Each month, the Intel team provides Red Canary customers with an analysis of trending, emerging, or otherwise important threats that we’ve encountered in confirmed threat detections, intelligence reporting, and elsewhere over the preceding month. We call this report our “Intelligence Insights” and share a public version of it with the broader infosec community.
Highlights
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Here’s how the numbers shook out for April 2023:
| Last month's rank | Threat name | Threat description |
|---|---|---|
| Last month's rank: ⬆ 1 | Threat name: | Threat description: Persistent rogue browser surreptitiously installed via files delivered by malvertising links, similar to ChromeLoader |
| Last month's rank: ⬆ 2* | Threat name: Dock2Master | Threat description: macOS ad fraud activity that has led to downloads of other macOS malware, such as Shlayer |
| Last month's rank: ⬆ 2* | Threat name: | Threat description: Collection of Python classes to construct/manipulate network protocols |
| Last month's rank: ⬆ 2* | Threat name: | Threat description: Activity cluster using a worm spread by external drives that leverages Windows Installer to download a malicious DLL |
| Last month's rank: ⬇ 5 | Threat name: | Threat description: Open source tool that dumps credentials using various techniques |
| Last month's rank: ⬆ 6* | Threat name: | Threat description: Malware that modifies victims’ browser settings and redirects user traffic to advertisement websites, similar to AdSearch |
| Last month's rank: ⬆ 6* | Threat name: TA577 | Threat description: Malware delivery affiliate named by Proofpoint that commonly conducts Qbot and IcedID campaigns, using letter pairs like "TR" and "BB" in its malware configuration campaign identifiers |
| Last month's rank: ⬆ 6* | Threat name: CrackMapExec | Threat description: Post-exploitation tool used to audit and assess security in Active Directory environments that leverages Impacket and PowerSploit |
| Last month's rank: ⬆ 8* | Threat name: Ippedo | Threat description: USB worm that can include a function to download and execute arbitrary binaries |
| Last month's rank: ⬆ 8* | Threat name: Lilac Lyrebird | Threat description: Tech support scam activity cluster tracked by Red Canary that uses search engine optimization and malvertising to trick users into giving access to adversaries via LogMeIn |
| Last month's rank: ⬆ 8* | Threat name: | Threat description: Malware family capable of a range of behaviors, including DLL sideloading, capturing the screen, and keylogging |
| Last month's rank: ⬇ 8* | Threat name: | Threat description: Banking trojan focused on stealing user data and banking credentials; delivered through phishing, existing Emotet infections, and malicious Windows Installer (MSI) packages |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Observations on trending threats
This month’s most prevalent threat was AdSearch, its first appearance in the top 10 since September 2022. AdSearch’s recent increase in activity is due to a new campaign in April that included an updated version of the binary that delivers the malware. In some cases, AdSearch activity led directly to ChromeLoader persistence, bringing ChromeLoader to the top 10 in a tie for sixth. Red Canary is still researching the malicious advertising delivery vector behind these two related threats. Raspberry Robin activity increased, landing it in a tie for the number 2 spot for the month and highlighting that USB drives remain a common initial access vector. Red Canary saw reduced threat volume in April, pushing threats like CrackMapExec and Ippedo that often fall just outside the top 10 onto this month’s list.
Metasploit Framework would have made the list in a tie for eighth place, but we removed it from the top 10 due to its frequent use in customer-confirmed testing and approved activity. Metasploit is a penetration testing framework used to probe systematic vulnerabilities on networks and servers and conduct post-exploitation activity on compromised hosts.
Qbot activity wanes in some countries as affiliates target global markets
Qbot activity waxes and wanes in cycles, a pattern we’ve previously noted. The decline in Qbot activity, from number 1 in February 2023 to a tie for number 8 this month, suggests we are currently in a lower-activity phase. The security community has a few well-informed theories surrounding what Qbot distributors like TA570 and TA577 do during these quieter phases. For example, one theory is that adversaries test new delivery methodology in preparation for the next major campaign.
Factors like global visibility can be useful to consider when tracking threat trends and patterns, which is why we look at reports from other teams to supplement our own visibility. Taking note of them can offer interesting insights into adversary activity, and help intelligence analysts like those on our team track threats more accurately.
A recent report from Kaspersky offers evidence that Qbot distributors sometimes target specific global markets, a trend that can make the malware appear more or less active depending on an enterprise’s presence in those targeted markets. Kaspersky reported seeing significant waves of Qbot phishing emails on April 4, April 6, and April 12, 2023, with upwards of 1,000 emails distributed on each of these days.
Over 47 percent of phishing emails during this time frame affected users in either Germany , Argentina, or Italy. Only 3 percent of the emails were sent to users in the United States, making the threat artificially appear nearly inactive if only looking at that one country’s activity.
