Our customers trust us to investigate threats thoroughly as we protect their enterprises broadly—their endpoints, cloud, SaaS apps, and beyond. We deliver, but it’s easier to say we do than to prove it, let alone prove it on an ongoing basis without taking up much of our customers’ time.
One way we show our work is via our unified threat timeline, which conveys to customers both the evolution of a threat chronologically and how Red Canary detected, responded to, and remediated that threat. It showcases the work of our built-in XDR platform, which aggregates and correlates disparate events from across your security tools; our detection engineers, who use that context to detect threats earlier than if they looked at siloed data from each data source; and our incident handlers, who lead customers through response and remediation.
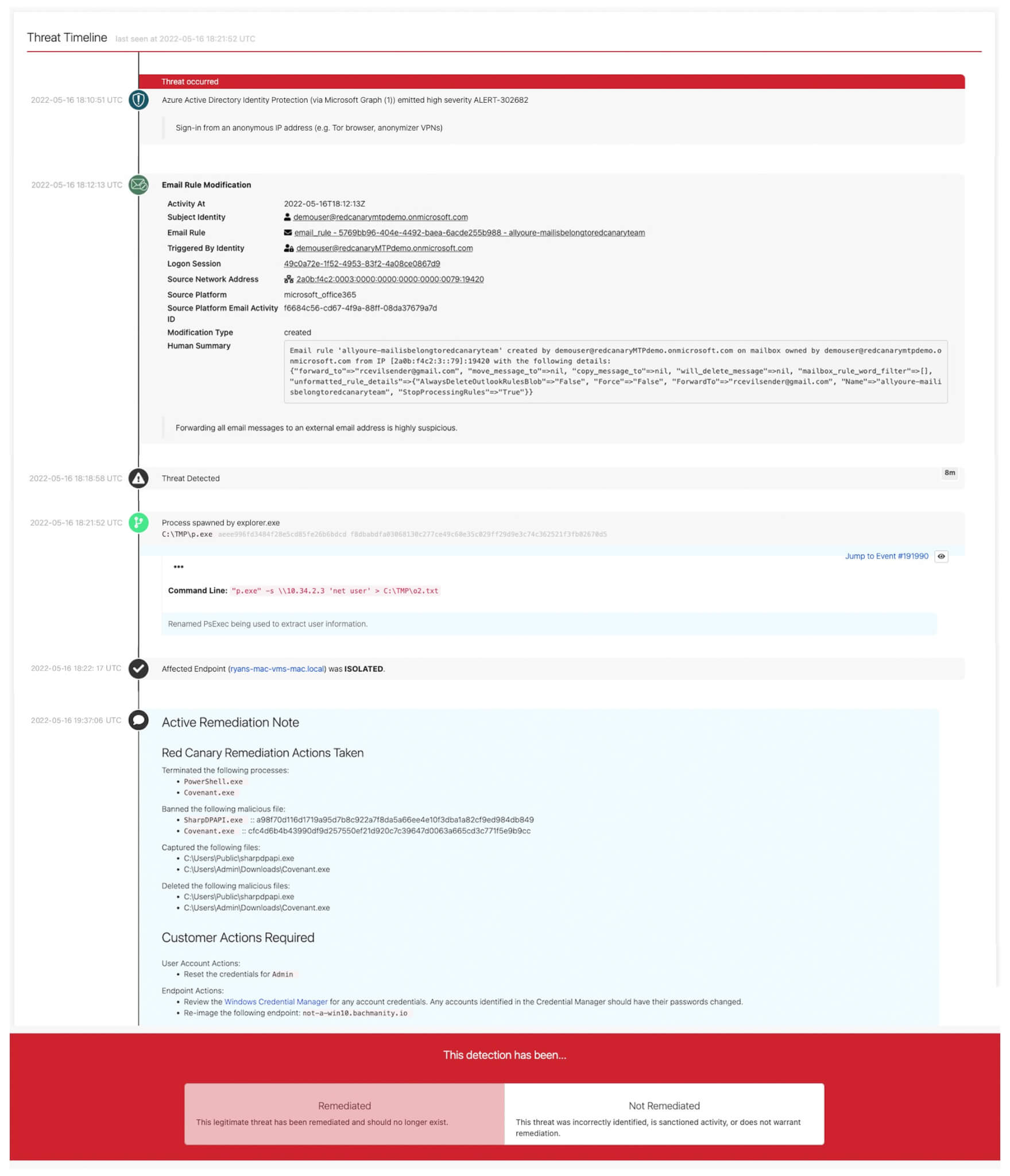
Every threat we detect has an associated timeline that addresses several questions upfront. How did Red Canary detect this threat? How quickly did they detect it? What is the scope of this threat? And what did Red Canary do to respond to this threat? Our threat timeline provides these answers at a glance for customers so they can quickly synthesize the relevant information (and, critically, only the relevant information) and take the appropriate next steps for their organizations.
