The Red Canary open source team is releasing VSCode-ATT&CK, an extension for Visual Studio Code that integrates the MITRE ATT&CK framework into one of the most popular integrated development environments (IDE) in use today. The extension offers network defenders, detection engineers, and threat intelligence analysts some useful features, including the following:
- auto completion to supply names and identification numbers associated with ATT&CK tactics, techniques, groups, mitigations, and software
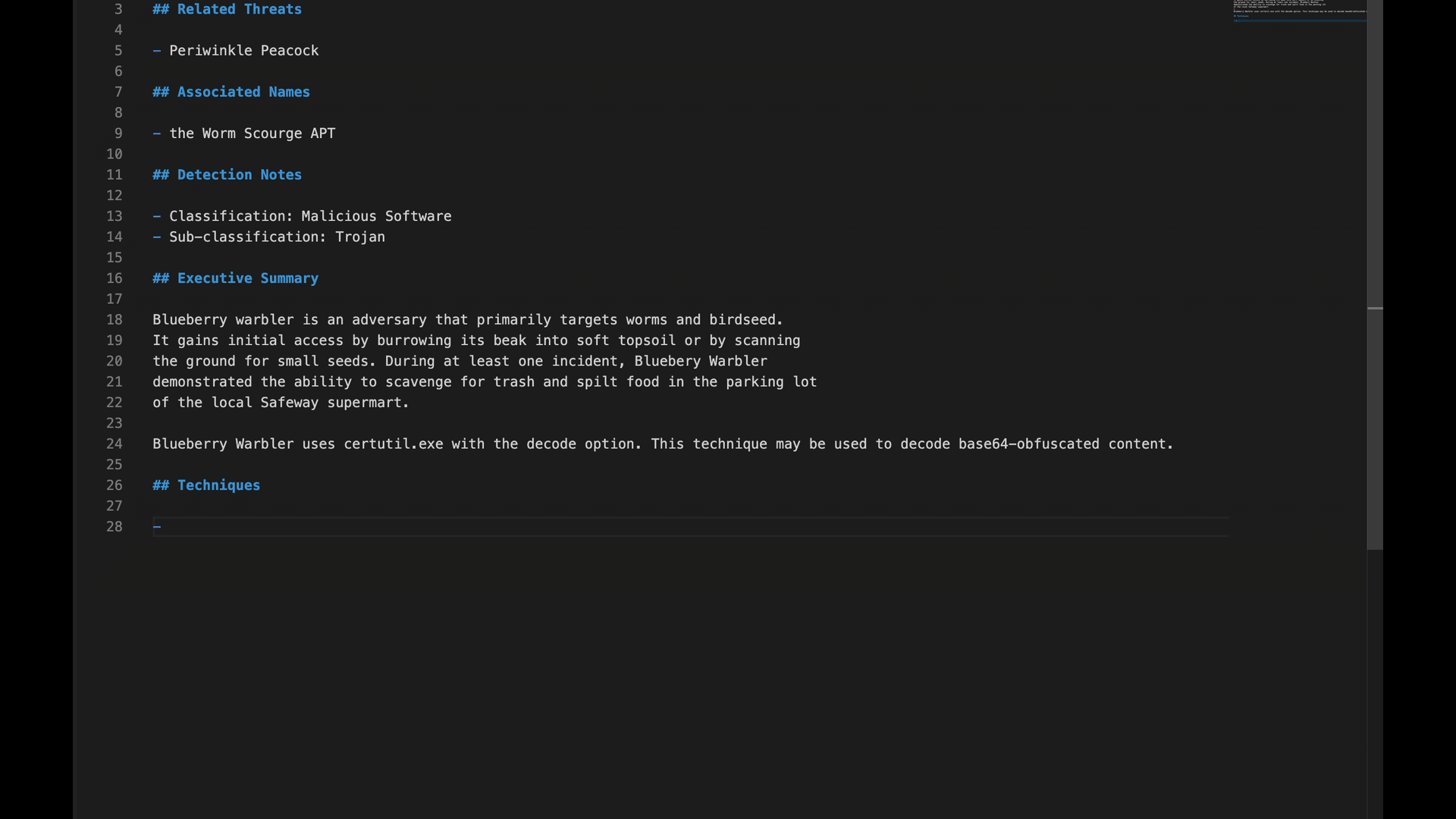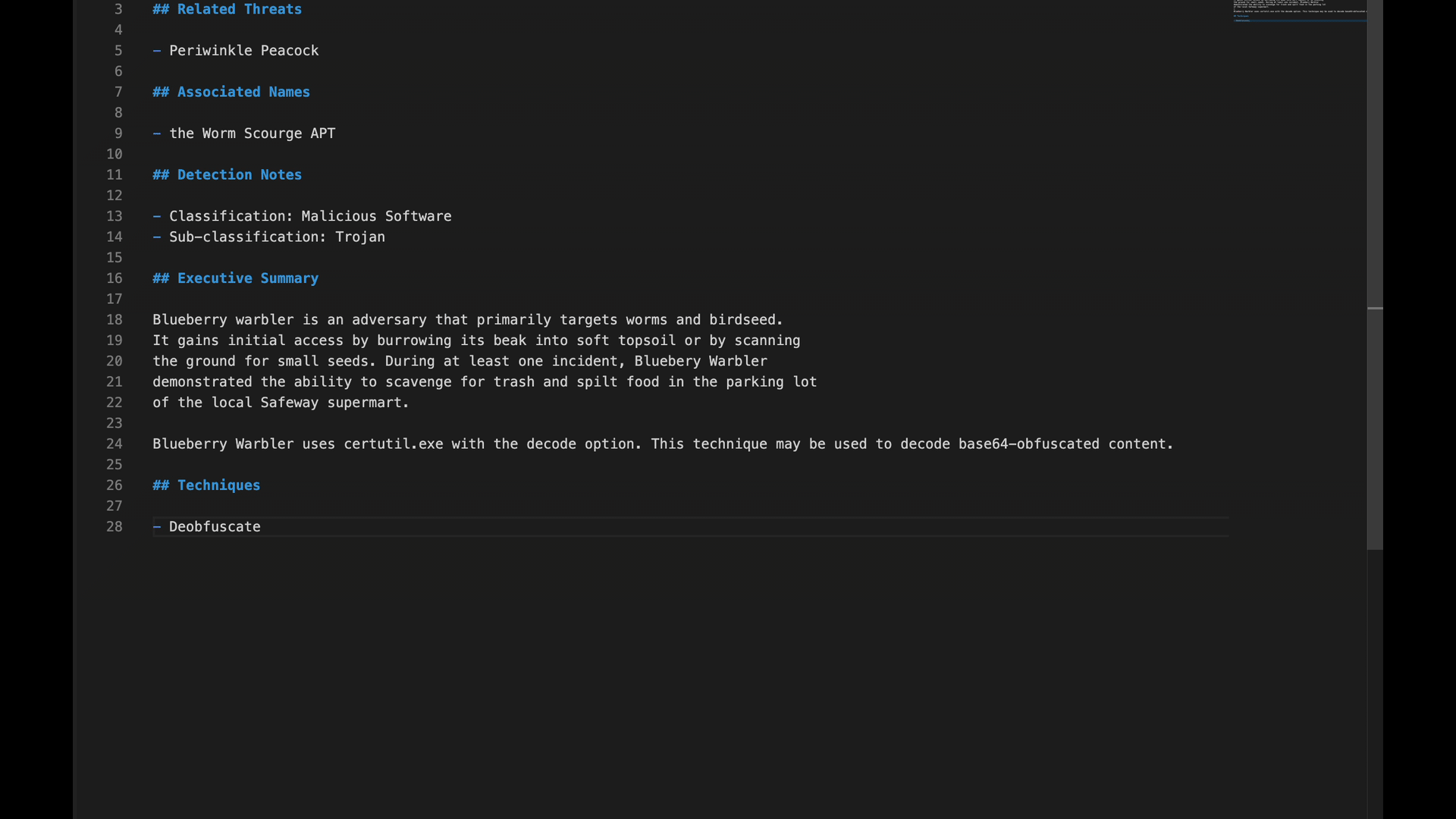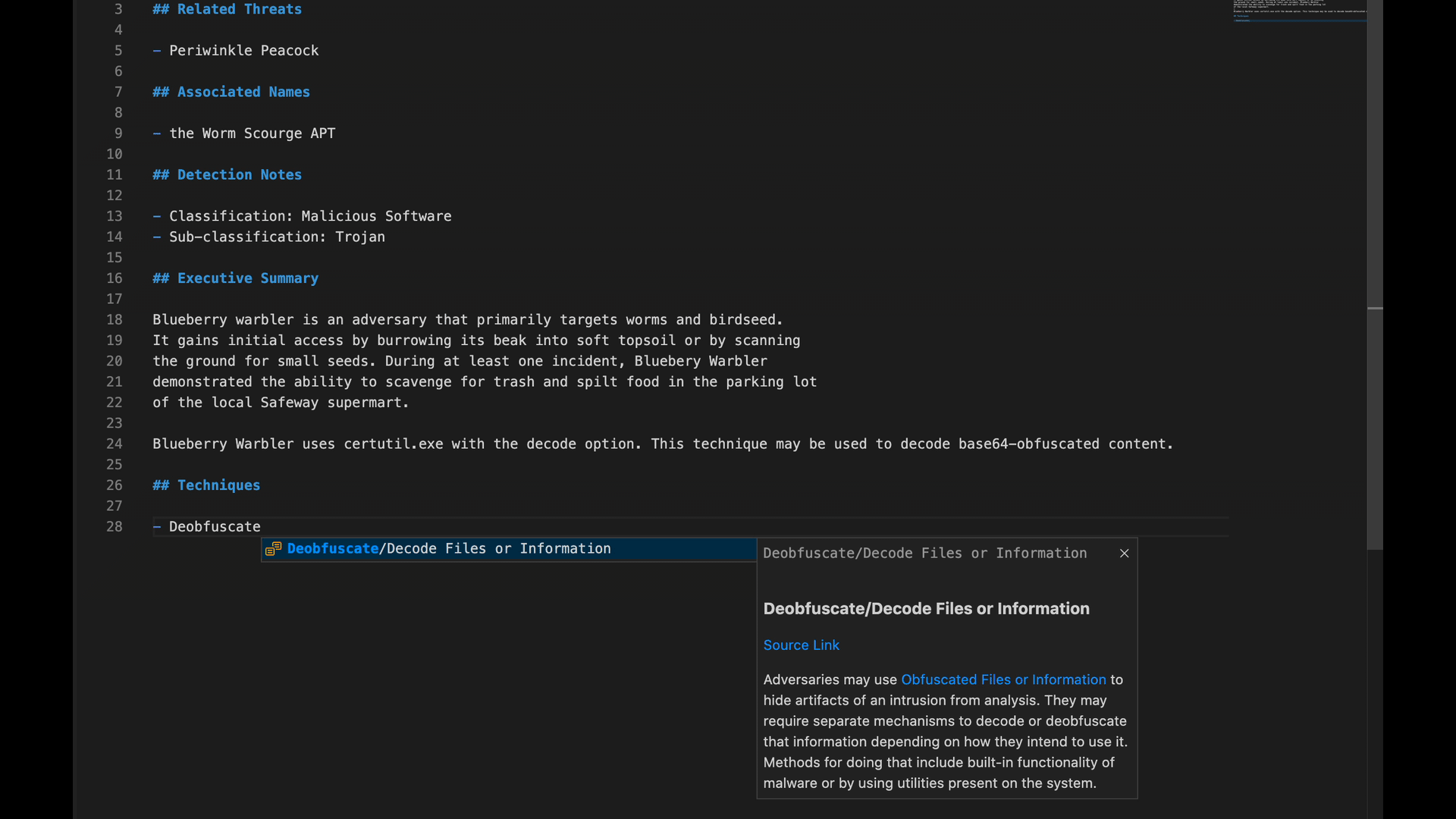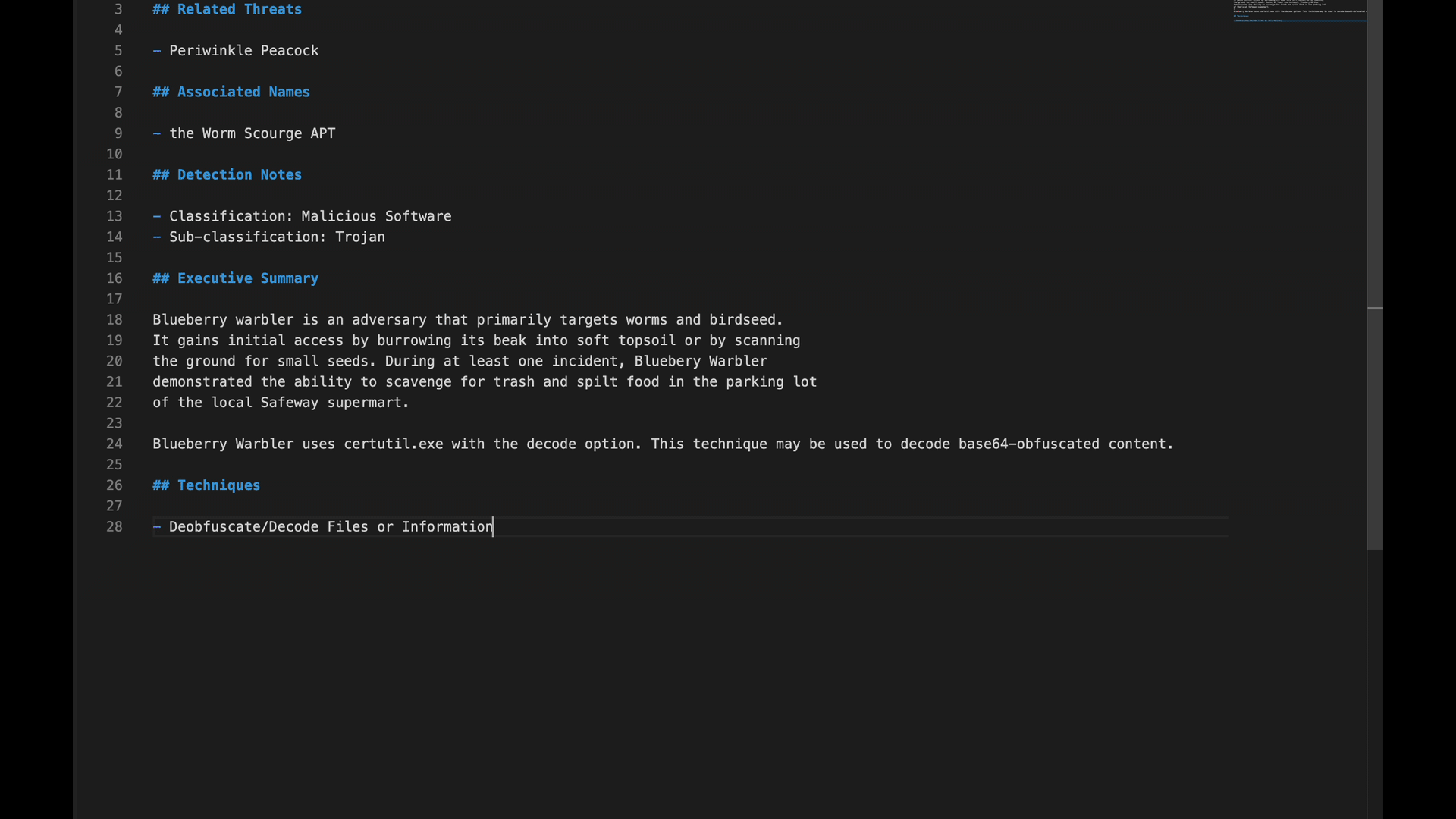
- code hovering to draw detailed information about tactics, techniques, groups, mitigations, and software from the ATT&CK website
- an integrated ATT&CK technique search command
A match made in threat research heaven
