There is no limit to the creativity attackers will use when masking their activity.
We observed a great example of this immediately after beginning a 14-day evaluation with a B2C services company. Like most of our customers, this company needed an endpoint visibility, detection and response solution to augment their existing security efforts and further protect its PCI and PII data.
Within the first 30 minutes of a proof-of-concept deployment on a small percentage of endpoints, we detected an obscure and targeted attack.
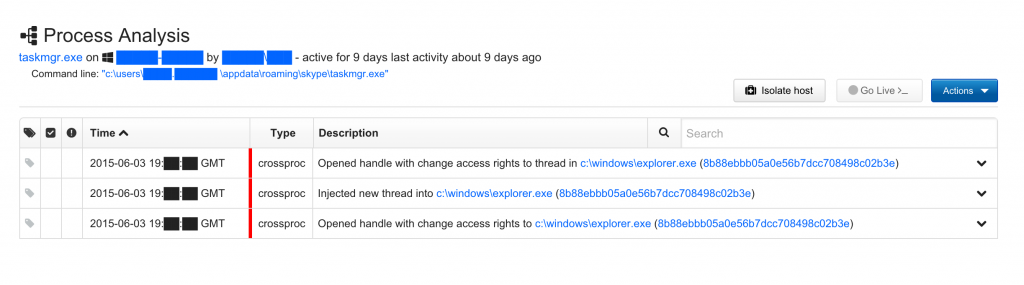
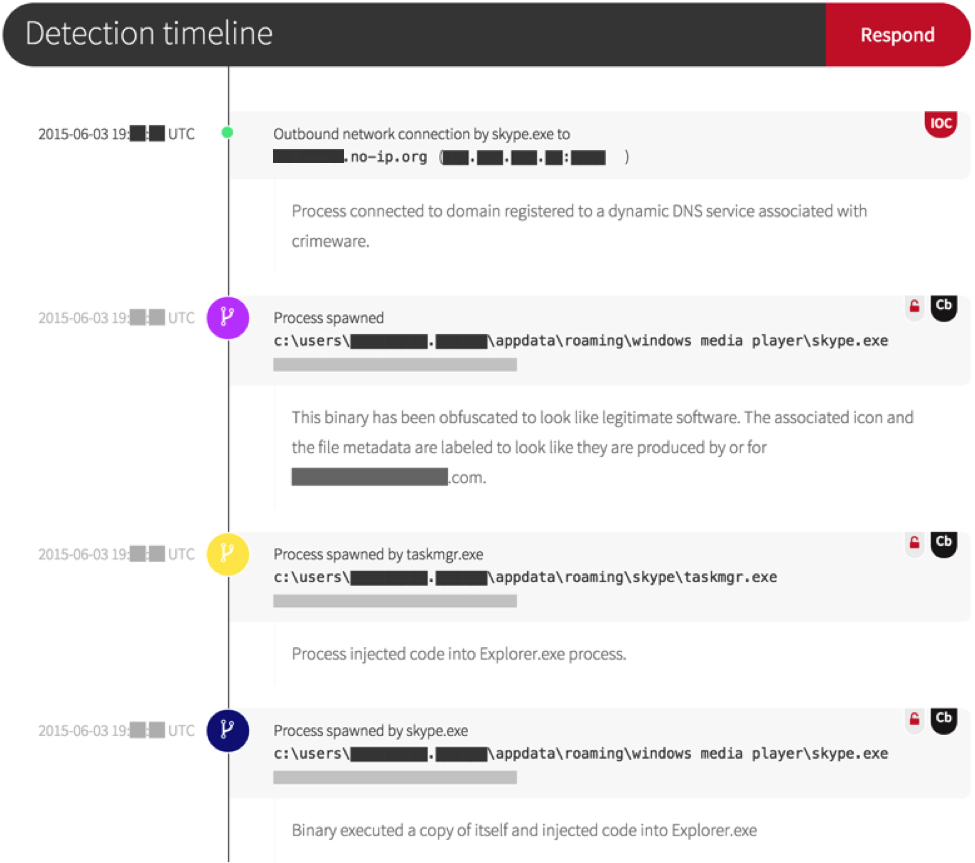
Red Canary initially identified the malware based on two key indicators: a network connection to a domain registered via a dynamic DNS service and the execution of a newly observed binary.
Upon review of the binary metadata, the attacker had gone to some effort to disguise their activity:
- The file name was Skype.exe but the “Company Name” field was that of the customer
- The customer’s logo was set as the binary’s icon
- The attacker cloaked a known command and control IP by registering a domain name that referenced the customer’s organization by name
Additional malicious behaviors were observed during our triage analysis, including code injection into an already running Explorer.exe processes.
The payload was a typical rootkit. And while we do see some level of target-based customization used to increase crimeware infection rates, this exceeded the norm.
The customer was promptly notified of the threat, and they were able to successfully construct a response plan based on our detection and the live response tooling in the Red Canary portal.
As usual, endpoint antivirus and intrusion prevention products identified neither the binary payload nor the behavior as malicious. Were it not for our proof-of-concept deployment providing the threat intelligence, newly observed binary review, and analyst reconstruction of all related endpoint activities, this attack would have progressed undetected.