TrickBot
TrickBot is a modular banking trojan that has led to ransomware such as Ryuk and Conti. 2020 signaled a significant decrease in the prevalence and efficacy of TrickBot.
Editors’ note: While the analysis and detection opportunities remain applicable, this page has not been updated since 2021.
TrickBot is a modular banking trojan that targets users’ financial information and acts as a dropper for other malware. Believed to be operated by a single group as a service, different users of the service tend to use different initial infection vectors for TrickBot, often first infecting systems with another malware family such as Emotet or IcedID. In some cases, TrickBot is the initial payload delivered directly from malicious email campaigns.
TrickBot primarily steals sensitive data and credentials and also has multiple additional modules enabling a more fully featured malware service. It has delivered follow-on payloads like Cobalt Strike that eventually lead to Ryuk and Conti ransomware. Other research teams have linked TrickBot code similarities to other malware families such as BazarBackdoor, PowerTrick, and Anchor. The threat group behind the development of these malware toolkits is referred to as WIZARD SPIDER by CrowdStrike.
Infrastructure takedown
This year’s big news around TrickBot occurred in October 2020, when U.S. Cyber Command and Microsoft conducted takedowns of TrickBot infrastructure. Researchers throughout the community debated how effective these takedowns were, but generally agreed there was some disruption. From Red Canary’s perspective, we saw no TrickBot activity in October, followed by fairly low numbers in November and December as compared to the rest of 2020. Around the same time of TrickBot’s decline, we also observed a rise in the prevalence of Bazar. While correlation is not causation, the timing of these patterns suggests WIZARD SPIDER (or other identifiers for the operators of these families) may have switched focus from TrickBot to Bazar.
Decline in prevalence
We observed TrickBot in fewer detections in 2020 as compared to 2019. Multiple TrickBot outbreaks in 2019 contributed largely to some of the top techniques in last year’s report, including Process Injection and Scheduled Task. While TrickBot still made it into our top 10 for 2020, it did not run rampant in environments in the same way we observed the previous year. Many of our TrickBot detections were only on the initial malicious executable being written, and we did not observe follow-on execution. Others were leftover TrickBot persistence via scheduled tasks that had not been cleaned up. Overall, this tells us that throughout 2020, TrickBot had less success in follow-on exploitation than it did in 2019. This suggests, but does not confirm, that TrickBot may have already been decreasing in prevalence and effectiveness throughout 2020, and the takedown operations may have just added on to that decline.
Detection opportunity 1
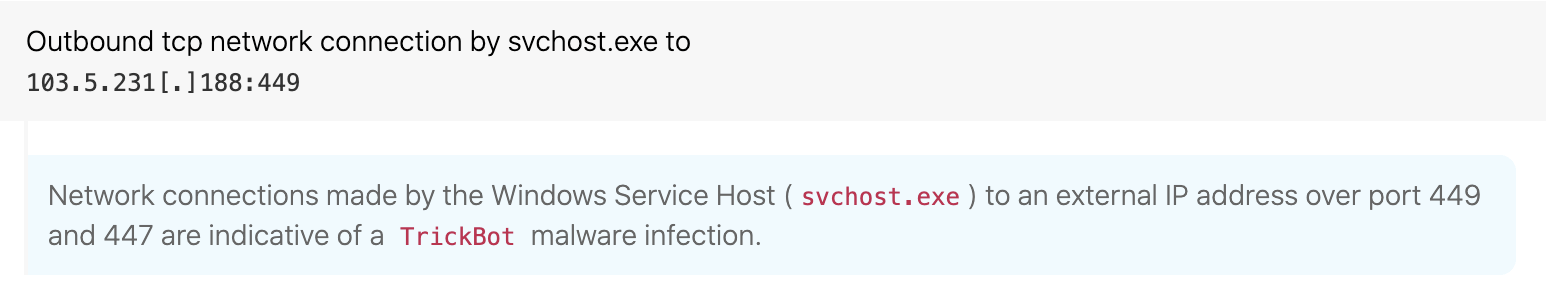
Unusual port connections from svchost.exe
ATT&CK technique(s): T1571 Non-Standard Port
ATT&CK tactic(s): Command and Control
Details: We as well as others in the community noticed that, soon after TrickBot is installed, it makes outbound network connections over HTTPS using TCP ports 443, 447, and 449. Furthermore, these connections came from svchost.exe. Based on this information and a “know normal, find evil” mindset, we determined it was unusual in most environments for svchost to make external connections over ports 447 and 449 and decided to create a detection analytic. This same analytic approach would work for other threats as well: if you notice a threat using non-standard ports, that can be a good opportunity for detection.
