Information security is grounded in risk management. And, because what gets measured gets managed, we rely on a variety of frameworks and key performance indicators to tell us whether we’re moving in the right direction.
Frameworks like those provided by the National Institute of Standards and Technology (NIST) and the Federal Financial Institutions Examination Council (FFIEC) allow us to measure programs. To measure operations, we often refer to common measures within these frameworks such as time to detect, respond, and recover. Less formal frameworks, such as Sounil Yu’s Cyber Defense Matrix, aim to make it easier to map processes and technology so that we can measure the presence of controls.
But something critically important is missing . . .
For all of our frameworks, mapping exercises, and operational measures, we don’t make it easy to measure what we detect. We “measure detection,” but we think in terms of events per second, alerts per day, false positives, and false negatives. As an industry, we have defined a taxonomy of terms that can be used to describe these things, and our frameworks define the corresponding operational measures. We have never had a framework that describes known attacker tactics and techniques in a way that can be used to describe, measure, and compare the observable attributes of an attack.
Why Defenders Need a Common Framework
Speaking a common language makes it possible to measure and compare what we see. As defenders, this means that we can identify the spectrum of techniques that we expect an attacker to exhibit. Once we’ve done this, we can look across our various processes and controls to identify visibility or analysis gaps. We can look at a specific threat and clearly understand how it was found and what happened. This was possible before, but the words we used were specific to organizations, control families, or even specific products.
