Each month, the Intel team provides Red Canary customers with an analysis of trending, emerging, or otherwise important threats that we’ve encountered in confirmed threat detections, intelligence reporting, and elsewhere over the preceding month. We call this report our “Intelligence Insights” and share a public version of it with the broader infosec community.
Highlights
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Here’s how the numbers shook out for June 2023:
| Last month's rank | Threat name | Threat description |
|---|---|---|
| Last month's rank: ⬆ 1 | Threat name: | Threat description: Activity cluster characterized by the delivery of an information stealer and .NET RAT via search engine redirects |
| Last month's rank: ⬆ 2 | Threat name: Stealc | Threat description: Information stealer used to steal credentials and other data |
| Last month's rank: ➡ 3 | Threat name: | Threat description: Malware family used as part of a botnet. Some variants are worms and frequently spread via infected USB drives |
| Last month's rank: ⬇ 4 | Threat name: | Threat description: Open source tool that dumps credentials using various techniques |
| Last month's rank: ⬇ 5 | Threat name: | Threat description: Collection of Python classes to construct/manipulate network protocols |
| Last month's rank: ⬆ 6 | Threat name: Dock2Master | Threat description: macOS ad fraud activity that has led to downloads of other macOS malware, such as Shlayer |
| Last month's rank: ⬆ 7* | Threat name: NetSupport Manager | Threat description: Legitimate remote access tool (RAT) that can be used as a trojan by adversaries to remotely control victim endpoints for unauthorized access |
| Last month's rank: ⬆ 7* | Threat name: AsyncRAT | Threat description: Open source remote access tool with multiple functions including keylogging and remote desktop control |
| Last month's rank: ⬆ 9* | Threat name: | Threat description: Penetration testing framework used to probe systematic vulnerabilities on networks and servers and conduct post-exploitation activity on compromised hosts |
| Last month's rank: ⬆ 9* | Threat name: | Threat description: Dropper/downloader, often distributed through search engine redirects |
| Last month's rank: ⬆ 9* | Threat name: 3LOSH | Threat description: Crypter, typically used to package and deliver a remote access tool like AsyncRAT |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Observations on trending threats
Our top 10 changed a lot between last month and this month. Several prominent threats fell completely off the list, most notably Qbot, Qbot delivery affiliates TA570 and TA577, and Raspberry Robin. Yellow Cockatoo returned to the top 10 to claim the number 1 spot, its first appearance in the top 10 since August 2022. Yellow Cockatoo, which overlaps with what researchers call the Solarmarker or Jupyter infostealer, reappeared in late May following a hiatus. Its activity continued to increase over the course of June.
Stealc, our number 2 threat and a newcomer to the top 10, was first identified in early 2023. Red Canary saw a wave of Stealc activity in mid-June that affected multiple customer environments. You can read more about Stealc below.
Our two other newcomers to the top 10 this month are AsyncRAT in a tie for 7th and 3LOSH in a tie for 9th. These two threats are related; 3LOSH is a crypter frequently used to package and deliver AsyncRAT, an open-source remote access tool used by a number of adversaries. We observed a phishing campaign distributing 3LOSH dropping AsyncRAT as its payload in the latter half of June.
Thou shall not Stealc
In the last half of June, Red Canary observed a surge of Stealc activity in our customer environments. Stealc is an information stealer with marked similarities to other stealers like RedLine, Raccoon, and Vidar. According to the researchers who identified Stealc, it is highly customizable and can target many types of sensitive information including browser data, browser extensions, cryptocurrency wallets, and details from additional applications like email clients.
We saw evidence of search engine optimization (SEO) poisoning being used as the delivery vehicle. SEO poisoning is an initial access technique that tricks users into visiting malicious websites masquerading as legitimate sites returned in search results. After navigating to the site, victims downloaded a Stealc executable with a misleading filename, designed to lure users into thinking they were downloading a software update. The Stealc executable reached out to command and control (C2) IP addresses and executed a clean-up command, which gives us a detection opportunity.
The Red Canary Intelligence Team uses different methodologies to conduct analysis, including the tool Synapse from the Vertex Project. As we examined a graph view of the Stealc activity, we were able to connect the disparate IP addresses and malware we observed on different victims based on overlap in one IP address, 77.105.146[.]191. We wanted to share this as an example of how link analysis can help identify connections.
