Imagine any typical Friday afternoon at your organization. Everyone is wrapping up their work, looking forward to a break from the hustle and bustle of the daily operations. At 4:30 PM, your accounts payable administrator receives a PDF document containing an invoice that appears to have gone unpaid for almost 90 days. She examines the document, but cannot recall using that specific vendor, so she sets it aside to ask about it on Monday before turning off her screen and heading out.
Unbeknownst to her and to the rest of the organization, the PDF document executed a script that subsequently downloaded the first stages of malware that allowed an undetected adversary to gain control of the system and launch a ransomware attack. The first sign that something was amiss was the call that the security officer received Sunday morning from a network operations technician who indicated that nearly 70 percent of all the systems on the network were infected and encrypted.
While this may seem like a far-fetched scenario, the reality is that ransomware operators and other adversaries have been able to go from an initial infection to complete control over a network in less than two days. The DFIR Report recently described a Conti ransomware affiliate that was able to pivot from an initial infection with Bazaar Loader to an enterprise-wide encryption with Conti in 32 hours.
Keeping up with the bad guys
The speed with which adversaries operate forces a reexamination of incident response (IR) and incident management, with an eye on building in as much automation and efficiencies as possible so that security teams can keep potential damage to a minimum. Having a plan that takes into account automated and manual processes—coupled with technology—goes a long way to reducing the potential for a catastrophic impact to the organization.
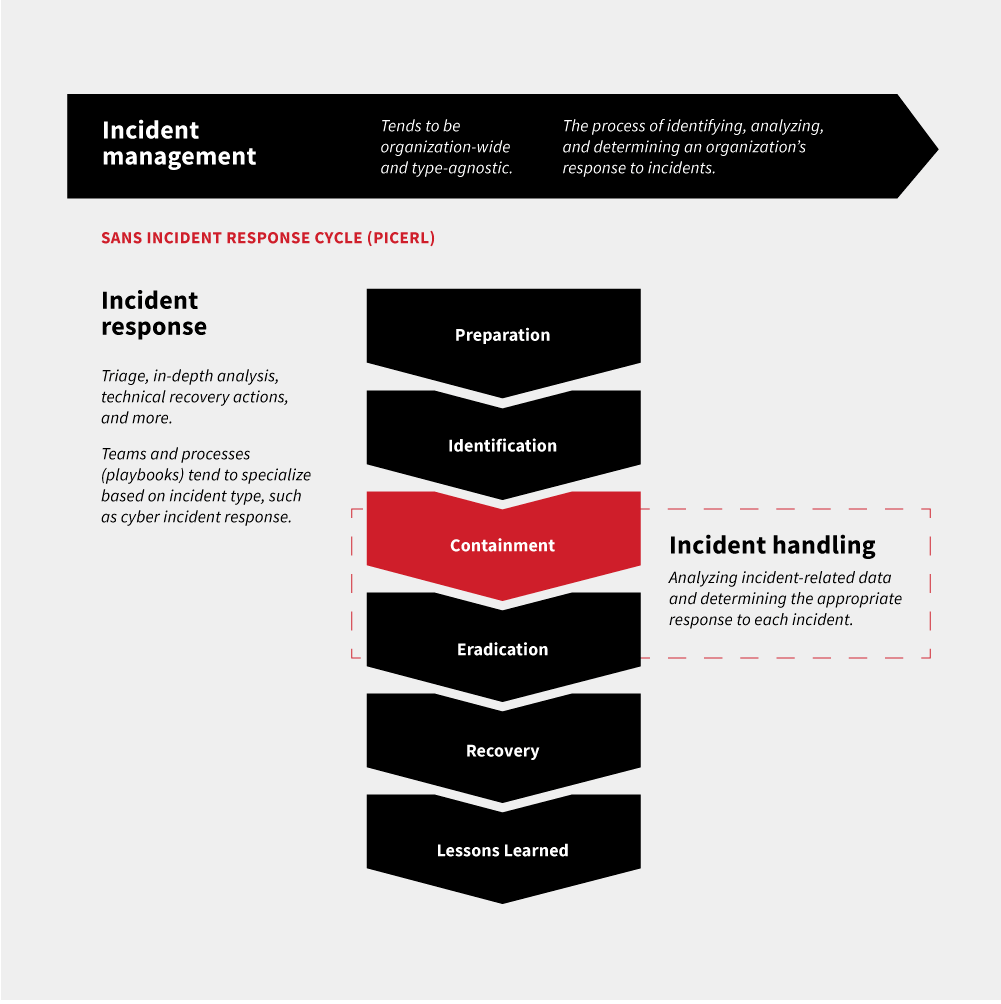
Incident handlers tend to operate at the epicenter of the SANS Incident Response Cycle, when a threat has been confirmed and malicious binaries have already been executed. Before we get into the nitty-gritty of the containment phase, it’s important to place it in the overall context of IR. Note that this phase comes directly after the identification of an incident.