I’ll walk you through an example to illustrate the point.
Detecting the threat
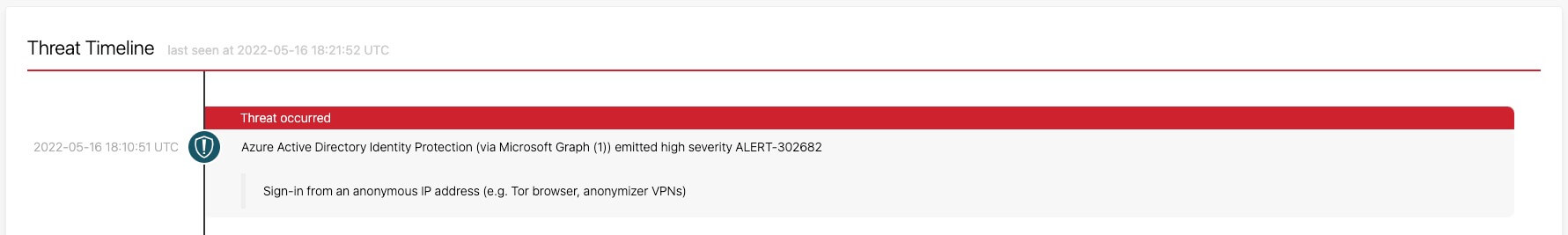
The first entry on the threat timeline above is a high-severity alert from Azure Active Directory Identity Protection. The tool noticed that someone from this organization used an anonymous IP address to sign in. This is absolutely suspicious behavior, but if your organization is like most, then you receive tens if not hundreds (…if not thousands) of high severity alerts across many different tools each day. It’s very possible, even likely, that you don’t address this alert immediately, purely due to it being buried below other high severity ones.
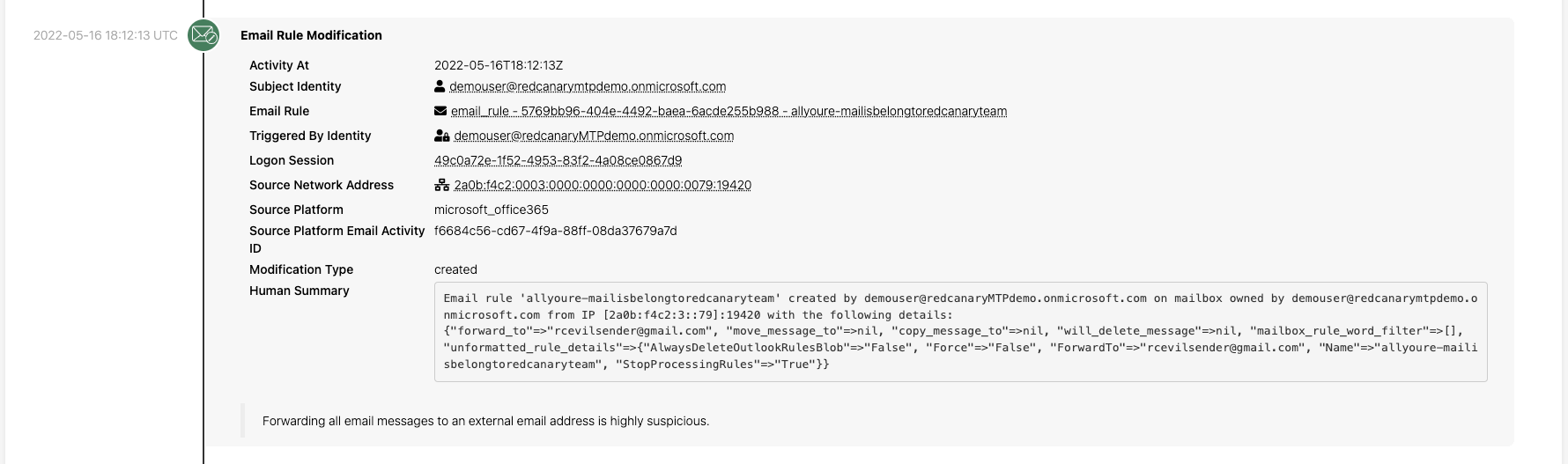
Two minutes later, we detected that a user set up an email forwarding rule that forwards every received email to an external address. This is very suspicious behavior, particularly in light of the anonymous login. We identified this suspicious forwarding rule via detections we create in-house and apply to Microsoft Unified Audit Logs.
As you can see, we provide the associated identity, session, and network address among other critical information to our customers. Our ability to aggregate and correlate disparate attributes such as these across different sources increases the value of each security tool. Tools that may have been seen as noisy are now adding security value; data that may have been ignored by an operator is now adding valuable context for understanding the scope and impact of the threat.
