If we’ve learned anything from the onslaught of ransomware and other notable attacks fueled by the recent Log4j software vulnerability, it’s the importance of preparation. Sure, fine-tuning your security stack decreases risk from a technical standpoint, but what about mitigating the financial and legal complications post-compromise? Historically, few companies have considered these as key functions of preparedness, and ultimately incident response (IR). As more and more organizations fall victim, however, many are awakening to cyber insurance as a mechanism to offset the costs of responding to and recovering from cyber attacks.
Why do you need cyber insurance?
Cyber-related coverage is an important component of risk management. While it certainly won’t prevent an attack, it will help your company recover. Think of cyber insurance (and related policies) as a metaphorical life raft. Without it, organizations of all sizes and maturity—from Fortune 500 companies to street vendors—would struggle to stay afloat as the financial burden of damage caused by a cyber attack could reach into the millions. In 2021, the cost of the average ransomware breach rose to $4.62 million. Of course, direct and indirect costs of such an event depend on scope and complexity.
To properly assess and resolve a major incident, external Digital Forensics and Incident Response (DFIR) and legal counsel is often required. While this type of assistance is typically included in a cyber policy, companies without coverage often find themselves adrift in a sea of legalese, technical deficits, and unexpected invoices. This equates to greater risk exposure and potential catastrophe, especially if the root cause was not correctly identified and remediated. Likewise, it increases the risk of regulatory actions—and thus costs—if sensitive or personally identifiable information (PII) was inappropriately accessed, viewed, or altered. Simply put, adverse impacts to response, recovery, reputation, and revenue increase exponentially for companies that are uninsured.
Cyber policies are not created equal
The type of insurance policy you apply for—and ultimately opt into—could mean the difference in coverage and/or compensation in the event of a cyber attack. More importantly, the types of coverage and degree of protection varies by insurer as well. While there are numerous cyber-related policies, the following is intended to help guide you in eventual discussions with cyber insurance brokers.