This is important to the information security industry as well. We openly lament the aggressive and often indistinguishable marketing that clouds decisions about the products and services security teams should adopt. Speaking a common language makes it easier for teams to compare products and services in an objective manner. And integration of this common language into our platforms makes it easier for consumers to use our products and test our claims.
Developing a Plan of ATT&CK
Adopting a common language would pervade every part of Red Canary operations and our platform. First, we needed to adopt a framework, and MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) framework was an easy choice. MITRE describes it as “a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s lifecycle and the platforms they are known to target.” ATT&CK is open, community-supported, and comprehensive. Critically, it is provided by MITRE as a resource to the community and is not operated or sponsored by any vendor. Anyone is free to leverage it, and everyone is free to contribute as new tactics and techniques are identified.
Next, we had to instrument our detection platform to leverage ATT&CK techniques, mapping our 800+ sets of detection criteria (“Detectors”) to the techniques they aim to identify. This was no small undertaking on the part of our Detection Operations and Applied Research teams, and along the way we identified a number of previously unmapped techniques that we’re working with the ATT&CK team to integrate. Our platform engineering team also needed to update our APIs to make this data available to customers who consume events and confirmed threats into their existing security systems.
Finally, our product team needed to reimagine the way our customers visualize threats we’ve detected. A hallmark of our product has always been a clean and intuitive representation of complex threat data and information. With the introduction of ATT&CK, we needed to give customers a wealth of additional data without taking away any of the data that they rely on for operations.
