Mac malware
macOS stealers ran rampant throughout most of 2024, until Apple remediated a Gatekeeper bypass with the release of macOS Sequoia.
In most years, macOS threats vary from their Windows counterparts for a variety of reasons, ranging from differences in operating system architecture, software support, relative market share, and more. In 2024, macOS experienced the same phenomenon that Windows did: An exponential increase in stealer malware. Stealers on macOS targeted cryptocurrency data, files on disk, and credentials in web browsers and user keychains—taking large amounts of data from victim systems.
The key difference in macOS threats from 2023 to 2024 was volume. Red Canary’s overall detection volume for macOS threats is relatively low, primarily because macOS devices represent a relatively small fraction of the endpoint devices we protect. Even so, we saw a 400 percent increase in macOS threats from 2023 to 2024, driven in large part by stealer threats like Atomic, Poseidon, Banshee, and Cuckoo stealers. Importantly, these threats were most active early in the year up until around the end of summer and then tapered off significantly toward the last few months of the year, a trend we’ll dive into below.
Red Canary observed four times as many macOS threats in 2024 than in 2023.
macOS threats in 2024
Although stealers have targeted macOS prior to 2024, this year showed a large proliferation of multiple stealer families targeting the platform. During the year, we observed Atomic, Poseidon, and Banshee stealers targeting macOS systems, with each family sharing some properties and diverging in small ways.
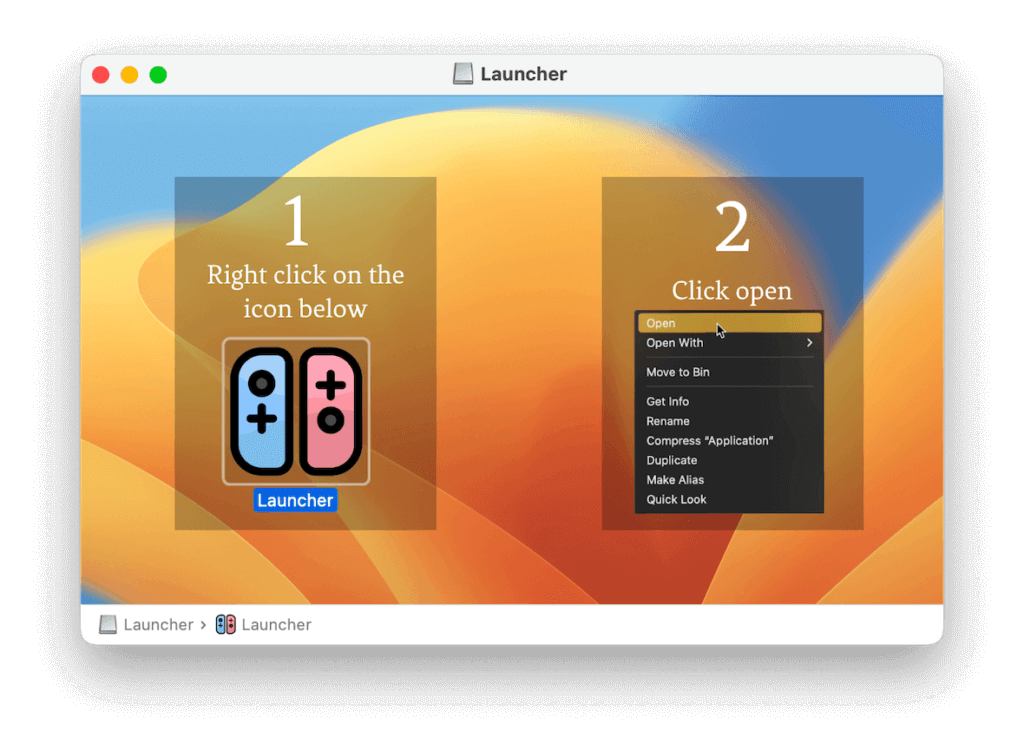
In terms of initial access, each of these families followed a well-tread pattern for most of the year. A victim encountered the malware by downloading it under the guise of free or cracked software or through a malicious advertisement. The user would download a disk image (DMG) file for macOS containing the malware inside. Once mounted, the user would encounter a dialog instructing them to right click on the downloaded software and click “Open.”
Image courtesy of Moonlock Labs
This dialog box surreptitiously instructed the user to bypass macOS Gatekeeper controls—a safety measure in macOS platforms to restrict the system into only executing signed code. At the time Gatekeeper could be bypassed for unsigned software by right-clicking on the unsigned software and instructing it to open. Apple eventually removed the ability to bypass Gatekeeper in this manner in September 2024 with macOS Sequoia, likely explaining the drop in detections we saw toward the end of the year.
