Red Canary is actively detecting CVE-2014-1776, the latest “Internet Explorer zero-day,” on the endpoint by leveraging our global network of managed Bit9+Carbon Black sensors. This post provides some insight into how you can do the same.
We know this exploit targets Internet Explorer (iexplore.exe), requires VGX.dll be loaded by the targeted iexplore.exe process, and is triggered by a malicious Flash file.
Using Carbon Black, we can quickly identify processes meeting these criteria:
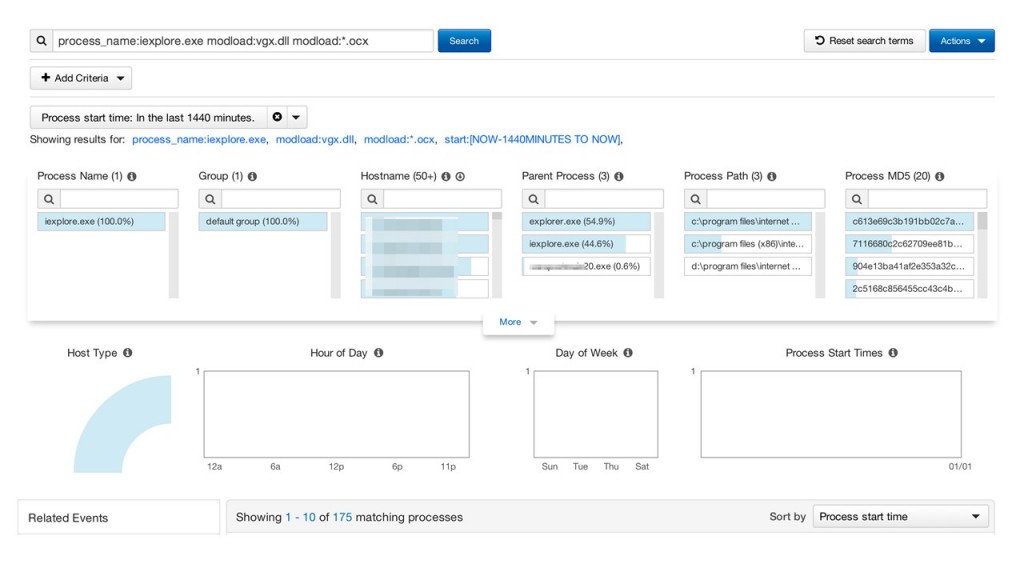
`process_name:iexplore.exe modload:vgx.dll modload:*.ocx`
Note this simply identifies processes where potentially exploitable conditions exist; results are not necessarily indicative of malicious activity. On this particular Carbon Black server, this query yields 175 results over 24 hours (click to enlarge images):
175 results is still a lot to go through, so we need to narrow our search down a bit. We know that upon exploitation, iexplore.exe spawns a child process, which by itself is fairly common behavior. However, the child process name in this case will match *.dll. And while we do observe legitimate processes spawned from DLLs, this is atypical at best. Doubly so when the parent process is a web browser. What we end up with is this:
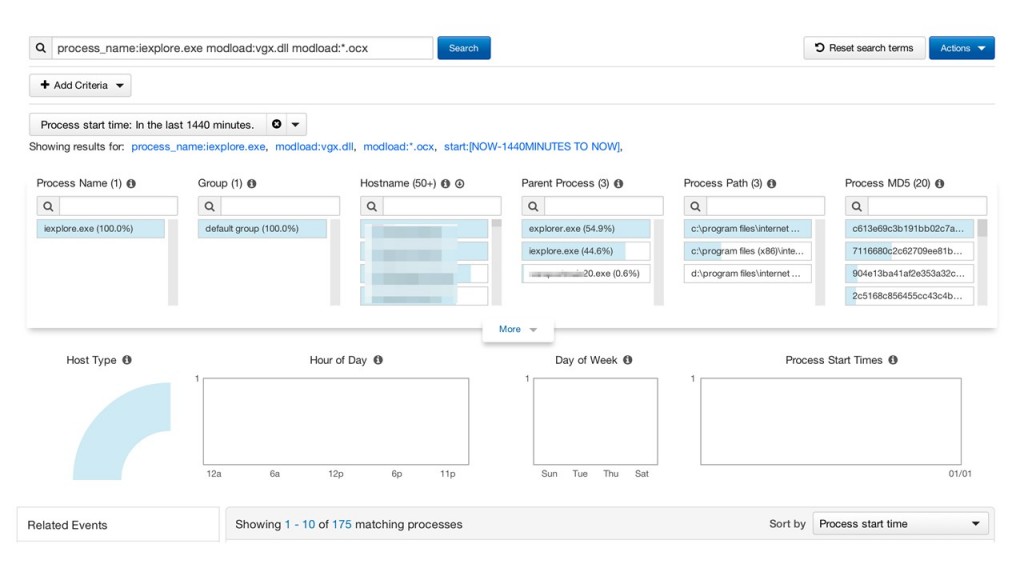
`modload:vgx.dll process_name:iexplore.exe modload:*.ocx childproc_name:*.dll`
