Midyear Updates
Threats
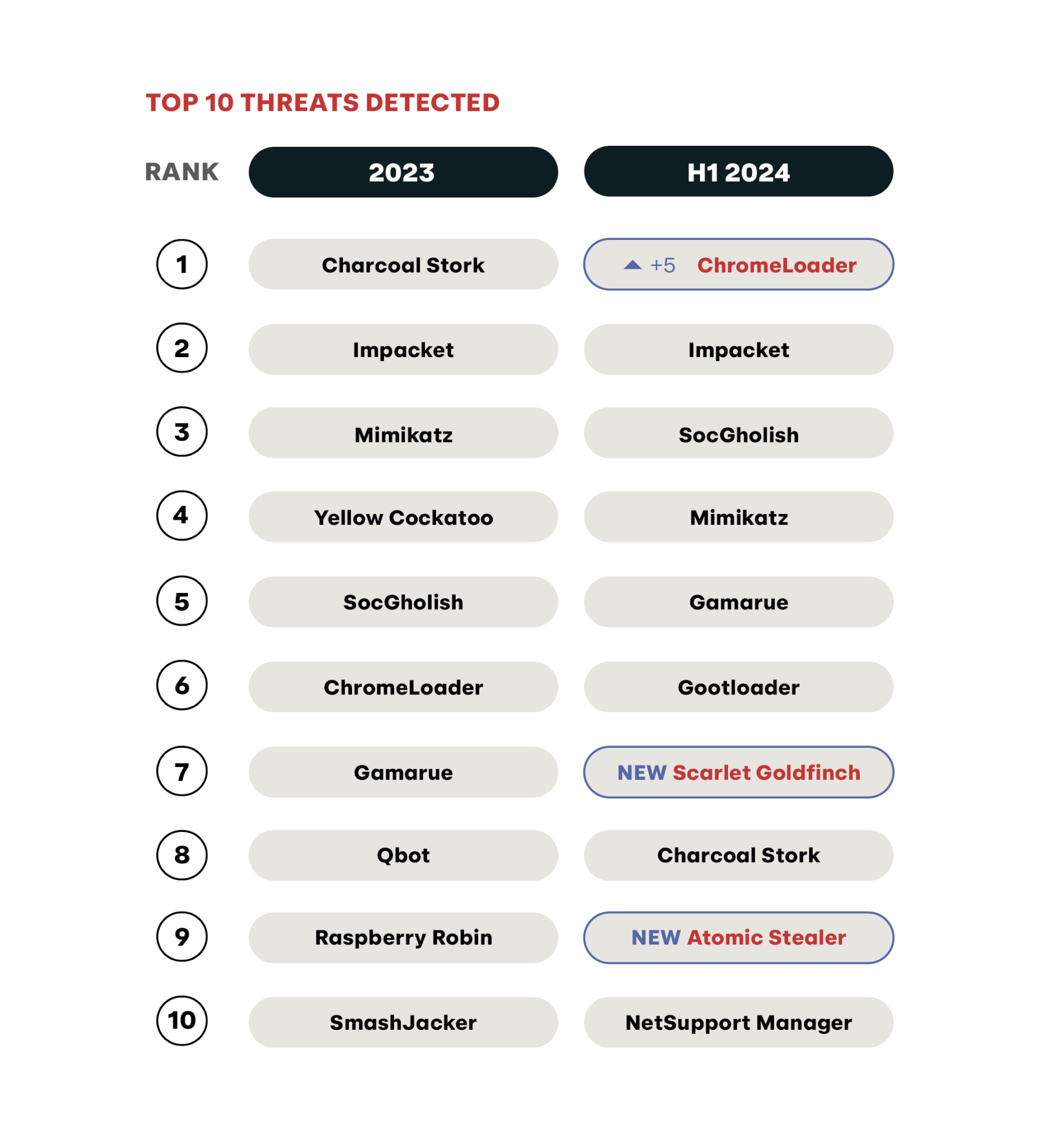
Our 10 most prevalent threats from the first half of this year bear a striking resemblance to the top 10 from 2023. Not much has changed, which is to be expected since there tends to be a decent number of holdovers from year to year. You’ve got the dual-use tools that show up almost annually in Impacket and Mimikatz; long-time threats that have been prevalent for years in SocGholish, Gamarue, and Gootloader; and the Charcoal Stork–ChromeLoader pairing that helped shape the top 10 threats in 2023.
