Stealers
There is no better way to compromise identities en masse than deploying info-stealing malware.
Adversaries are looking for opportunities to log in rather than hack in, realizing that a good username and password combination can provide access to a company’s local systems and cloud applications, all while blending into the environment. Adversaries use stealer malware to opportunistically gather identity information and other data at scale. Stealers can extract information from web browsers, applications, cryptocurrency wallets, and more. Credentials are the primary commodity that stealers capture, and adversaries can sell them in online marketplaces, share them with other adversaries, or use them in the service of a more complex scheme like ransomware.
In 2024, stealer malware infections increased across both Windows and macOS platforms.
What we saw in 2024
In 2024, stealer malware infections increased across Windows and macOS platforms. Many variants evolved their tradecraft, with some adapting to a growing population of macOS systems while others adapted to technological changes in the browser landscape on Windows systems.
macOS
Red Canary observed Atomic, Poseidon, and Banshee stealers targeting macOS systems at numerous organizations. Of the three, Atomic Stealer was the most prevalent by far, appearing on our monthly top 10 rankings five times.
In each case, we observed adversaries leveraging macOS’s native AppleScript to gather files, prompt users for passwords, and stage files into ZIP archives before extraction. In fact, AppleScript is the common thread that runs between most macOS stealers on the market, as it provides an easy way to gather information quickly and obviates the need to learn programming in Objective-C or Swift. Other developments in the macOS stealer market include Poseidon Stealer’s developer selling its infrastructure to exit the market and Banshee’s source code leaking.
Browsers
In 2024 Google introduced application-bound encryption, a major change for Chromium-based web browsers (e.g., Chrome, Edge, Brave, Opera, etc.). This update added extra requirements for non-browser applications to access cookie content, making it harder for malware to steal browser session cookies that adversaries can abuse to gain access to accounts.
Adversaries adapted to this change quickly, however, with the most popular stealers implementing app-bound encryption bypasses within a few short months.
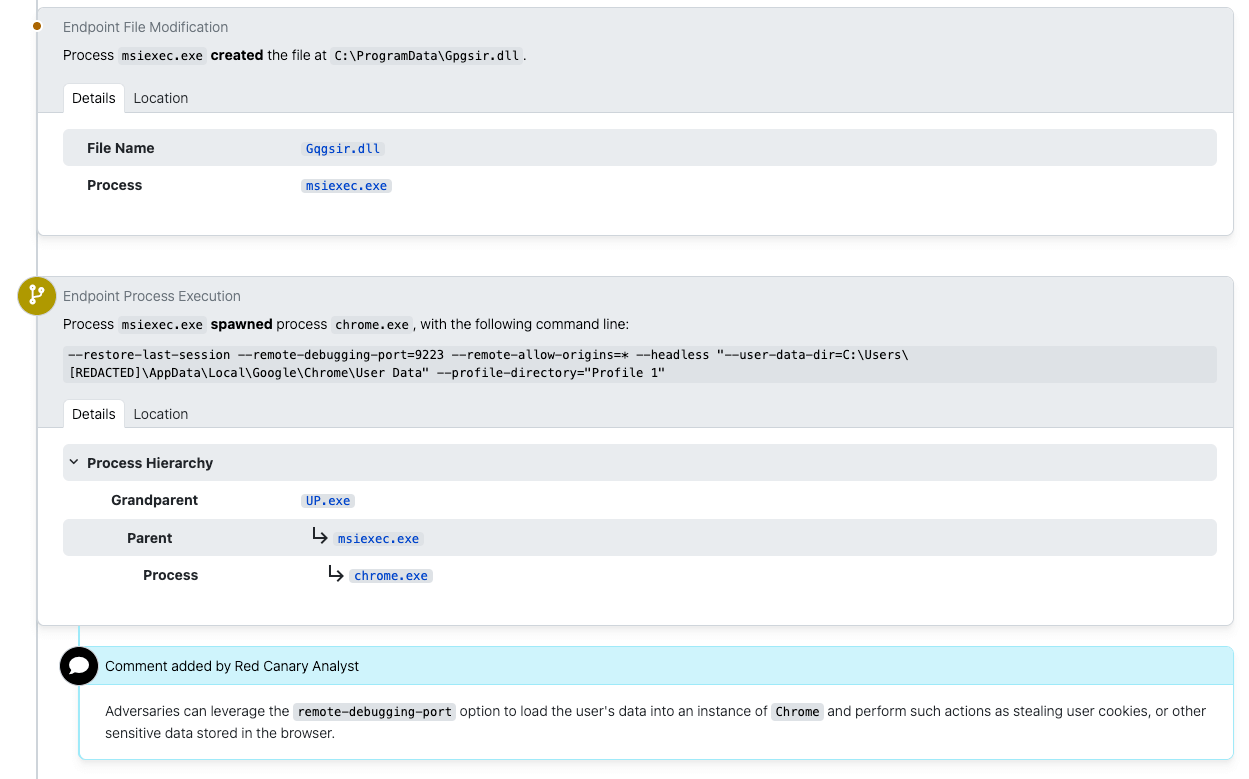
The following image shows what this activity might look like in a real detection:
Windows
In the last two months of the year, the occurrence of stealer malware jumped sharply, with adversaries deploying them in paste-and-run campaigns that instructed users to execute malicious PowerShell or Mshta commands via the Run dialog under the guise of a CAPTCHA challenge. These campaigns widely distributed LummaC2 in an opportunistic fashion, making it the most prevalent stealer we observed in 2024.