Running this query over the same period of time yields a single result, and a confirmed victim:
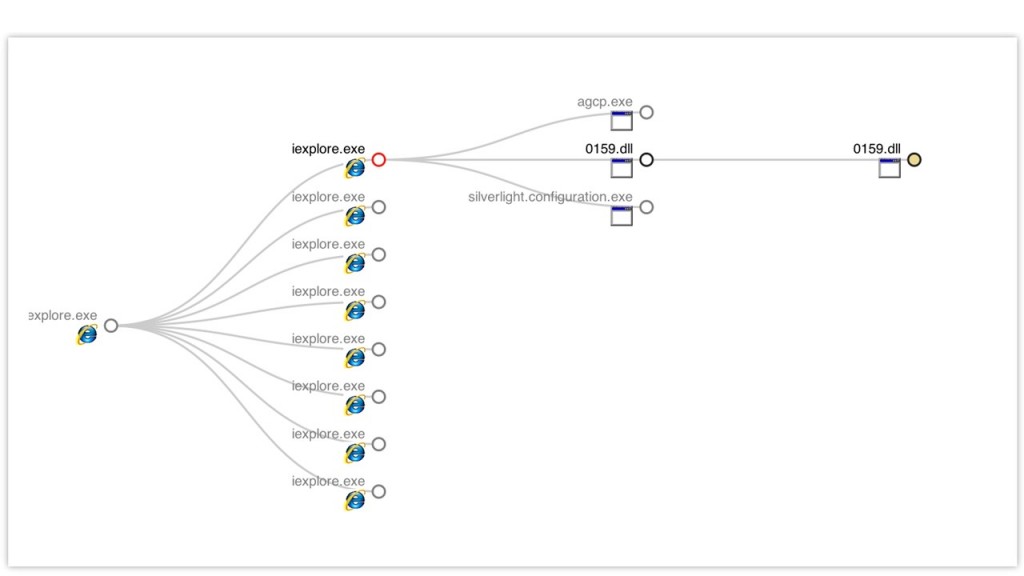
The process tree for our match:
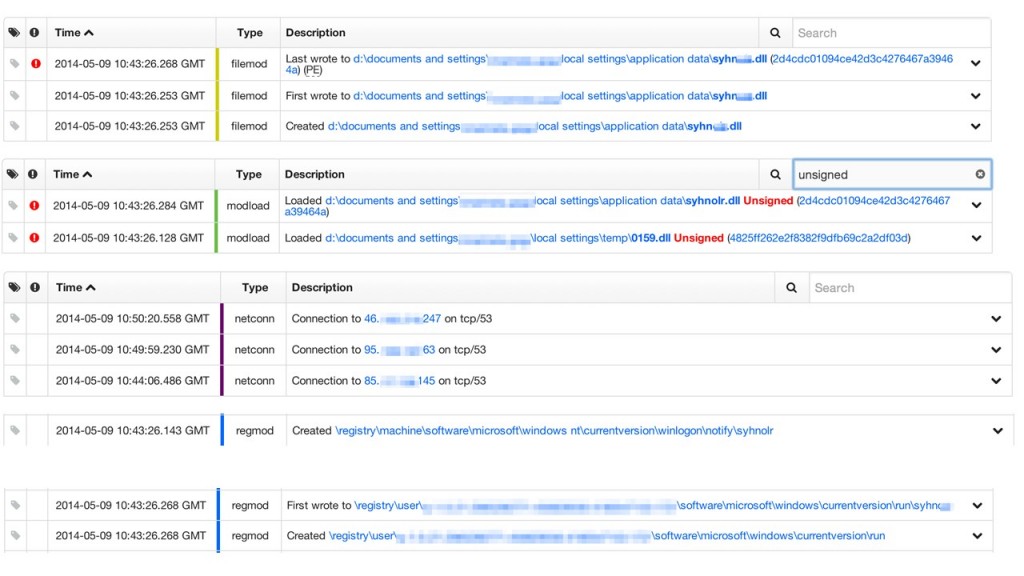
And a sample of some of the activity associated with child process 0159.dll:
Note: This raw Carbon Black query may identify activity that is not associated with CVE-2014-1776. Additionally, while this will detect exploitation of the aforementioned vulnerability, processes matching this query may have been compromised in another manner. In any event, a process matching these criteria should be further investigated.
While we are providing this detection for the benefit of the Carbon Black community, it also highlights a key benefit of our approach: rapid identification of suspicious behaviors without explicit knowledge of the tool(s) an attacker uses. After alerting our client to the occurrence, they or their IR partners can surgically remediate the threat. This also allows them to determine whether a more expansive investigation is warranted.
Red Canary uses internally-developed intelligence, intelligence gleaned from partners, and expert human analysts to sort through the noise, identifying and communicating legitimate threats to our clients in a timely manner. Put another way: Red Canary’s alerts to our customers are 100% actionable and contain zero false positives.