However, it’s interesting to see that ChromeLoader has moved dramatically up the charts and overtaken the number one slot. Scarlet Goldfinch is a newcomer to the top 10, never before featured in the Threat Detection Report’s annual top 10 (but something of a mainstay in our monthly Intelligence Insights rankings in recent months). Atomic Stealer warrants mention given that it targets macOS devices, which represent a small percentage of the endpoints we monitor, and so its appearance in the top 10 here suggests that this threat is extremely prevalent on macOS devices.
The following compares the 2023 top 10 threats featured in the 2024 Threat Detection Report to the top 10 threats from the first six months of this year. Refer to the methodologies section to learn more about where these data come from.
In this section, we’re going to briefly explore:
- ChromeLoader and its relationship with Charcoal Stork
- Scarlet Goldfinch and how it’s different from SocGholish
- Atomic Stealer and macOS threats generally
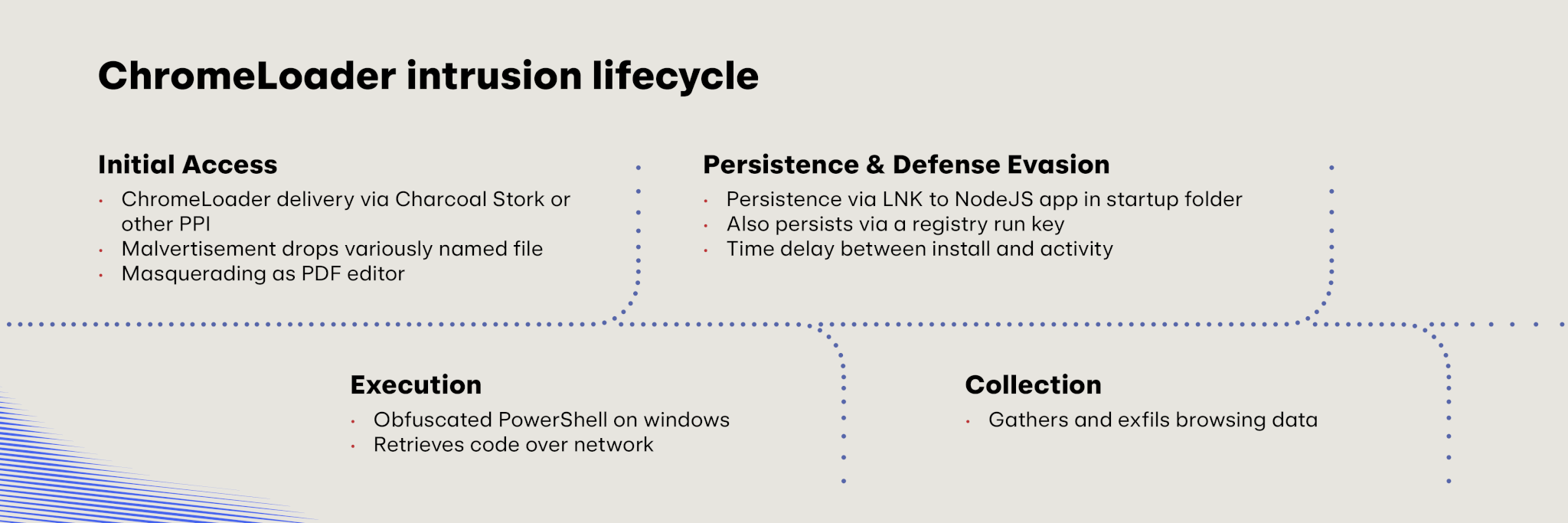
ChromeLoader (with special guest Charcoal Stork)
What is it?
