We just published the 2022 Threat Detection Report, which encompasses the latest trends, threats, and techniques prevalent over the course of 2021. The Threat Detection Report exists to help you understand and detect threats, and is based on in-depth analysis of more than 30,000 confirmed threats detected across our customers’ environments. This research arms security leaders and their teams with actionable insight into the threats we observed, techniques most commonly leveraged by adversaries, and trends that help you understand how these are changing and why. You can access and download the full report here.
New this year, we included a “Trends” section with insights into how threats are evolving, and how we as defenders must evolve in kind. From the continued influx of ransomware to high-impact vulnerabilities and supply chain attacks, this section synthesizes intelligence with insights from the front lines of threat detection and response. We also released vol. 2 of Threat Sounds, the Threat Detection Report playlist!
Key takeaways
- Ransomware continued to dominate the 2021 threat landscape, and operators took new approaches, like relying on affiliates to gain initial access into an environment.
- Supply chain compromises were a major theme in 2021, starting with SolarWinds, peppered with Kaseya and NPM package compromises mid-year, and ending with Log4j.
- 2021 was a busy year for vulnerabilities affecting popular enterprise platforms, and exploitation of these vulnerabilities has led to web shells and ransomware.
- Confirmed testing comprised almost one quarter of all of our detections in 2021, with many of the testing detections observed coming from open source tools.
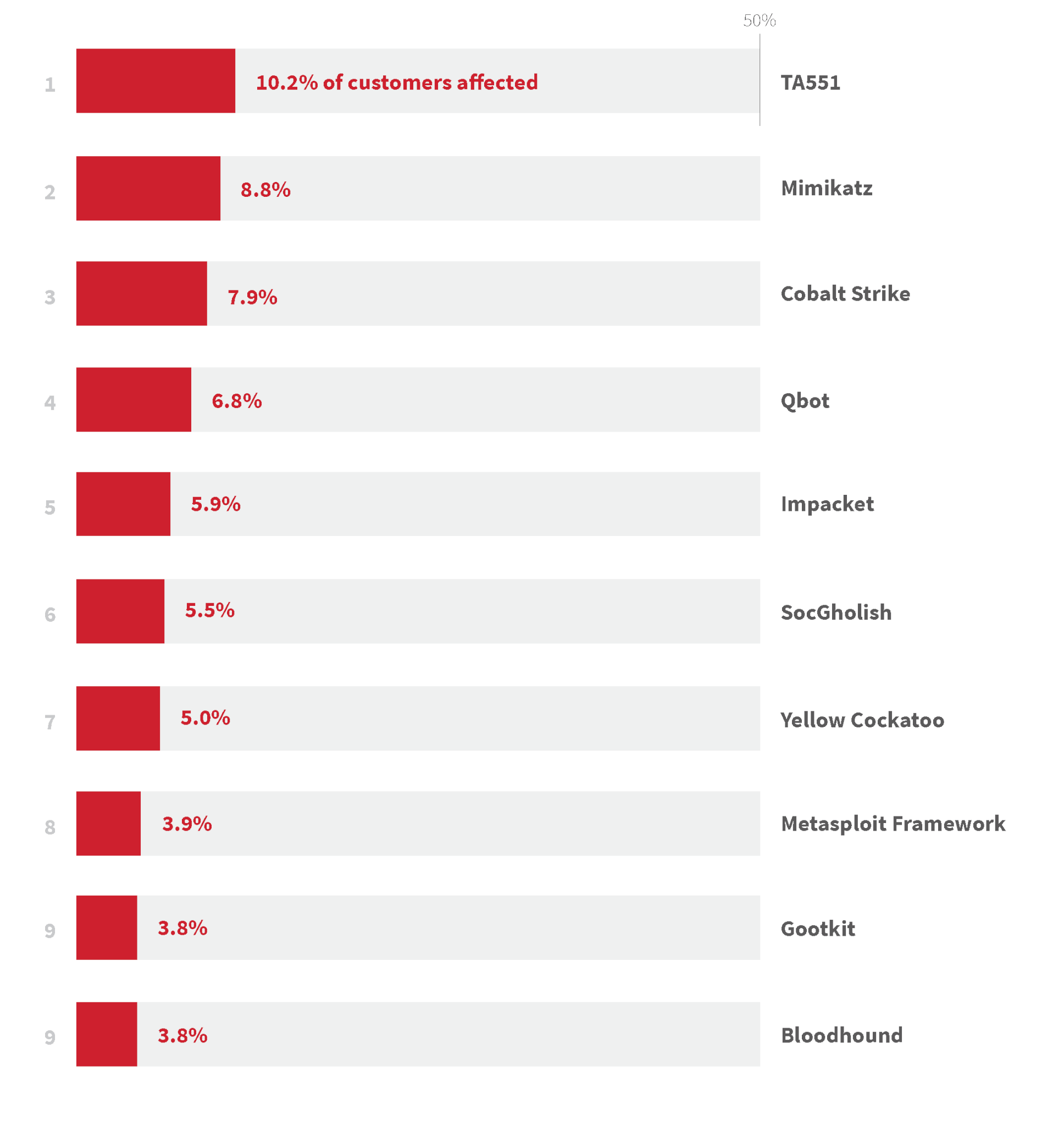
- TA551 was the top threat in 2021, impacting 10.2 percent of customers.