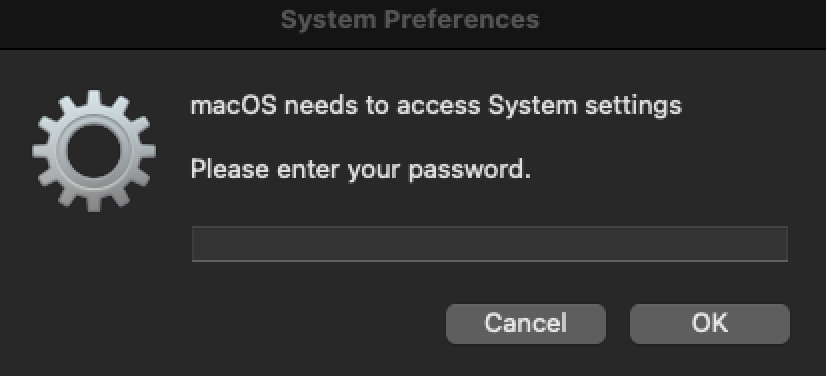
Once executed, the stealer would prompt the user for their password, mostly using AppleScript processes. Although the specific message often changed between stealer versions, it always either explicitly asked for password entry or implied the need to supply a password for a system change.
Images from sandbox executions
The adversary’s goal here is two-fold: to obtain the password itself and to use sudo commands in case they need to access additional sensitive data that requires elevated access. Once the victim enters their password, a multitude of file-gathering activities occur. These actions may change slightly between different stealer version, but they commonly target:
- macOS keychain files
- browser credentials in Google Chrome, Mozilla Firefox, Vivaldi, Brave, and other
- cookies in Safari
- Apple Notes databases
.txt,.pdf,.docx,wallet,key,keys, and.docfiles in user’sDesktopandDocumentsfolders- cryptocurrency wallets and browser extensions
- Telegram desktop data
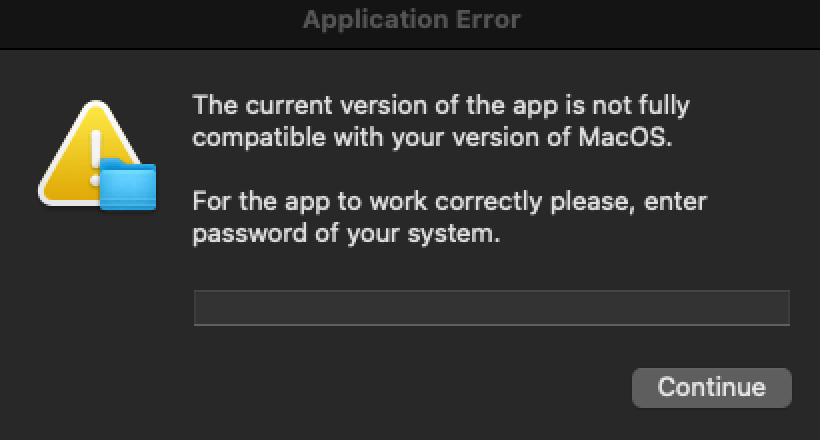
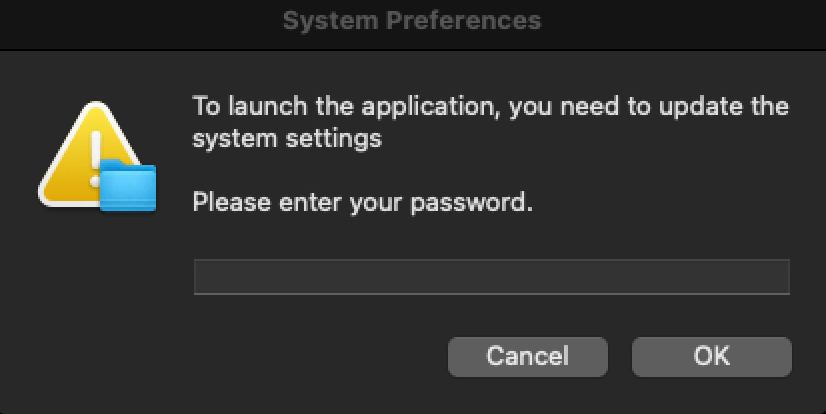
During the stealer execution, message boxes for macOS Transparency, Consent, and Control (TCC) would pop up asking to access sensitive data. From the number of stealers we observed in the year, we can assert that the TCC messages did precious little to stop the data theft as users clicked past them.
Image from sandbox executions
Once the data was gathered into a staging folder on disk, the stealers would compress it into a ZIP archive using a ditto command. Then, the ZIP archive would be exfiltrated to an adversary-controlled system over HTTP. Depending on the stealer family, this exfiltration may use curl commands to upload or it may be implemented in Objective-C or Swift code in the malware.
Apple takes action
In macOS Sequoia, Apple removed the Gatekeeper bypass commonly used by multiple stealer families for execution. This had a marked impact in the number of stealer executions we observed, with 95 percent of stealer infections happening prior to September and just 5 percent occurring after.
Starting in September, the number of macOS stealer detections tapered off with only occasional encounters.
95 percent of the year’s stealer detections arrived before September 2024.
