Microsoft Sentinel has become a leader in the Cloud SIEM market, helping thousands of organizations centralize and operationalize data from across their environment. For Red Canary customers using Microsoft Sentinel, we designed and built a connector that enables you to:
- correlate Red Canary detections with Microsoft Sentinel data
- triage Red Canary detections in Sentinel
- reduce the cost of Sentinel by storing less data
The best of both tools
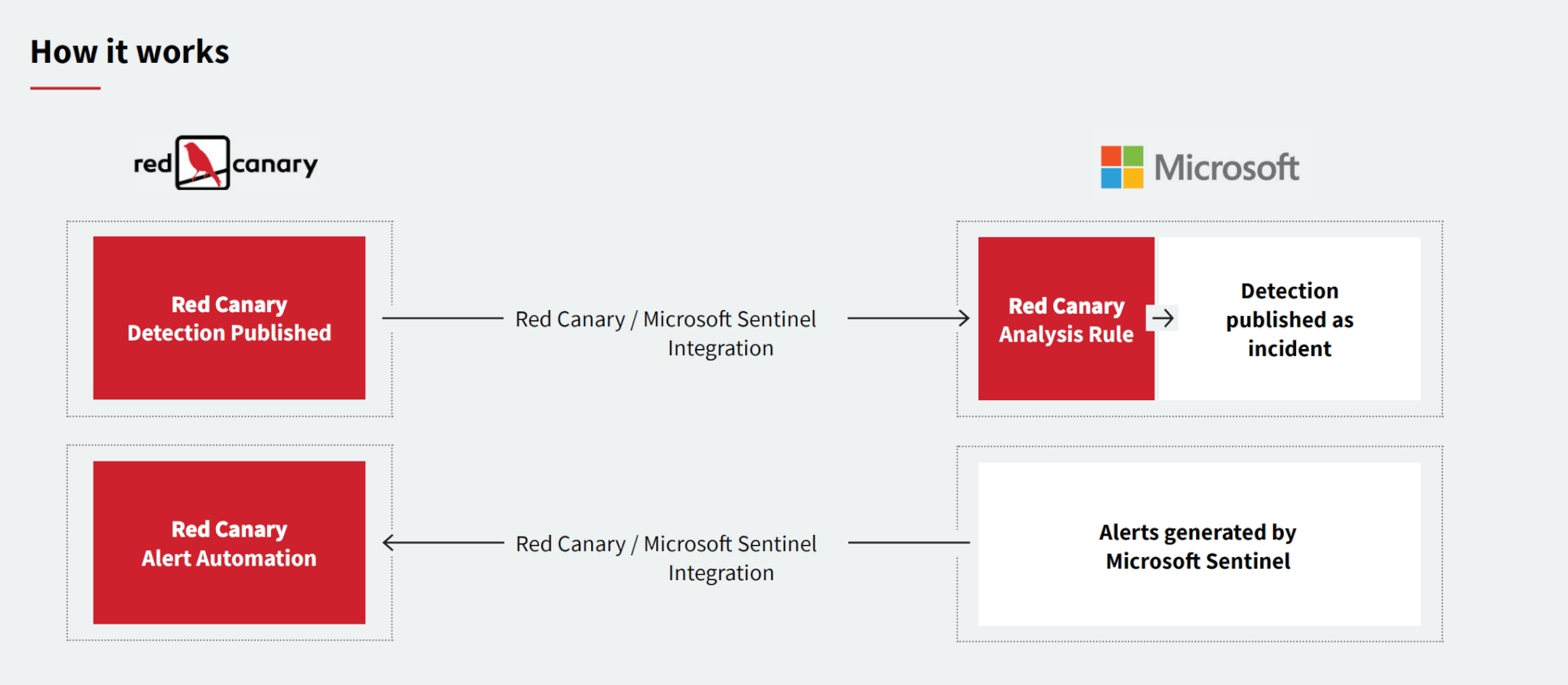
Red Canary’s integration with your existing Sentinel environment can be deployed in a few minutes and includes purpose-built Sentinel analytics rules to help you get the most out of the Red Canary data in Sentinel. The integration works bi-directionally, so you can easily configure it to fit your security operations workflow. Red Canary can push confirmed detections into the Sentinel platform, or collect alerts from Sentinel to be triaged in the Red Canary platform.
In Microsoft Sentinel, data from across your environment is stored and normalized for forensic analysis, threat hunting, and reporting. After configuring our Sentinel integration, Red Canary detections can be correlated and enriched with other sources of data that are stored in the SIEM. We’ve also developed an analytics rule that automatically elevates each Red Canary detection to an incident in Sentinel. The purpose-built rule also parses out indicators of compromise (IOCs) that Red Canary has associated with the detection and lists each out as an Entity, making it easy to pivot and interrogate key data to inform a response.
Automated triage
If you use the Sentinel platform for triage and response, this integration makes it simple to add Red Canary detections to the queue among your other alerts. Since Red Canary detections have already been triaged by the Red Canary Cyber Incident Response Team, we automatically elevate the detection to an incident within Sentinel so it can get attention quickly.
Alternatively, if you use Red Canary for triage, you can configure the platform to ingest alerts from Sentinel. In Red Canary, you can configure automation actions to notify your team when alerts meet your criteria, or configure response actions that automatically respond to alerts from Sentinel.
Save storage space—and money!
If Microsoft Defender for Endpoint telemetry is creating a cost burden within your Sentinel deployment, you can use Red Canary to analyze that raw telemetry data, and then only send confirmed threats and the data associated with those threats to Sentinel. If you then choose to stop sending Microsoft Defender for Endpoint telemetry directly to Sentinel, you will see significant reductions in data costs.
For your listening pleasure
Red Canary’s Cordell BaanHofman and Joe Savini recently stopped by Microsoft’s Security Insights podcast to discuss the two companies’ partnership and the new Sentinel integration. Listen below or here.