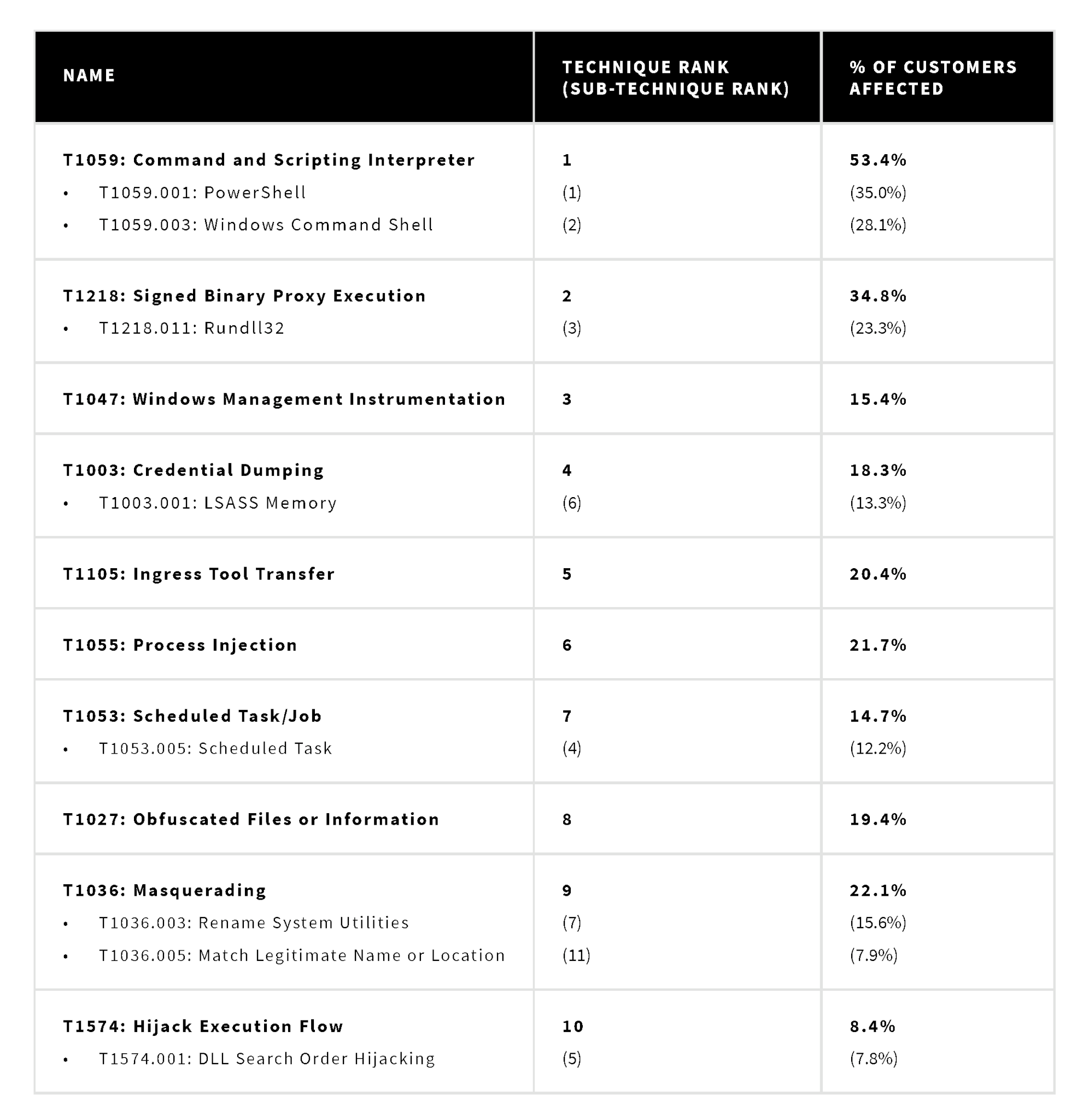
- ATT&CK® technique prevalence was consistent with previous years as we continued detecting adversaries abusing native system utilities for execution, privilege escalation, persistence, and defense evasion.
Trends
Red Canary performed an analysis of emerging and significant trends that we’ve encountered in confirmed threat detections, intelligence reporting, and elsewhere over the past year. We’ve compiled the most prevalent trends of 2021 to show major themes that may continue into 2022.
Throughout 2021, ransomware remained one of the top threats to every organization, with adversaries turning to affiliates to give them initial access into an environment. Vulnerabilities that impacted popular enterprise platforms led to web shells and ransomware, and supply chain compromises continued to cause major disturbances for businesses.
Other top trends include crypters-as-a-service becoming more prevalent in 2021, malicious macOS installers continuing to be targeted, and coinminers dominating the Linux threat landscape. Adversaries continued to abuse legitimate remote monitoring and management (RMM) software, and attacks leveraging remote procedure calls (RPC) increased.
Threats
The following chart illustrates the specific threats we detected most frequently across our customers in 2021. We ranked these threats by the percentage of customer organizations affected to prevent a single, major malware outbreak from skewing the metrics. Red Canary defines “threats” broadly as malware, tools, threat groups, or activity clusters. Eight of our top 10 threats are malware families or tools, while one (TA551) is a threat group named by another team (Proofpoint), and another an activity cluster