The overall volume of stealer detections increased slightly for 2024 compared to 2023, with each individual month fluctuating slightly in count. November 2024’s influx of LummaC2 drove up the statistics for the year.
Red Canary stealer detections
Note that the following guidance applies generally to stealers and specifically to LummaC2, so this information is largely replicated in our LummaC2 analysis in this report.
Because stealers are opportunistic and widely distributed in many ways, general preventative measures that apply to multiple malware families also help fight against stealers:
- Provide safe software installation sources for users
- Configure ad blocking tools where possible
- Deploy endpoint security controls for detection and protection
Nearly every organization is likely to encounter a stealer at some point, so it’s important to build a response plan before you need it. An excellent playbook would include determining what account details are stored in the software on an affected system, including:
- browsers
- file transfer software like FileZilla and WinSCP
- Telegram messaging
- Steam gaming
- cryptocurrency wallets
- VPN profiles
- cloud credentials in CLI tool configuration
- sensitive files stored in the user’s Desktop and Documents folders
Once you determine the scope of data theft, take steps to reset any credentials stored on the system. This may also involve manually revoking sessions to prevent cookie reuse. Finally, if financial details such as payment cards or cryptocurrency wallets are stored on the affected system, users may need to monitor the relevant accounts for unauthorized transactions.
Detection opportunities for stealer malware vary for each family. Multiple stealer families implemented a method of circumventing Google Chrome’s application bound encryption (ABE) controls, and that’s a great place to start.
Chrome ABE Bypass
The following detection analytic is a great starting point for security teams seeking to detect Chrome ABE bypass activity exhibited by multiple stealers.
process == ('chrome.exe' || 'msedge.exe')
&&
command_line_includes ('--remote-debugging-port' && '--headless')Some families such as RedLine do not leave file modification or registry evidence on disk for detection, while others, such as Raccoon, do. This means that detection depends on the different points of evidence that each malware family leaves behind. For example, RedLine is developed using the .NET Framework and it contains all the code necessary for taking information from browsers. During execution, RedLine leaves little telemetry but is often injected into other processes, which may be easily detected or mitigated depending on the process the adversary targets for injection. In the case of Raccoon and Vidar, these native C/C++ stealers rely on external DLLs for browser password theft. During execution, we can detect Raccoon and Vidar by identifying those DLL downloads and module loads.
Uncommon processes without command-line arguments and having network connections
Adversaries that deploy RedLine often combine the malware with different products intended to hide RedLine from security tools. These products often inject RedLine into unexpected processes such as InstallUtil.exe, MSBuild.exe, aspnet_compiler.exe, and more. While their intention to hide is clear, they usually don’t specify command-line arguments for these processes, which require arguments for successful legitimate execution. In addition, these processes don’t commonly establish external network connections. When taken together, these data points suggest that malware may have been injected into the suspicious process. While this isn’t always an indicator of RedLine stealer, it can help identify multiple malware families. See the Process Injection portion of this report for detailed detection guidance.
File modifications to AppData\LocalLow\*.dll
Raccoon stealer must download and load additional DLL files into memory so it can gather credentials from Chromium and Gecko-based web browsers. The downloaded DLLs often get stored in the AppData\LocalLow folder, which does not typically contain DLL content for Windows systems. These files include:
AppData\LocalLow\nss3.dllAppData\LocalLow\mozglue.dllAppData\LocalLow\sqlite3.dllAppData\LocalLow\msvcp140.dllAppData\LocalLow\vcruntime140.dllAppData\LocalLow\freebl3.dllAppData\LocalLow\softokn3.dll
File modifications to ProgramData\*.dll
Vidar stealer (and its derivatives) must also download and load additional DLL files for gathering credentials. The downloaded DLLs for this malware often get stored in the root of the ProgramData folder, a location that does not typically contain DLL content for Windows systems. The content of the DLL files themselves are the same as used by Raccoon; Vidar simply stores them in a different folder.
Start testing your defenses against stealers using Atomic Red Team—an open source testing framework of small, highly portable detection tests mapped to MITRE ATT&CK.
Getting started
As a category of threats, information stealers leverage far too wide a range of behaviors for us to offer meaningful testing guidance. However, security teams may be able to refine detection coverage for these and other stealers by running atomics for T1055: Process Injection and T1555.003: Credential from Web Browsers.
Additionally, security teams should consider testing their ability to observe or detect bypass techniques for Chrome’s new requirements for application bound encryption. Chrome v127+ uses app-bound encryption to protect cookies. The following test bypasses that protection to obtain the cookies. If successful, the test outputs cookie values to the console.
T1539: Steal Web Session Cookie (Atomic Test #4 – Steal Chrome v127+ cookies via Remote Debugging)
Review and repeat
Now that you have executed one or several common tests and checked for the expected results, it’s useful to answer some immediate questions:
- Were any of your actions detected?
- Were any of your actions blocked or prevented?
- Were your actions visible in logs or other defensive telemetry?
Repeat this process, performing additional tests related to this technique. You can also create and contribute tests of your own.