Today we’re excited to launch our fifth annual Threat Detection Report, based on in-depth analysis of threats detected across our 800+ customers’ endpoints, networks, cloud workloads, identities, and SaaS applications over the past year. This time around, we’ve included even more actionable insights to help security teams navigate the ever-widening threat landscape.
A few of the report’s authors sat down to chat about why we publish the report, how practitioners can use it, and what they’re most excited to share with the public:
Video produced by Laura Brosnan and Dalton Vanhooser
Once again, we present you with the top 10 threats, the top 10 MITRE ATT&CK techniques, and the key trends we observed over the past year. As the technology that we rely on to conduct business continues to evolve, so do the threats that we face.
Here’s what’s new in this year’s report:
- Cloud and identity attacks are becoming more prevalent across our customers’ environments and appear for the first time in this report
- Our unique visibility into email attacks, still the leading initial access vector used by adversaries, has put us in a position to detect even more attacks at earlier stages
- Mitigation guidance to limit adversaries’ effectiveness
- Adversary simulation and other authorized testing are excluded from our dataset, leading to a more accurate representation of the threat landscape
- Raspberry Robin, a USB-based threat first discovered by Red Canary, continues to evolve, and we provide updated research
Trends
Drawing from several narratives throughout 2022, we provide insight into key trends and developing tradecraft.
Threats
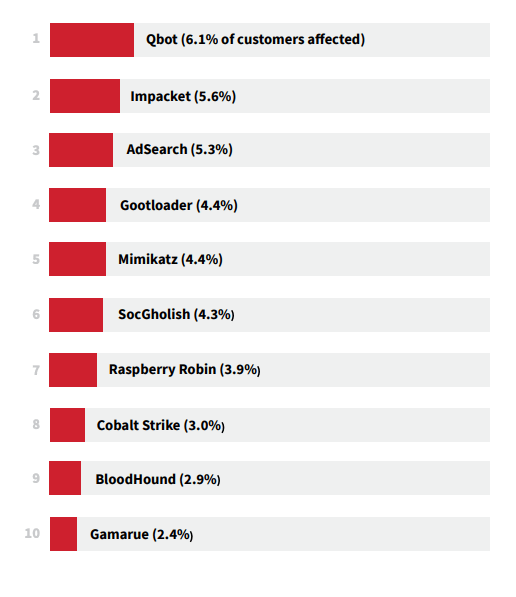
Qbot leads the pack this year, and Raspberry Robin, AdSearch, and Gootloader make their debuts in the top 10 most prevalent threats. Certain offensive security and malicious tools have become increasingly productized, giving adversaries an advantage and making some security controls less effective.
We also highlighted three additional threats to keep an eye out for:
Techniques
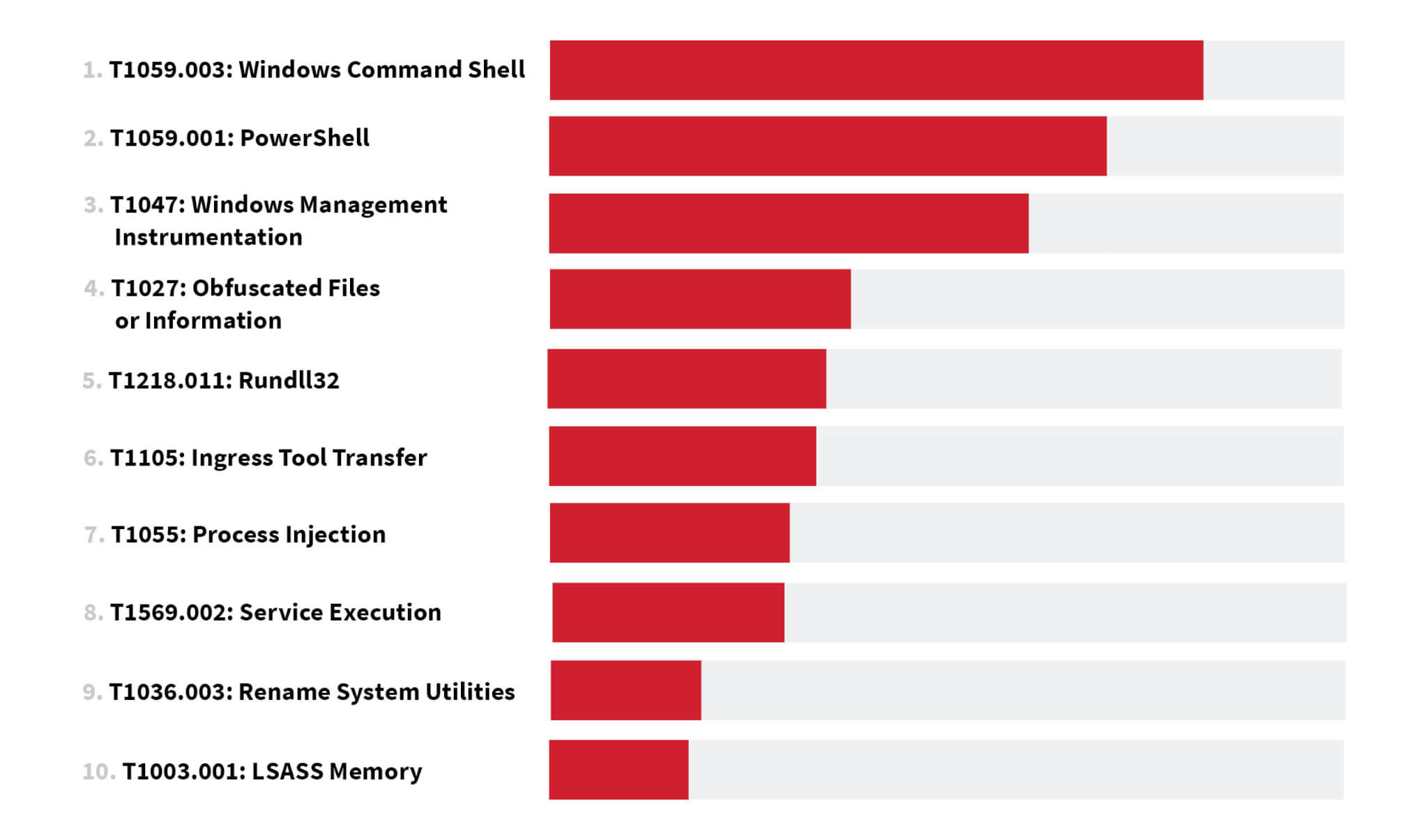
Though they switched places in rank, Windows Command Shell and PowerShell once again topped our list of the most prevalent MITRE ATT&CK techniques, as they have for the past three years. We also observed a noticeable increase in cloud and identity-specific techniques.
The following additional techniques may not be as prevalent as the top 10, but still warrant your attention:
• T1553.001: Gatekeeper Bypass
• T1553.005: Mark-of-the-Web Bypass
• T1548.001: Setuid and Setgid
• T1021.002: SMB/Windows Admin Shares
• T1621: Multi-Factor Authentication Request Generation
Get started
Dive deeper into the top 10 lists online and download the Executive Summary for high-level takeaways and action items. And don’t forget to press play on our accompanying playlist, Threat sounds vol. 3!
As our Director of Intelligence Katie Nickels says in the video above, “the first thing that readers should do after reading the report is take action.” On each trend, threat, and technique page you’ll find mitigation advice, detection opportunities, and Atomic Red Team tests that you can run to validate your coverage. Share the report with your colleagues and start a conversation about which threats and techniques you should prioritize as you refine your threat model. We’re here for you if you need help.