Cyber liability insurance. This coverage typically provides protection from cyber attacks resulting in the compromise of network or personally identifiable information (e.g., DDoS attack, exfiltration) and includes some level of remediation and notification assistance. In some cases, such policies may even cover theft of company-owned mobile devices such as cell phones and laptops. Generally speaking, if your company handles credit card information, sensitive data, and/or operates in the cybersecurity space, you’ll want this type of coverage.
Crime insurance. In the context of cyber incidents, this coverage commonly provides protection against extortion and social engineering campaigns (e.g., ransomware, nation-state activity) that lead to direct loss of funds. However, with the swell of these types of attacks as of late, some insurers have updated policy vernacular to exclude coverage for targeted network compromises that are deemed an “act of war.”
What is behind the increased demands from insurers?
The short answer: simple economics. The volatile threat landscape has increased demand for coverage within the last couple years. In turn, the volume of claims has skyrocketed, ultimately pushing supply down and prices up. The average premium for cyber insurance coverage increased by more than 25% during the second quarter of 2021. And there’s no signs of it slowing as insurers grapple with payouts and the risk of taking on additional customers in this new era of digital warfare.
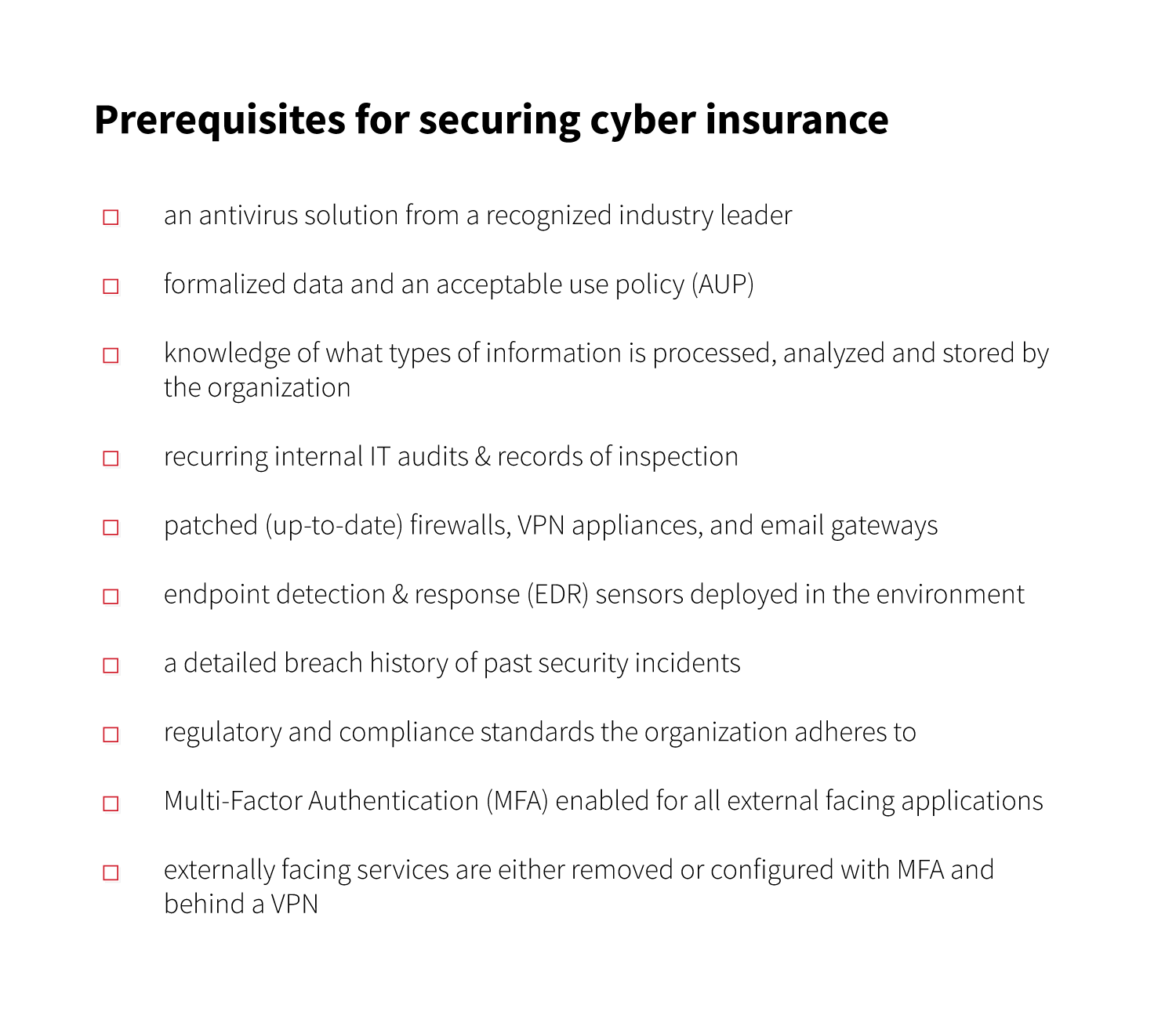
Poor cyber hygiene, noncompliance, and lack of controls are all things that sound the proverbial alarm for underwriters. The last thing they want is a high-risk customer that will more than likely require substantial bailouts in the future. The more risk you pose to an insurer, the less likely you are to receive a policy. Insurers want to know that your company is doing its part in preventing cyber attacks. Many require prospective customers to have reasonable security measures in place prior to applying.
To give you insight into what that means, we put together a checklist of requirements often sought by underwriters during the initial stages of consideration.
Applying for cyber insurance
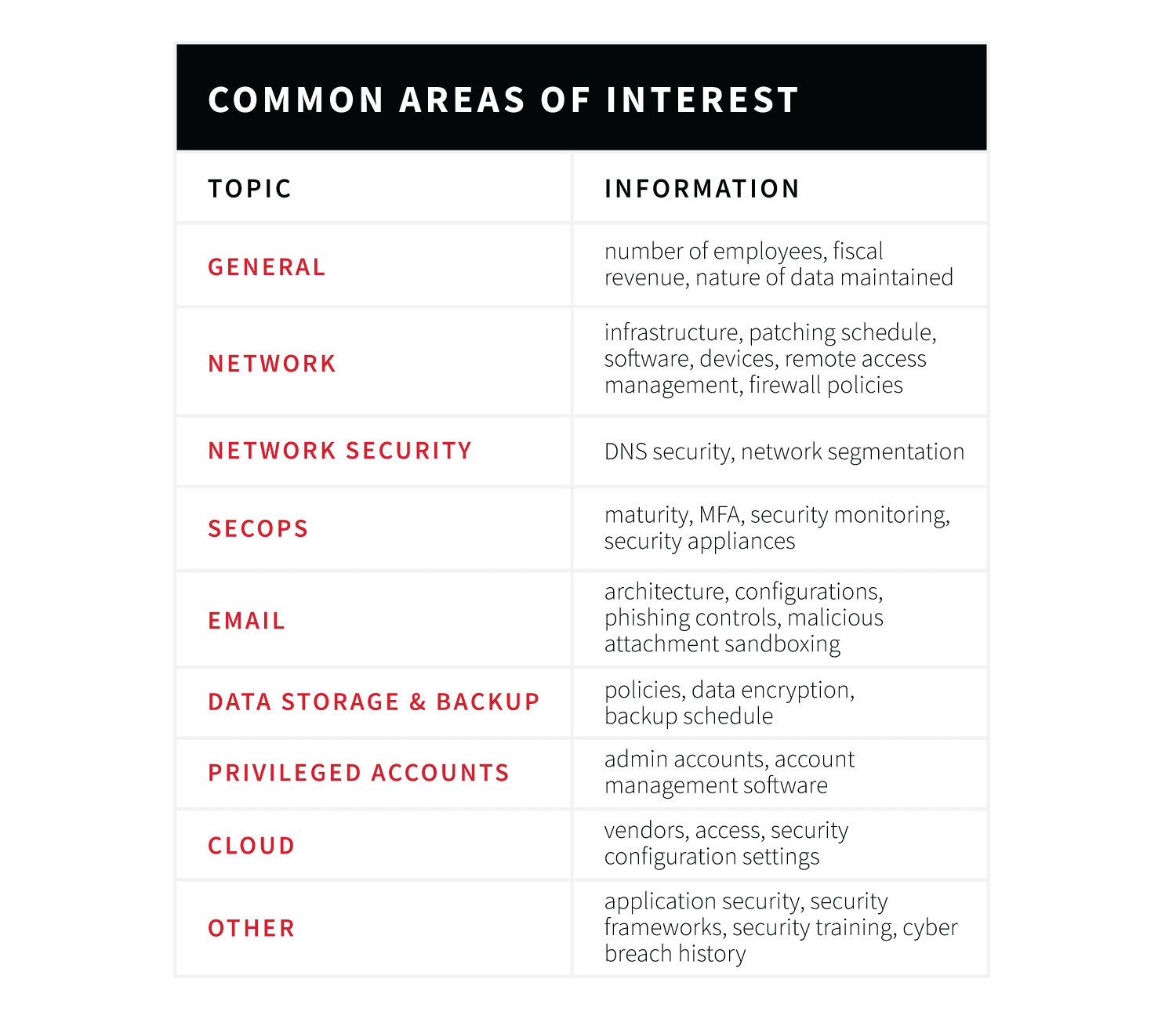
To apply for cyber insurance, you must submit a formal application. This will usually be forwarded to you by either the insurance agency or the insurance broker you’re considering. You can expect an application to be several pages of detailed questions designed to understand the maturity of your IT environment and what unique security challenges you may be facing.