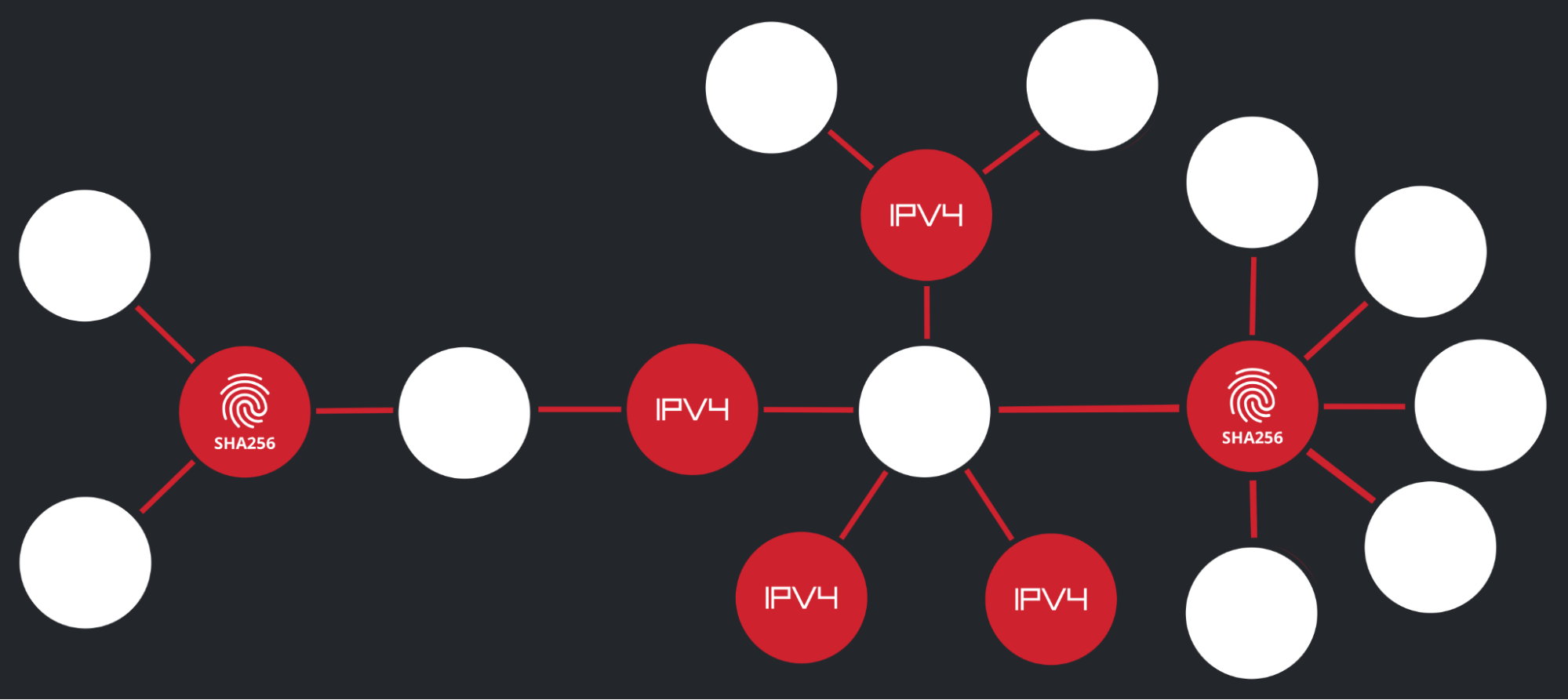
Stealc IOCs observed by Red Canary in June 2023
SHA256
1c4ee02f339e2c404a457cafdcbf9e1c06fb48546f0546765d41fd8fd471322d5e2076573f87cb747b06ac9b445c85a7b642c2bd7b42e39dcdde22d14014c16a
IP addresses
77.105.146[.]19177.105.146[.]16677.105.147[.]5977.105.146[.]127
Detection opportunity: cmd.exe command to delete initial installation files
The following pseudo-detection analytic looks for a cmd.exe command deleting files after an executable completes installation, which was one behavior observed from Stealc. After successfully achieving persistence on the endpoint, some types of malware like stealers will delete the initial install files. Legitimate installers or other scripts might use this activity to cleanup temporary files, so look for other signs of post-exploitation activity to confirm or deny malicious behavior.
process == (cmd.exe)
&&
command_line_includes_all == (timeout, del, /c, &)
&&
command_line_includes_any == (-t *, /t *, /q, /f, rd, exit, rmdir)
* is a placeholder for a number that pauses the command processor for the specified number of seconds
The “nOAuth” Azure AD application misconfiguration vulnerable to account takeover
In June, researchers from security firm Descope shared their discovery of a handful of widely used Azure Active Directory (AD) applications that improperly validate a user’s identity during authentication. This improper validation is referred to as “nOAuth.” The undisclosed applications insecurely validate whether a token is properly assigned to the correct user. A user from one Azure AD tenant could perform an account takeover of any user of a misconfigured application, whereby an adversary changes their email address in their home tenant to match the targeted user’s account.
When you log into an application using Azure AD, the system adds some information about you to a digital token. This token is like a temporary ID card that proves who you are to the application. However, some of this information can be changed, including your email address. For example, if an application is only checking the email address in the token to verify Alice’s identity, then Bob could change his email address to match Alice’s, and the system would think that Bob is actually Alice.
Therefore, if an adversary knows a user’s email address and knows that the user has an account with one of these faulty applications, the adversary could change their email address in Azure AD to match that user’s. When the adversary logs in, the faulty application would give them full access to that victim user’s account. Many applications are affected by this vulnerability. For example, Grafana announced a CRITICAL 9.4 CVSS score for CVE-2023-3128 related to this vulnerability.
Microsoft made an announcement acknowledging risks of this misconfiguration in June, providing guidance specifically to developers on how to migrate from unsafe authorization via email claims. Microsoft has also previously shared guidance on proper user validation.
Red Canary recommends auditing your Azure AD environment for unusual or malicious OAuth applications as well as overly permissive applications. If any are identified, revoke the OAuth application’s access. We also recommend monitoring your security products such as Azure AD Identity Protection for alerts relating to unfamiliar logons or impossible travel, as these will likely be generated during successful exploitation of this vulnerability.