Many of our internal teams map their work to the ATT&CK framework. For example, our detection engineering team maintains a living library of thousands of behavioral detection analytics that we associate with corresponding ATT&CK techniques or sub-techniques whenever possible. Similarly, our threat intelligence team uses ATT&CK tactics and techniques to help organize and standardize the threat profiles they produce to inform the CIRT, our customers, and the broader information security community.
These teams needed a way to search, identify, and integrate ATT&CK directly into their development processes, and since many of them already used Visual Studio Code, creating this extension was a natural fit. This has the added benefit of allowing us to easily customize how we integrate ATT&CK on a per-project basis. Often, our detection engineers will only reference ATT&CK techniques by their ID, while our threat intelligence team will use the entire technique name, including sub-techniques. We’ve baked this customization into the extension, so even if you wear multiple hats in your organization, this tool will fit your diverse needs.
We’ve written before about creating detectors as code, and we wanted to be able to search ATT&CK techniques without switching away from our code editors and into a browser window. Often, we find ourselves trying to answer a simple question: Based on the software I’ve seen, what technique do I need to apply here? An example of this would be certutil.exe. Many adversaries use this tool to decode data on the command line, but there’s no “certutil.exe” ATT&CK technique. Rather than interrupting focus by navigating to a web browser, going into https://attack.mitre.org, and searching for “certutil”, we’ve integrated the search directly in Visual Studio Code.
