threat
IcedID
IcedID, also known as Bokbot, is a banking trojan often delivered through phishing campaigns and other malware. In 2020, it was most commonly found as the result of TA551 initial access.
Threat Sounds
Editors’ note: While the analysis and detection opportunities remain applicable, this page has not been updated since 2021.
Analysis
IcedID is a crimeware-as-a-service banking trojan that steals sensitive financial information by creating a local proxy to intercept all browsing traffic on an infected host. First appearing in the wild in late 2017, IcedID is believed to be the successor to the formerly prolific Vawtrak (aka Neverquest) trojan, which declined following the arrest of key developers in January 2017. IcedID has historically been delivered as a later-stage payload from a variety of notable threats, including Emotet, TrickBot, and Hancitor. In 2020, the primary initial access vector Red Canary observed delivering IcedID was TA551. Early in the year, we often saw IcedID as a tertiary payload after TA551 initially deployed Ursnif or Valak. However, by July the intermediary payloads ceased as TA551 opted to deliver IcedID directly. Since TA551 ranked as our most prevalent threat for 2020, it is no surprise that IcedID—its primary payload—also placed near the top of the list.
Installation and execution
After the installer DLL is executed, IcedID pulls down a configuration file from its command and control (C2) server. It then spawns an instance of a legitimate process and hooks multiple Windows APIs in order to hollow that process and inject into it. Throughout most of 2020, msiexec.exe was the target of this process injection, although IcedID has used other processes, such as svchost.exe, in the past.
Once execution has been achieved via the hollowed process, IcedID proceeds to establish persistence and act on objectives. IcedID achieves persistence in multiple ways, notably via downloading an additional binary (in EXE or DLL form) to the user’s local folder. We’ve observed a few different folders where the binary has been written, typically either in a subfolder of AppData\Roaming or AppData\Local. In some cases this subfolder has been named after the username of the infected user, and in others it appears to be a random string of characters. IcedID then sets that binary to run via scheduled tasks. Upon restart, this persistence mechanism will execute the process hollowing routine again to return control to the main backdoor.
Main payload
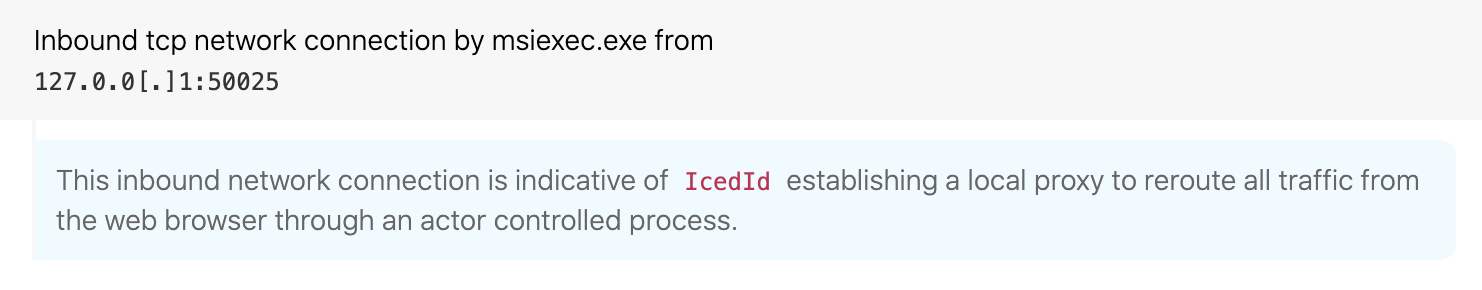
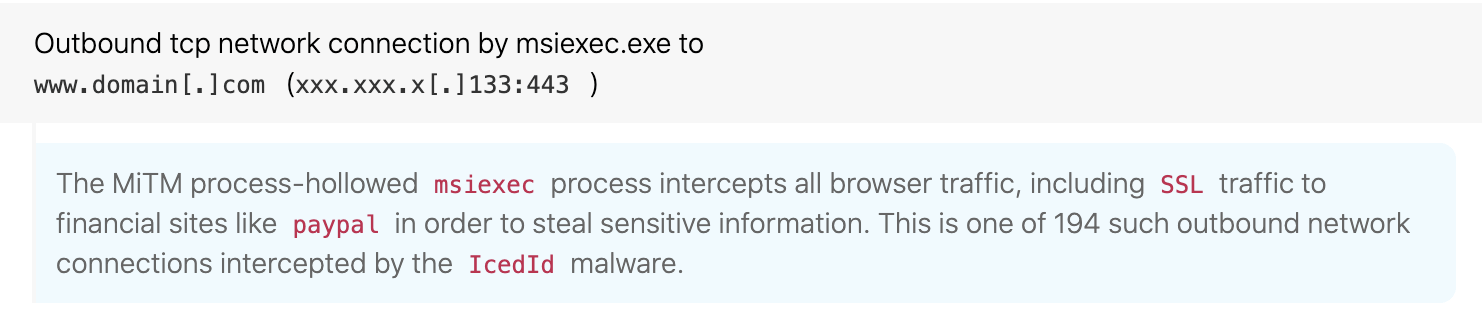
The primary purpose of the main backdoor is to steal sensitive data—in particular, browsing data including banking information. This is accomplished by hooking the browser and establishing a local proxy complete with self-signed certificates to reroute all web traffic through the adversary-controlled process. This enables the adversary to not only monitor traffic of interest, but also to use web injects to harvest information when a user attempts to visit a site such as online banking. In addition to data theft, IcedID contains a VNC capability for remote access to the victim machine. Juniper Threat Labs and IBM X-Force have also covered IcedID’s capabilities and injection techniques.