ATT&CK in Red Canary
Enough about the why and how: let’s see how it looks in action!
The first thing that customers will notice is that we’ve removed our internal detection categories and have replaced these with Observed Tactics. Observed Tactics are a mix of ATT&CK-defined Tactics and others that we use to describe the many observations that we detect, not all of which are malicious.
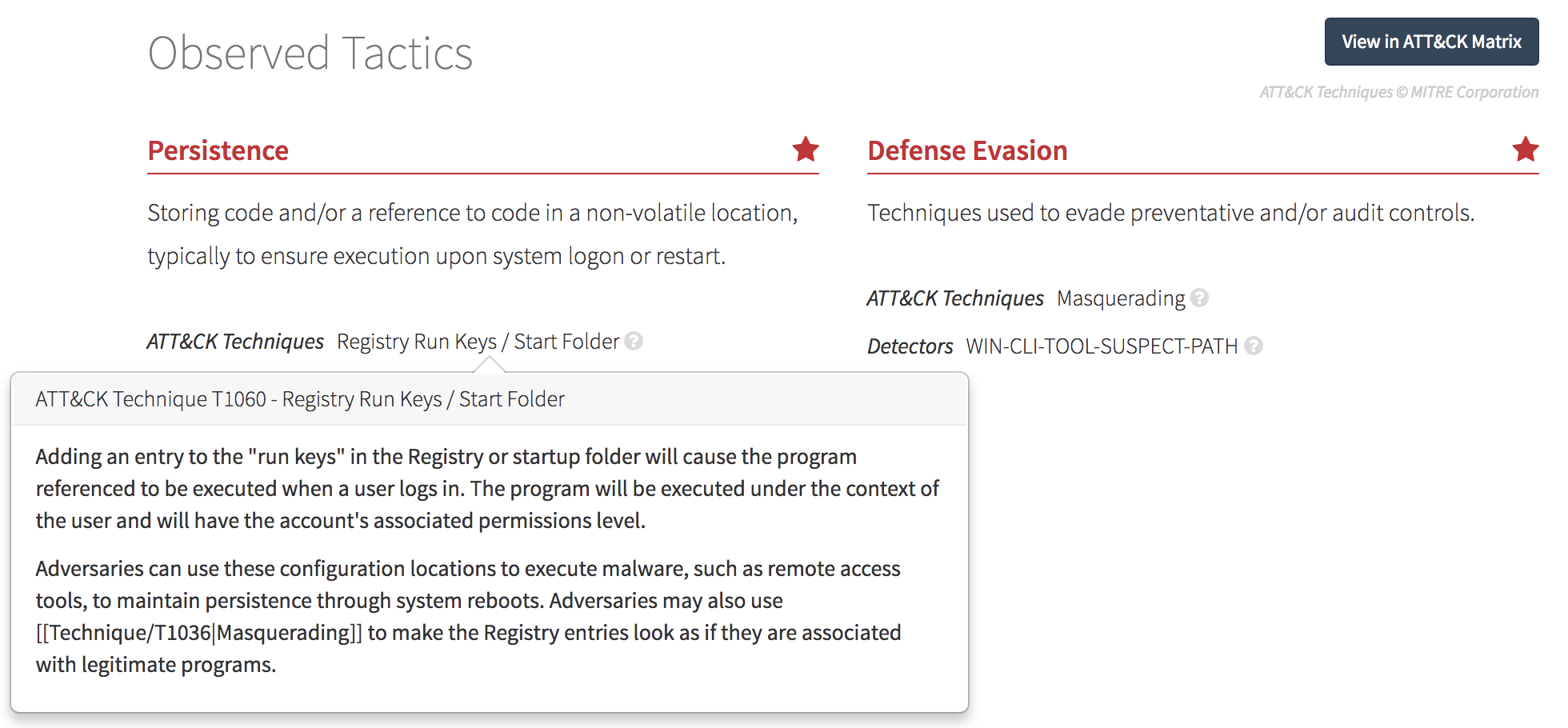
 What’s Next
What’s Next
Every bit as important as what we’ve already done is what we will do. Here’s a peek at what’s coming next:
- Several posts will look behind the scenes at the work our Detection Operations, Applied Research and Product teams have done to implement our vision for a more transparent, measurable and useful representation of threats. Each will share lessons learned your team can use to apply ATT&CK to your detection program.
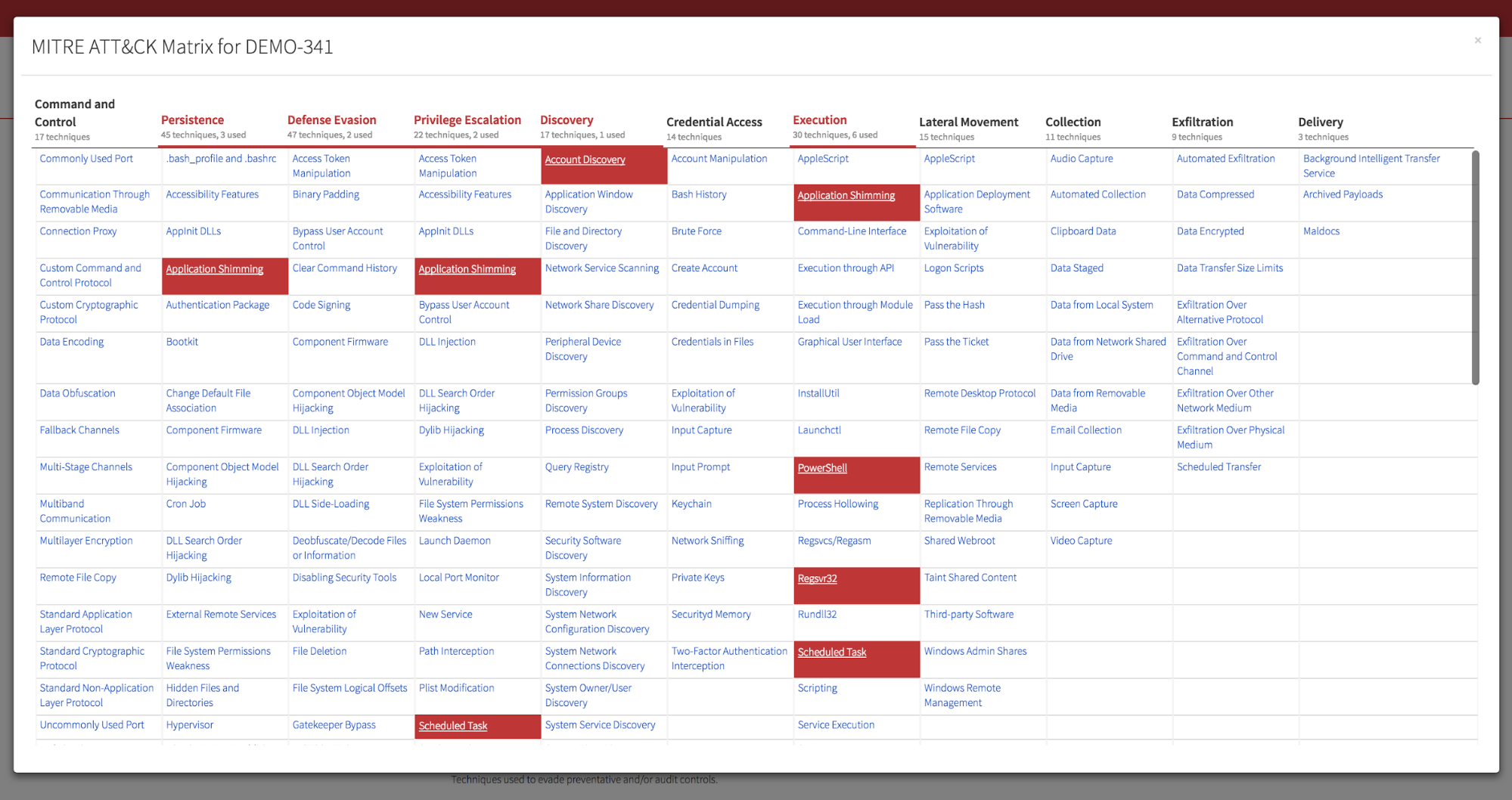
- A Red Canary coverage map, clearly showing what we detect (and what we do not).
- A variety of research products, including heat maps showing how these new tactics and techniques map to the tens of thousands of historical detections that we’ve confirmed over the years. We also plan to share these visualizations and the underlying data with MITRE and the community at-large so teams can prioritize detection and analysis where it matters most.
We hope that you’re as excited about this as we are. Huge thanks to the ATT&CK team and community that has grown around it—we’re one step closer to more transparency and measurement that helps security teams improve and cut through the noise. To make sure you receive the latest updates, subscribe to our blog using the form below.
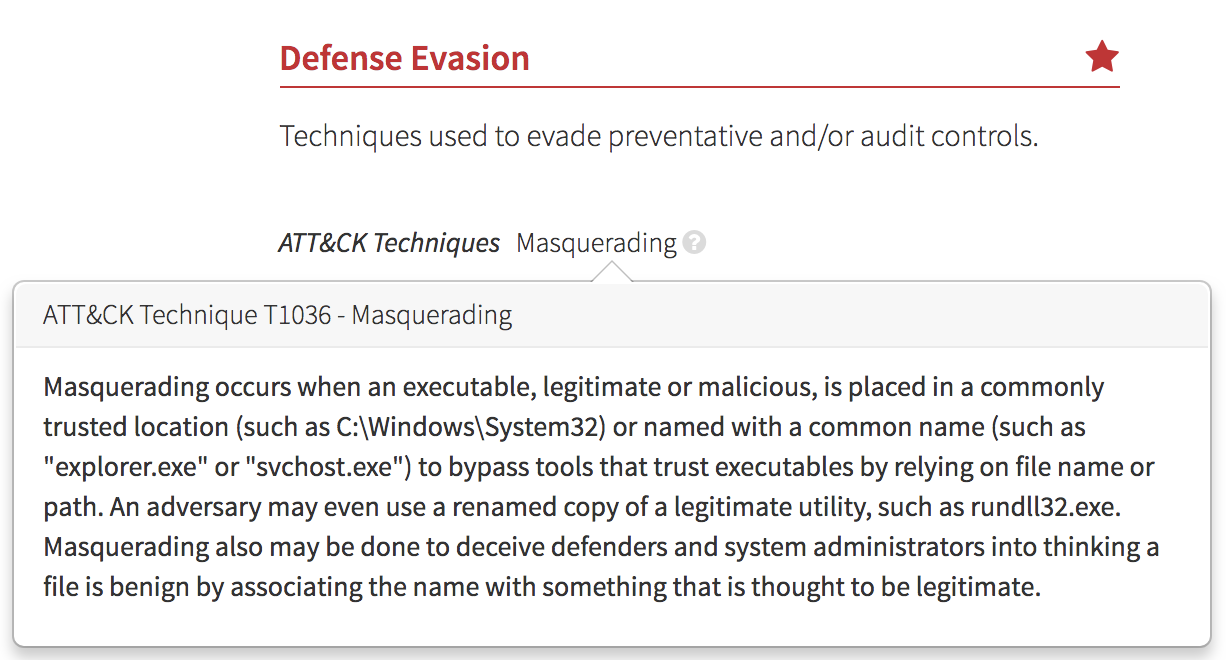 What’s Next
What’s Next