Backdoors & Breaches is back…this time, in red. The popular incident response card game is not only excellent for helping professional teams maintain a good security posture, it also makes for a great party game among security practitioners of all experience levels.
The new Red Canary expansion deck is an amalgamation of experiences from real-world incidents, combining common incidents with some of the more unusual and thought-provoking. Of course, we couldn’t help but add in some fun hypotheticals…
What is Backdoors & Breaches?
Backdoors & Breaches, lovingly envisioned by the folks at Black Hills Information Security, is a tool meant to train and hone the skills of incident responders. Inspired by Dungeons & Dragons and other role-playing games, the format of a card deck offers a laid-back experience that is way more fun and conversational than a traditional training.
Who should play?
Security professionals of all experience levels will get something out of playing Backdoors & Breaches. In real-world incidents, having well-defined procedures and an understanding of common threats makes incident response significantly faster and more effective. This game emulates actual incident response closely and encourages players to learn new tools and processes to improve future incidents.
Managers and other team leaders should take note of the game’s simplicity and speed. It can be played regularly to keep incident responders on their toes, integrated into processes, and used for training new incident responders.
What’s new in the Red Canary expansion deck?
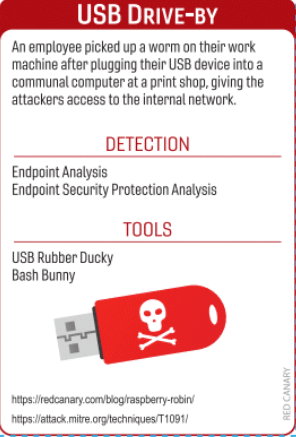
In designing our expansion deck, we used our Threat Detection Report and integrated our Atomic Red Team open source testing library to envision the most useful and interesting scenarios and techniques. One of our favorite cards is based off of our research into the Raspberry Robin activity cluster, which has been known to be spread by USB drives.
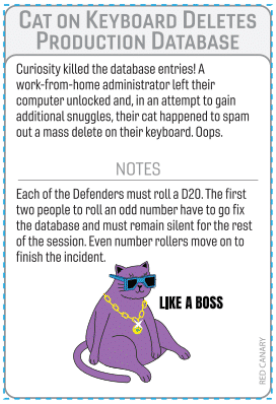