See VSCode-ATT&CK in action
The following GIF demonstrates how you can query the ATT&CK framework to figure out what ATT&CK technique most closely relates to certutil.exe:
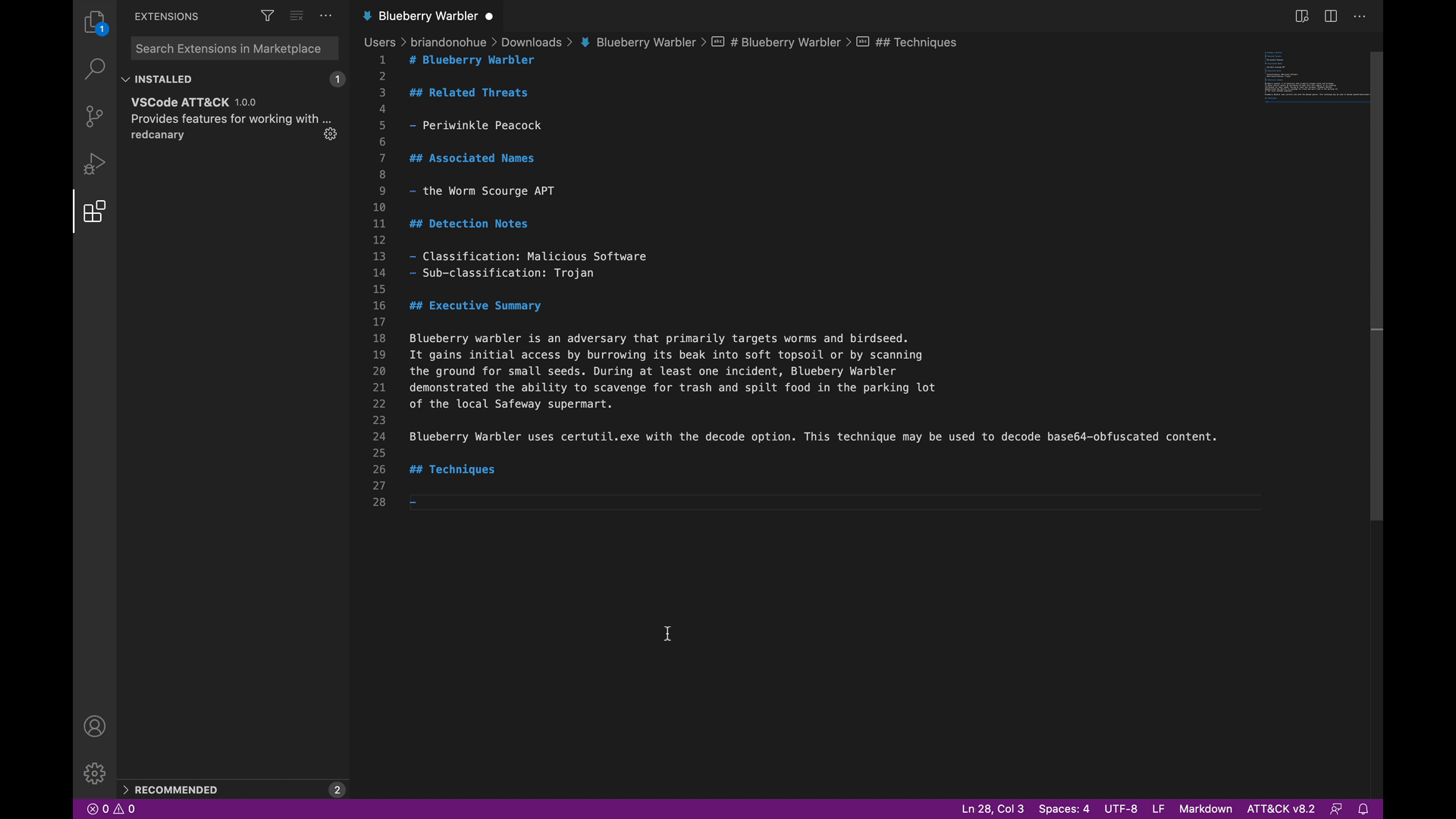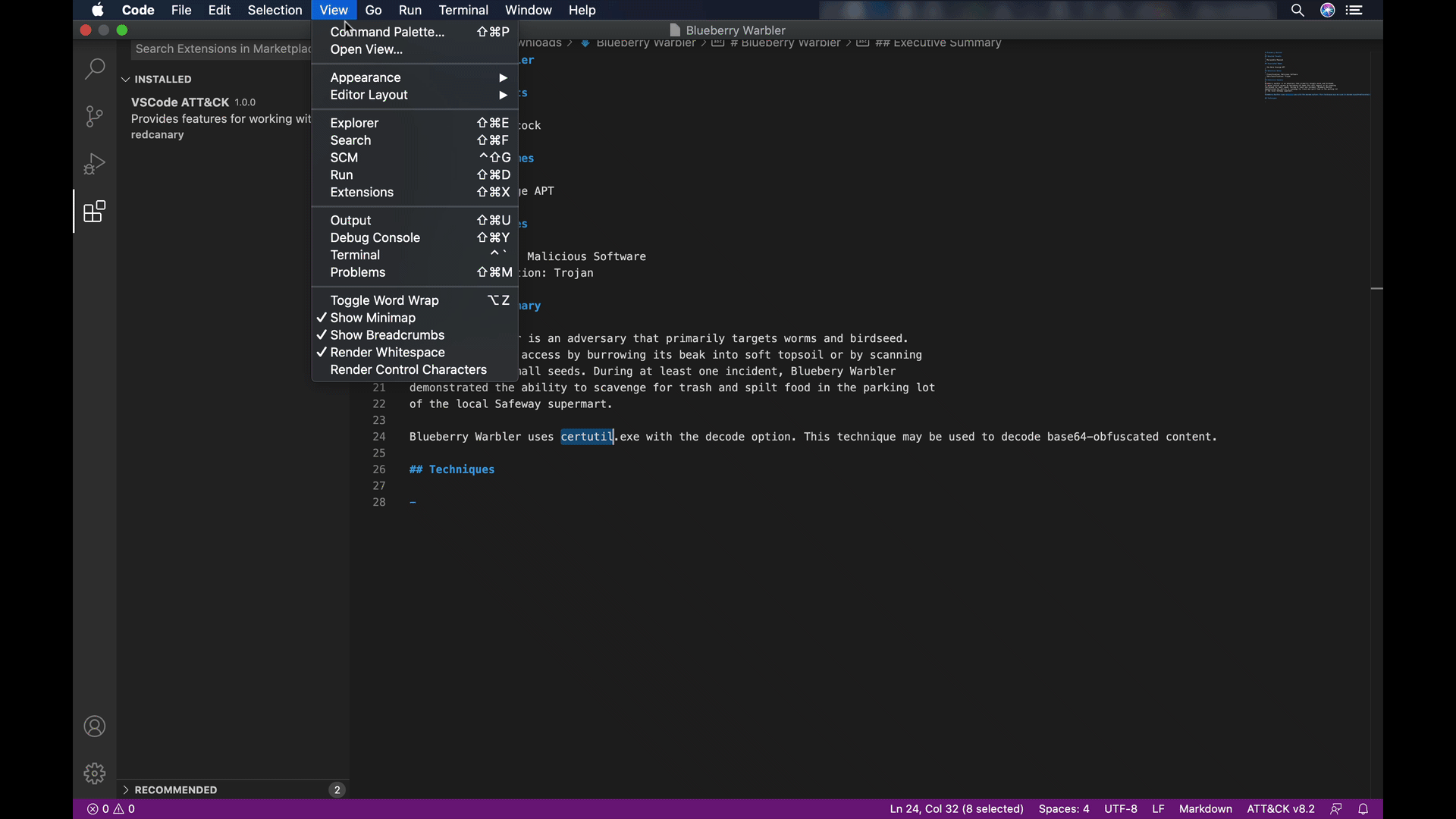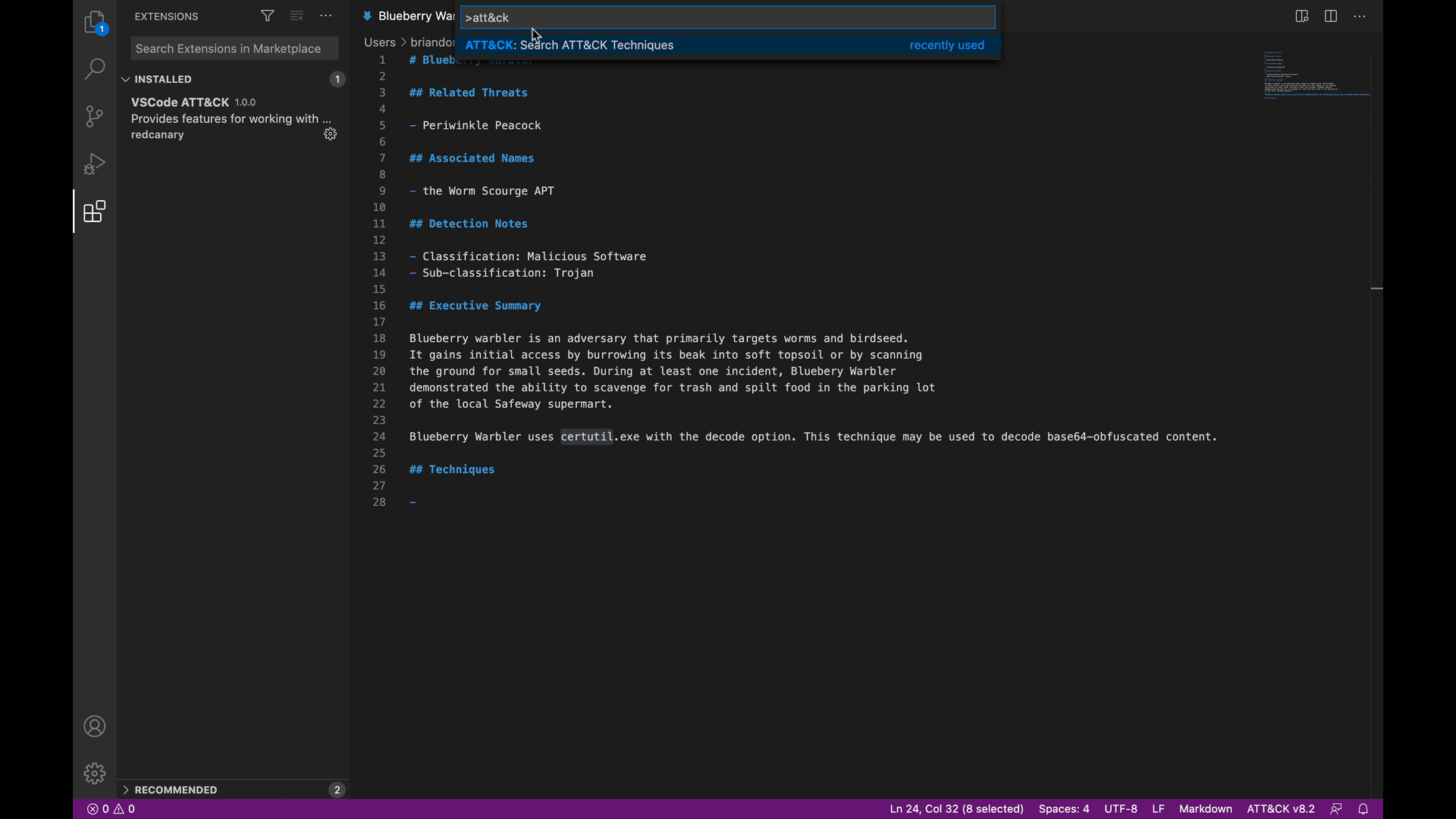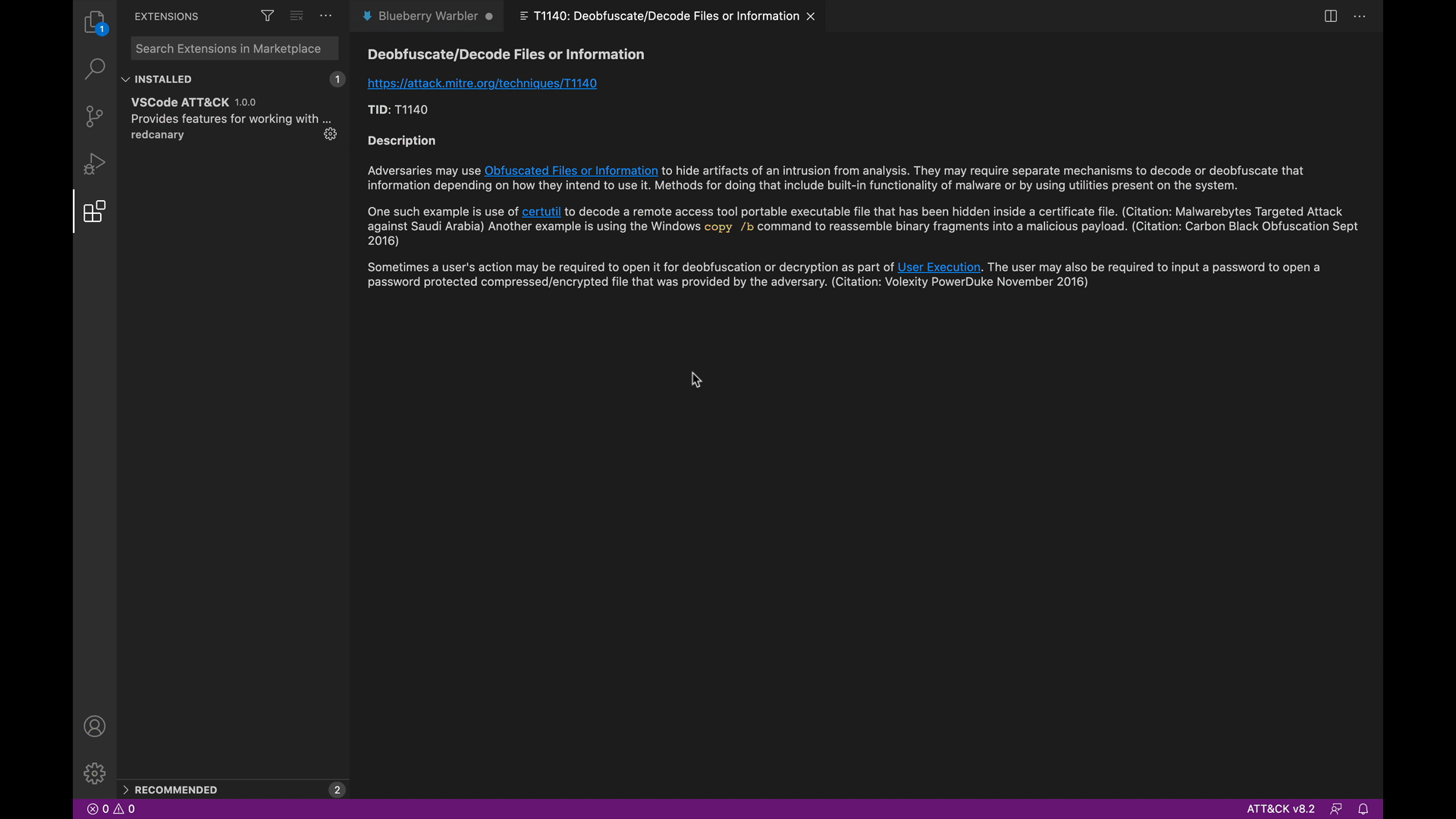