ChromeLoader is a malicious browser extension that reads and hijacks browser traffic by modifying victims’ browser settings and redirecting their traffic to advertisement websites—likely to perform some kind of pay-per-click ad fraud. While the threat is admittedly more innocuous than the ransomware precursors in our top 10, it is nonetheless extremely prevalent and we consider it malicious (and not mere adware) because of its use of persistence mechanisms, ability to read and redirect searches, and potential for exposing sensitive information that could be used for targeted phishing campaigns. Furthermore, while ChromeLoader currently seems to serve the purpose of perpetuating some kind of advertising fraud, it could be readily adapted to deliver more overtly malicious code in the future.
ChromeLoader is closely related to another threat in our top 10: Charcoal Stork. A suspected pay-per-install provider, Charcoal Stork was our number one threat in the most recent Threat Detection Report following a dominant run of infections in 2023. Adversaries typically deliver Charcoal Stark via malvertising that promotes malicious installers masquerading as cracked games, fonts, or desktop wallpaper.
What can you do about it?
There’s extensive guidance on how to defend an organization against ChromeLoader (and Charcoal Stork) in the 2024 Threat Detection Report that remains viable, so we won’t retread all of that here. However, there are two relatively simple preventive strategies that nearly any security team can implement to diminish the risk posed by these threats.
- Forcing the installation of ad blockers across your organization may prevent the malicious advertisements that deliver Charcoal Stork (and by extension ChromeLoader) from rendering in the first place. Google has relatively simple instructions on how to do this from the Admin console in Chrome, and similar controls exist for Edge as well. Alternatively, more complex solutions for ad blocking may be available to organizations via their firewall configuration settings.
- Additionally, you can establish block and allow lists for extensions across an enterprise, potentially blocking users from ever installing the ChromeLoader browser extension in the first place. Google has simple instructions on how to do this in Chrome.
Scarlet Goldfinch (with special guests SocGholish and NetSupport Manager)
What is it?
Scarlet Goldfinch is an activity cluster defined by Red Canary that uses fake browser updates to trick users into downloading NetSupport Manager, a legitimate remote management and monitoring (RMM) tool that adversaries commonly abuse in intrusions. Another of the many examples in our prevalence list of web-based threat delivery, Scarlet Goldfinch is similar to SocGholish (hence the “S” and the “G”), but we started tracking it as a distinct threat in 2023 after observing conspicuous differences in tradecraft between the two threats.