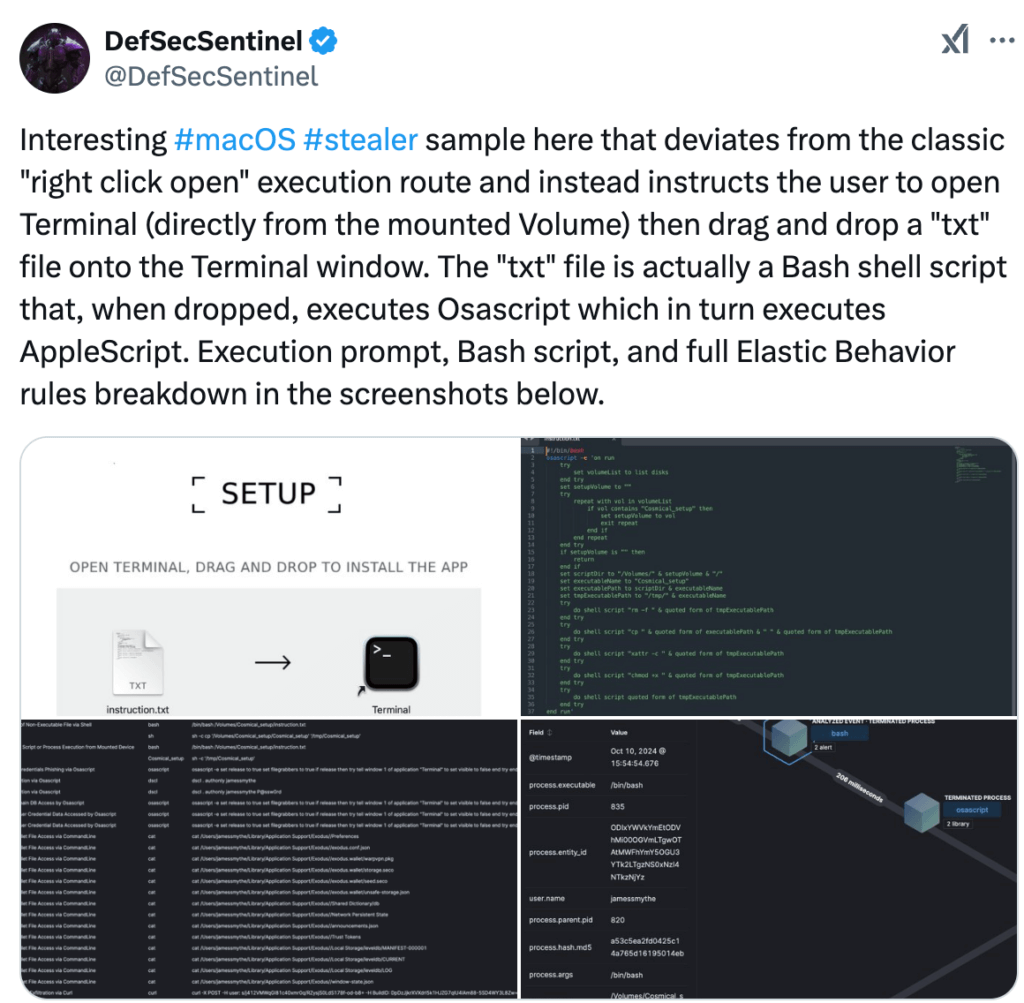
This feature change also caused adversaries to experiment with different ways to distribute their malware, as seen in this tweet by DefSecSentinel:
In the malware sample shown, the adversary decided to distribute their initial payload as a shell script within a DMG file, coaching the user through dragging it on top of a Terminal icon to launch it. With this approach, Gatekeeper doesn’t stand in the way of malware execution.
With Gatekeeper bypasses off the menu in new macOS builds, adversaries now have to try harder to distribute their malware. This trend has continued into 2025 as some adversaries have tried to distribute stealers masquerading as the Homebrew tool for macOS, or even as “video interview” material.
macOS devices should have comprehensive protections in place, including:
- antivirus
- anti-malware controls
- endpoint detection and response (EDR)
Without visibility, detection and response are much more difficult. To explore what telemetry data is possible to gather, consider checking out the free Mac Monitor.
The mitigations here are the same for any other stealer families, providing safe software sources and a robust response plan. For macOS-specific actions, consider further educating users on TCC controls in macOS and presenting scenarios when users may not want to bypass TCC to preserve their own security and privacy.
For endpoints where a stealer has run, consider resetting all TCC permissions so they will re-fire in the future even if a user approves access by executing:
sudo tccutil reset All
Password theft via osascript
The following pseudo-detector looks for adversaries abusing the osascript process in an effort to prompt a user to enter passwords.
process_name == osascript
&&
command_line includes ('password' and 'answer')Stealing files and cookies with osascript
The following pseudo-detector looks for adversaries abusing osascript to steal Safari cookies.
process_name == osascript
&&
command_line includes ('duplicate file' && 'Cookies.binarycookies')The following Atomic Red Team tests can help generate telemetry common to macOS stealers:
This test copies the contents from Keychain using the cat utility in a manner consistent with Atomic stealer.
T1539: Steal Web Session Cookie (Atomic Test #5 – Copy Safari BinaryCookies files using AppleScript)
This test leverages AppleScript to copy cookies from the Safari browser in a manner consistent with Atomic Stealer.
T1005: Data from Local System (Atomic Test #3 – Copy Apple Notes database files using AppleScript)
This test leverages AppleScript to copy the contents of the Apple Notes database in a manner consistent with Atomic Stealer.