The security team at a prominent tech company receives an urgent alert indicating that their internal systems are under attack. Panic momentarily grips the team, but their well-practiced incident response plan kicks into gear. They swiftly isolate the affected systems, identify the origin of the breach, and neutralize the threat; all while communicating transparently with stakeholders. Thanks to their readiness, what could have been a catastrophic data breach turns into a valuable learning experience.
Exemplary scenarios like the one highlighted above seem far too utopian to ever be a reality—especially today, with organizations victimized by attackers every 8 minutes—but what if I told you that effective incident response is possible with a targeted approach and a little tenacity?
The onset of cybercrime-as-a-service, cloud adoption, and the never-ending hurdles with cyber insurance coverage have made it crystal clear that the way we handle incidents must continually evolve. This underscores the need for increased vigilance, preparedness, and coordinated response efforts for all industries and security shops worldwide.
Here at Red Canary, we are relentless in our pursuit of improving security, not just for our customers, but for the entire community. That’s why we’ve updated our popular Incident Response & Readiness Guide to account for new factors driving security personnel and organizations to better strategize and prepare for defending their digital fortresses.
In the guide you’ll learn how to:
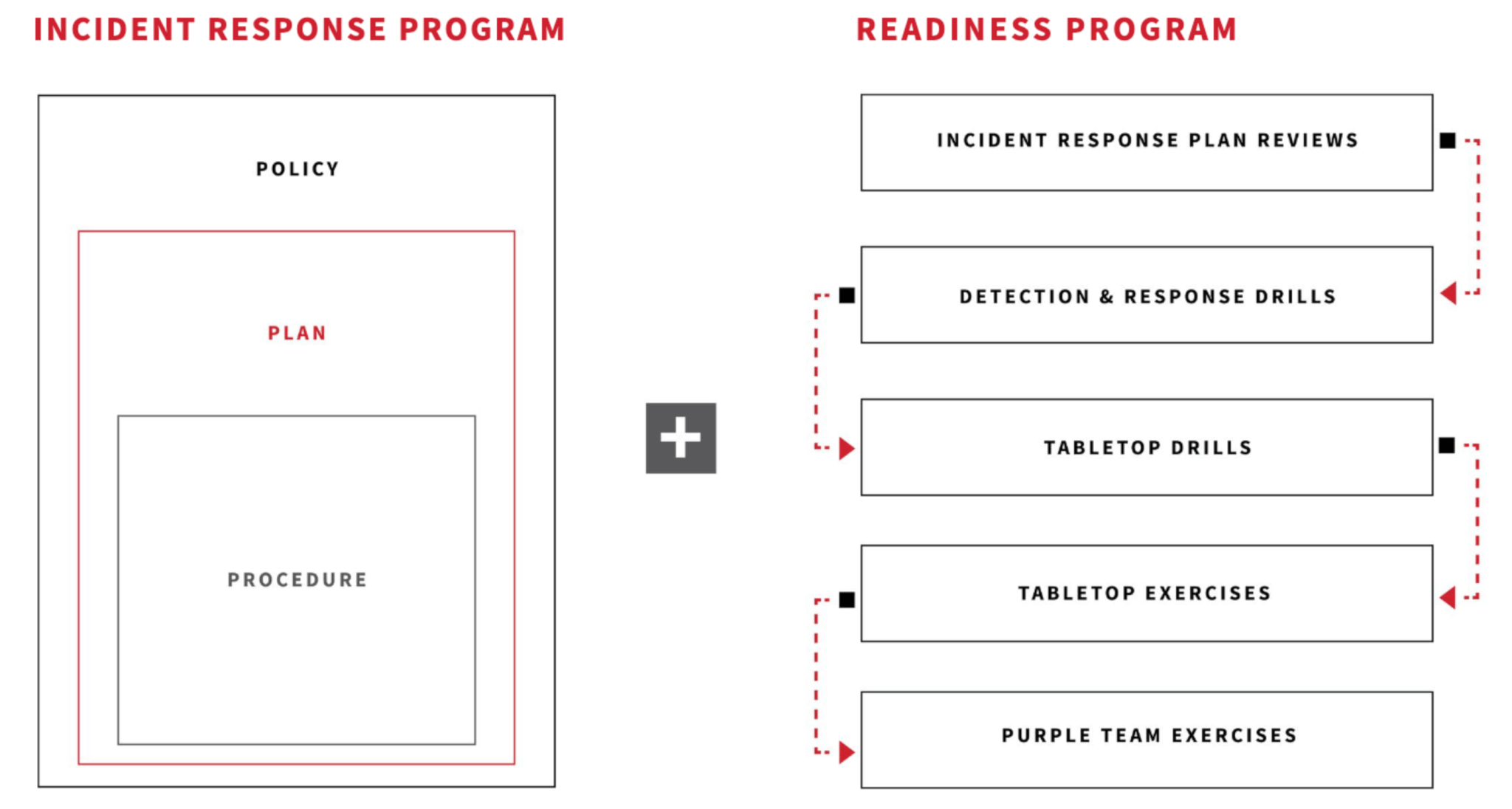
- Build an effective incident response program
- Implement an ongoing training program for your organization
- Identify key stakeholders, roles, and responsibilities
- Recognize and monitor threats in the cloud
- Prepare your organization for a cyber attack
We hope this guide proves useful in helping your organization develop an improved incident response program that aids in planning for and practicing the core skills required when responding to an incident.