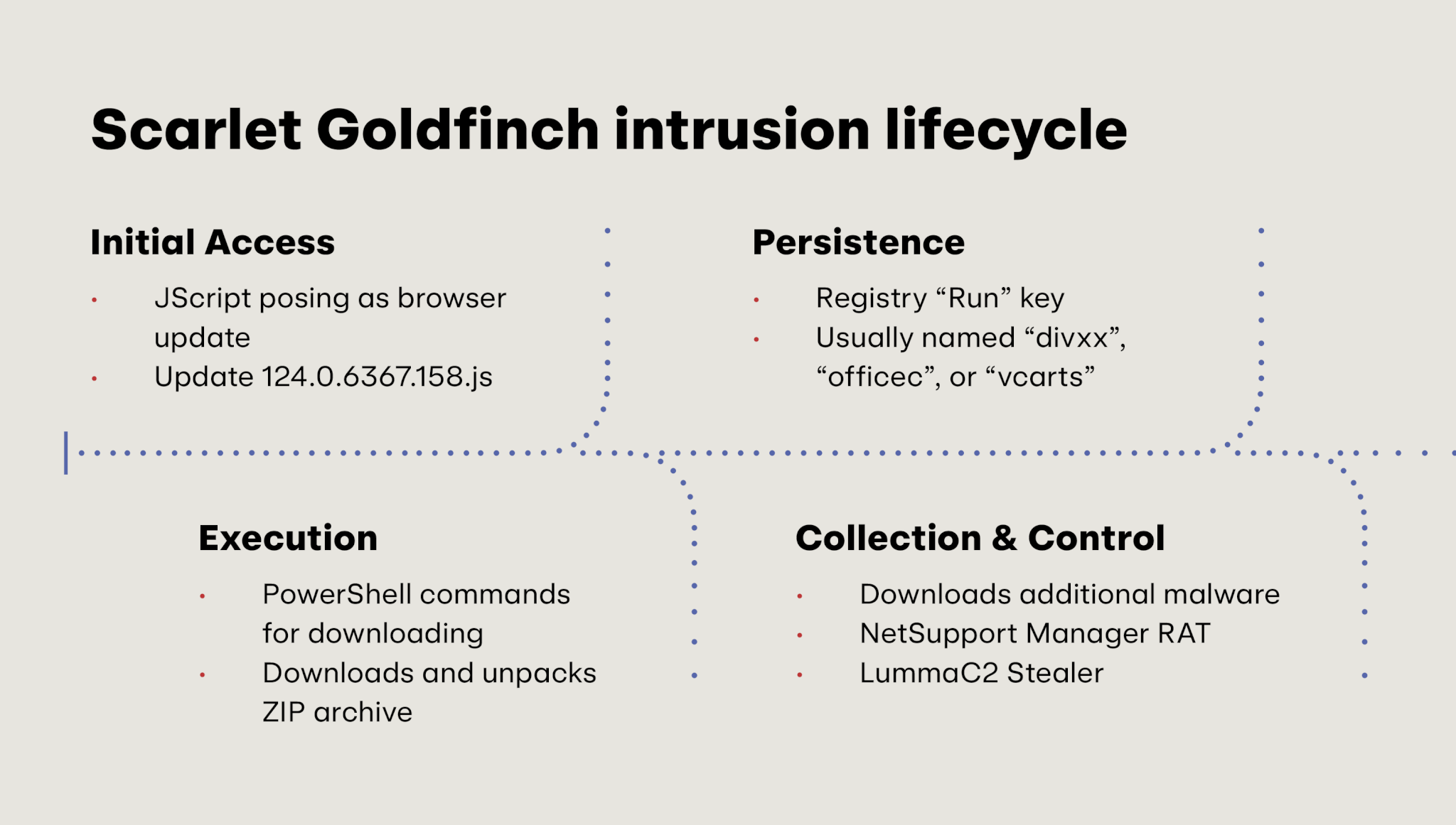
The following image briefly illustrates what separates SocGholish from Scarlet Goldfinch:
The crucial differentiator here is that Scarlet Goldfinch delivers NetSupport Manager—an RMM tool with the veneer of legitimacy—as its follow-on payload, whereas SocGholish typically delivers more overtly malicious or suspicious malware. Further, NetSupport Manager, the 10th most prevalent threat in the first six months of 2024, is a dynamic administrative tool offering a robust array of remote administration features that many organizations leverage to apply updates, manage assets, and deploy software. Adversaries often use this tool maliciously (and those are the instances where we detect it) because it simultaneously blends in while also giving adversaries a great deal of flexibility as they attempt to accomplish whatever their ultimate objectives are.
The following shows a rough timeline of a Scarlet Goldfinch infection.
What can you do about it?
There are multiple relatively straightforward ways to mitigate the threat posed both by Scarlet Goldfinch and its primary follow-on payload. We’ll start with the former.