There are also several Inject cards based off of unusual incidents that our team has seen, including one based off of a real incident in which a plant pot was the hiding place for a rogue access point during a popular conference.
How do you play Backdoors & Breaches?
You can find a full list of instructions here, and we’ll lay out the broad strokes below.
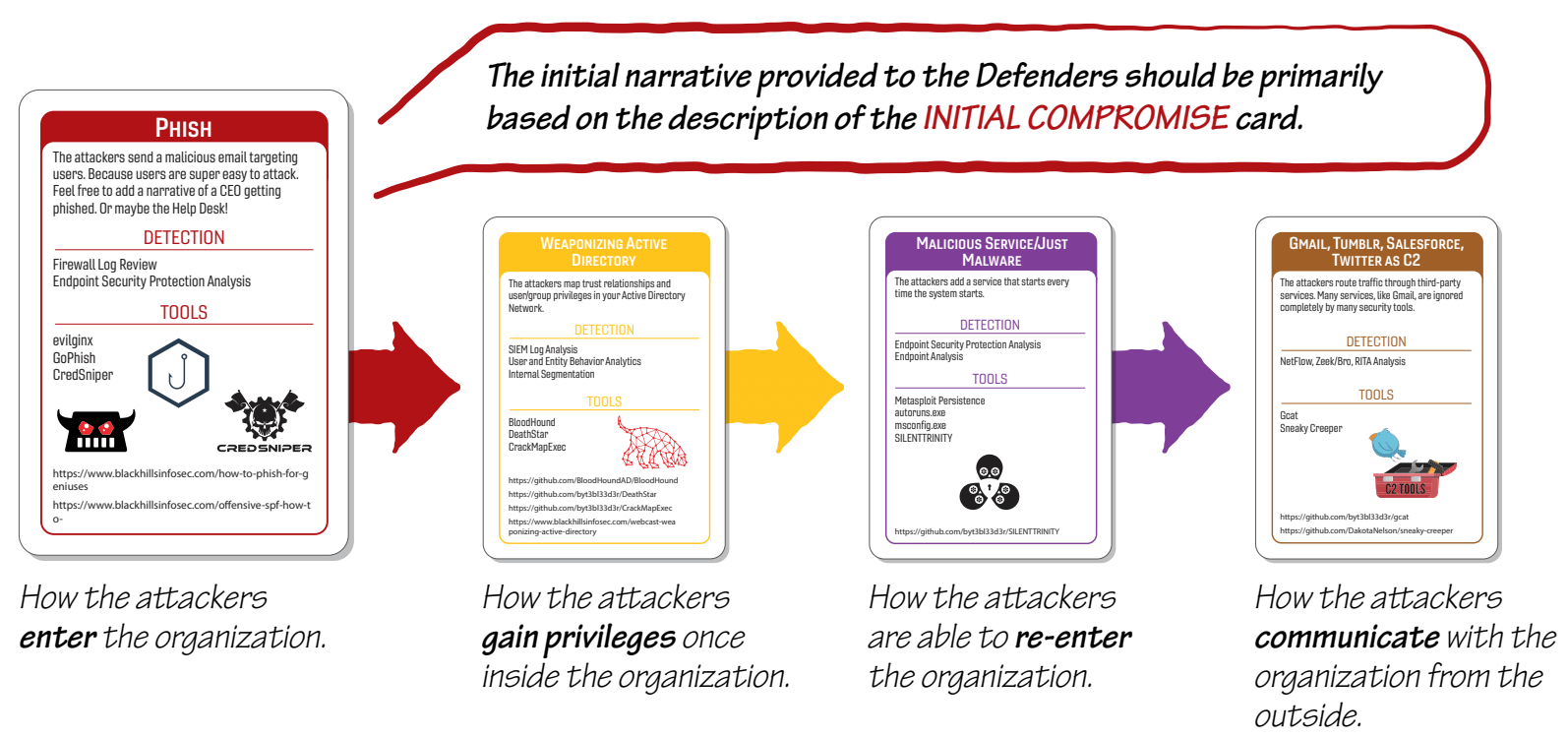
The game has players taking the part of Defenders, with a single Incident Master guiding the game. Cards follow the MITRE ATT&CK framework and guide the incident responder in crafting unique incidents for the defenders to respond to—Incident Response, Pivot and Escalate, Persistence, and C2 and Exfil cards are drawn to outline the incident and start the game.
Image from the B&B Visual Guide
The Defenders randomly draw Procedure cards, which they can use to react to the incident. A roll of a 20-sided die determines if their procedure was successful. Procedure cards also contain information on real-world tools that players might use in an actual incident.
If a roll was successful, the Incident Master reveals attack cards that have corresponding Detections, mimicking a successful finding of malicious activity. If there were no corresponding cards, the Incident Master explains why, without revealing the card.
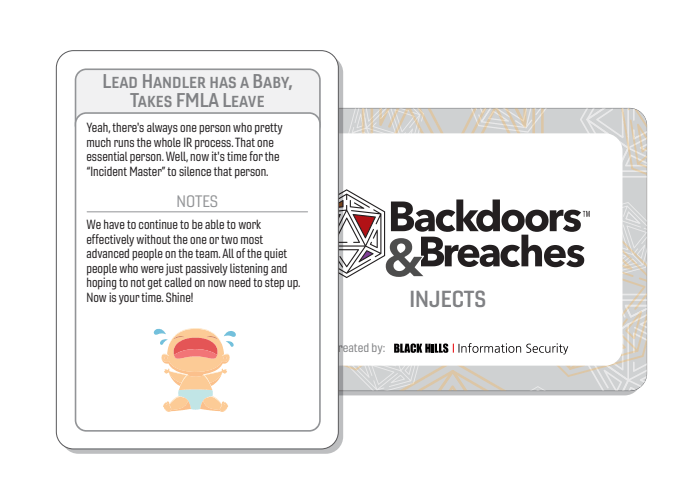
Inject cards add chaos to the game and facilitate conversation. Sometimes they reveal a card, sometimes they do not affect the game, sometimes they end the game. They are pulled by the Incident Master when a 1 or 20 is rolled, or when 3 unsuccessful rolls occur in a row.
Image from the B&B Visual Guide
This process repeats until either the Defenders have revealed all the attack cards (in which case they win), or the Defenders use all 10 turns without revealing all four attack cards (in which case
they lose).
When can I play?
For those who can’t wait, an online version of the game is available now. Otherwise, you’ll be able to buy your own decks at The Spear Phishing Store soon.