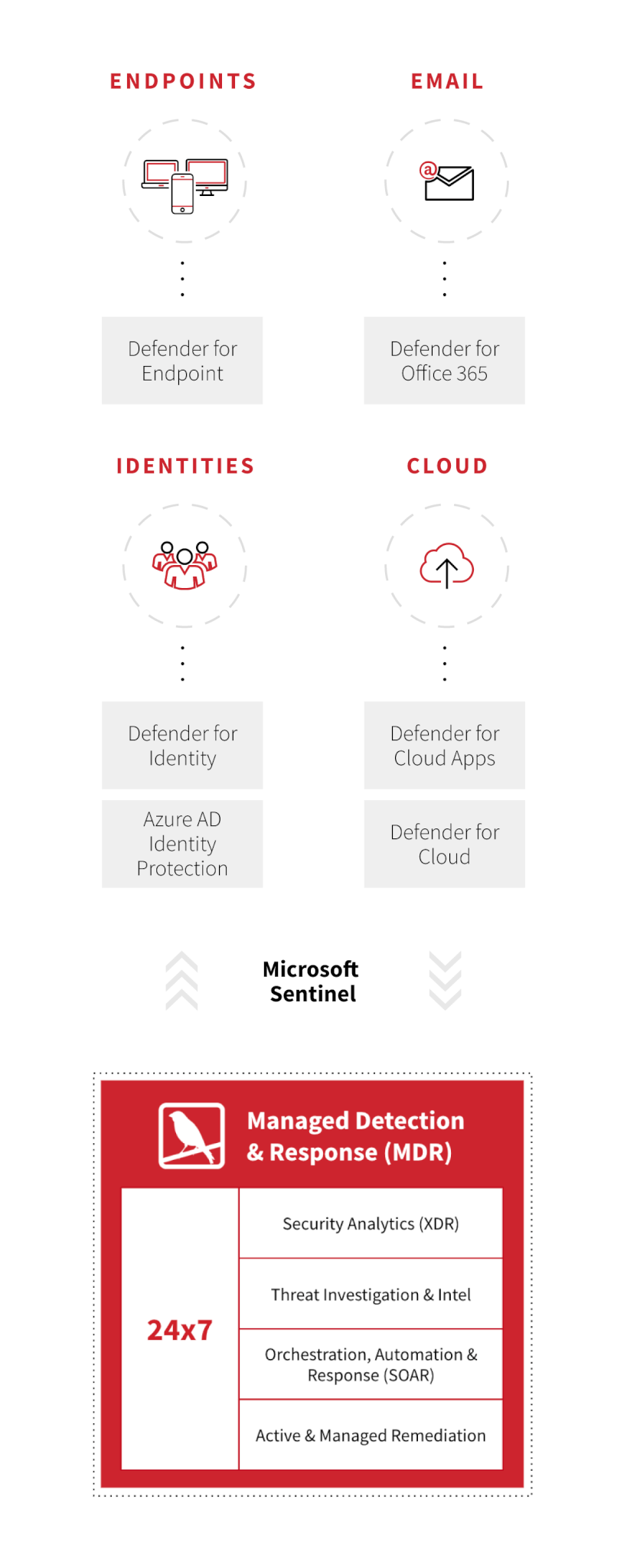
SECURE MICROSOFT 365
"It was the 24×7 support that Red Canary gave. It was that additional threat piece where we could import impossible travel alerts, access logs, and other things from Microsoft 365."”

THE BENEFITS
24/7, Microsoft-focused threat coverage
Our detection engineers monitor and proactively hunt for threats across your environment around the clock. When we confirm a threat, we notify you immediately and present relevant context from across your Microsoft security stack and other tools to you via a unified threat timeline.
Offload alert review and investigation
Send your Microsoft alerts to Red Canary: our experts and autobots will separate signal from noise and we notify you only when we’ve confirmed suspicious activity. We can pivot into your Microsoft Sentinel environment to investigate as necessary, and you can review the alerts that matter in Sentinel or Red Canary, whichever platform you prefer.
Catch threats you would otherwise miss
Our proprietary detections increase your coverage. For example, we help you detect 3.8x more threats on average than you otherwise would using Defender. We apply these high-fidelity, behavior-based detections to raw telemetry across your endpoints and cloud.
Respond and remediate faster
Our automated playbooks integrate with Defender’s LiveResponse API and your other security and IT tools to contain threats and notify internal teams upon threat confirmation. Want us to respond on your behalf? No problem: with Active Remediation, our Threat Hunting Team will provide hands-on-keyboard response to ban IP addresses, collect forensics, quarantine files, and much more.
STREAMLINE YOUR MICROSOFT SECURITY OPERATIONS
“With identity there’s a lot of data and it’s difficult to track down. Red Canary far outmatches our ability to get high-fidelity detections and see the value of Defender for Identity alerts.”
Grover Mewborn
Cybersecurity Technical Team Lead, CoStar Group
Quantify Your Security Improvements
Red Canary MDR for Microsoft reduced one technology company’s alert volume by 90 percent. They used to see 55+ alerts daily; with Red Canary filtering out all the false positives, the SOC team now averages about one alert a week confirmed and shipped to them by Red Canary. As an added benefit, they achieved these outcomes without deploying any agents.
95%
productivity increase
90%
reduced alert fatigue
55+
daily alerts to 1x per week