Since Scarlet Goldfinch is delivered in the form of a JavaScript payload, defenders can effectively stop this threat before it starts by changing the default program that opens and executes JavaScript files from wscript.exe to something innocuous like notepad.exe. You can do this relatively easily by creating a Group Policy Object (GPO), which we described in depth in a blog in late May.
The most concerning component of Scarlet Goldfinch is its follow-on payload, NetSupport Manager. Broadly speaking, the first thing you may want to know is whether anyone—benign or otherwise—is using NetSupport Manager in your environment. Fortunately, Surveyor is a free and open source tool that works with supported EDRs to baseline environments for the presence of certain tools. Surveyor contains a definitions file that will search across an environment for the presence of NetSupport Manager (and a long list of other RMM and other tools) based on the presence of its process name (client32.exe), internal name (client32), domain connections to geo.netsupportsoftware.com, and its digital signature publisher (NetSupport Ltd).
Perhaps most importantly, security teams can leverage application control solutions to ensure that only approved RMM tools are used in their environment.
Atomic Stealer (and macOS threats generally)
What is it?
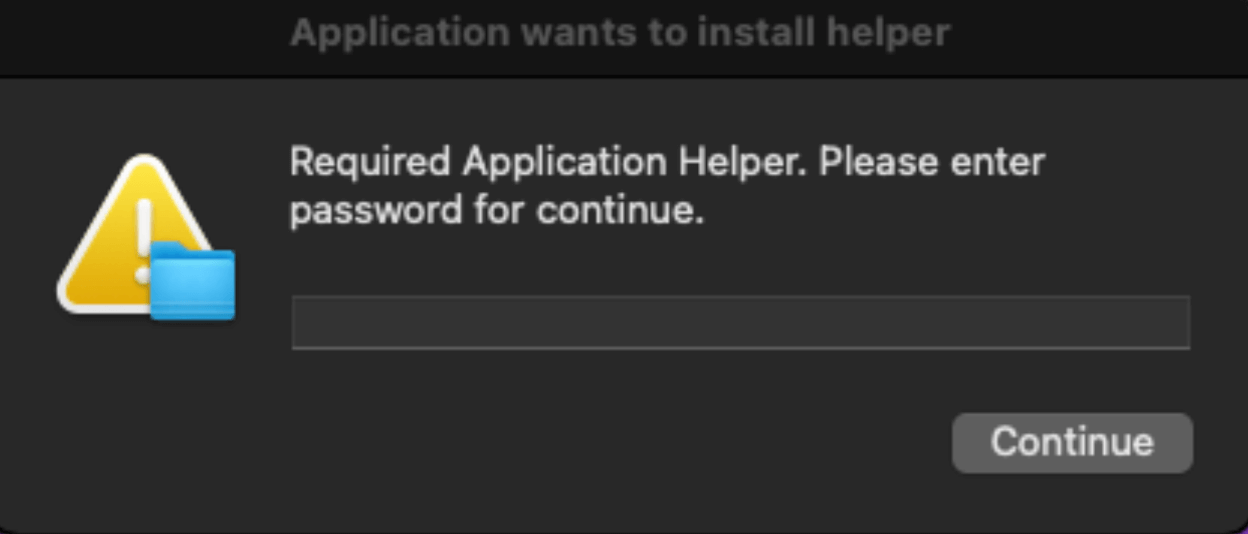
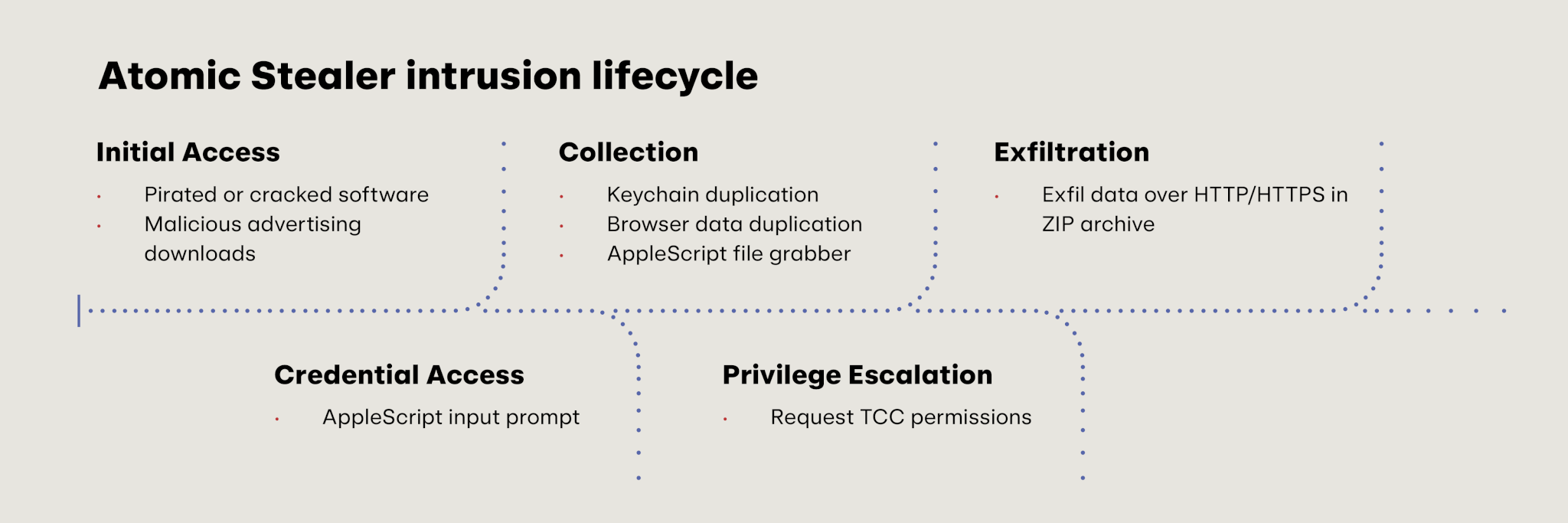
Yet another web-delivered threat in our top 10, Atomic Stealer is an infostealer that targets macOS systems—and it’s part of a general proliferation of stealers that target macOS systems along with threats like Banshee, Cthulhu, and Poseidon. Specifically, Atomic Stealer targets credentials, payment card data, cookies, keychain details, and information related to cryptocurrency wallets. It’s delivered via pirated or cracked software and malicious advertisements that prompt the end user to download the malware.