Once the application is received, the insurer will work with an independent security firm to perform due diligence to ensure your organization has the required measures in place. This usually consists of external scans to determine the footprint of your internet-facing systems and potential vulnerabilities or security risks for your organization.
For example, insurers may perform a scan against your O365 or Microsoft Exchange instances to verify that known insecure configurations are disabled (e.g., Autodiscover). Once insurers receive the results of your scans, they’ll place you in a certain risk category. Some insurers will create stipulations in which they’ll only agree to grant you cyber insurance if certain conditions are met, such as updating an appliance to mitigate a vulnerability. Worst case scenario, an insurer may determine your organization to be too risky and opt to not offer coverage at all. The better your scan results, the higher chance you’ll secure a policy.
Pro tips on securing coverage
Landing a policy that effectively protects your company’s future is no small feat. So, we put together a list of tips to consider before you dive in:
Be proactive. Make sure your organization is implementing existing methodologies such as the NIST Cybersecurity Framework and/or the CIS Critical Security Controls. In general, we recommend these as first steps towards procuring cyber insurance and securing your entire network. Not only does this help improve your overall security posture, but it assists with identifying previously unknown gaps. This is a net positive, regardless of your coverage outcome.
Be transparent. Be upfront and honest about the state of your business, network, and security posture. Insurers will call your bluff during the vetting process and, thus, may not offer to write your policy because taking on an untrustworthy customer is a risk in and of itself.
Keep good records. Records of findings from internal IT audits, previous security breaches, and acceptable use policies will signal to potential insurers that your organization takes cybersecurity seriously and has already taken the steps to identify and reduce risk.
Do your research. Work with an experienced insurance broker—like our friends over at Brown & Brown Insurance—to help guide you through the process. Cyber insurance can be daunting, and a good broker can work with you to identify the specific needs of your organization. Conversely, don’t assume a policy meets all your needs; read the fine print and ask questions. Your coverage should reflect the unique requirements of your company and those it serves.
6 Questions with a Cyber Insurance Agent