Earlier this year, each member of the Red Canary threat research team had the opportunity to choose a featured MITRE ATT&CK® technique and analyze it for the 2023 Threat Detection Report. On the macOS end of the spectrum, we decided to take a closer look at Apple’s software inspection and verification technology, Gatekeeper.
We’re no stranger to Gatekeeper at Red Canary—having written extensively about it and helped influence ATT&CK’s technique (T1553.001) for it. However, in the process of conducting threat research with a then-private version of our Mac Monitor tool to develop a pair of detection heuristics that’ve been on our wishlist for a while, we discovered two novel and exploitable vulnerabilities.
Both vulnerabilities could enable an adversary to bypass Gatekeeper by evading a related security control called File Quarantine.
Discovering CVE-2023-27951 and CVE-2023-27943
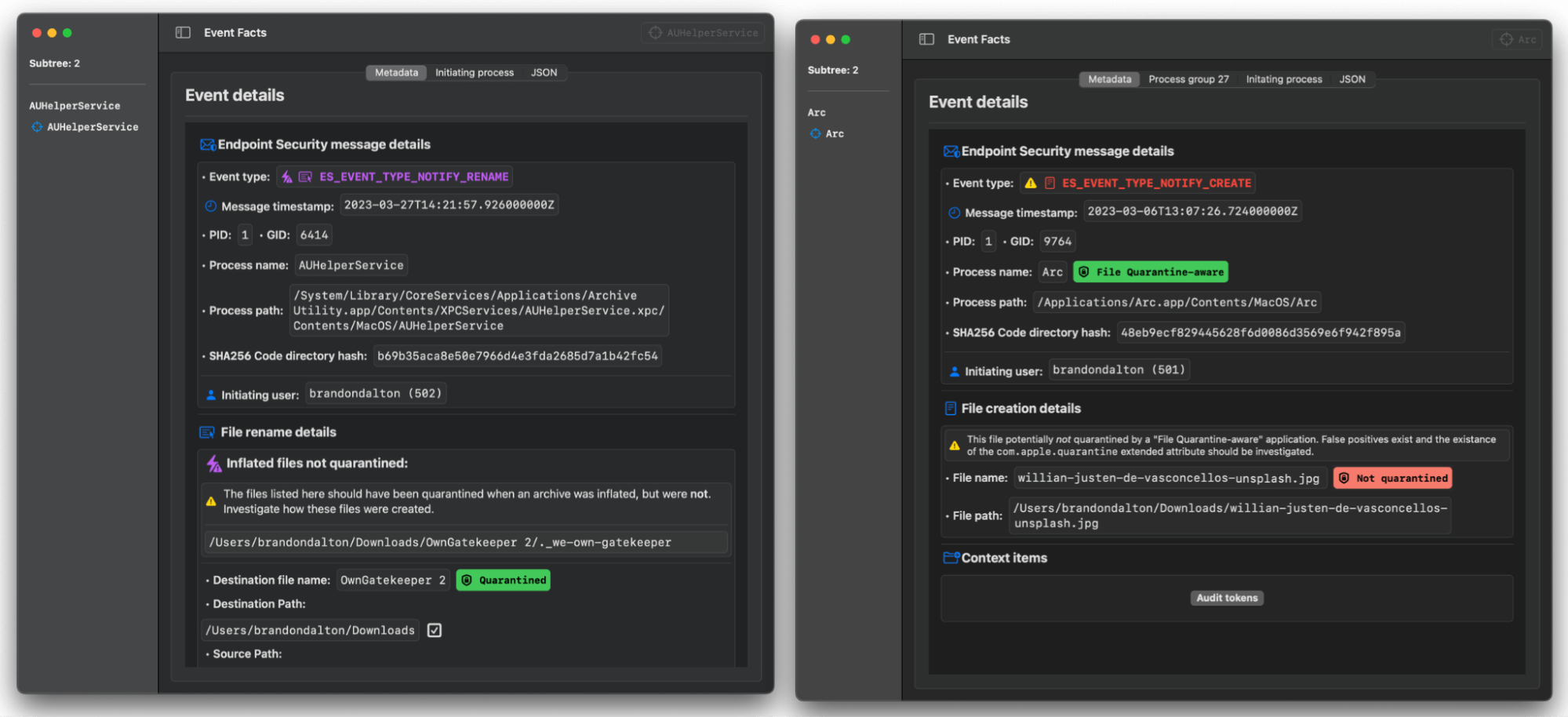
We needed a way of validating that macOS was quarantining and inspecting the files that were supposed to be quarantined and inspected. So we developed these detection analytics and implemented them in Mac Monitor to do exactly that. In the process of testing these analytics, we found a way to trick macOS into mismanaging the application of quarantine flags that prompt inspection by Gatekeeper.
The “quarantine flag” (com.apple.quarantine) is an extended attribute whose data is stored in resource forks. After digging in for a short while, we came across an interesting bit of code from the “virtual file system” implementation: darwin-xnu/bsd/vfs/vfs_xattr.c
/* "._" Attribute files cannot have attributes */
if (vp->v_type == VREG && strlen(basename) > 2 && basename[0] == '.' && basename[1] == '_') {
error = EPERM;
goto out;
}
This same concept shows up elsewhere in the code. Naturally, we wanted to know what would happen if we crafted a Mach-O binary named with the prefix of a resource fork file, ._. So we compiled a simple Mach-O with that prefix, compressed it into an archive, downloaded it with Safari (a File Quarantine-aware app), and immediately noticed the file was not quarantined—but in fact, readily executable.
We reported this to Apple on January 27. They later acknowledged the bug, codified it as an archive utility problem with CVE-2023-27951, patched it, and recognized us and Csaba Fitzl (@theevilbit) for discovering and disclosing it.
Finding non-quarantine aware software
After reporting this issue to Apple, we also noticed some of our favorite software was not File Quarantine-aware (i.e., it failed to apply the file quarantine attribute to downloads). One of these was Arc, a web browser developed by The Browser Company. The team quickly responded to our security feature request and enabled File Quarantine for Arc by adding LSFileQuarnatineEnabled to the Info.plist of Arc itself and all of its helpers. This, according to Apple, opts the application into File Quarantine, and nothing else is needed to be done by the developers.
However, we noticed something curious: After we updated Arc to the File Quarantine-aware version, it still was not quarantining downloaded files. Initially, we thought this was an issue with Arc itself, so we reported it and waited.
Finally, after directly posing the question on Apple’s developer forums, we decided to submit the issue to Apple Product Security on March 4 with what we knew, including the telemetry from Mac Monitor. Apple promptly assigned CVE-2023-27943 to it, said it impacted LaunchServices, fixed it, and credited an anonymous researcher, us, Milan Tenk, and Arthur Valiev for its discovery.
The heuristics mentioned in our Threat Detection Report page on Gatekeeper Bypass are baked into Mac Monitor by default. Here are two of them in operation detecting each of these zero days.
These vulnerabilities were patched with the release of macOS 13.3 (Ventura), 12.6.4 (Monterey), 11.7.5 (Big Sur), and *OS 13.4 (for CVE-2023-27943 only).
Conclusion
Huge thanks to Apple and The Browser Company for promptly fixing the vulnerabilities and bugs mentioned in this article, and to all the great researchers out there who find and responsibly disclose security vulnerabilities!
Stay tuned for additional blogs, videos, and more exploring the many use cases for our newly released (and free!) dynamic analysis and collection tool, Mac Monitor.