Each month, the Intel team provides Red Canary customers with an analysis of trending, emerging, or otherwise important threats that we’ve encountered in confirmed threat detections, intelligence reporting, and elsewhere over the preceding month. We call this report our “Intelligence Insights” and share a public version of it with the broader infosec community.
Highlights
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Last month we started calculating our trending threat data in a new way. We now filter threats related to customer-confirmed testing from our top 10 rankings. This change helps boost our signal-to-noise ratio, increasing the visibility of potential true positive malicious activity and decreasing the influence of known-good testing on the rankings. We’ll still comment on threats that would have made the top 10 had we included testing activity, but the monthly and year-to-date rankings no longer include this information.
Here’s how the numbers shook out for September 2022:
| September rank | Threat name | Threat description |
|---|---|---|
| September rank: ⬆ 1 | Threat name: | Threat description : Banking trojan focused on stealing user data and banking credentials; delivered through phishing, existing Emotet infections, and malicious Windows Installer (MSI) packages |
| September rank: ➡ 2 | Threat name: | Threat description : Activity cluster using a worm spread by external drives that leverages Windows Installer to download a malicious DLL |
| September rank: ➡ 3 | Threat name: | Threat description : Dropper/downloader, often distributed through search engine redirects |
| September rank: ⬆ 4* | Threat name: | Threat description : Collection of Python classes to construct/manipulate network protocols |
| September rank: ⬆ 4* | Threat name: Redline | Threat description : Information stealer sold on underground forums and used by a variety of adversaries |
| September rank: ⬆ 4* | Threat name: Web Companion | Threat description : Potentially unwanted program which, if given permission, will access and change users’ browser settings |
| September rank: ⬆ 7 | Threat name: Zloader | Threat description : Banking trojan with many variants that originally focused on credential theft but in more recent years has delivered pre-ransomware payloads for a number of different ransomware families |
| September rank: ⬆ 8* | Threat name: PureCrypter | Threat description : Multi-stage encrypted malware suite that uses process injection to deliver and execute additional malicious payloads of the adversary’s choosing, often information stealers or remote access tools |
| September rank: ⬇8* | Threat name: | Threat description : Malware family associated with ad fraud activity through the distribution of adware applications |
| September rank: ⬇10* | Threat name: | Threat description : Open source tool used to identify attack paths and relationships in Active Directory |
| September rank: ➡ 10* | Threat name: | Threat description : Malware family used as part of a botnet. Some variants are worms and frequently spread via infected USB drives |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Observations on trending threats
Many threats from August 2022 stayed in the top 10 this September, however we did see a few changes. September saw a major resurgence in Qbot activity, putting Qbot in the number 1 spot and back into the top 10 for the first time since July 2022. Newcomers to the trending threat list include Web Companion, Zloader, and PureCrypter. AdSearch, previously at number 1, fell out of the top 10 altogether. SocGholish activity decreased as well, falling to 12th after tying for 5th in August.
Mimikatz would have made the list in a tie for 4th place, but was removed from the top 10 due to customer-confirmed testing activity. Mimikatz is an open source tool that dumps credentials using various techniques.
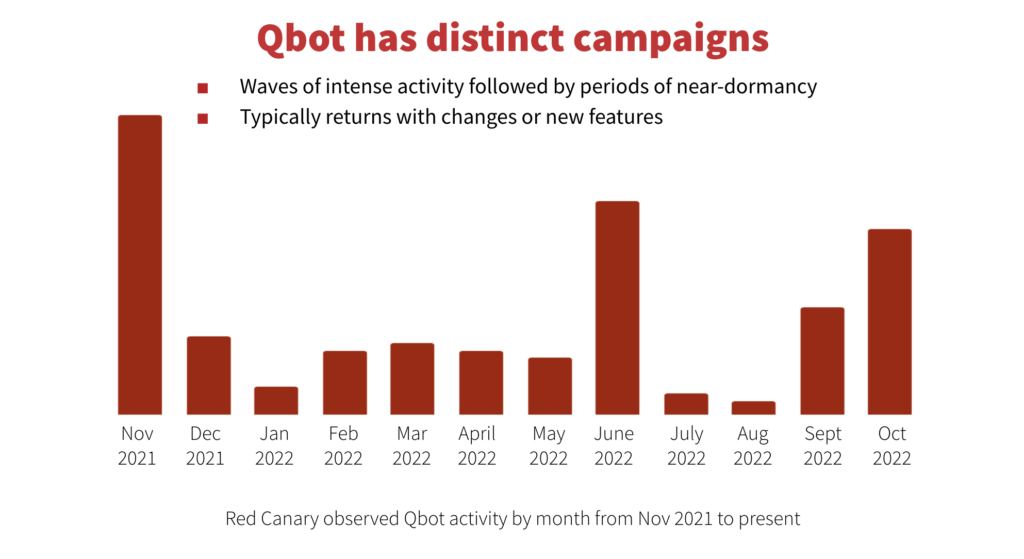
New Qbot campaign
Qbot historically cycles between periods of intense activity followed by quiet, near-dormancy. A sharp increase in Qbot activity paired with changes to the malware—likely in an attempt to make it more challenging for defenders to detect—can signal the start of a new Qbot campaign. In mid-September Red Canary observed such a surge in Qbot detections with clear differences from the activity we saw during earlier campaigns.
