We think differently
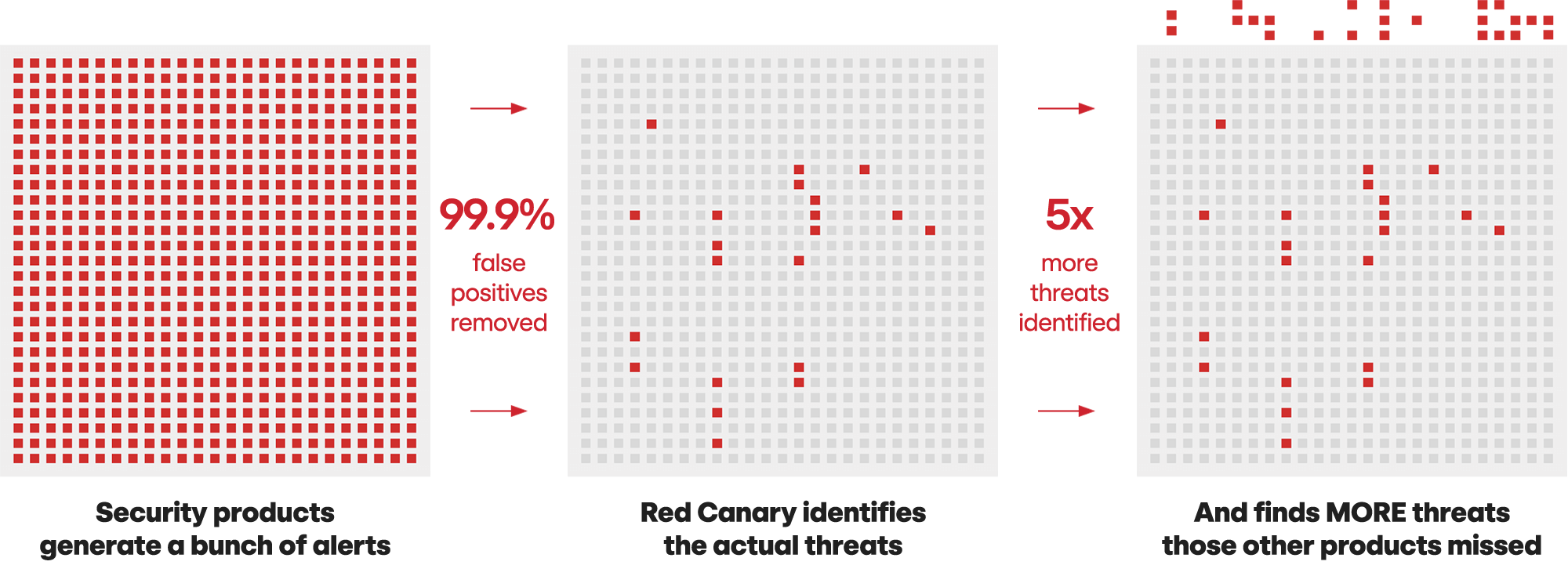
While most managed detection and response (MDR) vendors depend solely on the alerts from your security stack, we built a platform that ingests both alerts and raw telemetry. Raw data enables us to find more threats and to provide you with better protection from a breach. Security solutions inherently will miss threats, as they are built to detect and flag threats with an acceptable level of noise. We don’t believe it makes sense to build an MDR solution upon a flawed foundation.
We hunt differently
We detect threats that no one else does. Red Canary optimizes for coverage and cast the broadest detection net possible with more analytics and security telemetry than anyone else. We also focus on and dive deeper where the “threat action” happens in your environment.
3000+
Analytics
20000+
Detection Coverage Tests
1+
Petabytes of security telemetry per day
We treat you differently
You deserve the best possible security and an ally in the fight. We’re always here for you—you have unlimited access to our security teams whenever you need us, at no additional cost. Our pricing is simple, all-in, and predictable. It’s a flat price per endpoint/per year: no complicated bundles and no ”gotchas”—plus, professional services are included at no additional cost.
We’re all in this together. That is why we make our community education and open source tools available to everyone.
Learn more about our capabilities
We keep you focused on your mission
We truly care about serving security teams and making information security better. We know firsthand the stress of defending an organization against cybersecurity threats. And that fuels our passion for making the information security community more open and collaborative.
Our values
We are relentless
Our adversary is very human and relentless in their crimes. We are equally relentless in finding and stopping those adversaries. Security teams we partner with have to be ready 24×7, and we are always there alongside them. Every time we ship code, respond to a support request, or coach our partners, we always push to go a little faster.
We always deliver quality
Our industry is littered with products that were well loved when they were small but lost their quality as they grew. We obsess over not being one of them. Our guiding principle is that we’ll try to grow as quickly as possible, while maintaining quality.
We are kind and authentic
Being kind is often a novelty in security and technology business, and we believe in changing that. We embrace our authenticity and show kindness to other Canaries, competitors, and the community.
We do what’s right for our customers
Our hypergrowth means we are making hundreds of decisions every day, and we believe we can quickly make the best decisions by thinking about what is best for our customers in both the near and long term.


“I view Red Canary as an extension of my internal team. I communicate with them 24 hours a day, 7 days a week. I feel like they care about our security as much as my internal team does.”