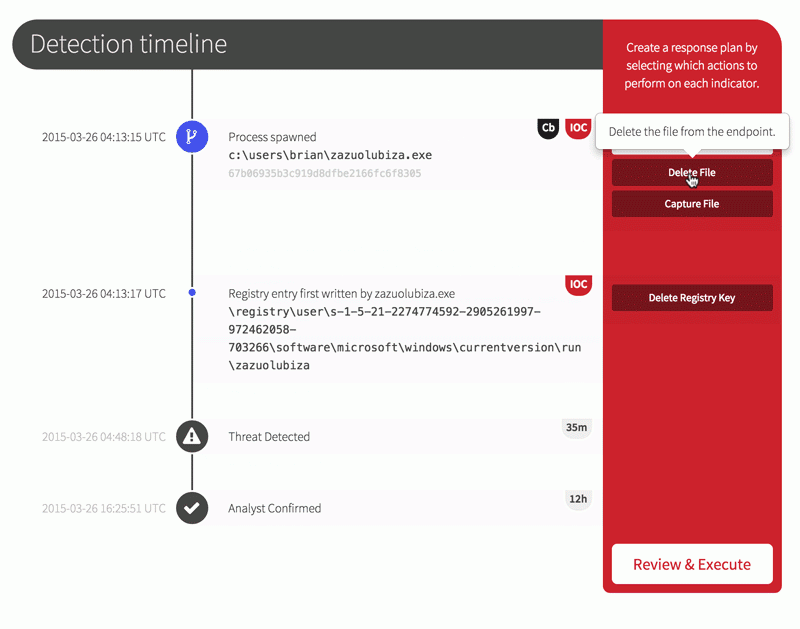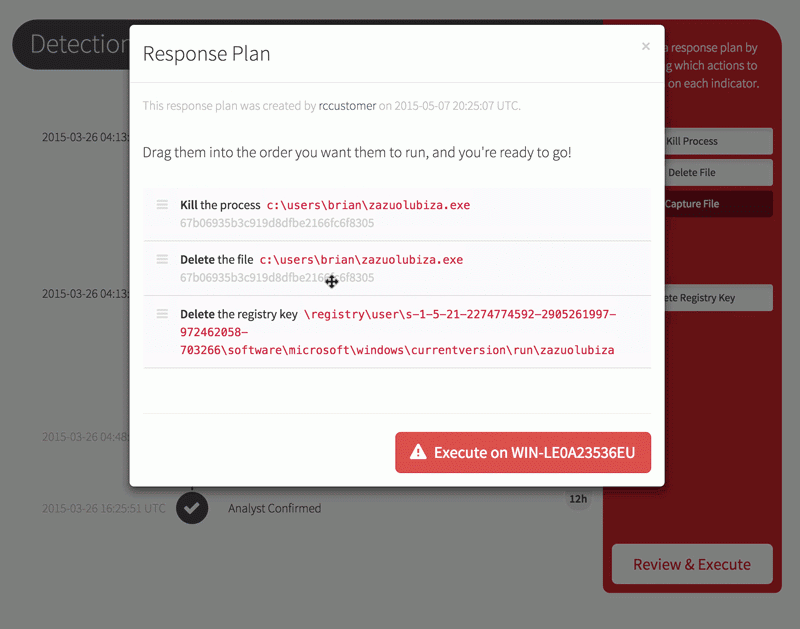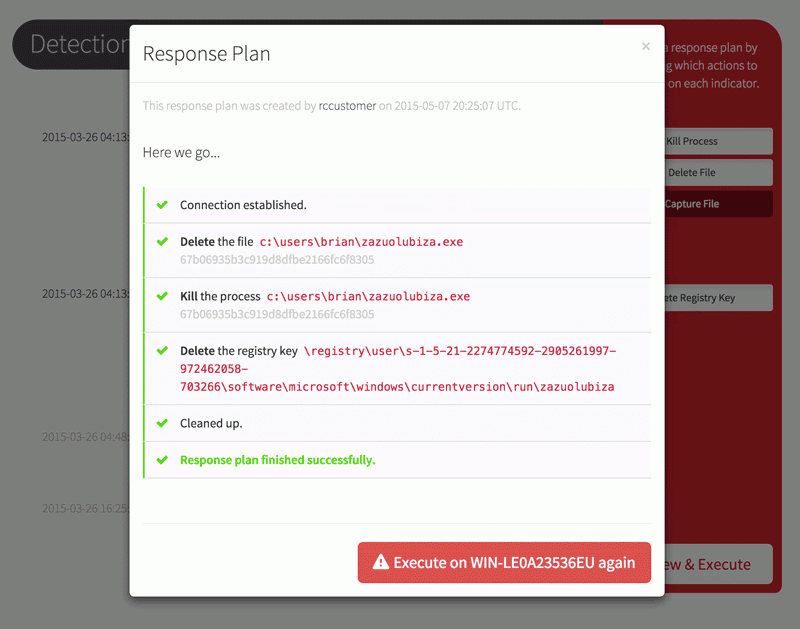
Now that you’ve been alerted to a confirmed threat, it’s time to stop it in its tracks. From your Red Canary portal, you can first isolate the endpoint from the rest of the network and then build a response plan that:
- Kills the process
- Deletes persistence registry keys
- Bans the binary from ever running in your environment, and
- Captures the binary for later analysis when you really need a full-panel reverse engineering report on it
And lastly, your very own Technical Account Manager
Mixed in with all of this day-to-day activity with Red Canary are ongoing conversations with your Technical Account Manager (an actual trained information security professional, not a sales rep). TAMs exist for many reasons, and when you are getting up and running they will answer questions, ensure proper configuration, and review numerous baselining reports. These reports highlight potentially-suspicious activity in your organization and ensure our detection technology is perfectly calibrated to your environment:
File sharing tools (Most companies quickly learn they have rampant use of Dropbox that they thought had been “prevented”)
- Scripting activity (WMIC, VBScript, PowerShell)
- Users accessing an unusually high number of endpoints
- Systems running vulnerable software
- Presence of remote access, file transfer and other types of interesting software and activity
You discuss these reports at your first few weekly account management meetings (and on an ongoing basis) and we continue to tune our detection algorithms to your environment.
That is what getting started with Red Canary looks like. You emailed Red Canary, deployed sensors across your organization, and brought to bear the full power of the top endpoint threat detection technology and team to defend your endpoints.