Downloading Atomic Stealer and other malware on macOS is relatively straightforward and can seem legitimate to unsuspecting users as it’s often nearly indistinguishable from downloading legitimate software from the internet. In fact, the malware often coaches users through the process of installing the malware.
That macOS malware would make our top 10 most prevalent threats at all is noteworthy. Like most infosec vendors, the majority of machines we protect are not macOS machines. To say we protect 10 times more Windows machines than macOS machines is probably a dramatic understatement, so Atomic Stealer’s presence on this list is a testament to just how prevalent it is in organizations with a significant macOS footprint.
The following shows the rough timeline of an Atomic Stealer infection:
What can you do about it?
The most common initial access for these threats is through users searching for software and obtaining it from malicious sources instead of trusted ones. Educating users about how and where to source software is critical, especially for macOS, where application control solutions are less common and complicated to use. However, providing ways for users to obtain software from safe, trusted sources can be massively beneficial. This can be as simple as a spreadsheet of known good links to approved software or as complex as a device management solution with software deployment options that put the burden of software installation on the IT department. We also strongly recommend proactively implementing some kind of ad-blocking technologies where possible.
It’s also important to keep your macOS systems updated. The built-in macOS XProtect YARA engine (their equivalent to Windows Defender) gets updated regularly and may get new detection rules for stealers. In addition, new updates may also improve controls such as Gatekeeper, which is supposed to protect users from threats downloaded from the internet.