Detection opportunities
Detection opportunity 1
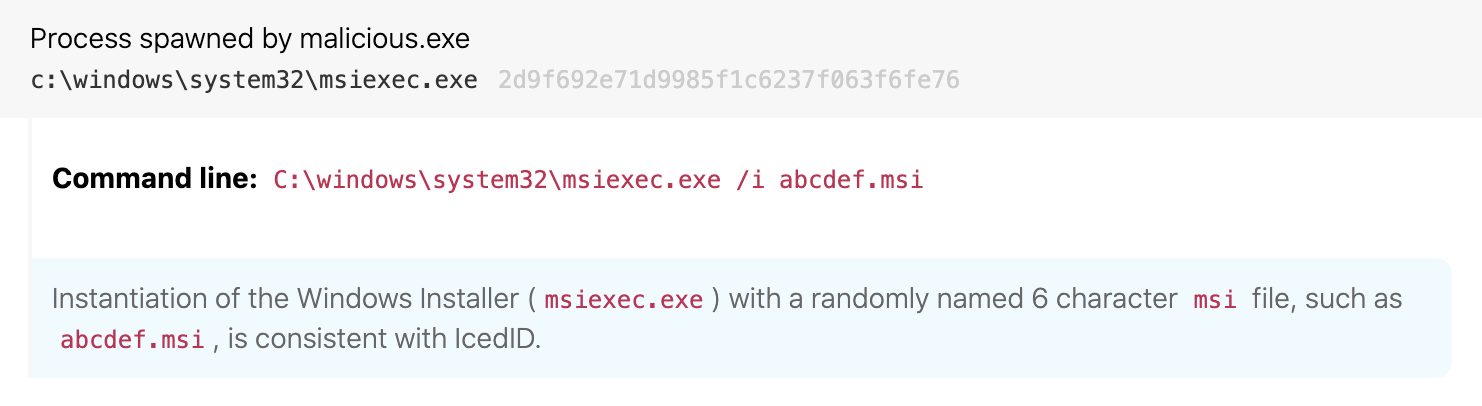
Process hollowing msiexec.exe with randomly named .msi file
ATT&CK technique(s): T1055.012 Process Injection: Process Hollowing, T1185 Man in the Browser
ATT&CK tactic(s): Defense Evasion, Execution
Details: IcedID uses a process-hollowed instance of msiexec.exe as a proxy to intercept all browsing traffic. Despite the attempts to blend in, it is unusual to see a “product” named with six random letters in the msiexec.exe command line.
Coupled with that unusual MSI package name, the man-in-the-middle (MitM) proxy creates unusual network connections for msiexec.exe as it intercepts all traffic from the user’s browser.
Detection opportunity 2
Scheduled task persistence from user’s roaming folder with no command line
ATT&CK technique(s): T1053.005 Scheduled Task/Job: Scheduled Task
ATT&CK tactic(s): Persistence
Details: One way IcedID persists is via the Windows Task Scheduler. A good detection opportunity for a variety of threats is to look for scheduled tasks executing from the %Users% folder. In particular, we have found that such tasks executing without any command-line options tend to be more suspicious. The random nature of both the file being executed and the folder containing that file are common traits of not only IcedID, but a variety of malicious and unwanted software.