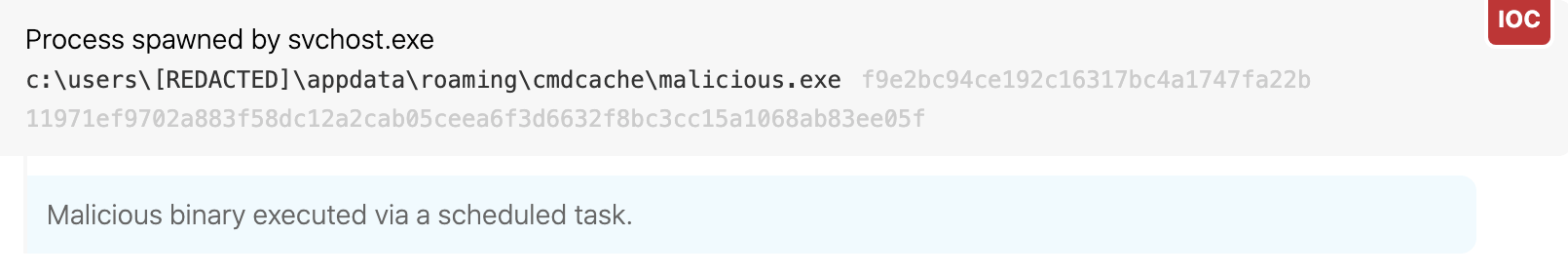
Detection opportunity 2
Scheduled task execution from %appdata%
ATT&CK technique(s): T1053.005 Scheduled Task/Job: Scheduled Task
ATT&CK tactic(s): Persistence
Details: Detecting malicious persistence at scale can be difficult in environments with a lot of different applications setting up legitimate persistence and executing from scheduled tasks. Though detecting the execution of every scheduled task can be too noisy in some environments, we’ve found that narrowing down scheduled task execution to certain folders commonly used by adversaries can help identify evil. In the case of TrickBot, we observed it regularly creating scheduled tasks that contain the folder of appdata\roaming. A useful analytic we created to detect TrickBot and other threats is looking for a parent process of taskeng.exe or svchost.exe executing an .exe located in appdata\roaming. This is one that will take a little tuning based on the environment, but once tuned, should be helpful for finding evil.
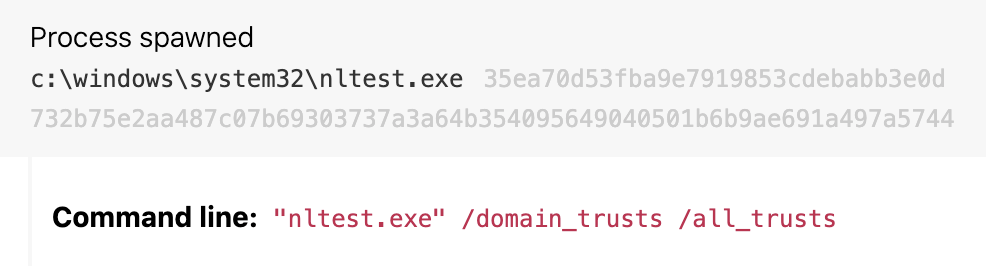
Detection opportunity 3
Enumerating domain trusts activity with nltest.exe
ATT&CK technique(s): T1482 Domain Trust Discovery
ATT&CK tactic(s): Discovery
Details: We observed operators of TrickBot using nltest.exe to make domain trust determinations. While you probably can’t disable nltest.exe, looking for instances of it executing with a command line that includes /dclist:<domain>, /domain_trusts or /all_trusts has proven to be a high-fidelity analytic to catch follow-on activity to both TrickBot as well as Bazar (which didn’t make it into our top 10, due in part to its emergence partway through the year). The use of nltest means discovery activity is occurring beyond initial access and that Cobalt Strike and ransomware such as Ryuk aren’t far behind.