The National Institute of Standards and Technology (NIST) has released version 2.0 of their seminal cybersecurity framework (CSF). Originally intended as guidance for organizations protecting critical infrastructure, CSF 2.0 is “designed for all audiences, industry sectors and organization types, from the smallest schools and nonprofits to the largest agencies and corporations — regardless of their degree of cybersecurity sophistication,” per NIST. This expansive charter aligns with the White House National Cybersecurity Strategy, which aims to strengthen the United States’s overall position in this area.
The product of this years-long exercise is a framework that has many of the hallmarks of versions that come before it, but is broader in scope and intended to be used alongside other government and industry resources, as opposed to being a comprehensive and prescriptive resource.
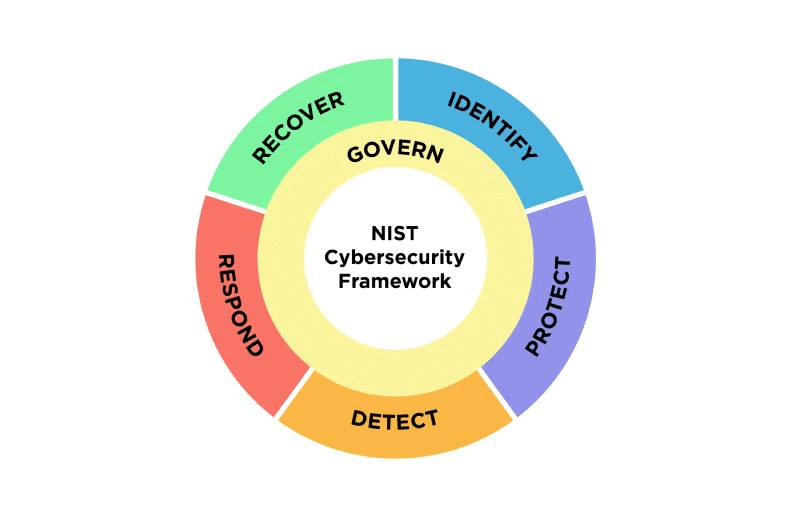
Risk management in the NIST CSF Core
For the majority of organizations, the NIST CSF Core is the most recognizable component of the framework. This introduced the concepts Identify, Protect, Detect, Respond, and Recover, a set of interrelated concepts upon which countless matrices, derivative frameworks, and models have been built.
The most notable change in CSF 2.0 is that governance becomes a first class citizen, across all functions and notably incorporating concepts like supply chain management. Per Dr. Laurie Locascio, director of NIST and under secretary of Commerce for Standards and Technology, the Govern concept “really represents the fact that we have to bring this into the boardroom for discussion.”
The addition of Govern to the Core is both simple and impactful. Whereas before, a number of governance or non-operational functions were included or implied in each area, these are now specifically assigned to this new risk management function. This change both underscores and aligns with components of the National Cybersecurity Strategy, as well as other policy-level changes such as the SEC cybersecurity risk management and incident disclosure rule. A key takeaway for everyone should be that cybersecurity has officially graduated from a niche technology and risk management specialization to a recognized, regulated business and economic priority.
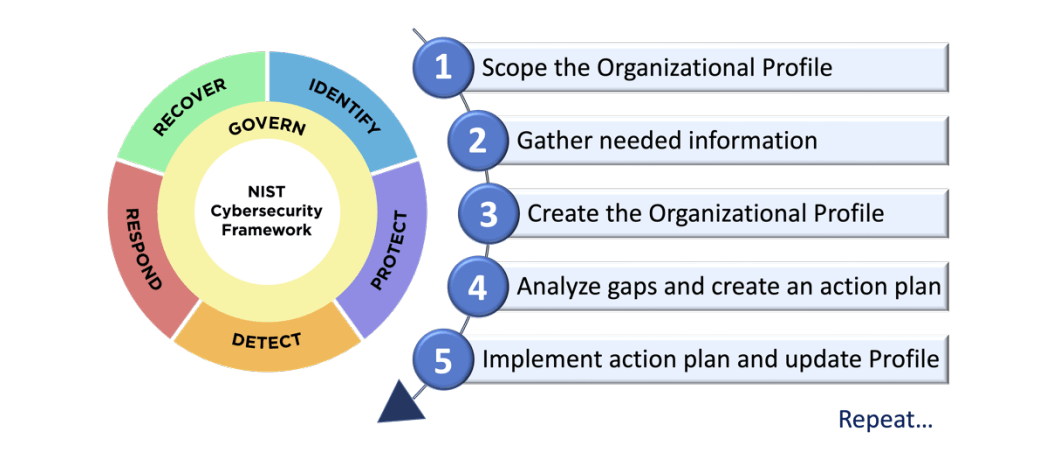
Implementation of the Core concepts is predicated on organizations using Profiles and Tiers:
- Profiles, which describe the organizations current and target cybersecurity posture
- Tiers, a form of maturity model used to define progression in the areas of cybersecurity risk governance and management, from Partial to Risk Informed to Repeatable, and ultimately, Adaptive
A toolkit, not a checklist
Strategically, NIST encourages security professionals to use CSF as a reference and a toolkit, rather than a prescriptive set of standards, metrics, and guidance. The CSF 2.0 document is the foundation, but much more time and attention have been devoted to collecting, organizing, and recognizing the relationships between the CSF and other standards, regulations, implementation guides, and more.