Detection opportunity 3
Suspicious child processes from msiexec.exe
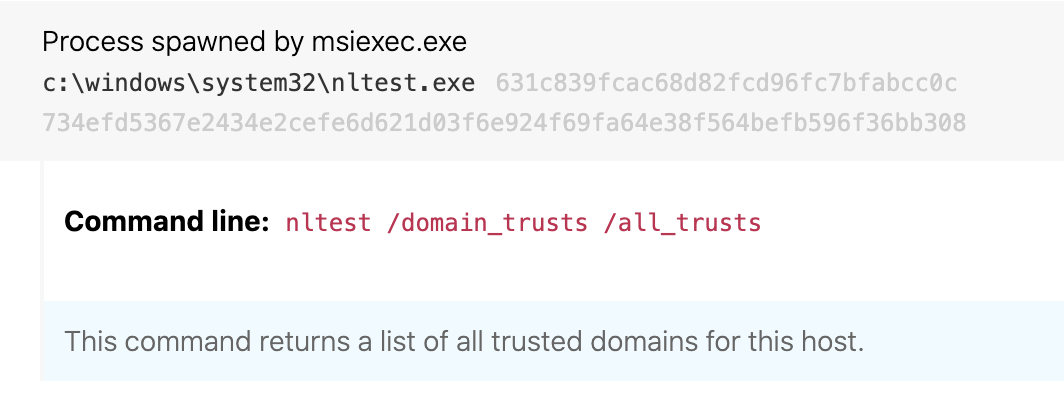
ATT&CK technique(s): T1482 Domain Trust Discovery, T1082 System Information Discovery
ATT&CK tactic(s): Discovery
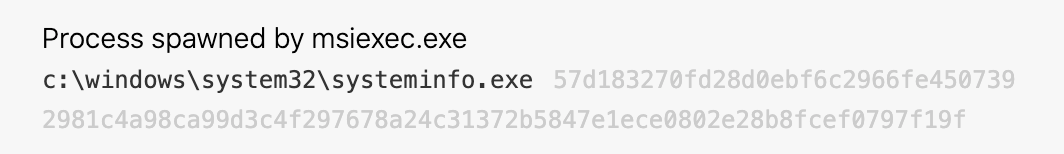
Details: Detecting techniques in the Discovery tactic is one of the most daunting tasks for a security team. Typically the commands used for discovery are the same commands system administrators run as part of normal IT operations. One way to distinguish legitimate discovery commands from suspicious ones is to look for unexpected parent/child process relationships. In the case of IcedID, the activity stems from the process-hollowed instance of msiexec.exe. The IcedID sysinfo command executes several specific commands that are highly unusual to see coming from msiexec.exe. Each of the commands below are unusual to see as child processes of msiexec.exe in some way or another. In some cases, the simple process execution stands out—systeminfo.exe and nltest.exe fall into this category of processes we almost never see executed by a legitimate instance of msiexec.exe.
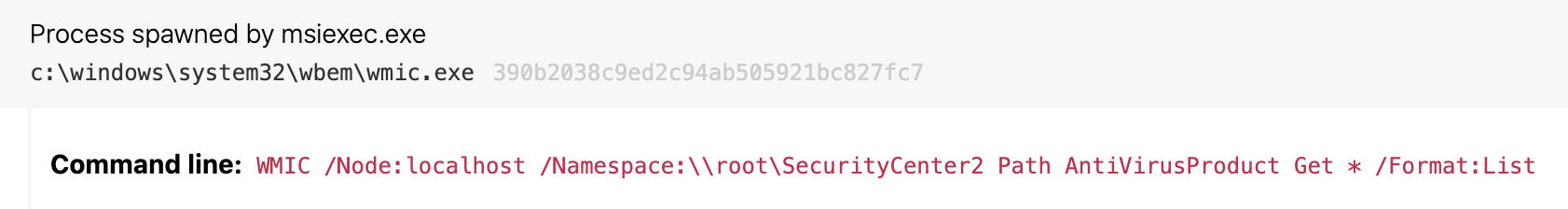
In other cases, the abnormality is a bit more nuanced, and we have to consider the command-line behavior of the child process. For instance, it is uncommon to see msiexec.exe execute wmic.exe to query the installed antivirus (AV) software, as seen in the below screenshot. This is a parent-child process relationship that, when combined with the command line, provides a detection opportunity.