created by Red Canary (Yellow Cockatoo). This is expected because distinct malware families and tools are often more straightforward to identify, while associating activity to threat groups or activity clusters requires longer-term analysis that may extend beyond the year.
Techniques
Red Canary identified the most prevalent ATT&CK techniques observed in confirmed threats across the Red Canary customer base in 2021. We have a library of roughly 3,000 detection analytics that we use to surface potentially malicious and suspicious activity across our customers’ environments. These are mapped to corresponding MITRE ATT&CK techniques whenever possible, allowing us to associate the behaviors that comprise a confirmed threat detection with the industry standard for classifying adversary activity. Unlike threats, we count and rank techniques by raw detection volume. The following chart shows the most prevalent techniques we detected this year.
Recommendations for defenders
Defenders have options when it comes to protecting their organizations, and there are many things that can be done immediately to start reaping the benefits of the Threat Detection Report.
- Use this report to:
- make architectural decisions
- drive testing and validation of your defenses
- drive IR preparedness and scope tabletop exercises
Start perusing the most prevalent techniques, trends, and threats to see what we’ve observed in our customers’ environments. Talk with your team about how the ideas, recommendations, and priorities map to your security controls and your overall strategy.
If you have any questions or would like to have a discussion about the content in the Threat Detection Report, please contact us at research@redcanary.com and we will put you in touch with one of our experts.