Timely detection is a critical component to reducing the impact of a cyber incident. Mandiant’s 2021 M-Trends report calculated the mean dwell time (the time from an adversary’s initial access to detection) to be 24 days. Imagine for a moment the amount of damage an embedded attacker can wreak in even a 24-hour period. As mentioned above, the Conti ransomware group was able to move from initial access via the BazarLoader initial access tool to lateral movement in as little as two and half hours. In that time, the group was able to deploy Cobalt Strike, leverage Windows binaries to uncover information about the network, compromise credentials, and map the network. Security and network teams that can rapidly pivot from incident detection to containment have a far better chance of limiting the impact of an attack and getting back to normal operations.
Figuring out what to automate
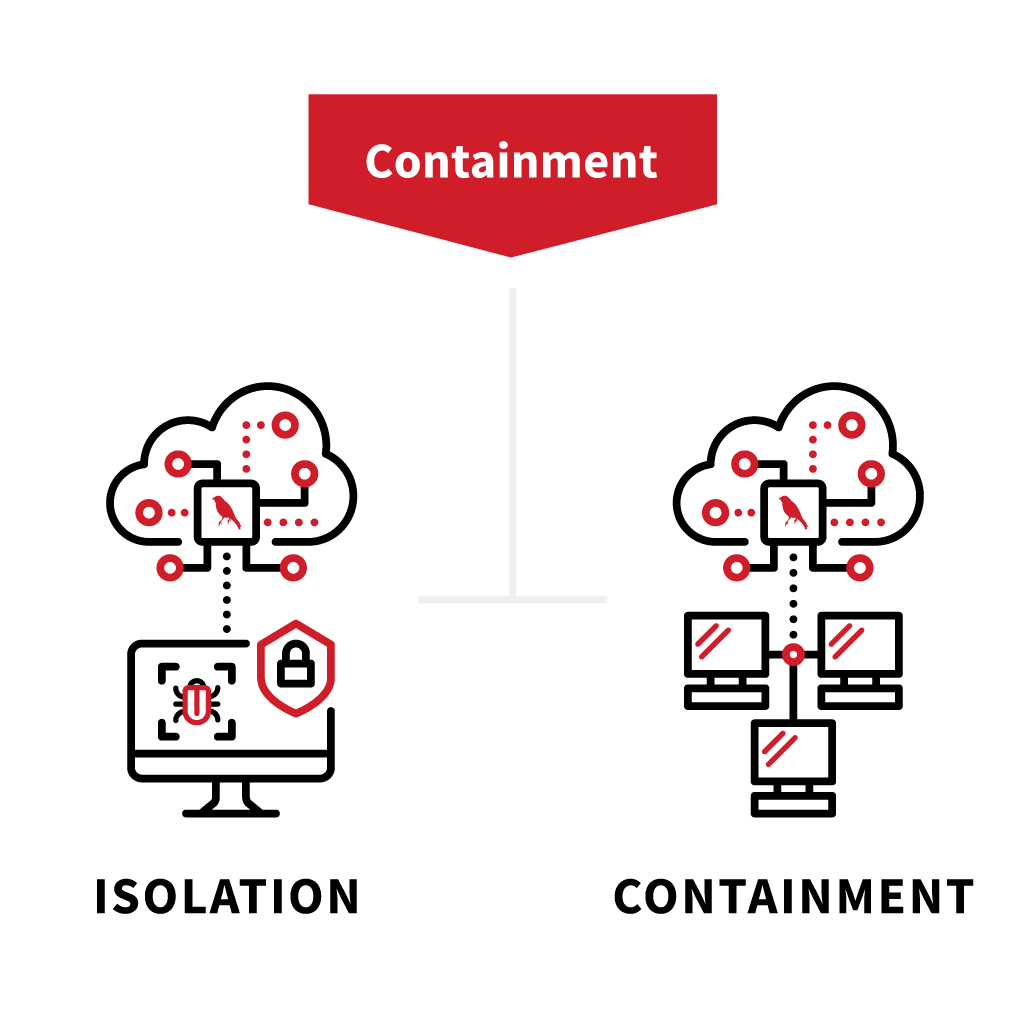
The containment stage of the incident management framework is actually two separate actions: isolation and containment. While the two are often conflated, there are significant differences in these two concepts.