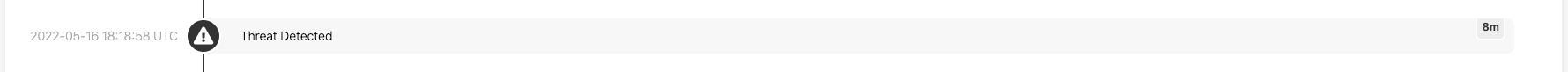
In this example we’re confident that this is a threat, so we notify the customer, as evidenced by the “Threat Detected” entry on the timeline. With its associated timestamp you can see how long it took us to detect the threat after the first evidence of it in the customer environment. At this point, our Incident Handling team proactively contacts the customer and guides them through suspending the associated identity’s access to the corporate and cloud networks, as well as all SaaS apps, and of course remediating the email forwarding rule.
Containing the threat
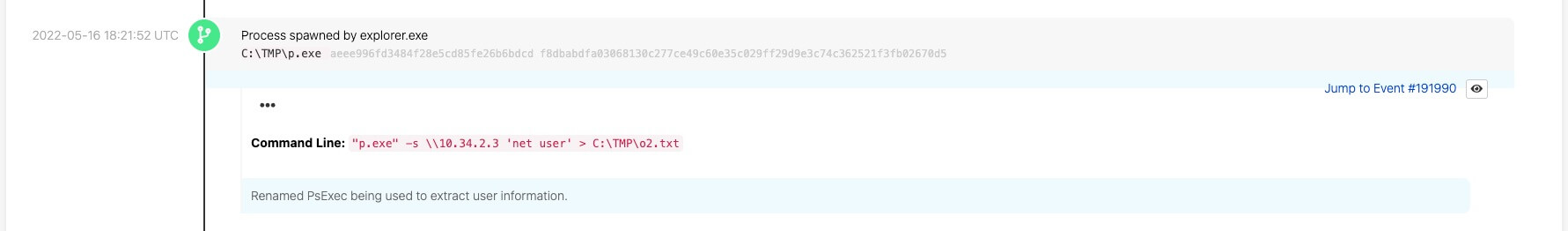
Soon after notifying the customer of this threat, another of Red Canary’s behavior-based detections fired—this time on an endpoint associated with the identity whose email account was compromised. Using raw telemetry collected from Microsoft Defender for Endpoint, we spotted a process spawned by explorer.exe in which the now clear adversary renamed PsExec—a light-weight telnet replacement that lets you execute processes on other systems—so that they could exfiltrate information. This threat now unambiguously requires urgent containment and remediation.