Lilac Lyrebird uses SEO poisoning and malvertising in their tech support scam
In April 2023, Red Canary began tracking a tech support scam activity cluster we named “Lilac Lyrebird,” which leverages search engine optimization (SEO) and malicious advertising. We have not seen activity from this cluster since mid-April, potentially due to infrastructure takedown. Even though this specific cluster may no longer be active, we assess the techniques it used could be relevant in future campaigns and wanted to share the details.
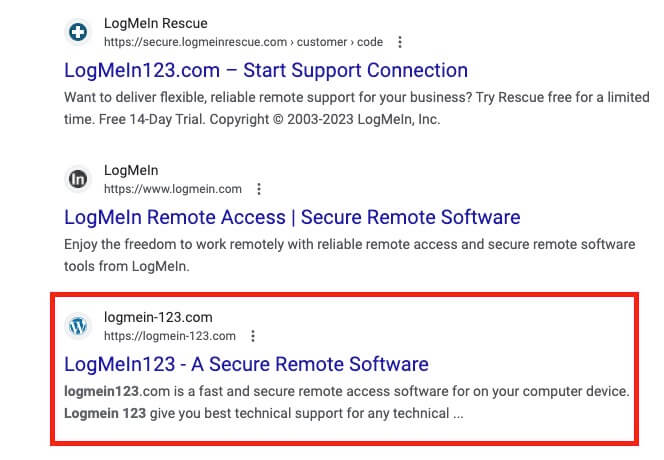
Tech support scams are not a new type of threat. Adversaries historically used malware, social engineering, or a combination of the two to lure victims into downloading remote access software onto their endpoints. Lilac Lyrebird used slightly different tradecraft than previous tech support scams to gain initial access to victim systems. When users searched for “LogMeIn Rescue” or “LogMeIn123,” Lilac Lyrebird used SEO techniques to make their malicious sites as prominent as authentic sites for the legitimate remote access tool LogMeIn. On April 12, 2023, Lilac Lyrebird’s malicious site was the third result returned when searching for “LogMeIn123,” as seen below:
Top three search results for “LogMeIn123” on April 12, 2023, including Lilac Lyrebird’s malicious site
Lilac Lyrebird may also have used ads displayed on search engine pages masquerading as legitimate software download sites, a technique known as malicious advertising, or malvertising. SEO and malvertising were two of the most popular initial access trends in 2022, used by a number of other threats, including Gootloader and IcedID.
After being tricked into navigating to Lilac Lyrebird’s fake LogMeIn websites, victims were redirected to a site that downloaded a file named support-logmeinrescue.exe.zip. After the ZIP was downloaded, observed follow-on behaviors included:
- Executing a process named
Support-LogMeInRescue.EXE.cmd - Opening a browser directing the victim to the legitimate URL
https[:]//secure.logmeinrescue[.]com/customer/code.aspxto facilitate social engineering of a victim to trick them into entering a code in the URL - PowerShell connecting to an external domain such as
support.onli-ne[.]comto download a.batfile - Creating a scheduled task to execute the downloaded
.batfile
Sometimes malicious Lilac Lyrebird downloads caused a message box to appear on a victim’s screen asking them to call a phone number. During the phone call, the adversary likely instructed the victim to visit a legitimate website for LogMeIn and enter a code. Not all Lilac Lyrebird infections appeared to result in a message box with a phone number.
Giving adversaries remote access to endpoints in an environment opens up the possibility of information theft, credential theft, or additional malware installations, making the risk of successful Lilac Lyrebird or similar activity potentially significant. Organizations may find it useful to make users aware of the potential for tech support scams, and reiterate the proper channels through which users should communicate with approved tech support solutions. SEO and malicious advertising can be challenging to mitigate completely. To mitigate malicious ads, organizations should consider deploying ad-blocking software across the enterprise.
If victims are tricked into giving tech support scammers access to their endpoints, detecting suspicious follow-on activity will help you respond rapidly and reduce impact to your organization. For example, Lilac Lyrebird used PowerShell to download .bat files from external domains, presenting the detection opportunity below.
Detection opportunity: PowerShell using iex(New-Object Net.WebClient).DownloadString to download remotely hosted files
The following pseudo-detection analytic looks for instances of PowerShell using iex(New-Object Net.WebClient).DownloadString to download files hosted remotely. Adversaries can leverage this function to download malicious scripts or other code onto victim systems. This function can also have legitimate uses, for example by Chocolatey or Chef for updates, so additional tuning will likely be needed depending on your environment.
process == (powershell)
&&
command_line_includes == (downloadstring)
&&
command_line_does_not_include == (*)
Note: * is a placeholder for command line strings and processes associated with approved use of this function by PowerShell in your environment