Think of isolation as an automated function that is set to execute based on a specific trigger. This allows for minimizing potential damage to an endpoint without compromising the overall network operations by focusing on specific impacted endpoints.
Containment, on the other hand, involves more manual processes, where network operations or other situated personnel take actions such as changing VLAN communication or disabling user accounts to stop the spread of malware or other malicious activity. This type of action—though necessary, especially in ransomware cases—does have the potential to significantly impact network operations. The reason that containment is not automated is that every organization needs to weigh the costs of such activity in light of the type of incident that they are dealing with.
Identification to isolation: MDR to the rescue
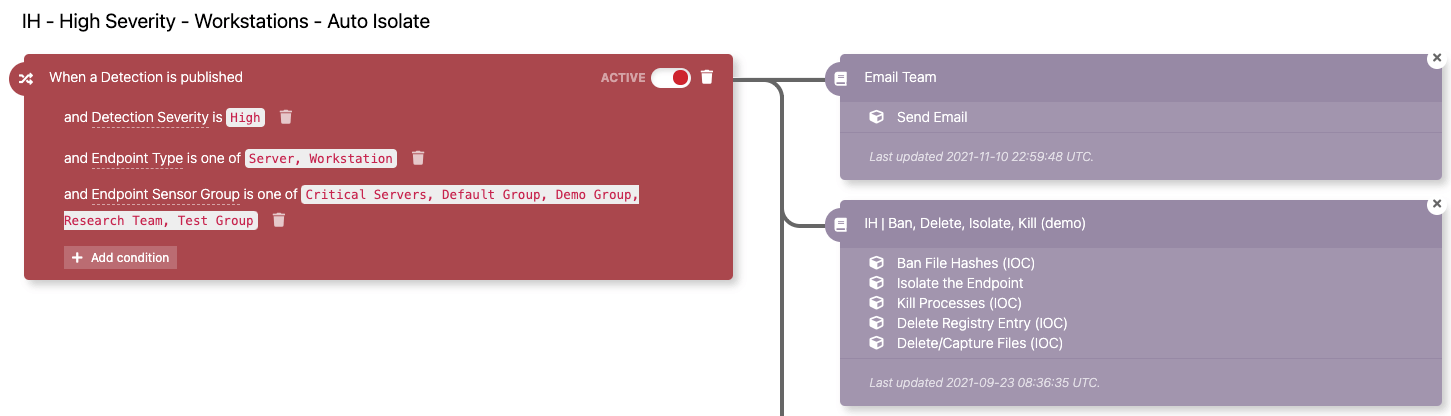
Red Canary’s advanced detection capabilities make use of known malicious indicators of compromise (IOC) through signature-based detection married with behavior-based detection, presenting the best option for identifying malicious activity. When the adversary executes malware or other malicious activity that matches these detection criteria, an alert is triggered.