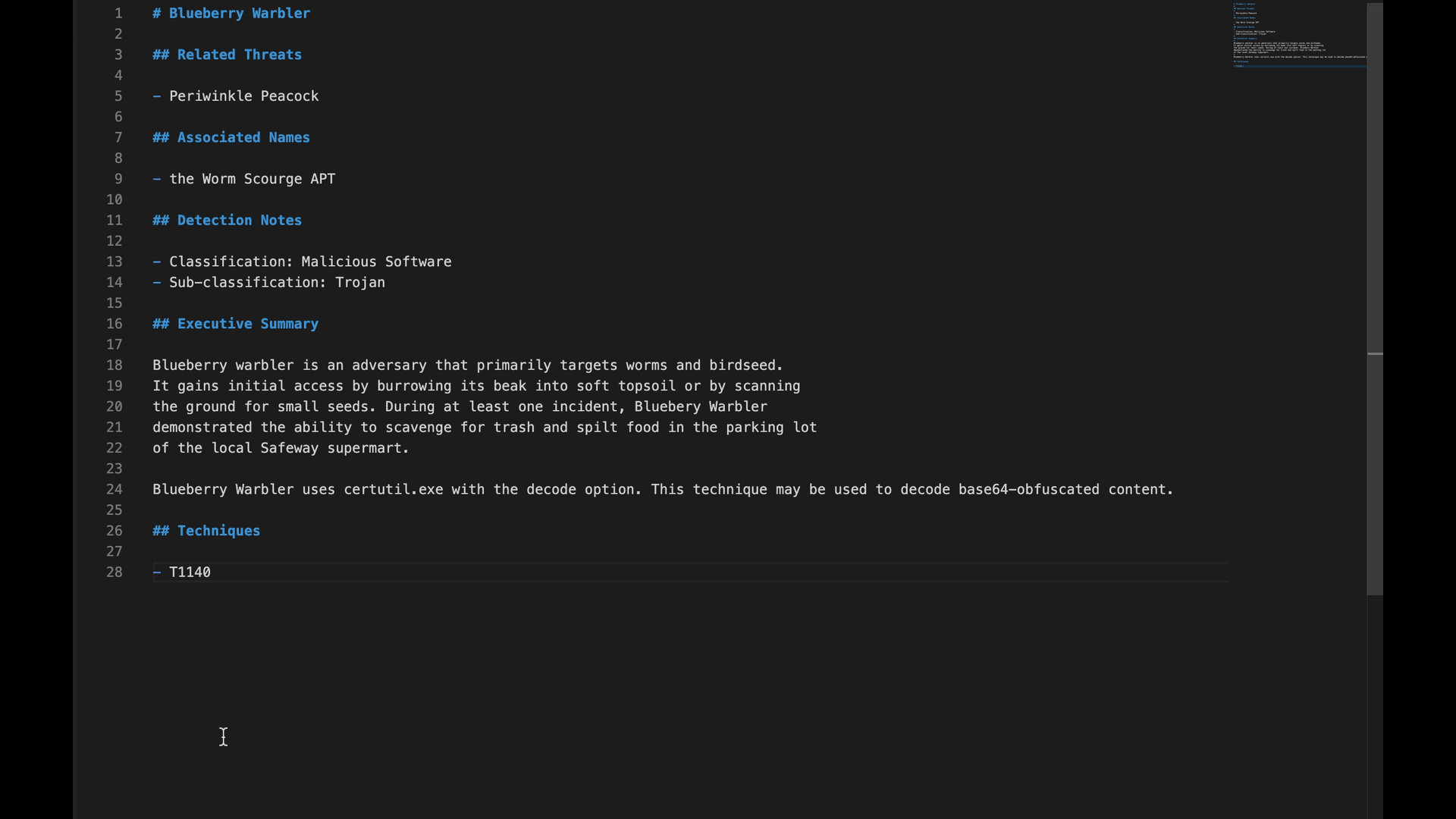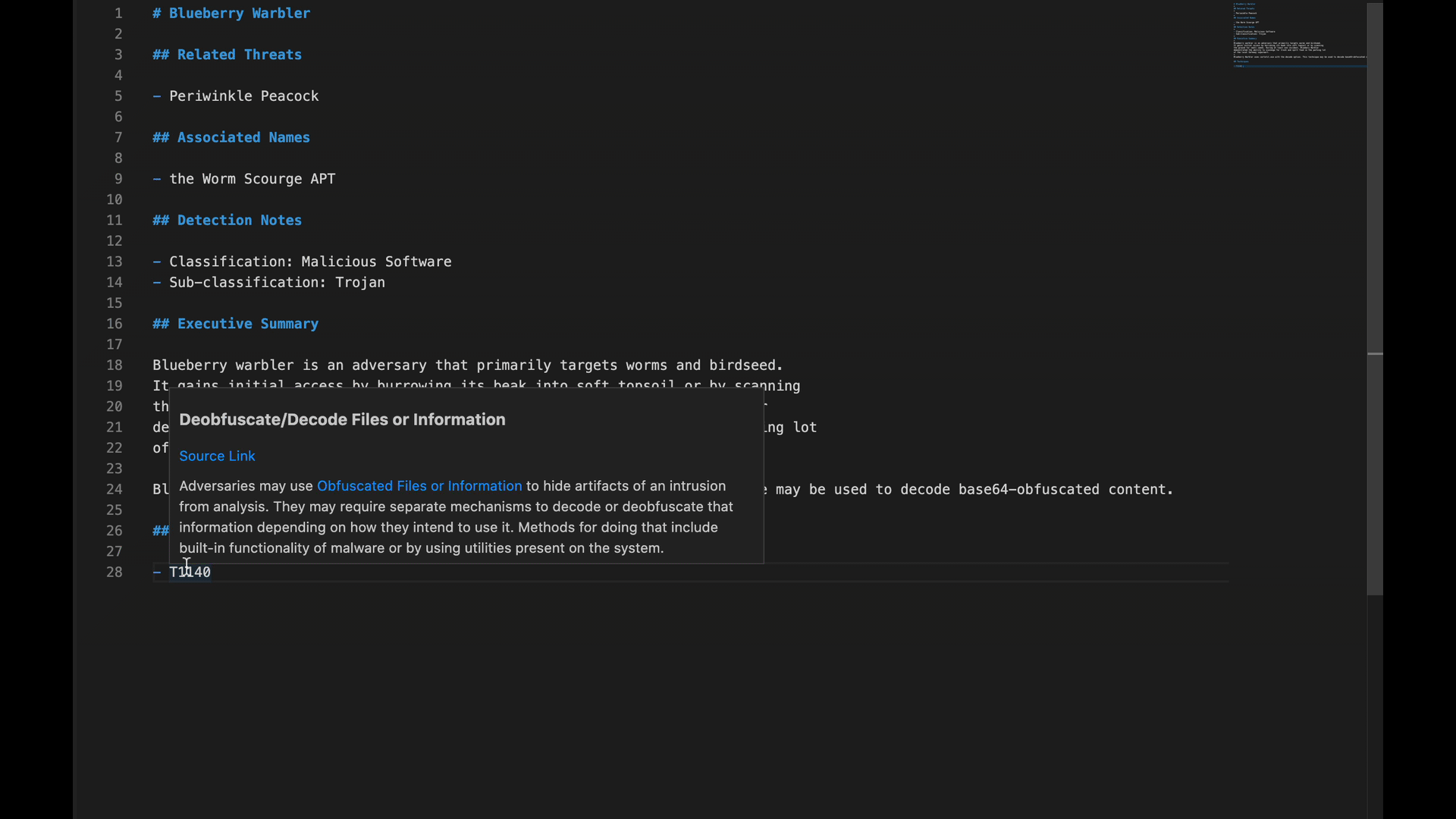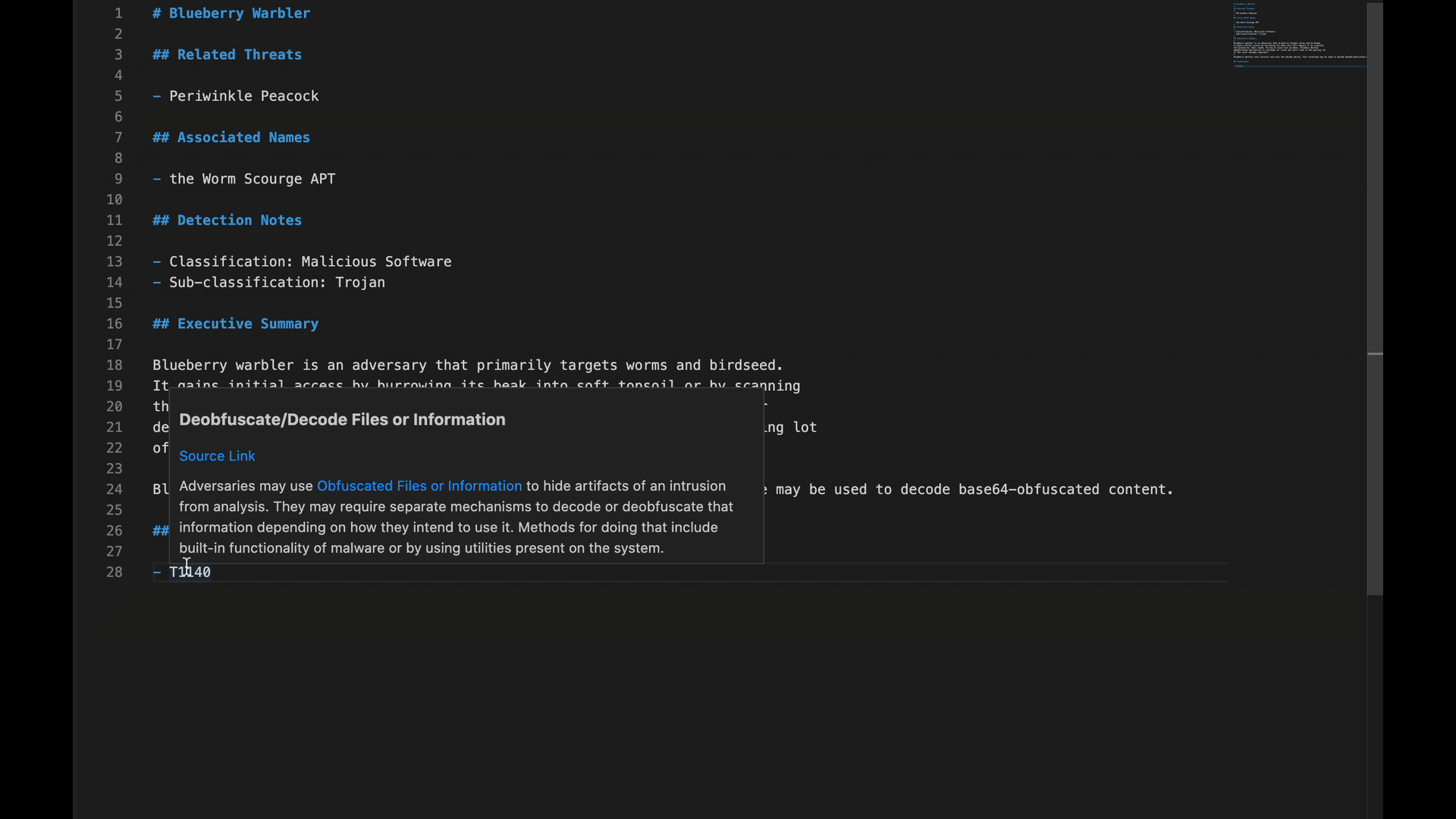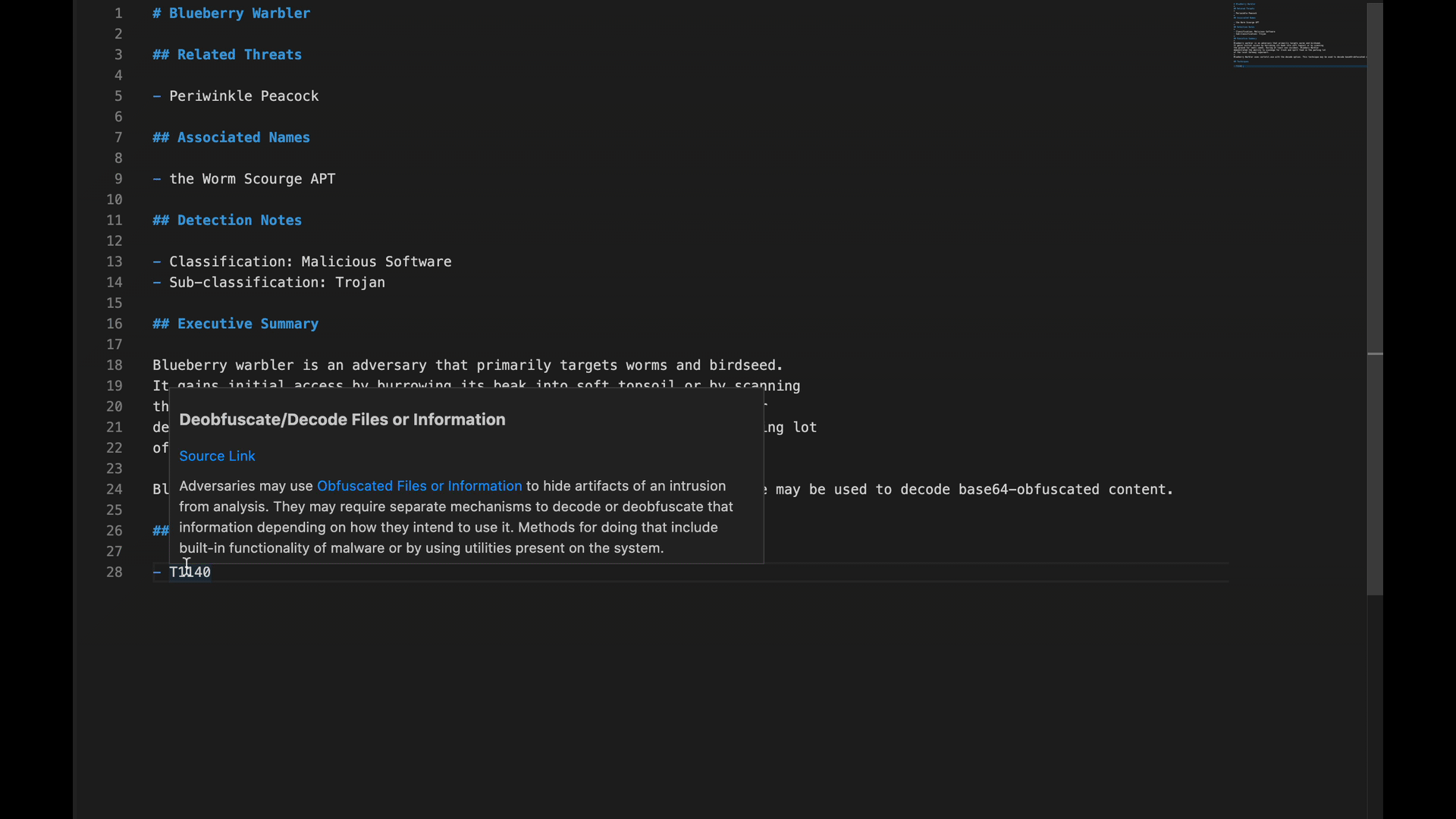
If you already know that certutil.exe is mostly closely related to T1140: Deobfuscate/Decode Files or Information, then VSCode-ATT&CK can auto populate that technique as you begin to type.
Additionally, if you encounter just a technique ID, like “T1140” for example, and you aren’t sure what exactly the technique refers to, you can hover over “T1140” to see MITRE ATT&CK’s description of the technique without having to pivot out of the VSCode interface.
More to come
We developed VSCode-ATT&CK to satisfy our own internal needs, which are relatively narrow. Even so, we’ve still got a short list of of features we’d like to add moving forward in order to satisfy some additional use cases we’ve uncovered in the process of releasing this thing to open source.
The general purpose of open sourcing is twofold: it makes a tool available to anyone who might want to use it, and it allows the community to contribute to the development of the tool. We certainly hope that members of the infosec and ATT&CK community both find this tool useful and contribute new features that satisfy their own use cases. If you have any questions or ideas about this new tool, don’t hesitate to reach out.