Qbot has created randomly named directories and files for years as part of the installation process. Previously, most of these random strings were made up of alphabetical characters, as well as random words, starting in June 2022. The newest wave of Qbot activity appears to use random numbers for similar purposes, for example E:\6342\6189.dat.
The current iteration of Qbot offers several detection opportunities based on unusual regsvr32.exe behavior. We have seen Qbot attempt to install renamed versions of regsvr32.exe. We have also seen regsvr32.exe attempt external network connections with no command-line arguments, which is extremely suspicious behavior. Note: It’s possible for Qbot to very rapidly change which processes it uses on any given day, so keep an eye out for similar unusual behavior from other system processes.
Detection opportunity: Network connections from the command line with no parameters
The following pseudo-detection analytic identifies outbound network connections with no command-line arguments or parameters by regsvr32.exe or rundll32.exe. It is unusual for these processes to attempt network connections with an empty command line, which can indicate malicious command and control (C2) activity.
process == (regsvr32.exe, rundll32.exe)
&&
process_command_line_contains == (“”)
&&
has_netconnection
*Note: double quotes (“”) within the command line means null.
PureCrypter: A malicious loader
One newcomer to the top 10 list this month is PureCrypter. PureCrypter, first documented by Zscaler, is a malicious product sold to adversaries and used to both deploy malware and protect it from analysis. It allows adversaries to select a malicious payload of their choosing. PureCrypter leverages a combination of encryption and process injection techniques to download and execute the chosen payload, enabling the malware to evade endpoint and network security controls.
PureCrypter executes in two stages that rely on each other for execution:
- Stage 1 initiates the download, decryption, and loading of the second stage
- Stage 2 performs additional anti-analysis checks and loads the final chosen malware payload into memory using reflective code loading or injection
Red Canary and other organizations have seen PureCrypter used to deliver a number of information stealers and remote access tools (RAT) such as AsyncRAT, Agent Tesla, Azorult, Lokibot, NanoCore, RedLine, Remcos, and Raccoon. Note that here at Red Canary we track PureCrypter-stage behaviors as separate from the adversary-selected final payload.
Detecting PureCrypter
PureCrypter often uses encoded PowerShell commands:
- Commands can include Start-Sleep delays of varying lengths, for example
powershell.exe -enc UwB0AGEAcgB0AC0AUwBsAGUAZQBwACAALQBTAGUAYwBvAG4AZABzACAAMQAyAA==, which decodes toStart-Sleep -Seconds 12 - Commands can attempt to set Windows Defender exclusions, for example
powershell.exe Set-MpPreference -ExclusionPath
Since PureCrypter can use process injection in its second stage, telemetry may detect activity that suggests process injection behavior.
Detection opportunity: A shortened -EncodedCommand flag in PowerShell commands
The following pseudo-detection analytic identifies powershell.exe commands that include a shortened version of the -EncodedCommand flag. Adversaries can use PowerShell’s ability to recognize shortened flags to obfuscate malicious encoded commands. Note that legitimate processes such as Chocolatey may use shortened -EncodedCommand flags.
process == powershell.exe
&&
Deobfuscated_command_line_includes == (-e , -ec , -en, -enc, -enco, -encod, -encode , -encoded, -encodedc, -encodedco, -encodedcom, -encodedcomm, -encodedcomma, -encodedcomman)
&&
Deobfuscated_command_line_does_not_include == (-encodedcommand)