Thanks to this alert, the Red Canary platform can immediately move to isolate the endpoint from the rest of the network without the need for any intervention.
In this case, the trigger—shown in red—is configured to alert when a high-severity detection impacts servers and workstations. The automated isolation function then kicks off and executes several tasks, most importantly killing the malicious process and isolating the endpoint.
Once this automated isolate feature triggers, the impacted organization is at a decision point. If this was a one-off detection, say someone had inadvertently opened a malicious attachment, there may be no need to escalate this further. The endpoint can be removed from the network, and the malware removed and then redeployed. In other situations, the detection may be indicative of a larger incident wherein the organization needs to contain the spread of the malware.
Isolation to containment: Make a plan
Executing containment requires escalating the incident into the proper resources. Where this escalation goes is dependent on the organization. Some may escalate network containment to the network operations team. In other cases, it is escalated to the security operations team. In any case, there should be plans and procedures in place that identify who is responsible for executing network containment and under what circumstances.
For example, suppose that an adversary was able to gain access to systems on the internal network and cause a widespread infection. In addition to the infection, the adversary has established command and control (C2) with their infrastructure. A containment strategy should focus on first limiting connectivity to the adversary’s infrastructure followed by limiting connectivity between LAN segments.
Allow the network operations personnel to craft a firewall rule to block C2 traffic without having to navigate through various levels to get authorization. Your containment playbooks should contain the following scenarios, at a minimum:
- Disabling compromised user/admin accounts. A large number of attacks involve compromising credentials. This includes user and service accounts. Incident management playbooks should include workflows on who and under what circumstances these accounts can be disabled.
- Blocking lateral movement. Lateral movement is one of the key tactics employed by ransomware operators. Using a combination of compromised credentials and legitimate network tools, adversaries connect to additional systems to pilfer data and deploy ransomware. Playbooks that address the rapid containment of LAN segments or the removal of system to system connectivity such as Remote Desktop or SMB are critical in reducing the impact of a ransomware incident in progress.
- Disconnecting the infected machines or network. In a network-wide attack, it may be necessary to remove network connectivity to specific LAN segments or even the entire network as a whole. This can be considered the “nuclear” option with regards to containment. In incidents that span a wide range of the network, it is often necessary. One strategy is to cut off network connectivity, recover specific network segments based on priority, and then return connectivity in a staged approach. This staged approach allows for more granular control while minimizing damage as much as possible.
Speed things up
Proper containment strategies are imperative to limit the impact of an intrusion. Here are a few steps that you can take to accelerate this process.
- In addition to the aforementioned playbooks, ensure that you have appropriate personnel with the authority to take independent action in the event of an incident that impacts the entire enterprise.
- Automate the isolation of as many infected systems as possible. This significantly reduces the ability of an adversary to propagate malware and additional tools into the network.
- Train teammates and test your plan. Everyone that is involved with containment execution needs to be fully aware of their roles and responsibilities. They should also have had the training necessary to carry out those responsibilities. Finally, a tabletop exercise that runs through the process will help identify any gaps and potential repercussions that may have been overlooked.
In the rapidly accelerating attack tempo, having the necessary planning and ability to execute both isolation and containment is critical to limiting the damage from ransomware and other attacks. If these strategies were in place that fateful Friday night, what would have been a catastrophe could have been limited to a single infected endpoint that needed to be cleaned up. A combination of carefully thought out and tested automated and manual processes will bring you a long way toward becoming a more resilient organization that does not get taken down.