Red Canary allows customers to set up simple but powerful automated playbooks to immediately respond to threats. In this case, a playbook ran that isolated the affected endpoint, neutralizing the threat on the endpoint within seconds of our confirming it.
Remediating the threat
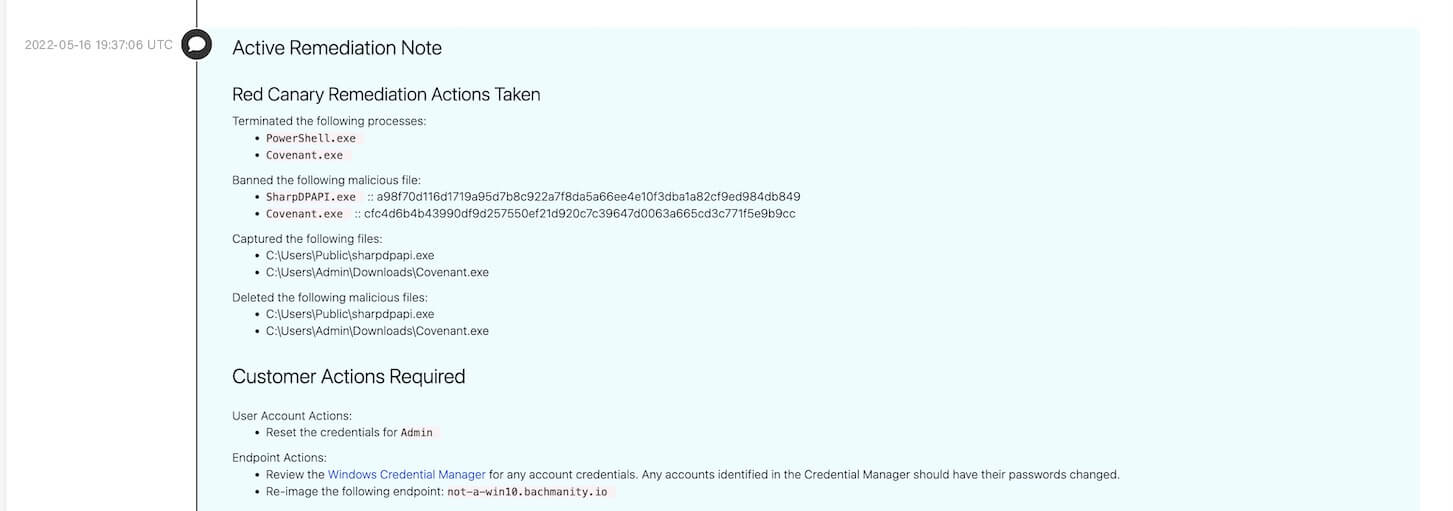
Threat neutralization is critical but is still not full remediation, particularly on endpoints. Adversaries often leave artifacts that, if left on the endpoint, enable them to retake the device and establish command and control. We’ll find and remove those artifacts for you–we call this service Active Remediation.
Because this customer had Active Remediation, our Incident Handling team got to work with hands-on-keyboard support immediately after the playbook fired; they killed persistent processes and then banned, captured, and deleted malicious files on the device. They also provided explicit requirements for the customer to complete to fully remediate the threat, e.g., resetting the associated user’s credentials across the corporate network, cloud infrastructure, and SaaS apps, and re-imaging the device. We guide all customers through endpoint threat remediation, but we also offer this hands-on-keyboard service because customers kept asking us, “…can you just do it for me?”
When the customer feels confident that the threat is fully remediated, they can note so at the bottom of the threat timeline.
The moral of the story? Red Canary is here to help!
Just by looking at our threat timeline, a customer can tell how quickly we detected a threat relative to its first indication in their security data, how we brought relevant data from across their tools to bear on detecting a threat, and how fast we responded to and remediated the threat. The threat timeline is just one of many ways that we prove the value of Red Canary to our customers, and we like how it keeps us accountable and ensures that we’re walking the walk.