Images courtesy of NIST
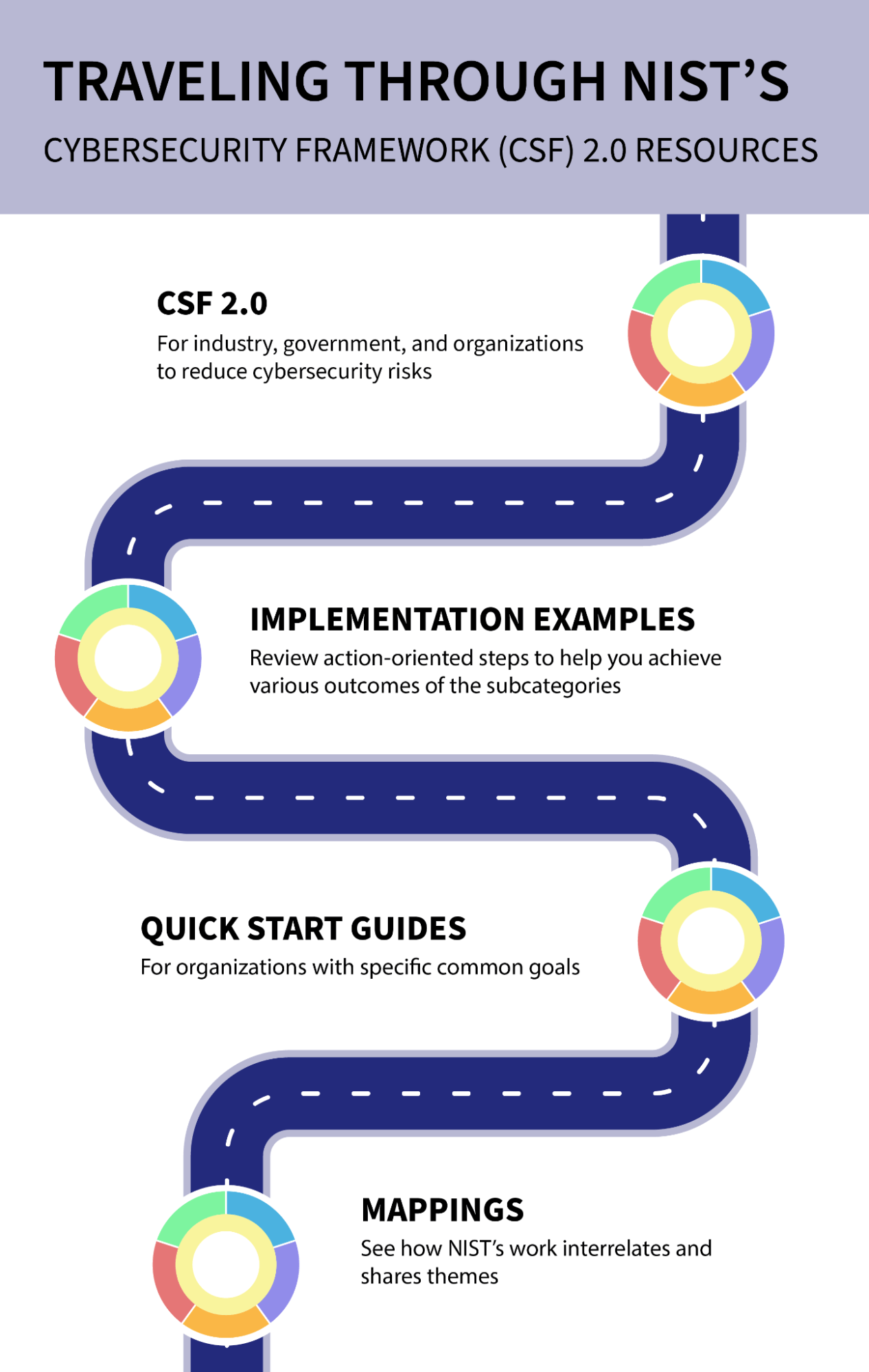
NIST resources
| Resource | Description |
|---|---|
| Resource: | Description : The authoritative framework, released February 26, 2024 |
| Resource: | Description : A table that concisely breaks down each function in the CSF Core into several categories, each of which contains subcategories and a set of examples that can be used as a basis for simple scoring. This resource will be the most familiar, and likely the most useful, for organizations looking to establish a baseline profile and/or for organizations looking for a level of specificity similar to that found in SOC, ISO, and related certification criteria. |
| Resource: | Description : These guides make abstract concepts in the CSF more specific and approachable, speeding implementation:
Also included are guides for two concepts not central to the CSF model, but critical for a robust implementation: Enterprise Risk Management and Cybersecurity Supply Chain Risk Management (C-SCRM) |
| Resource: | Description : This tool allows the user to choose a NIST publication (e.g., CSF 2.0) and cross-reference it against a wide variety of government or industry standards. For instance, it will quickly provide a matrix showing the delta between CSF 1.X and CSF 2.0. |
| Resource: | Description : A search-based interface to quickly hone in on CSF sections related to a given topic, category, function, etc. |
Serving the greater good
It’s worth noting that this approach—providing an abstract framework and expansive menu of examples—has been met with some contrition. Some security leaders claim that lack of actionable, specific guidance makes this more difficult to adopt for some organizations. However, NIST is explicitly optimizing for the greatest possible percentage of organizations, and providing specificity at every level and for every organizational profile might mean that new versions feel more complete but also take longer to release.
Overall, and despite the desire from some to see NIST take a more prescriptive approach, NIST’s stated goals are to build a framework that the majority of organizations can adopt, and one that aligns with national policy directives to increase and elevate cybersecurity awareness, preparedness, and maturity. By those measures, CSF 2.0 and the compendium of resources being collected to supplement it will lead to more cybersecurity conversations, and at more appropriate levels within both government and private industry.